当前位置:网站首页>Apache multiple component vulnerability disclosure (cve-2022-32533/cve-2022-33980/cve-2021-37839)
Apache multiple component vulnerability disclosure (cve-2022-32533/cve-2022-33980/cve-2021-37839)
2022-07-08 01:47:00 【Murphy safety】
OSCS( Open source software supply chain security community ) Launch free vulnerabilities 、 Poison information subscription service , Community users can subscribe to intelligence information through robots , For specific subscription methods, please refer to :
https://www.oscs1024.com/?src=csdn
7 month 6 Japan ,OSCS Detected Apache The loopholes of many projects under the foundation are open , Please pay attention to the developers who use the corresponding components .
Vulnerability description
1、Apache Portals Jetspeed-2(CVE-2022-32533)
Apache Portals Jetspeed-2 User input is not handled securely , Led to including XSS、CSRF、XXE and SSRF Including many problems .
- Vulnerability impact level : Middle risk
- Utilization cost : low
- Affected components :org.apache.portals.jetspeed-2:jetspeed-2
- Affects version :[*,2.3.1], The government no longer maintains , No fix version
- CVE Number :CVE-2022-32533
With XSS For example , The registered user name is set to when , After registering and logging in, each time the user name is loaded, a pop-up window will be triggered , To configure xss.filter.post = true Can mitigate risks .
But officials say Apache Portals Jetspeed-2 yes Apache Portals Items that are no longer maintained in , No updates will be provided ,OSCS Suggest developers to replace .
Reference link :
https://www.oscs1024.com/hd/MPS-2022-17607/?src=csdn
https://nvd.nist.gov/vuln/detail/CVE-2022-32533
2、Apache Commons Configuration(CVE-2022-33980)
Apache Commons Configuration Is a component for managing configuration files , stay 2.8 Some previous versions supported multiple variable value methods , Include javax.script、dns and url, Result in arbitrary code execution or network access .
- Vulnerability impact level : Middle risk
- Utilization cost : high
- Affected components :org.apache.commons:commons-configuration2
- Affects version :[2.4,2.8.0), The authorities are already in 2.8.0 Version fixes this problem by disabling dangerous methods
- CVE Number :CVE-2022-33980
Form like ${prefix:name} The string of can be parsed , When interpolate When the string of the operation is controllable , Vulnerabilities can be exploited , Supported by prefix Here's the picture .

The following code can trigger

Reference link :
https://www.oscs1024.com/hd/MPS-2022-19214/?src=csdn
https://nvd.nist.gov/vuln/detail/CVE-2022-33980
3、Apache Superset(CVE-2021-37839)
Apache Superset Is a data visualization and data exploration platform . stay Apache Superset In the affected version , Authenticated users can access metadata information related to the dataset without authorization , Include dataset name 、 Columns and indicators .
- Vulnerability impact level : Middle risk
- Utilization cost : in
- Affected components :apache-superset
- Affects version :[*,1.5.1), The authorities are already in 1.5.1 Version to fix this
- CVE Number :CVE-2021-37839
Reference link :
https://www.oscs1024.com/hd/MPS-2021-28604/?src=csdn
https://nvd.nist.gov/vuln/detail/CVE-2021-37839
The disposal of advice
OSCS It is recommended that users use the above components according to the above risk tips , Repair to a safe version as soon as possible .
See more vulnerability information :https://www.oscs1024.com/hl
Learn more about
1、 Free use OSCS Intelligence subscription service
OSCS ( Open source software supply chain security community ) The latest security risk dynamics of open source projects will be released at the first time , Including open source component security vulnerabilities 、 Information such as events , Community users can use enterprise and wechat 、 nailing 、 Fly Book Robot and other ways to subscribe to intelligence information , For specific subscription methods, please refer to :
https://www.oscs1024.com/docs/vuln-warning/intro/


————————————————
Copyright notice : This paper is about CSDN Blogger 「 Open source ecological security OSCS」 The original article of , follow CC 4.0 BY-SA Copyright agreement , For reprint, please attach the original source link and this statement .
Link to the original text :https://blog.csdn.net/cups107/article/details/125653978
边栏推荐
- Euler Lagrange equation
- Understanding of maximum likelihood estimation
- 为什么更新了 DNS 记录不生效?
- qt-使用自带的应用框架建立--hello world--使用min GW 32bit
- ANSI / NEMA- MW- 1000-2020 磁铁线标准。. 最新原版
- Gnuradio 3.9 using OOT custom module problem record
- Understanding of prior probability, posterior probability and Bayesian formula
- Dataworks duty table
- Voice of users | understanding of gbase 8A database learning
- How to fix the slip ring
猜你喜欢

