当前位置:网站首页>Common sense of cloud server security settings
Common sense of cloud server security settings
2022-07-02 04:04:00 【Yile】
1、 Server external firewall
Server security group , Some are called security groups ; Some are called firewalls
2、 External firewall and internal firewall
External firewall ( Security group / A firewall )
Built in firewall (iptables/firewalld)
3、 Firewall function :
A firewall is like a door , Imagine hiding your money in your room , At this time, a thief wants to steal your money , Thieves need to sneak into your front door first 【 External firewall ( Security group / A firewall )】,
And then sneak into your room 【 Built in firewall (iptables/firewalld)】
Although the built-in firewall and the external firewall are more secure when used together , But it affects the efficiency of data access , For speed , Sometimes just make sure it's safe , No need to be safer .
4、 Buy a good server , First, set up the external firewall
(1) Aliyun server : Configuration release 80、443、ssh port (ssh The port is recommended to be modified , Do not use default 22)
(2) Tencent cloud server : Configuration release 80、443、ping port 、ssh port (ssh The port is recommended to be modified , Do not use default 22)
Those who have purchased Tencent cloud services should pay attention to :
Create security groups , When configuring rules , Do not choose to release all ports , To select custom , Then release 80、443、ping、ssh port
5、 modify ssh Port number
modify 22 Port idea :
Let go at the external firewall first ssh Default port for 22, And then use xshell Connect with the remote connection tool ,
Then add... In the configuration file 22 port 、 new port , After the configuration is successful , After testing the new port, you can comment out the... In the configuration file 22 port , And the external firewall is prohibited 22 port
(1) Release the default port number at the external firewall 22

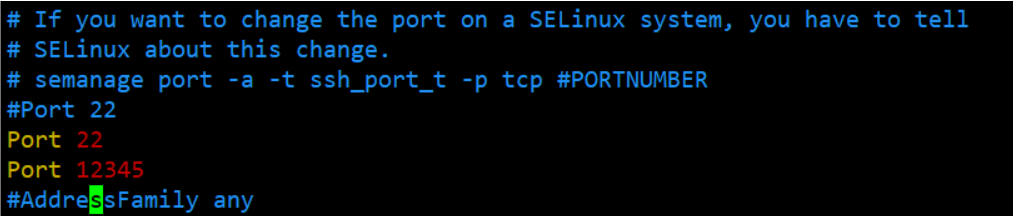
(2) edit /etc/ssh/sshd_config file , Add port number
vim /etc/ssh/sshd_config
- for example : Add port 22、12345, Exit after saving
Add two ports to keep 22 The purpose of the port : Prevent possible permissions and configuration issues , It can be closed after the test is successful 22 port
- The newly added port number range is recommended : When you modify the port, you'd better choose 10000~65535 Port number between ,10000 The following are easily occupied by the system or some special software , Or when a new application is going to occupy the port in the future , But you took it first , Cause the software to fail to run .
(3) restart sshd
- CentOS 7.x The above systems , Carry out orders
systemctl restart sshd.service
- CentOS 6.x The following systems , Carry out orders
/etc/init.d/sshd restart
(4) Add firewall rules , Release the modified port
- if centos7 System :
Example opening 12345 port :
* Open port 12345: firewall-cmd --zone=public --add-port=12345/tcp --permanent
● Close the port 12345: firewall-cmd --zone=public --remove-port=12345/tcp --permanent
* Reload : Make rules effective : firewall-cmd --reload
* see zone=public Port information for :firewall-cmd --list-ports --zone=public
- if centos6 System :
# iptables Profile location /etc/sysconfig/iptables
# add to 12345 Port rules
iptables -A INPUT -m state --state NEW -m tcp -p tcp --dport 12345 -j ACCEPT
# Preservation rules
service iptables save
# Restart the service
service iptables restart
(5) The external firewall prohibits 22 port , Add the newly configured port

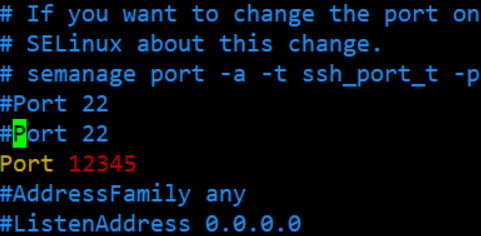
(6) modify xshell Port number in the attribute of , After the test connection is successful , take ssh Profile's 22 Port commented out
- modify xshell Port number in the attribute of , Test connection :

