当前位置:网站首页>Advantages and disadvantages of evaluation methods
Advantages and disadvantages of evaluation methods
2022-07-06 10:25:00 【How about a song without trace】
1、 Over fitting : When the learner learns the training samples well , It is possible to take the characteristics of the trained samples as the general properties of all potential samples , This will lead to the decline of Pan China capability ( Generalization ability refers to the ability of the learning model to be applied to unknown samples ).
2、 Under fitting : Low learning ability , I think the general characteristics are all characteristics .
Evaluation methods :
- Set aside method : If the training set contains the vast majority of samples , Then the trained sample may be close to the desired training model , But because of the small test set , The assessment results may not be accurate enough , The pattern of basic partitioned data sets :2:1,4:1 The front is used for training , The latter is used for testing .
- Cross validation : Equal division , Stratified sampling , Take the mean , The defect is : Large data sets are too expensive , Spend more time .
- Self help law : Loop from the overall data into the sample , Put it back again , The final initial data are 0.368 The sample of does not appear , Used for testing . The self-help method can be used to test from the samples that appear in the initial data set , Such a test is also known as out of package estimation . advantage : The self-help method is smaller in the data set , It's hard to divide training effectively \ Test sets are useful , Multiple different training sets can be generated from the initial data set , shortcoming : But it changes the distribution of data sets , This will introduce Estimated deviation .
But when the initial data volume is enough , Set aside method and cross validation method are more commonly used .
Participate in the final parameter model :
General rules of parameter adjustment : Select a range and a varying step size for each parameter , This is a compromise between computational overhead and performance .