用户之声 | 对于GBase 8a数据库学习的感悟
MATLAB R2021b 安装libsvm
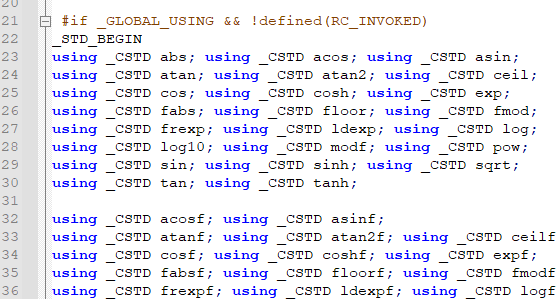
从cmath文件看名字是怎样被添加到命名空间std中的

Voice of users | winter goes and spring comes, waiting for flowers to bloom -- on gbase 8A learning comprehension
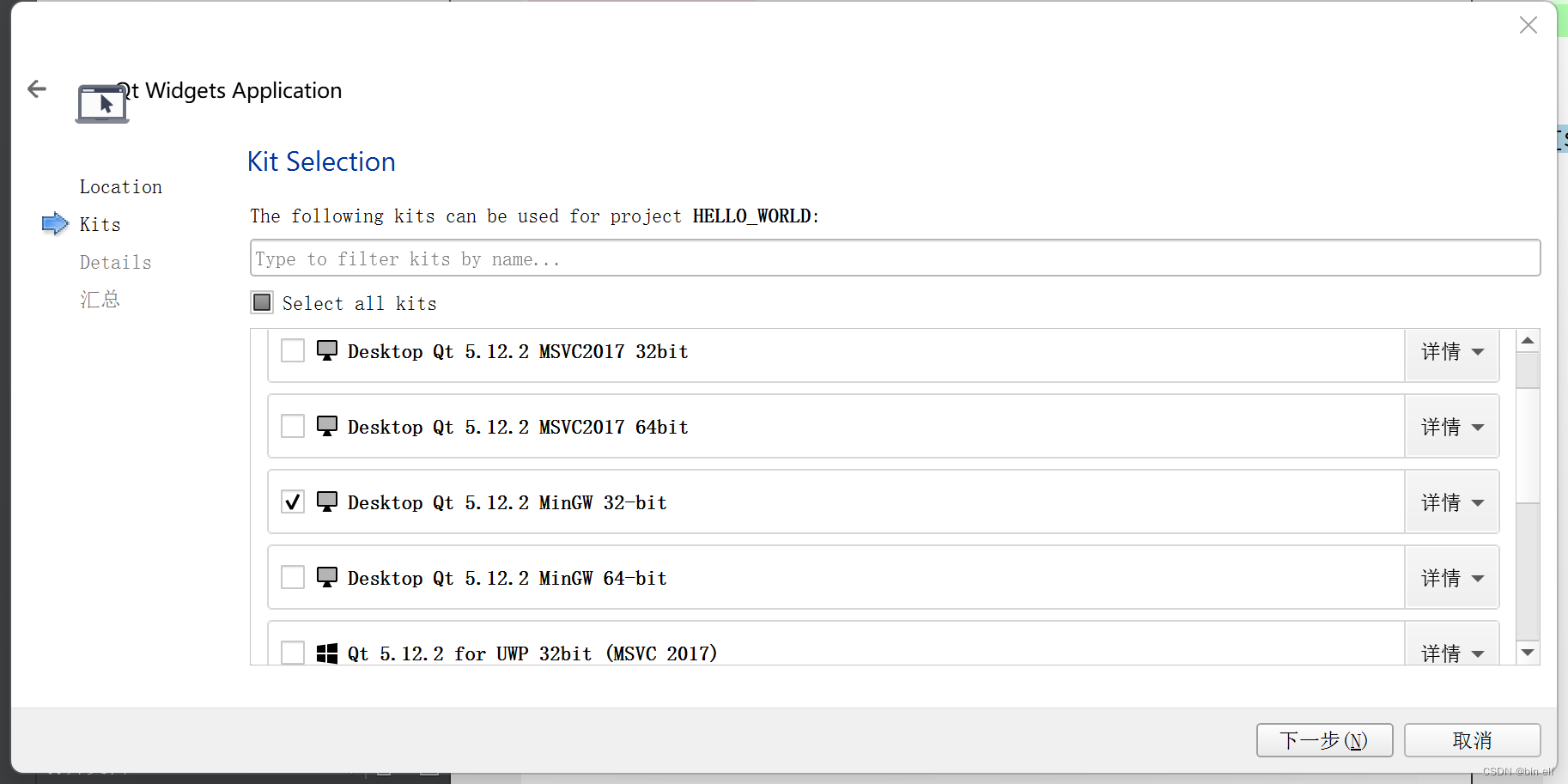
qt-使用自带的应用框架建立--hello world--使用min GW 32bit
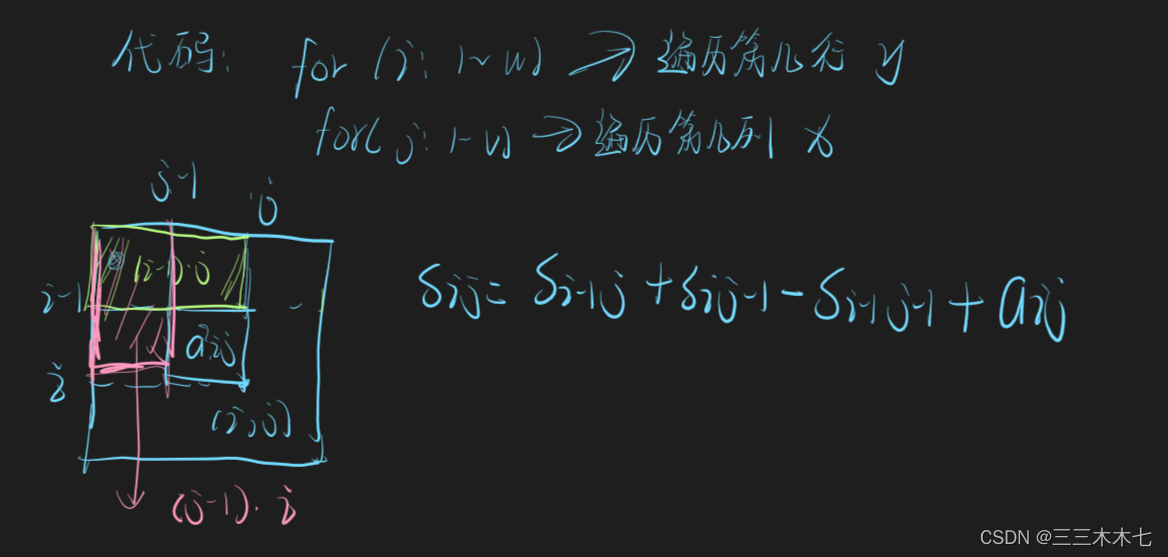
Sum of submatrix

