当前位置:网站首页>Network security - Novice introduction
Network security - Novice introduction
2022-07-05 13:43:00 【Sex sex ~ ~】
MISC
1、 Simple steganography
2、 Looking for your sister
CRYPTO
1、 Four Caesars or four fences
2、 Beautiful notes
3、 Little rabbit
WEB
1、 Sign in
2、EZphp
1、 Simple steganography
 Open the topic prompt , Follow the instructions , Search for CTF Steganography routine Search for
Open the topic prompt , Follow the instructions , Search for CTF Steganography routine Search for 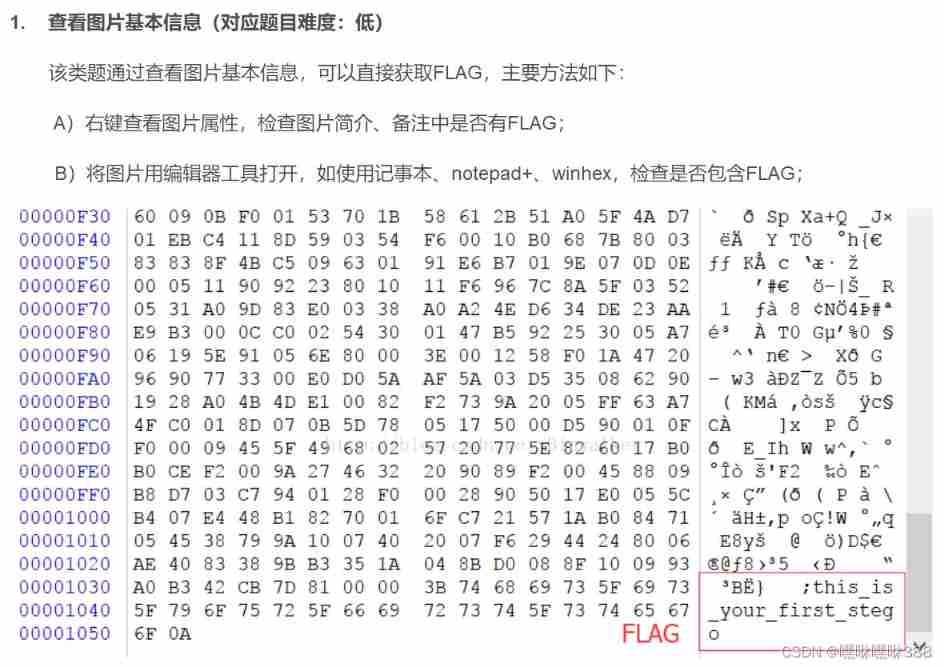
Check the picture information according to our search results and find that there is no relevant flag Information about . Open according to the second method 010Editor.exe Software Ctrl+F Search for
![]()
The result appears .
SLsec{e2e0061f251355de79777499528d6d75}
2、 Looking for your sister

Download the file on the topic , Because the file is zip Format , So rename the file and open the compressed package 
After opening the compressed package, there are two files

After the first one opens

good heavens , This is the declassification of the type of socialist core values .
![]()
After decryption, he told me this flag It's not true , So I opened the second compressed package ,
When looking at the properties, I didn't find What useful information , Drag it into 010Editor.exe Search for flag

flag{you_are_lucky_d0g}
CRYPTO
1、 Four Caesars or four fences
According to the title prompt, first decrypt the characters by Caesar , The title says four , Then the number may be 4
![]()
Then the decrypted characters will be decrypted , The number is still chosen 4,

flag:slsec{55fb656d28c55e09ecc45424f952370f}
2、 Beautiful notes
 Open file
Open file

Because they are all decryption type topics , Search for notes and decrypt , Decrypt the characters in the file to get a string of characters
![]()
Characters consist of the case of letters and numbers base64 The encryption type of , And then decrypt it
SLsec{D0FA06CD93335C8CAE357FFE5CD1C4E9}
3、 Little rabbit
The title says little rabbit , So we went to search rabbit Decrypt Open file 

Decryption requires a key. Today is a good day , Fill in the date of the day when you do the question , Decrypt .
SLsec{f330ad0d5bba3bab338d99a7b2ba81ca}
WEB
1、 Sign in
 Click the title link
Click the title link

F12 Key to view the source code

SLsec{We1c0me__T0_SLsec_Recru1t new [email protected]}
2、EZphp
 Open the title link
Open the title link 
Look at the code , first if It means if a If it is a number, it stops running , the second if Means to a=8848, stay php In the weak type of ,php Will compare the number before the character with the number after the character , So you should not only input a=8848 Also enter one or more characters after
![]()
SLsec{[email protected]@ge}
边栏推荐
- What about data leakage? " Watson k'7 moves to eliminate security threats
- 研究生可以不用学英语?只要考研英语或六级分数高!
- Shandong University Summer Training - 20220620
- FPGA 学习笔记:Vivado 2019.1 添加 IP MicroBlaze
- 那些考研后才知道的事
- 通讯录(链表实现)
- Clock cycle
- JS to determine whether an element exists in the array (four methods)
- Jasypt configuration file encryption | quick start | actual combat
- PHP generate Poster
猜你喜欢
FPGA learning notes: vivado 2019.1 add IP MicroBlaze

