当前位置:网站首页>Simple use of Xray
Simple use of Xray
2022-07-07 08:52:00 【Colorful @ star】
xray Simple use
summary
Xray Is a powerful security assessment tool , Support Take the initiative 、 passive Multi scan mode , Support common web Loopholes automated testing , Flexible definition of POC, Rich in functions , Easy to call , Support multiple operating systems
characteristic
- Fast detection speed
- Support a wide range of
- High quality can be customized
- There is no threat to safety
- Fast update speed
Supported vulnerability detection types
- XSS Vulnerability detection (key: xss)
- SQL Injection detection (key: sqldet)
- command / Code injection detection (key: cmd-injection)
- Directory enumeration (key: dirscan)
- Path crossing detection (key: path-traversal)
- XML Solid injection detection (key: xxe)
- File upload detection (key: upload)
- Weak password detection (key: brute-force)
- jsonp testing (key: jsonp)
- ssrf testing (key: ssrf)
- Baseline check (key: baseline)
- Arbitrary jump detection (key: redirect)
- CRLF Inject (key: crlf-injection)
- Struts2 Serial vulnerability detection ( premium ,key: struts)
- Thinkphp Serial vulnerability detection ( premium ,key: thinkphp)
- POC frame (key: phantasm)
among POC The frame is built-in by default Github On the contribution of poc, Users can also build on demand poc And run
Download and install
Download address
GitHub Address :https://github.com/chaitin/xray/releases
Document address :https://docs.xray.cool/
Support installation and download of various operating systems 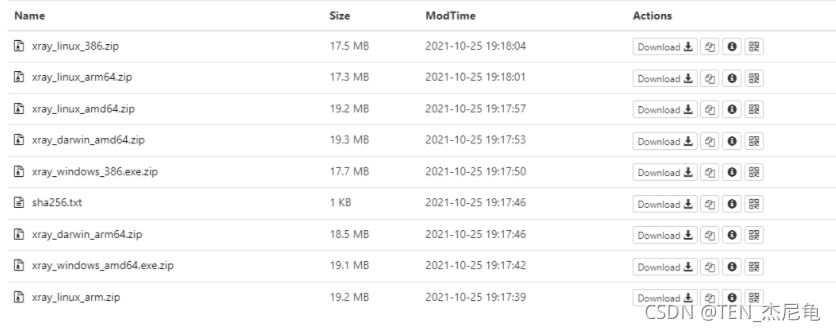
install
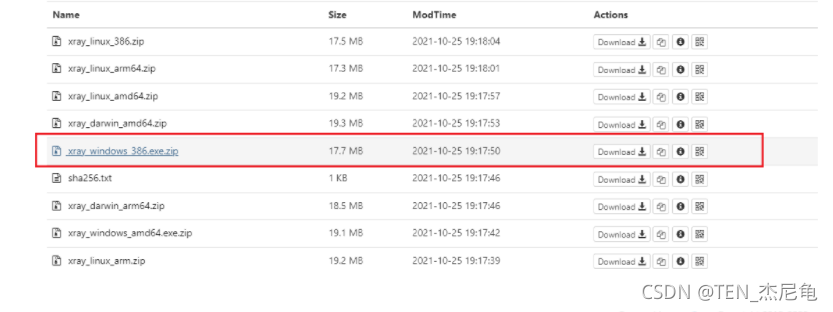
1、 Because the blogger is Windows64 Bit operating system , So choose 64 Bit installation file
2、 unpack , Just one exe file
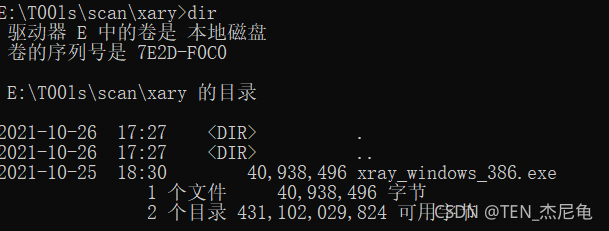
3、 Use cmd The command line navigates to the current xray.exe Path
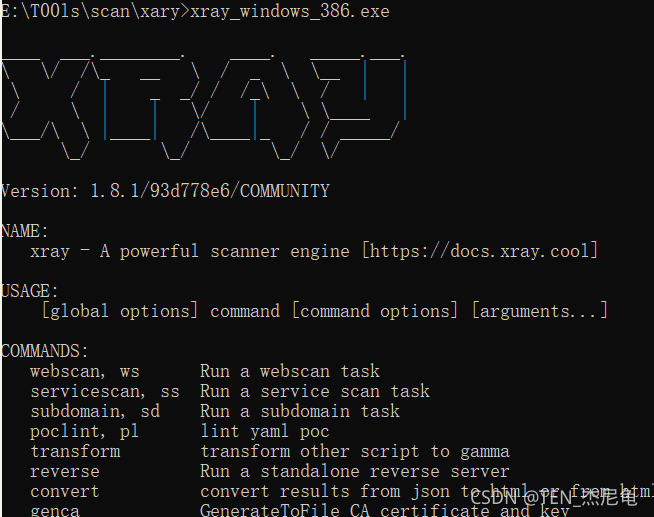
Run the file
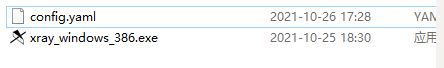
meanwhile xray_windows_386.exe Under the same directory of the file config.yaml The configuration file
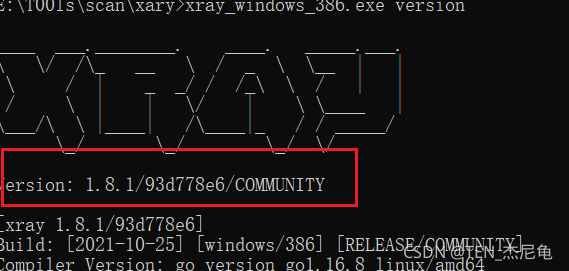
see xray Version number of version
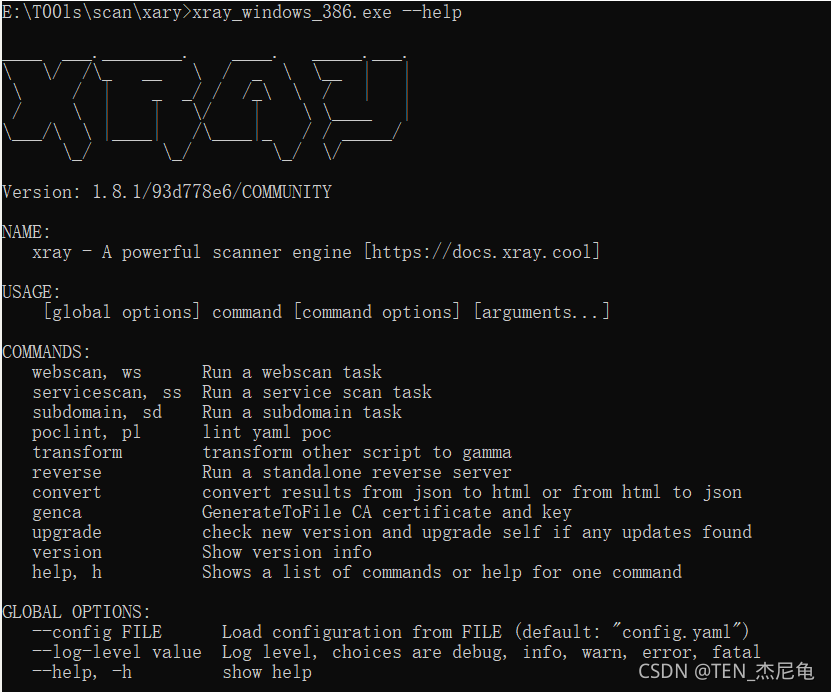
see Help document --help
Configuration is introduced
Xray In the catalog config.yaml The file contains all the configuration information , Configuration mainly includes five categories :http、plugins、 reverse、mitm、basic_crawle
Set the domain name that allows scanning
