当前位置:网站首页>Competition between public and private chains in data privacy and throughput
Competition between public and private chains in data privacy and throughput
2022-07-06 23:40:00 【BSV blockchain】

* Time of publication :2022 year 2 month 22 Japan
Source of information :bsvblockchain.org

This article will discuss common misconceptions about public and private chains , And compare the public chain with the private chain in terms of data privacy and throughput .
When enterprises and government entities review different blockchain solutions , One of the first questions to consider is whether they should use public chains or “ License type ” Private blockchain .
In general , The entity will validate the certificate 、 Applications such as pilot projects or R & D projects are placed on the public chain . But when they want to create their own pass or data applications involving sensitive data of enterprises or individuals , They will choose a licensed blockchain platform .
At a glance , take “ Private blockchain ” Equivalent to data privacy , take “ Licensed blockchain ” Equivalent to network security , That makes sense .
On the other hand , This assumption also means that the public chain cannot be applied to scenarios involving sensitive data , And the security will be relatively poor .
However , These two assumptions are derived from the blockchain prototype Wrong understanding .
01 Misunderstanding of private chain and public chain
● Data privacy is one of the main considerations leading to the project's choice of private blockchain , Because it is generally believed that the public chain cannot meet the EU GDPR And other regulations .
● Name the private ledger “ Licensed blockchain ”, People assume that the public chain cannot provide flexible permission setting options .
● Because the infrastructure and computing services of the public chain can be used by all public entities , People believe that this kind of network will inevitably be difficult to quickly handle the workload of data applications .
02 Data privacy : Public chain vs Private chain
The mainstream view is that , If you are a bank or enterprise , You may want to implement a licensed blockchain . And the public chain , Because it contains “ Male ” This word , It is understood that it will automatically put the enterprise 、 Government and personal data are exposed in the public domain .
But it's a misunderstanding , And this misunderstanding can be traced back to the era when the function of the public chain has not been truly understood and utilized .
“ alias ” yes BSV Standard functions of blockchain
Although a simple blockchain migration scheme will face privacy problems , But like BSV Blockchain is based on UTXO Blockchain , It's essentially a “ alias ” System . Each bit of data published to the chain is associated with the digital signature of the publisher and the entity interacting with the data . This kind of digital signature sets a line between transaction and identity information A firewall .
In short : The deal is Open Of , But the identity of the user is still Privacy Of .
And by using a one-time alias , Further confuse the relationship between individual or organizational transactions , It can further strengthen the privacy of users .
Briefly : Although an entity uses BSV Blockchain has released millions of data to blockchain , But it is impossible to see the relationship between these data by viewing the public blockchain records , And want to trace the source of all data , It's very heavy ( And expensive ) The task of .
Ensure data integrity without publishing underlying data
BSV Blockchain uses SHA-256 Algorithm , A string of text is converted into a deterministic output called a hash value . Input information cannot be inferred from output information , But if the corresponding hash value is public , Anyone who has input information can verify its authenticity .
When you have a secure hash algorithm , Even the smallest change in input , You will also get a completely different output . for example , Change a letter from uppercase to lowercase , Or just add a period , The results will be different .
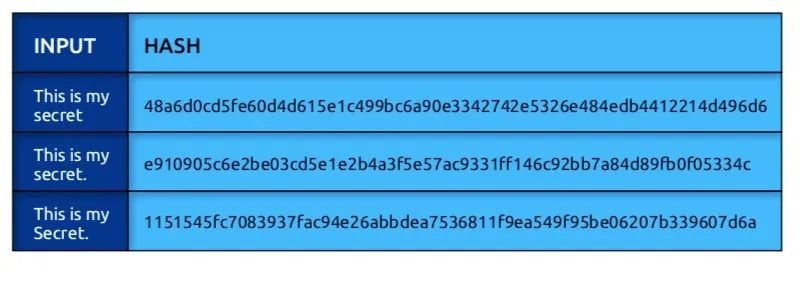
This function creates a “ Digital fingerprinting ”, And by the transaction processor ( Also known as node ) To ensure the integrity of blockchain . Blockchain is just a sequence of blocks ( Or a list of linked blocks ), Contains the data of the previous block header linked by the hash pointer . The block header hash contains the hash output of the previous block and the hash of the data in the current block ( Merkel Gen ).
This powerful format creates an effective blockchain , It can be traced back to the first “ creation ” block . Because these blocks are established one by one through workload proof , Any attempt to overwrite or change these stored data requires attackers to build a new workload proof chain , At the same time, its speed should surpass the honest node . From the perspective of computing power , This is impractical . therefore , Any information stored in a block that has established a certain amount of workload proof is extremely difficult to change .