【华南理工大学】考研初试复试资料分享
龙芯派2代烧写PMON和重装系统
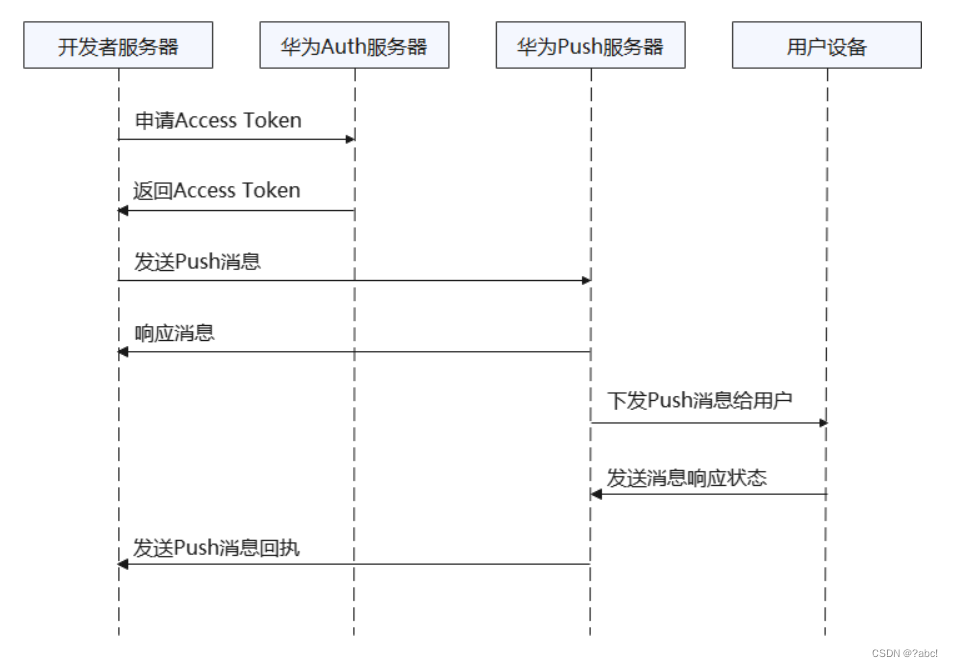
Huawei push service content, read notes

华为推送服务内容,阅读笔记
![[deep learning paper notes] hnf-netv2 for segmentation of brain tumors using multimodal MR imaging](/img/52/5e85743b1817de96a52e02b92fd08c.png)
[deep learning paper notes] hnf-netv2 for segmentation of brain tumors using multimodal MR imaging
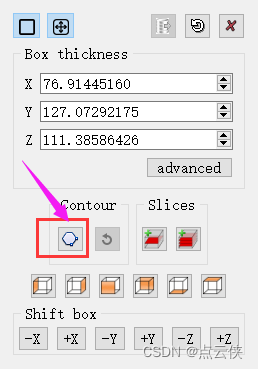
Cloudcompare - point cloud slice
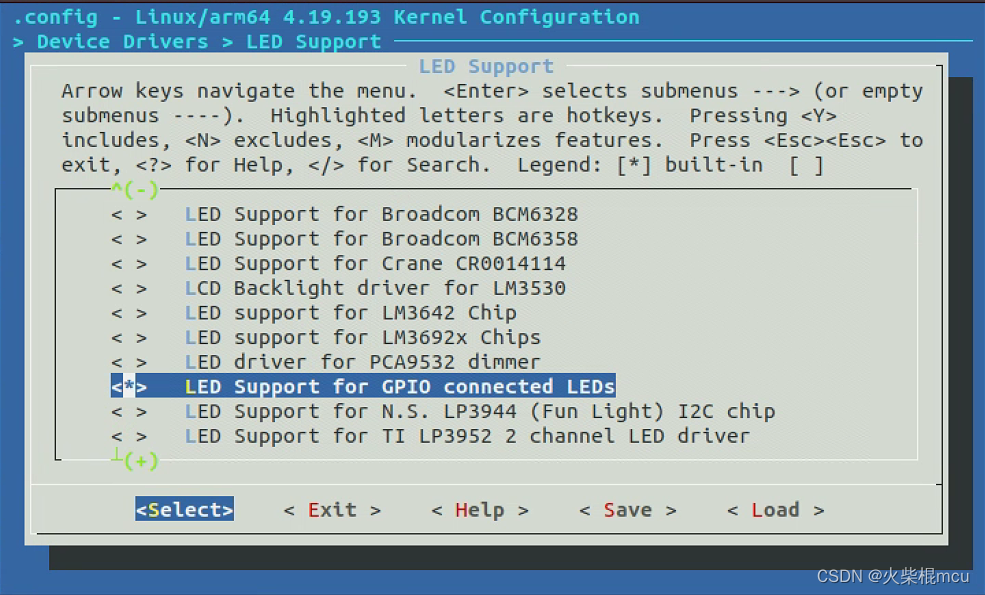
RK3566添加LED
Talk about seven ways to realize asynchronous programming

Wonderful express | Tencent cloud database June issue
随机推荐
Nantong online communication group
Shandong University Summer Training - 20220620
Jetpack Compose入门到精通
Idea remote debugging agent
Backup and restore of Android local SQLite database
[深度学习论文笔记]TransBTSV2: Wider Instead of Deeper Transformer for Medical Image Segmentation
Record in-depth learning - some bug handling
49. Grouping of alphabetic ectopic words: give you a string array, please combine the alphabetic ectopic words together. You can return a list of results in any order. An alphabetic ectopic word is a
jasypt配置文件加密|快速入门|实战
kafaka 日志收集
go map
Kotlin协程利用CoroutineContext实现网络请求失败后重试逻辑
[daily question] 1200 Minimum absolute difference
Can and can FD
Cloudcompare - point cloud slice
Could not set property 'ID' of 'class xx' with value 'XX' argument type mismatch solution
Idea set method annotation and class annotation
Could not set property ‘id‘ of ‘class XX‘ with value ‘XX‘ argument type mismatch 解决办法
zabbix 监控
Address book (linked list implementation)