hostname_allowed: Is the domain name that allows scanning ,hostname_disallowed: Is a domain name that is not allowed to be scanned , You can use asterisks ( Express all ) matching
Scan plug-in configuration
The plug-in configuration modification is mainly on and off , The default is all on , Detect all types of vulnerabilities during scanning , The type of vulnerability that does not need to be detected is modified to false; You can also specify plug-ins during scanning , Such as :–plugins xss,xxe,cmd_injection
Contracting rate limit
Prevent requests from being too quickly waf Intercept , You can reduce the number of requests per second , Default per second 500
Scan agent configuration
Setting up a proxy can work with burp suite And other software
The proxy pattern
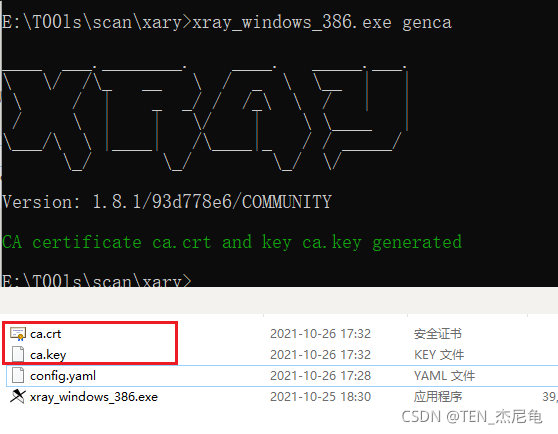
1、 Generate ca certificate
xray_windows_386.exe genca
- 1
2、 Import to browser ca certificate
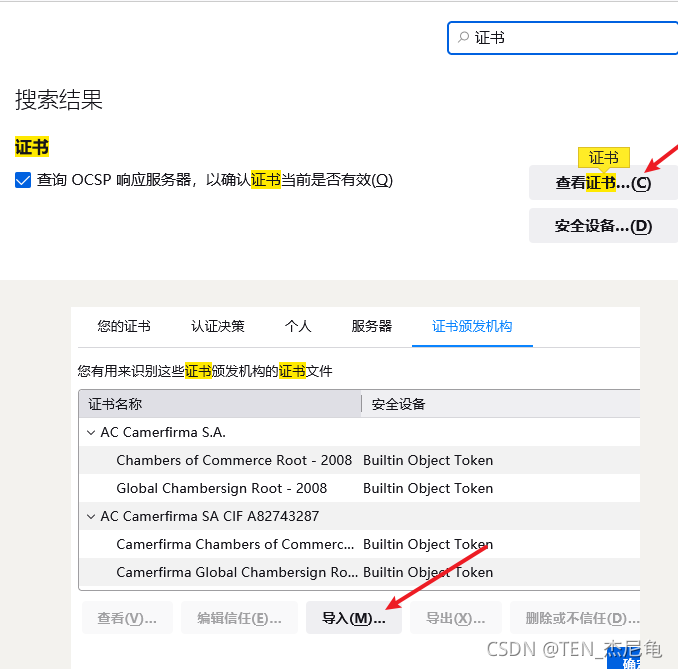
choice ca The path of the certificate
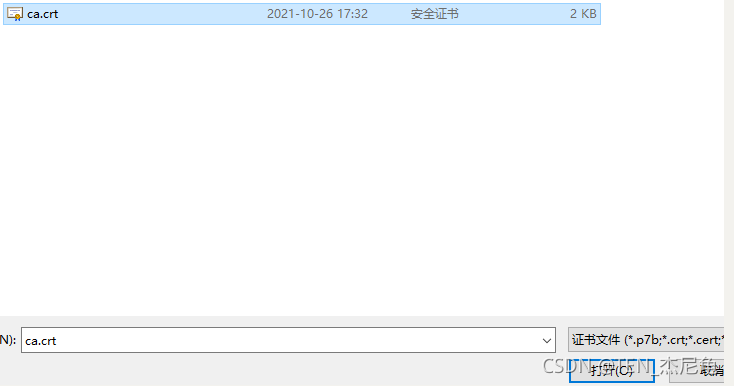
Certificate of trust
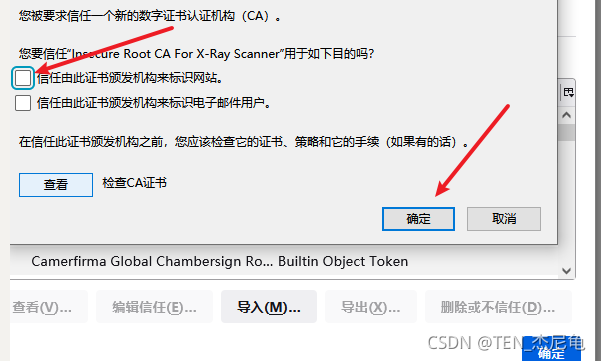
end
3、 Set up proxy for browser
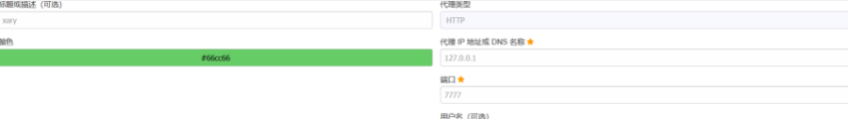
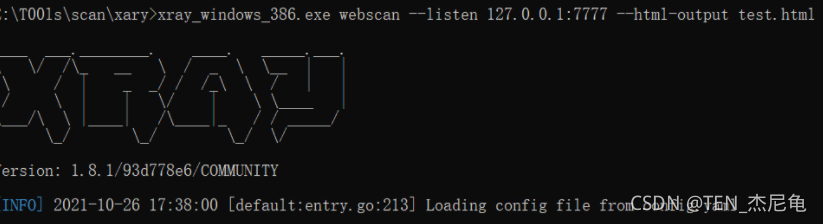
4、 function xray, monitor
xray_windows_386.exe webscan --listen 127.0.0.1:7777 --html-output test.html
webscan web Page vulnerability detection