- After the test connection is successful , take ssh Profile's 22 Port commented out :
vim /etc/ssh/sshd_config
6、 The meaning of opening the firewall to release only the required ports
There is no need to expose ports casually , Otherwise there will be security risks , There are always a lot of machines scanning your ports , Try to access your service .
Especially like redis port , It may cause mining virus in you ; also ssh port 22, Every moment in the public network, someone tries to log in to your server by brutally cracking the password dictionary .
7、 Summarize the security common sense of using the server
* Minimize the number of exposed ports , And try to modify the default port number , Try to set complex passwords
* Do not use or install software from unknown sources
* Timely repair the vulnerabilities prompted by the system and known vulnerabilities of the software
* Check the log regularly
* Install anti-virus software : Kaspersky Free Edition can resist blackmail virus ; install banip Software , error 5 Secondary cipher , Refuse 24 Hours , Prevent violent password cracking ;
Minimize the number of exposed ports
First expose the necessary ports http(80)、https(443)、ssh port ( Do not use default )、ping( Tencent server needs ); Other ports that need to be released , Consider using nginx Forwarding by proxy
Modify the default port :
such as mysql The default port number is 3306, Need to use mysql If exposed , It is suggested to amend it to mysql The configuration file of is changed to another port number ;
Empathy ,redis If you want to use it on the public network , It is also suggested to modify redis The port number in the configuration file is another port number , No default 6379
Set complex password :
You can set the password , And the password should not be set too simply .
such as mysql Set too weak password , Can also pass through myql Weave into the Trojan horse program ; And such as redis Release default port 6379, And then do not set redis password , It may be embedded in the mining program .
If this article is helpful to you, remember to give me a compliment , thank !
边栏推荐
- 整理了一份ECS夏日省钱秘籍,这次@老用户快来领走
- Demonstration description of integrated base scheme
- 66.qt quick-qml自定义日历组件(支持竖屏和横屏)
- [personnel density detection] matlab simulation of personnel density detection based on morphological processing and GRNN network
- Delete the code you wrote? Sentenced to 10 months!
- Recently, the weather has been extremely hot, so collect the weather data of Beijing, Shanghai, Guangzhou and Shenzhen last year, and make a visual map
- 树莓派GPIO引脚控制红绿灯与轰鸣器
- 《动手学深度学习》(二)-- 多层感知机
- 潘多拉 IOT 开发板学习(HAL 库)—— 实验2 蜂鸣器实验(学习笔记)
- Analysis of the overall design principle of Nacos configuration center (persistence, clustering, information synchronization)
猜你喜欢

The second game of the 12th provincial single chip microcomputer competition of the Blue Bridge Cup

【无线图传】基于FPGA的简易无线图像传输系统verilog开发,matlab辅助验证

云服务器的安全设置常识
Learn more about materialapp and common attribute parsing in fluent
蓝湖的安装及使用
10 minutes to understand CMS garbage collector in JVM
MySQL error: expression 1 of select list is not in group by claim and contains nonaggre

Lei Jun wrote a blog when he was a programmer. It's awesome

Hand tear - sort

C语言:逻辑运算和判断选择结构例题
随机推荐
JVM knowledge points
Installation and use of blue lake
Which insurance company has a better product of anti-cancer insurance?
Pandora IOT development board learning (RT thread) - Experiment 1 LED flashing experiment (learning notes)
[JS event -- event flow]
go 分支与循环
LxC limits the number of CPUs
Hand tear - sort
Go language naming specification
整理了一份ECS夏日省钱秘籍,这次@老用户快来领走
[wireless image transmission] FPGA based simple wireless image transmission system Verilog development, matlab assisted verification
Go branch and loop
Jetpack之LiveData扩展MediatorLiveData
Www2022 | know your way back: self training method of graph neural network under distribution and migration
"No war on the Western Front" we just began to love life, but we had to shoot at everything
2022-07-01: at the annual meeting of a company, everyone is going to play a game of giving bonuses. There are a total of N employees. Each employee has construction points and trouble points. They nee
Wpviewpdf Delphi and Net PDF viewing component
Hands on deep learning (II) -- multi layer perceptron
Document declaration and character encoding
Vite: configure IP access