Performance metrics : Measure the pan China capability of the model , Performance depends not only on Algorithms and data , It also determines mission requirements .
The most commonly used performance measure for regression tasks : Mean square error .
Recall rate (TP/(TP+FN))、 Precision rate (TP/(TP+FP)):TP Real examples FP False positive example TN True counter example FN False counter example .
F1 It is based on the harmonic average of recall and precision :2*TP/( Total number of samples +TP-TN)
ROC: Characteristics of test work . The horizontal axis TPR( Real examples )=TP/(TP+FN), The vertical axis FPR( False positive example ):FP/(TN+FP).
Normalization : Map values from different ranges of variation to the same fixed range , Common is [0,1], Also known as normalization .
deviation : The difference between the expected output and the real tag , Describe the fitting ability of the learning algorithm itself .
Generalization error can be decomposed into deviation 、 variance ( Have you measured the change of learning performance caused by the change of the same size training set , The impact of data perturbation is characterized )、 And noise ( The lower bound of the expected generalization error that any learning algorithm can achieve in the current task is expressed ) The sum of the .
边栏推荐
- Typescript入门教程(B站黑马程序员)
- 该不会还有人不懂用C语言写扫雷游戏吧
- In fact, the implementation of current limiting is not complicated
- ZABBIX introduction and installation
- MySQL实战优化高手06 生产经验:互联网公司的生产环境数据库是如何进行性能测试的?
- MySQL learning diary (II)
- vscode 常用的指令
- How to make shell script executable
- 16 medical registration system_ [order by appointment]
- Sichuan cloud education and double teacher model
猜你喜欢
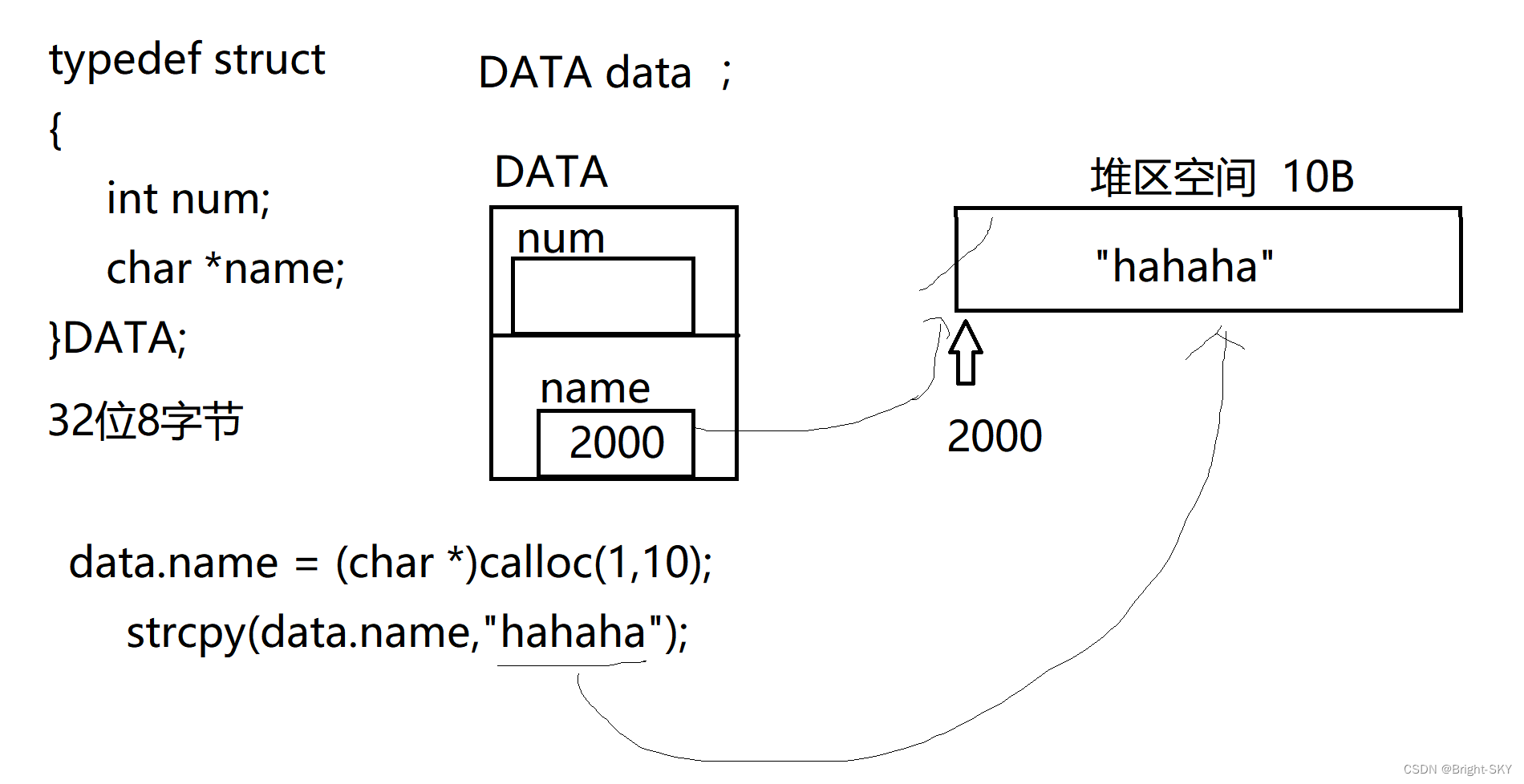
C miscellaneous shallow copy and deep copy
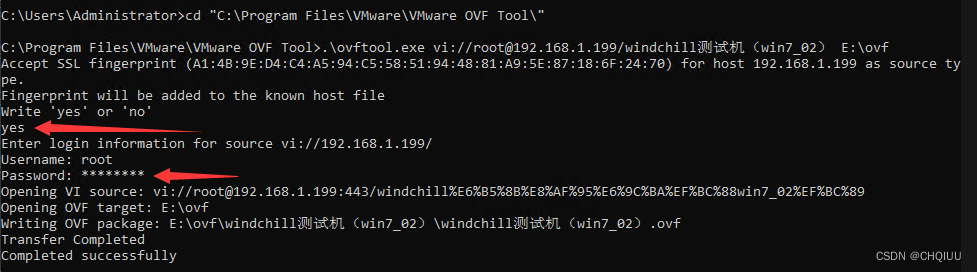
使用OVF Tool工具从Esxi 6.7中导出虚拟机
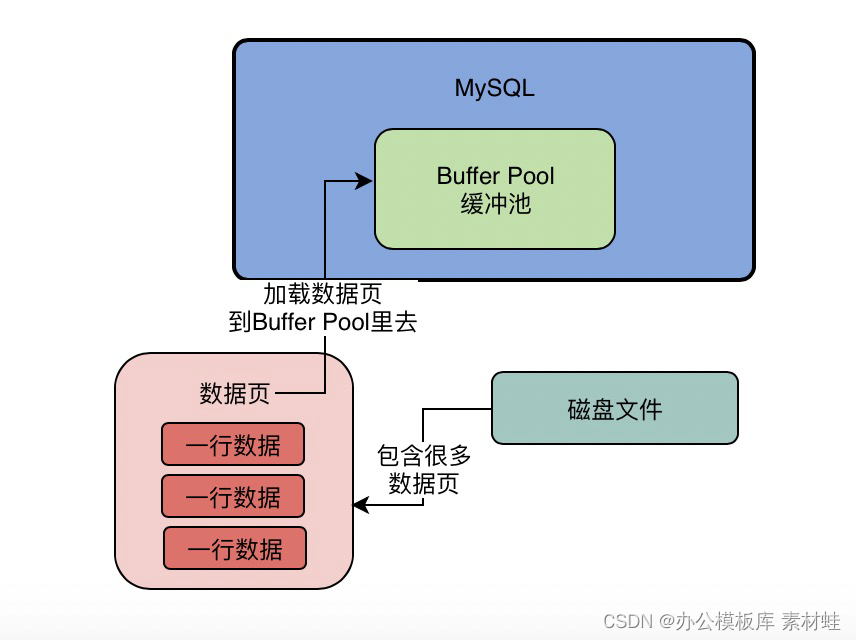
MySQL combat optimization expert 12 what does the memory data structure buffer pool look like?