–listen monitor
–html-output Output html Format
- 1
- 2
- 3
- 4
- 5
visit dvwa Of sql Injection module
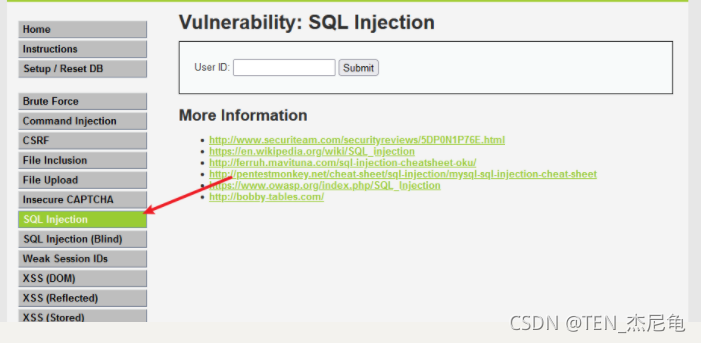
xray change
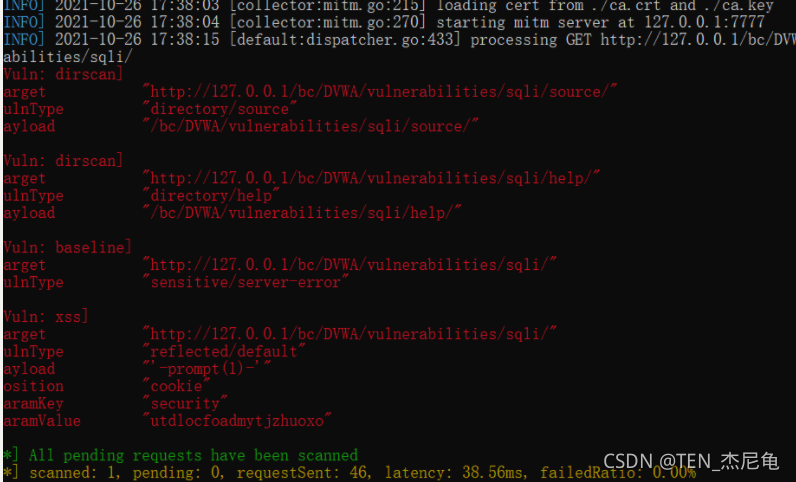
end CTRL+c
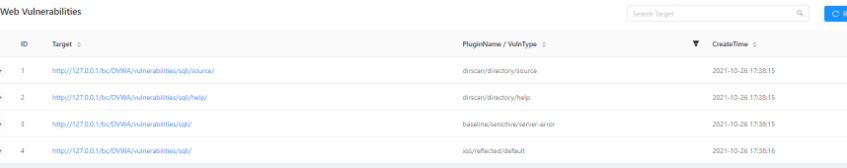
3、 open test.html, View generated reports
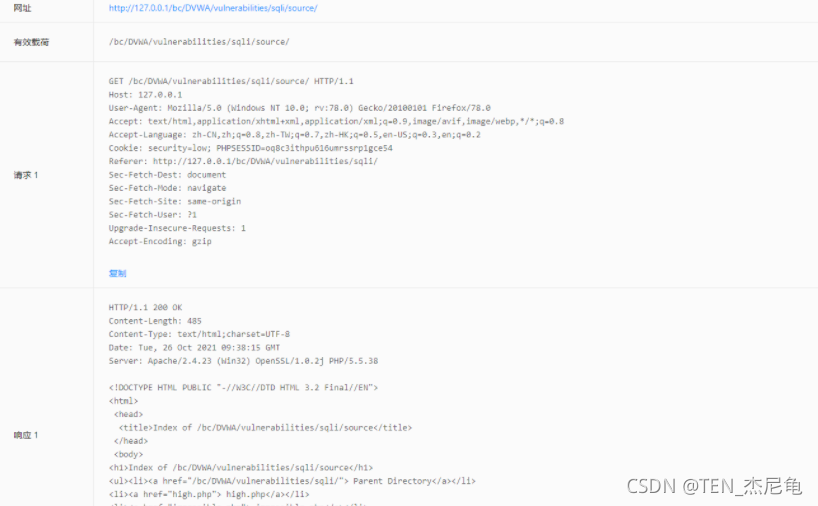
Reptile mode
xray Bugs can be checked with the help of crawlers
xray_windows_386.exe webscan --basic-crawler http://127.0.0.1/bc/DVWA/vulnerabilities/sqli/?id=2&Submit=Submit# --html-output 111.html
webscan web Page scan
–basic-crawler Basic reptiles
- 1
- 2
- 3
- 4
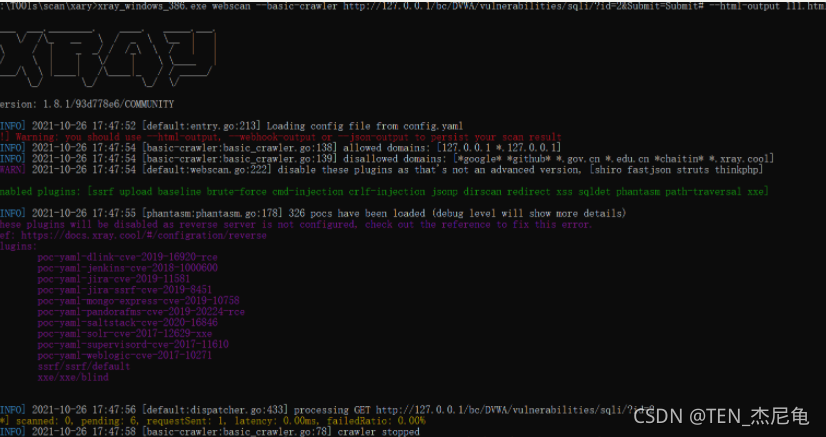
Xray + BurpSuite
burpsuite As Xray The upstream agent of ( Grab Xray Contract awarding )
namely : browser -> Xray -> burpsuite -> Server side
This method is convenient to view Xray Scan the packets sent by the website , And it can also be tested poc Whether it is right
Xray As burpsuite The upstream agent of ( Assist in testing )
namely : browser -> burpsuite -> Xray -> Server side
This method is convenient to test wherever you want , If you want to test, send it to Xray, Don't want to throw away the data packet
</article>
边栏推荐
- AVL balanced binary search tree
- Greenplum 6.x version change record common manual