Any node or user can quickly verify and verify the integrity of the data in the transaction by using only the Merkel certificate of the transaction , To ensure the reliability of hash value .
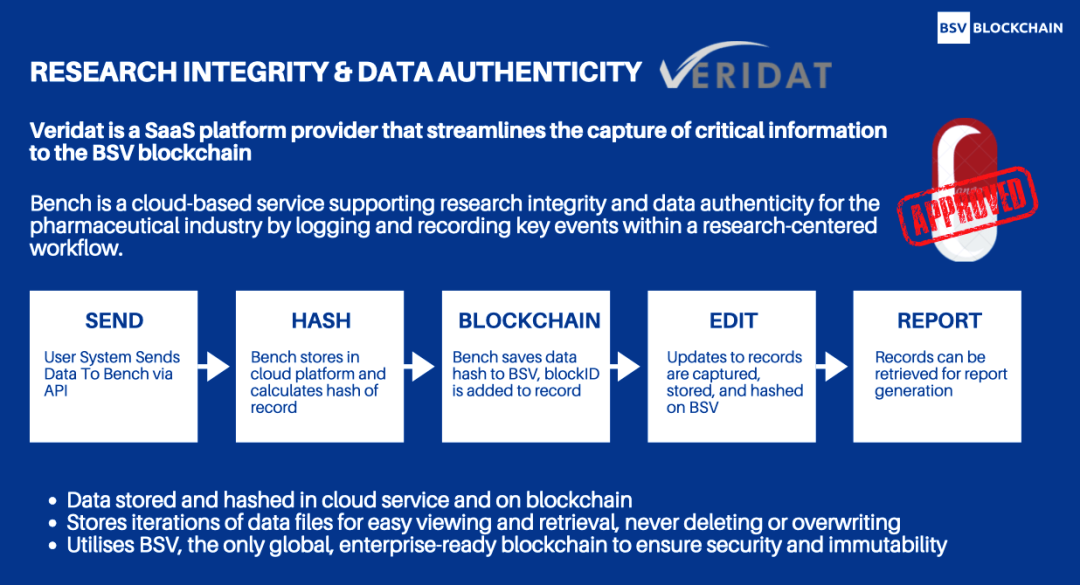
A case study :BSV Medical research data on blockchain
Veridat It's a SaaS( Software as a service ) platform , It can simplify the collection process of key information , And store the information in BSV Block chain .Bench It is a cloud based service launched by them , By recording key events in the research workflow , Provide support for the research integrity and data authenticity of the medical industry .
They do not publish data directly to BSV Block chain , Instead, hash the data , Then chain the hash value . Pharmaceutical companies do not want their data to appear on the public chain . Using hash values can ensure that their data is protected from theft by competitors , At the same time, it can still prove the effectiveness of the workflow .
Encryption technology to strengthen the data privacy of blockchain
except BSV In addition to the built-in data privacy measures of blockchain , Privacy can also be enhanced by using simple encryption techniques such as end-to-end . You can also use zk-SNARK( Concise non iterative knowledge demonstration of zero knowledge ) And other more advanced technologies .
A case study : Medical data on the public chain
To illustrate the public chain —— namely BSV How blockchain is applied to store and process the most sensitive data , Let's consider a practical example involving sensitive data : Medical health data .
On a global scale , Providers of medical and health services ( From doctor 、 Pharmacists go to drugmakers ) At present, they will work with patients 、 The data related to drug trials and drug treatment are stored in a closed data island . These data islands often do not have enough security layers and firewalls . This practice will not only lead to data leakage , It will also restrict medical practitioners from fully understanding the patient's medical history .
National Health Commission (NHC) Subsidiary company 、 Personal health data platform EHR Data Inc, Transferring NHC Of medical data migrated to BSV Blockchain . except BSV Outside the private key system ,EHR The data platform encrypts the data before publishing it to the blockchain , Thus, the privacy of patients is guaranteed while sharing key data .
When asked about their choice of public blockchain and private blockchain ,EHR Data Chief scientist of Ron Austring Use the analogy of Internet and intranet to answer :
“ If you build a website and put it on your company's intranet , You can't get more ( Internet ) Exposure . If you start with a public chain , You immediately know that your service can be used by other entities on the public chain .”
03 throughput : Public chain vs Private chain
Throughput is also a problem that people often talk about , Because most public chains are facing the problem of capacity expansion .
about BSV In terms of blockchain , Scalability Is one of its core foundations , It also has stability 、 Security and immediacy .
BSV It is the only blockchain that can be expanded on a large scale .
BSV The network supports greater data capacity , faster 、 Stronger data processing ability , And a very low handling fee , This enables developers to build countless innovative applications based on this . Multinational enterprises and the entire supply chain will be able to be based on BSV Blockchain protocols and infrastructure to run their own data systems .
BSV Main network TPS Reached 5124Tx/s( Block height 686127), And this number is still growing .
04 The only global blockchain
Imagine such a world : We have a large number of different private blockchains , Each blockchain runs on its own infrastructure and protocols . What is the essential difference between it and the current heap of different federated database schemas ?
and BSV Blockchain provides us with a vision : Through a single global database , Bring interoperability and shared markets to global data , And return control and data ownership to users .
at present , There are more than 400 Projects built on BSV On the blockchain . With rock solid protocol and ultra-high network performance ,BSV Rapid development of ecosystem , We look forward to more unprecedented commercial applications in the future .
- Yes BSV Friends interested in blockchain development can CSDN Private message Contact us , Apply to join BSV Developer community .
- meanwhile , You can also scan the QR code below , Focus on BSV Block chain official WeChat official account , Learn more about blockchain in real time .