基于Pytorch肺部感染识别案例(采用ResNet网络结构)
What is the current situation of the game industry in the Internet world?
Const decorated member function problem
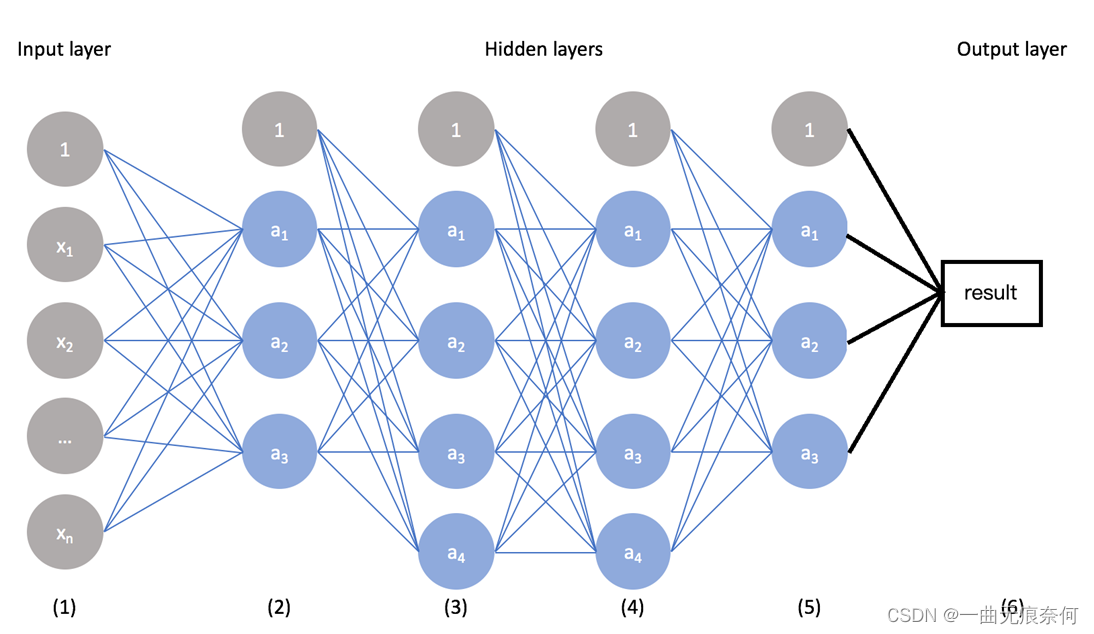
Pytorch LSTM实现流程(可视化版本)
Not registered via @enableconfigurationproperties, marked (@configurationproperties use)
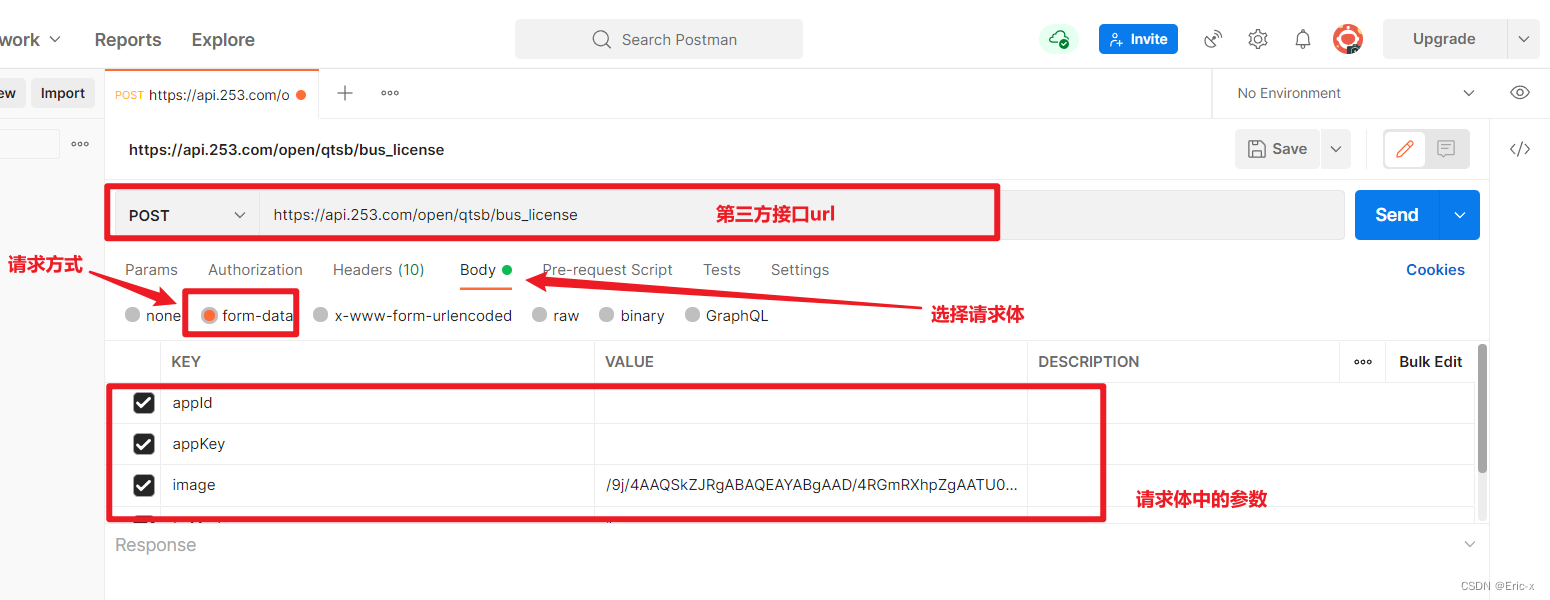
Implement sending post request with form data parameter
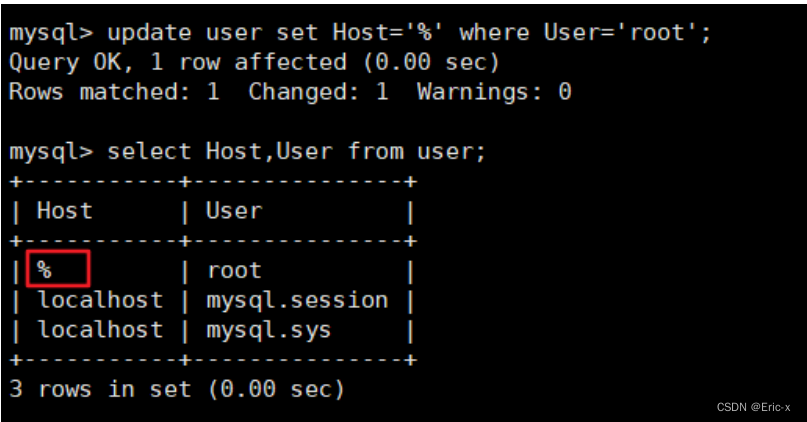
解决在window中远程连接Linux下的MySQL
随机推荐
安装OpenCV时遇到的几种错误
How to make shell script executable
MySQL real battle optimization expert 11 starts with the addition, deletion and modification of data. Review the status of buffer pool in the database
Solve the problem of remote connection to MySQL under Linux in Windows
【C语言】深度剖析数据存储的底层原理
Super detailed steps for pushing wechat official account H5 messages
评估方法的优缺点
17 医疗挂号系统_【微信支付】
The governor of New Jersey signed seven bills to improve gun safety
MySQL實戰優化高手08 生產經驗:在數據庫的壓測過程中,如何360度無死角觀察機器性能?
Zsh configuration file
Upload vulnerability
MySQL ERROR 1040: Too many connections
Jar runs with error no main manifest attribute
① BOKE
[after reading the series of must know] one of how to realize app automation without programming (preparation)
14 医疗挂号系统_【阿里云OSS、用户认证与就诊人】
15 medical registration system_ [appointment registration]
Contest3145 - the 37th game of 2021 freshman individual training match_ C: Tour guide
Good blog good material record link