当前位置:网站首页>Redis: hash type data operation command
Redis: hash type data operation command
2022-07-04 04:28:00 【dengfengling999】
single key: object ( Property name - Property value ...)
Hash type (hash)
Redis Of hash It's a string Type of key and value Mapping table , there value It's a series of key-value pairs ,hash Ideal for storing objects .
The general idea of hash type data operation is through key and field operation value,key It's a data ID ,field Is domain ,value It's our feeling
Business data of interest .


1.hset
grammar :hset key field value [field value …]
function : Set the key value to field-value Set to Hash list key in , If key non-existent , Then create a new Hash list , The assignment is then performed , If key Under the field Already exist , be value Value override .
Return value : Returns the number of key value pairs successfully set .
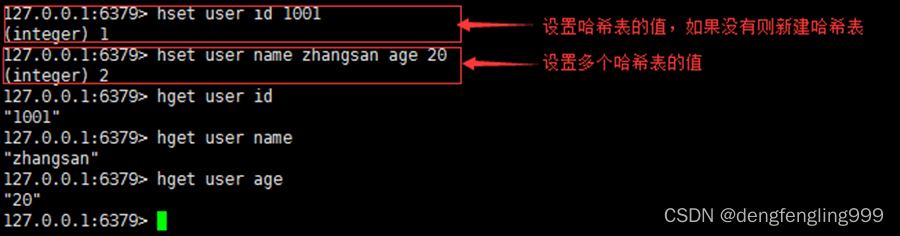
for example :

2.hget
grammar :hget key field
function : Get hash table key Given domain in field Value .
Return value :field Domain value , If key Nonexistence or field There is no return nil.
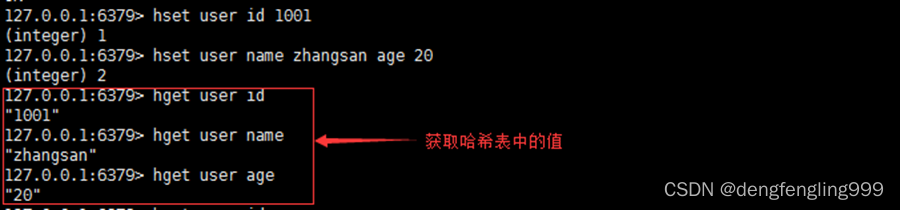
for example :

3.hmset and hset Function as
grammar :hmset key field value [field value…]
function : There will be more than one field-value ( Domain - value ) Set to hash table key in , This command will overwrite the existing field,hash surface key non-existent , Create empty hash surface , Re execution hmset.
Return value : Set successfully returned ok, If it fails, an error is returned .

for example :
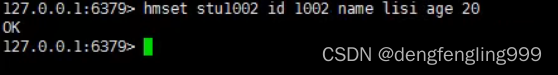
4.hmget
grammar :hmget key field [field…]
function : Get hash table key The value of one or more given fields in
Return value : Return and field The value corresponding to the order , If field non-existent , return nil.
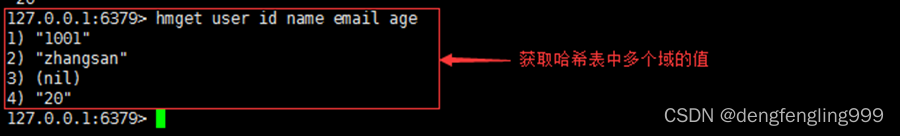
for example :

Don't know hsah Medium file Time use :
5.hgetall
grammar :hgetall key
function : Get hash table key All fields and values in
Return value : Return... As a list hash The values of the middle field and the field ,key non-existent , Returns an empty hash.
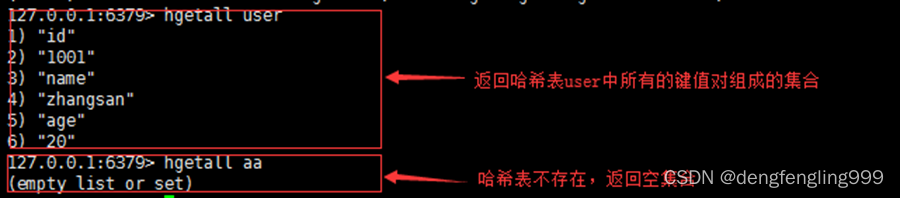
for example :

6.hdel
grammar :hdel key field [field…]
function : Delete hash table key One or more specified domains in field, non-existent field Direct to ignore .
Return value : Successfully deleted field The number of .

for example :

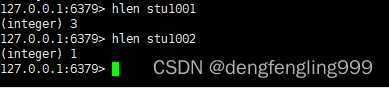
7.hlen
grammar :hlen key
function : Get hash table key Mesosphere field The number of
Return value : The number ,field The number of .key There is no return 0.
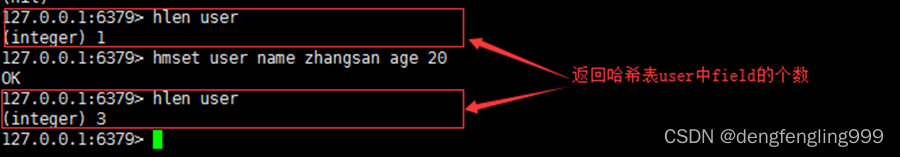
for example :
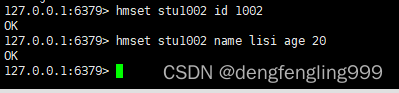
8.hexists
grammar :hexists key field
function : Look at the hash table key in , Given domain field Whether there is
Return value : If field There is , return 1, Other return 0.

