当前位置:网站首页>Zhongke Panyun - data analysis and forensics packet flag
Zhongke Panyun - data analysis and forensics packet flag
2022-07-04 04:59:00 【Beluga】
Data analysis and forensics
Need to be private
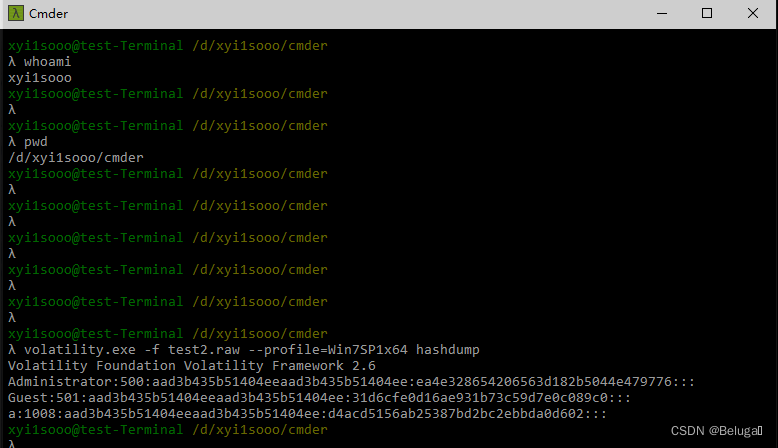
1. Use Wireshark View and analyze virtual machines windows 7 Under the desktop attack.pcapng Package file , through Analyzed packets attack.pcapng Find the hacker's IP Address , And put the hacker's IP Address as FLAG( form :[IP Address ]) Submit :
tcp.connection.syn
By analyzing the port , Because hackers scan common ports
Flag:[172.16.1.102]
2. Continue to view the package file attack.pacapng, Analyze which ports the hacker scanned , And make all ports by FLAG( form :[ Port name 1, Port name 2, Port name 3…, Port name n]) From low to high :
tcp.connection.syn and ip.src==172.16.1.102
Flag:[21,23,80,445,3389,5007]
3. Continue to view the package file attack.pacapng Analyze what the hacker finally gets the user name , And users Name as FLAG( form :[ user name ]) Submit :
http.request.method==POST
Flag:[Lancelot]
4. Continue to view the package file attack.pacapng Analyze what the hacker finally got the password , And make the password by FLAG( form :[ password ]) Submit :
http.request.method==POST
flag:[12369874]
5. Continue to view the package file attack.pacapng Analyze what the password of the hacker connecting the Trojan horse is , And will In a word, the password is used as FLAG( form :[ In a word, the password ]) Submit :
Ctrl+f
Flag:[alpha]
6. Continue to view the package file attack.pacapng Analyze what files the hacker downloaded , And put the file name and suffix As FLAG( form :[ file name . Suffix name ]) Submit :
http.request.method==POST
flag:[flag.zip]
7. Continue to view the package file attack.pacapng Extract the files downloaded by hackers , And the contents in the document are FLAG( form :[ The contents of the document ]) Submit :
binwalk -eM attack.pcapng
flag:[ flag{Manners maketh man}]
边栏推荐
- 【MATLAB】MATLAB 仿真模拟调制系统 — SSB 系统
- Flutter 调用高德地图APP实现位置搜索、路线规划、逆地理编码
- C basic (VII) document operation
- Several smart watch related chips Bluetooth chip low power consumption
- Flutter ‘/usr/lib/libswiftCore.dylib‘ (no such file)
- 附件三:防守方评分标准.docx
- 中科磐云—2022广东木马信息获取解析
- 《Cross-view Transformers for real-time Map-view Semantic Segmentation》论文笔记
- 【无标题】
- 【MATLAB】MATLAB 仿真数字基带传输系统 — 双极性基带信号(第 I 类部分响应波形)的眼图
猜你喜欢
Secondary vocational group network security - memory Forensics

Download kicad on Alibaba cloud image station
关闭的数据能用dbca删除吗? 能
6-5 vulnerability exploitation SSH weak password cracking and utilization

Beipiao programmer, 20K monthly salary, 15W a year, normal?

Unity中RampTex介绍和应用: 溶解特效优化
GUI application: socket network chat room
附件五:攻击过程简报.docx

RAC delete damaged disk group

Unity 接入天气系统
随机推荐
网络设备应急响应指南
Flutter 调用高德地图APP实现位置搜索、路线规划、逆地理编码
【MATLAB】MATLAB 仿真数字带通传输系统 — QPSK 和 OQPSK 系统
【MATLAB】通信信号调制通用函数 — 傅里叶变换
拼夕夕二面:说说布隆过滤器与布谷鸟过滤器?应用场景?我懵了。。
Kivy tutorial 07 component and attribute binding implementation button button click to modify the label component (tutorial includes source code)
【MATLAB】MATLAB 仿真数字基带传输系统 — 数字基带传输系统
令人头痛的延时双删
Introduction and application of rampax in unity: optimization of dissolution effect
Utiliser des unités de mesure dans votre code pour une vie meilleure
Sample template of software design document - learning / practice
【MATLAB】通信信号调制通用函数 — 低通滤波器
我们认为消费互联网发展到最后,依然会局限于互联网行业本身
红队视角下的防御体系突破之第二篇案例分析
Binary search tree
[wechat applet] good looking carousel map component
First knowledge of batch processing
Fault analysis | mongodb 5.0 reports an error, and the legal instruction solves it
MySQL JDBC programming
CRS-4013: This command is not supported in a single-node configuration.