当前位置:网站首页>The solution of permission denied
The solution of permission denied
2022-07-04 12:23:00 【Programmer straw hat】
When debugging the startup file , The following error occurred :
Permission deniedThe reason is that the permission of the file is not enough , The measured solutions are as follows :
// Be careful :777 Use permissions with caution For high permissions
$ sudo chmod -R xxx A directory
// Define your own xxx, Here's a description among
-R Refers to cascading all subdirectories and files applied to the directory
750 Indicates that the file owner has read 、 Write 、 Executive authority , File group has read 、 Executive authority , Other users don't have permission
Belong to :rwx=4+2+1=7.
Generic group :r-x=4+0+1=5.
other :---=0+0+0=0
write in 、 Read and execute permissions have the following numerical values :
r ( read ) = 4
w ( Write ) = 2
x ( Executable ) = 1
No authority = 0
The permission number of a specific user class is the sum of the permission values of that class .
Solve the problem after operation ,OK!
边栏推荐
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 19
- Ternsort model integration summary
- Local MySQL forgot the password modification method (Windows)
- How to judge the advantages and disadvantages of low code products in the market?
- OSI model notes
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 10
- Experiment 7. IPv6
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 9
- Definition and method of string
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 11
猜你喜欢

Hongke case study on storm impact in coastal areas of North Carolina using lidar
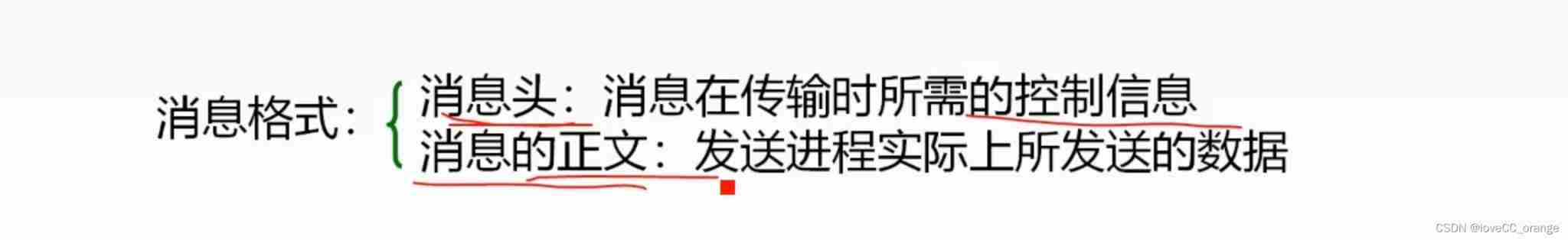
Process communication and thread explanation
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 20](/img/d5/4bce239b522696b5312b1346336b5f.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 20
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 23](/img/72/a80ee7ee7b967b0afa6018070d03c9.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 23
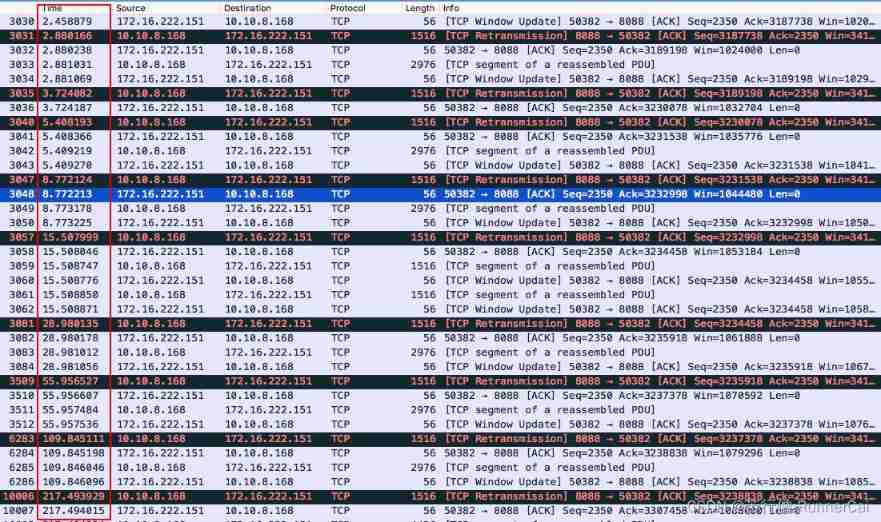
TCP fast retransmission sack mechanism

2020 Summary - Magic year, magic me

Decrypt the advantages of low code and unlock efficient application development
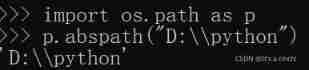
os. Path built-in module
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 12](/img/b1/926d9b3d7ce9c5104f3e81974eef07.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 12
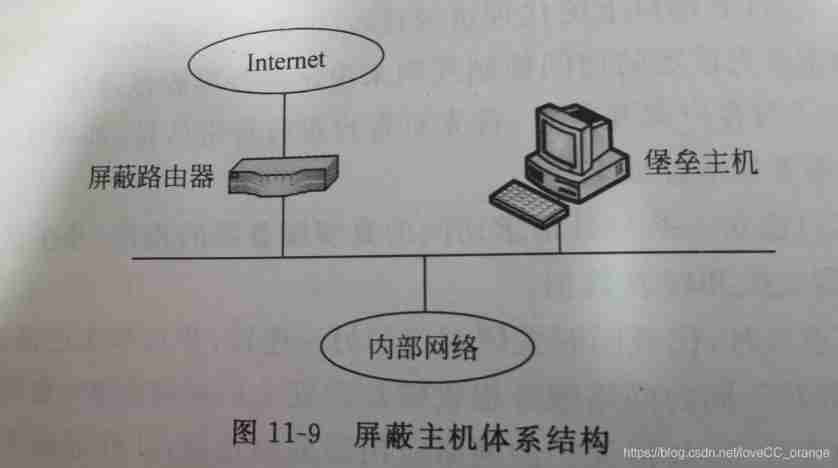
Summary of Shanghai Jiaotong University postgraduate entrance examination module firewall technology
随机推荐
IPv6 experiment
The most robust financial products in 2022
Four sorts: bubble, select, insert, count
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 17
Reptile learning winter vacation series (2)
Data communication and network: ch13 Ethernet
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 23
[Android reverse] function interception instance (③ refresh CPU cache | ④ process interception function | ⑤ return specific results)
French Data Protection Agency: using Google Analytics or violating gdpr
Anti clockwise rotation method of event arrangement -- PHP implementation
Install freeradius3 in the latest version of openwrt
[directory] search
TCP slicing and PSH understanding
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 18
World document to picture
Configure SSH key to realize login free
Summary of Shanghai Jiaotong University postgraduate entrance examination module firewall technology
Translation D29 (with AC code POJ 27:mode of sequence)
LVS load balancing cluster deployment - Dr direct routing mode
The latest idea activation cracking tutorial, idea permanent activation code, the strongest in history