边栏推荐
- 云原生(三十二) | Kubernetes篇之平台存储系统介绍
- 【通信】两层无线 Femtocell 网络上行链路中的最优功率分配附matlab代码
- Face recognition class attendance system based on paddlepaddle platform (easydl)
- Please help xampp to do sqlilab is a black
- B 站弹幕 protobuf 协议还原分析
- 若依请求url中带有jsessionid的解决办法
- Restoration analysis of protobuf protocol of bullet screen in station B
- 浅谈现在的弊端与未来的发展
- Station B Big utilise mon monde pour faire un réseau neuronal convolutif, Le Cun Forward! Le foie a explosé pendant 6 mois, et un million de fois.
- 【OFDM通信】基于深度学习的OFDM系统信号检测附matlab代码
猜你喜欢

使用MitmProxy离线缓存360度全景网页
B 站弹幕 protobuf 协议还原分析
借助这个宝藏神器,我成为全栈了
If the request URL contains jsessionid, the solution

Cover fake big empty talk in robot material sorting
电脑重装系统u盘文件被隐藏要怎么找出来

What can be done for traffic safety?
MySQL implementation of field segmentation from one line to multiple lines of example code

若依请求url中带有jsessionid的解决办法
内网穿透zerotier 外网(手机、电脑等)访问内网设备(树莓派、NAS、电脑等)
随机推荐
CRMEB 商城系统如何助力营销?
借助这个宝藏神器,我成为全栈了
快讯 l Huobi Ventures与Genesis公链深入接洽中
不要再说微服务可以解决一切问题了
Coscon'22 community convening order is coming! Open the world, invite all communities to embrace open source and open a new world~
亚朵三顾 IPO
The programmer refused the offer because of low salary, HR became angry and netizens exploded
Face recognition class attendance system based on paddlepaddle platform (easydl)
Gpt-3 is a peer review online when it has been submitted for its own research
Implementation steps of mysql start log in docker
Leetcode problem solving - 889 Construct binary tree according to preorder and postorder traversal
Per capita Swiss number series, Swiss number 4 generation JS reverse analysis
Gold three silver four, don't change jobs
浅谈现在的弊端与未来的发展
Oracle对表进行的常用修改命令
JS import excel & Export Excel
AI金榜题名时,MLPerf榜单的份量究竟有多重?
Can async i/o be implemented by UDF operator and then called by SQL API? At present, it seems that only datastre can be seen
达晨史上最大单笔投资,今天IPO了
What can be done for traffic safety?