滑环使用如何固定

How to fix the slip ring

保姆级教程:Azkaban执行jar包(带测试样例及结果)
ArrayList源码深度剖析,从最基本的扩容原理,到魔幻的迭代器和fast-fail机制,你想要的这都有!!!
随机推荐
What kind of MES system is a good system
Version 2.0 of tapdata, the open source live data platform, has been released
Plot function drawing of MATLAB
Kindle operation: transfer downloaded books and change book cover
Codeforces Round #633 (Div. 2) B. Sorted Adjacent Differences
QT -- package the program -- don't install qt- you can run it directly
3、多智能体强化学习
Common operations of numpy on two-dimensional array
从cmath文件看名字是怎样被添加到命名空间std中的
用户之声 | 冬去春来,静待花开 ——浅谈GBase 8a学习感悟
Tapdata 的 2.0 版 ,开源的 Live Data Platform 现已发布
Kafka connect synchronizes Kafka data to MySQL
php 获取音频时长等信息
Usage of hydraulic rotary joint
Gnuradio operation error: error thread [thread per block [12]: < block OFDM_ cyclic_ prefixer(8)>]: Buffer too small
LaTeX 中 xcolor 颜色的用法
MySQL查询为什么没走索引?这篇文章带你全面解析
碳刷滑环在发电机中的作用
PHP 计算个人所得税
Optimization of ecological | Lake Warehouse Integration: gbase 8A MPP + xeos