当前位置:网站首页>leetcode刷题_反转字符串中的元音字母
leetcode刷题_反转字符串中的元音字母
2022-07-06 01:19:00 【身影王座】
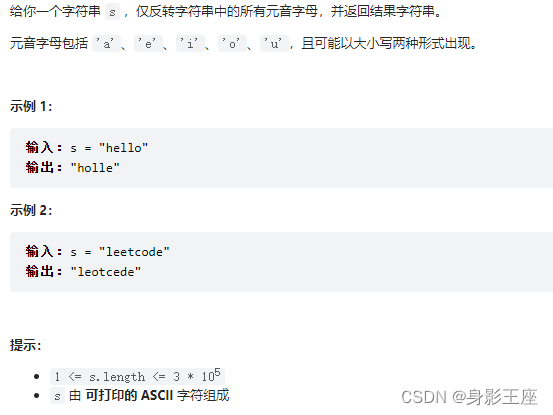
题目描述
Java解决方法
import java.util.*;
class Solution {
public String reverseVowels(String s) {
// ArrayList中有判断一个字符是否在一个数组中
Collection c = new ArrayList();
c.add('a');c.add('e');c.add('i');c.add('o');c.add('u');
c.add('A');c.add('E');c.add('I');c.add('O');c.add('U');
int head = 0;
int tail = s.length() - 1;
// 修改字符串中某个字符需要StringBuilder
StringBuilder s1 = new StringBuilder(s);
while(head < tail)
{
char a1 = s1.charAt(head);
char a2 = s1.charAt(tail);
if(!c.contains(a1))
{
head++;
}
else if(!c.contains(a2))
{
tail--;
}
else
{
s1.setCharAt(head, a2);
s1.setCharAt(tail, a1);
head++;
tail--;
}
}
String s2 = s1.toString();
return s2;
}
}
C语言解决方法
int nocontains(char a)
{
if(a != 'a' && a != 'A' && a != 'e' && a != 'E' && a != 'i' && a != 'I' && a != 'o' && a != 'O' && a != 'u' && a != 'U')
{
return 1;
}
return 0;
}
char * reverseVowels(char * s){
int head = 0;
int tail;
tail = strlen(s) - 1;
while(head < tail)
{
char a;
char b;
a = s[head];
b = s[tail];
if(nocontains(a))
{
head++;
}
else if(nocontains(b))
{
tail--;
}
else
{
s[head] = b;
s[tail] = a;
head++;
tail--;
}
}
return s;
}
边栏推荐
- IP storage and query in MySQL
- Vulhub vulnerability recurrence 75_ XStream
- Beginner redis
- Yii console method call, Yii console scheduled task
- Live video source code, realize local storage of search history
- [Arduino syntax - structure]
- The inconsistency between the versions of dynamic library and static library will lead to bugs
- Is chaozhaojin safe? Will it lose its principal
- cf:H. Maximal AND【位运算练习 + k次操作 + 最大And】
- Pbootcms plug-in automatically collects fake original free plug-ins
猜你喜欢
Five challenges of ads-npu chip architecture design
Pbootcms plug-in automatically collects fake original free plug-ins
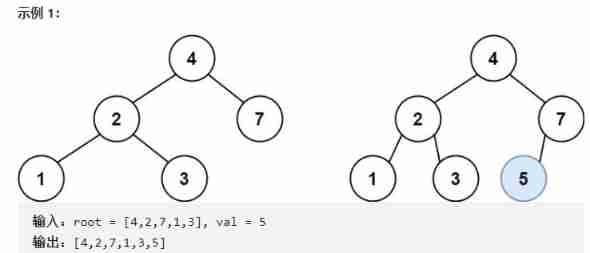
Recursive method to realize the insertion operation in binary search tree
About error 2003 (HY000): can't connect to MySQL server on 'localhost' (10061)
Dedecms plug-in free SEO plug-in summary
![Cf:d. insert a progression [about the insert in the array + the nature of absolute value + greedy top-down]](/img/9e/c933f454a39d906a407e4d415f0b87.png)
Cf:d. insert a progression [about the insert in the array + the nature of absolute value + greedy top-down]
毕设-基于SSM高校学生社团管理系统
yii中console方法调用,yii console定时任务
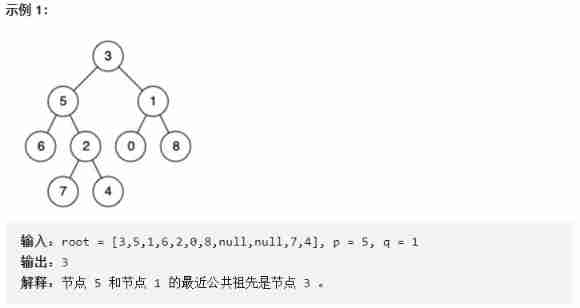
Finding the nearest common ancestor of binary tree by recursion
Loop structure of program (for loop)
随机推荐
Vulhub vulnerability recurrence 74_ Wordpress
Exciting, 2022 open atom global open source summit registration is hot
MobileNet系列(5):使用pytorch搭建MobileNetV3并基于迁移学习训练
ADS-NPU芯片架构设计的五大挑战
cf:H. Maximal AND【位运算练习 + k次操作 + 最大And】
Netease smart enterprises enter the market against the trend, and there is a new possibility for game industrialization
现货白银的一般操作方法
什么是弱引用?es6中有哪些弱引用数据类型?js中的弱引用是什么?
视频直播源码,实现本地存储搜索历史记录
Cglib dynamic agent -- example / principle
Four dimensional matrix, flip (including mirror image), rotation, world coordinates and local coordinates
Electrical data | IEEE118 (including wind and solar energy)
Xunrui CMS plug-in automatically collects fake original free plug-ins
MATLB|实时机会约束决策及其在电力系统中的应用
Leetcode study - day 35
Recoverable fuse characteristic test
A glimpse of spir-v
DD's command
Remember that a version of @nestjs/typeorm^8.1.4 cannot be obtained Env option problem
Is chaozhaojin safe? Will it lose its principal