当前位置:网站首页>The CTF introduction of PHP file contains
The CTF introduction of PHP file contains
2022-08-02 04:02:00 【SevenCold】
One.php pseudo-protocol execution code
byAs can be seen from the figure, the include function can be triggered only by sending the url variable through the get request. The initial idea was to directly use the file name of the flag, such as flag.php, etc., and then all failed. Then I thought of the file inclusion vulnerability and exploited phpPseudo agreement.
https://blog.csdn.net/yao_xin_de_yuan/article/details/108326427 php pseudoProtocol introduction
There are two methods here:
1.url=data://text/plain, Find directory by wildcardAll files under 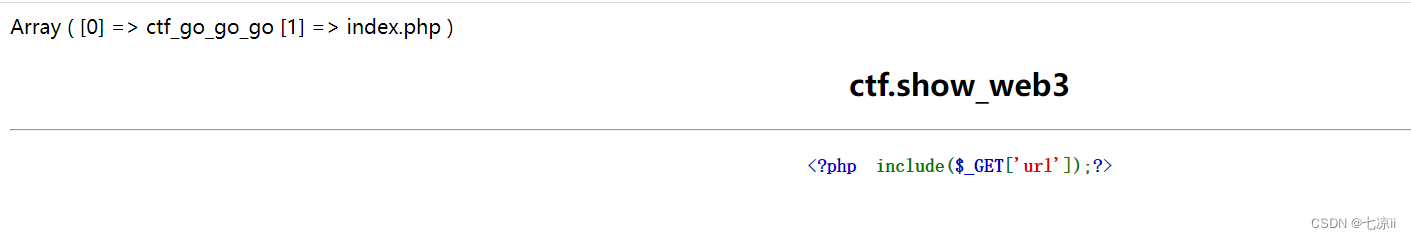
Two files were found, ctf_go_go_goThe file is flag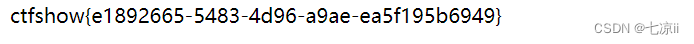
2. Construct url=data:text/plain,")?> Then use a kitchen knife or ant sword to connect.


The connection is successful, just open the relevant file.
2. Log injection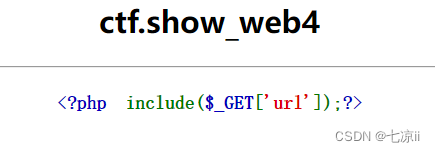
Title and aboveThe same, but using the php pseudo protocol is to find an error, so it should filter php, and then log injection can be performed.The server can ask nginx, so its log directories are /var/log/nginx/access.log and /var/log/nginx/error.log
Therefore construct url=/var/log/nginx/access.log
It is found that the log will record the request method and user-agent. Because the request method cannot be changed, we can insert the php code at the user-agent, and use bp to change the user-agent field to After sending, it is found that the ua in the log file is empty, this is because the php code will run directly and will not be displayed.Then we can use a kitchen knife or ant sword to connect, but pay attention to the url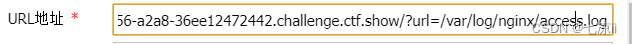
After entering, just flip through to find the flag.
3.php pseudo-protocol read file
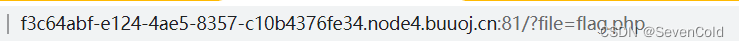
The title url is as shown, because there is no clearPrompt, so you can use the php pseudo-protocol to read the content of the file and take a look
Construct url: ?file=php://filter/read=convert.base64-encode/resource=flag.php
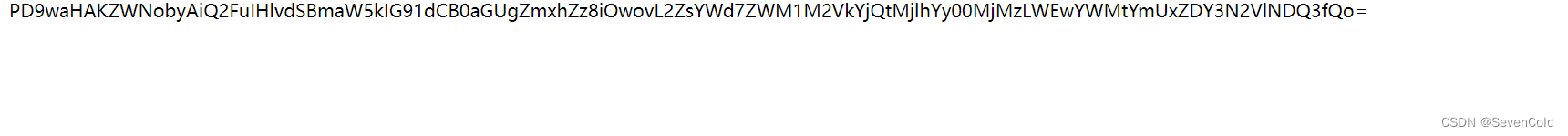
You can see that the file content is encoded by base64, we decode itClick to get the flag
边栏推荐
- 16. JS events, string and operator
- 利用cookie获取admin权限 CTF基础题
- (8) requests、os、sys、re、_thread
- 13.JS输出内容和语法
- SQL classification, DQL (Data Query Language), and corresponding SQL query statement demonstration
- (1) the print () function, escape character, binary and character encoding, variables, data type, the input () function, operator
- Add a full image watermark to an image in PHP
- Solve the problem of Zlibrary stuck/can't find the domain name/reached the limit, the latest address of Zlibrary
- Pycharm打包项目为exe文件
- hackmyvm: again walkthrough
猜你喜欢
随机推荐
web安全之目录遍历
After the mailbox of the Pagoda Post Office is successfully set up, it can be sent but not received.
TypeScript error error TS2469, error TS2731 solution
Cookie is used to collect the admin privileges CTF foundation problem
一次代码审计的笔记(CVE-2018-12613 phpmyadmin文件包含漏洞)
(8) requests、os、sys、re、_thread
web渗透必玩的靶场——DVWA靶场 1(centos8.2+phpstudy安装环境)
Eric target penetration test complete tutorial
hackmyvm: kitty walkthrough
What are the PHP framework?
16. JS events, string and operator
Masashi: 1 vulnhub walkthrough
13.JS输出内容和语法
(1)Thinkphp6入门、安装视图、模板渲染、变量赋值
PHP Foundation March Press Announcement Released
(4) Function, Bug, Class and Object, Encapsulation, Inheritance, Polymorphism, Copy
(3) 字符串
About the apache .htaccess file of tp
Scrapy crawler encounters redirection 301/302 problem solution
14. JS Statements and Comments, Variables and Data Types