for example :stu1002 above name Has deleted

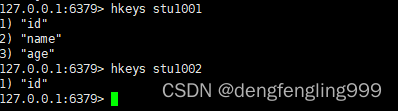
9.hkeys
grammar :hkeys key
function : Look at the hash table key All in field Domain list
Return value : Contains all the field A list of ,key There is no return empty list
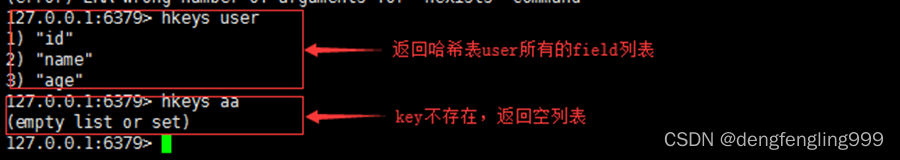
for example :
10.hvals
grammar :hvals key
function : Return hash table List of values for all fields in
Return value : A list of all the field values in the hash table ,key There is no return empty list .

for example :

11.hincrby
grammar :hincrby key field int
function : To the hash table key Medium field Domain addition int
Return value : Returns the added field Domain value
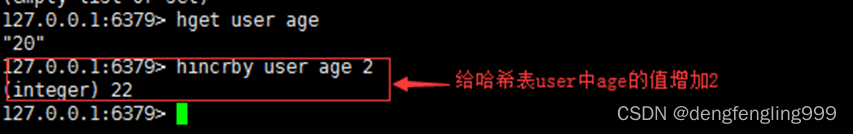
for example :


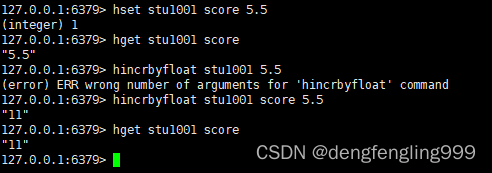
12.hincrbyfloat
grammar :hincrbyfloat key field float
function : To the hash table key Medium field Domain addition float
Return value : Returns the added field Domain value

for example :
13.hsetnx
grammar :hsetnx key field value
function : Hash table key In the domain field Is set to value , If and only if domain field Set when it doesn't exist , Otherwise, do not set .
Return value : Set value returned successfully 1, Other return 0.
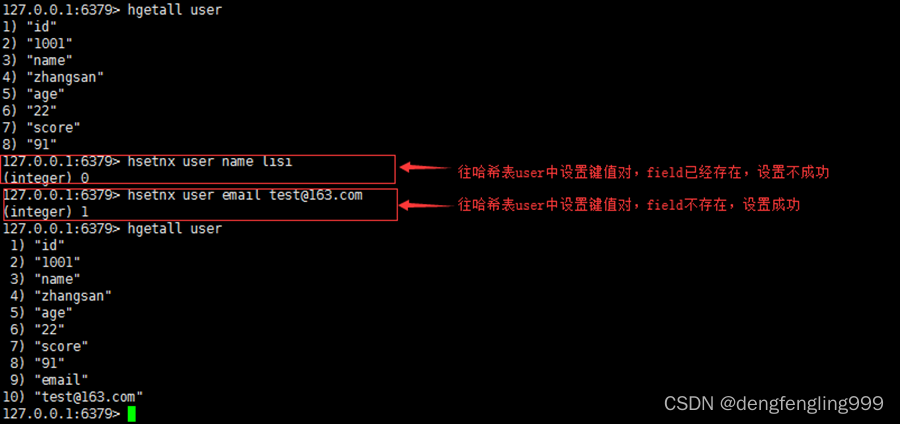
for example :

边栏推荐
- [microservices openfeign] two degradation methods of feign | fallback | fallbackfactory
- Leetcode brush question: binary tree 06 (symmetric binary tree)
- (pointeur) Écrivez - vous une fonction qui compare la taille de la chaîne et fonctionne comme strcmp.
- [webrtc] M98 Ninja build and compile instructions
- Interpretation of leveldb source code skiplist
- “找工作不要太在意工资”,这是我听过最大的谎言
- Unity Resource path
- Leetcode skimming: binary tree 09 (minimum depth of binary tree)
- Flink learning 7: application structure
- Use NRM and NVM to manage your NPM source and node versions
猜你喜欢

透过JVM-SANDBOX源码,了解字节码增强技术原理

Flink学习7:应用程序结构

深入解析结构化异常处理(SEH) - by Matt Pietrek

Redis:有序集合zset类型数据操作命令
【微服务|openfeign】@FeignClient详解

NFT新的契机,多媒体NFT聚合平台OKALEIDO即将上线

Flink学习6:编程模型

Flink learning 7: application structure

UnicodeDecodeError: ‘gbk‘ codec can‘t decode byte 0x98 in position 1093: illegal multibyte sequence
RHCSA 04 - 进程管理
随机推荐
The interactive solution of JS and app in the H5 page embedded in app (parameters can be transferred and callbacks can be made)
领导:谁再用redis过期监听实现关闭订单,立马滚蛋!
[microservice openfeign] use openfeign to remotely call the file upload interface
NFT新的契机,多媒体NFT聚合平台OKALEIDO即将上线
RHCSA 04 - 进程管理
毕业三年,远程半年 | 社区征文
Katalon uses script to query list size
EIG在智利推出可再生能源平台Grupo Cerro
Pytest basic self-study series (I)
软件测试是干什么的 发现缺陷错误,提高软件的质量
ROS2中CMake编译选项的设置
VIM mapping command
Main applications of TDK lambda power supply
Tcp- simple understanding of three handshakes and four waves
疫情远程办公经验分享| 社区征文
微信脑力比拼答题小程序_支持流量主带最新题库文件
leetcode刷题:二叉树07(二叉树的最大深度)
RHCSA 03 - 文件的基础权限
B. All Distinct
透过JVM-SANDBOX源码,了解字节码增强技术原理