- [Yugong series] February 2022 U3D full stack class 008 - build a galaxy scene
- All about PDF crack, a complete solution to meet all your PDF needs
- redis故障处理 “Can‘t save in background: fork: Cannot allocate memory“
- 实现自定义内存分配器
- Frequently Asked Coding Problems
- Greenplum 6.x monitoring software setup
- Download and install orcale database11.2.0.4
- 测试踩坑 - 当已有接口(或数据库表中)新增字段时,都需要注意哪些测试点?
猜你喜欢
随机推荐
年薪50w阿里P8亲自下场,教你如何从测试进阶
let const
快速集成认证服务-HarmonyOS平台
PPT模板、素材下载网站(纯干货,建议收藏)
You should use Google related products with caution
[Yugong series] February 2022 U3D full stack class 007 - production and setting skybox resources
Golan idea IntelliJ cannot input Chinese characters
如何在图片的目标中添加目标的mask
selenium自动化集成,八年测试经验软测工程师,一篇文章带你学懂
uniapp 微信小程序监测网络
联想混合云Lenovo xCloud:4大产品线+IT服务门户
channel. Detailed explanation of queuedeclare parameters
数字三角形模型 AcWing 1027. 方格取数
Go write a program that runs within a certain period of time
测试踩坑 - 当已有接口(或数据库表中)新增字段时,都需要注意哪些测试点?
RuntimeError: Calculated padded input size per channel: (1 x 1). Kernel size: (5 x 5). Kernel size c
A bug using module project in idea
Un salaire annuel de 50 W Ali P8 vous montrera comment passer du test
Teach you how to select PCB board by hand (II)
National SMS center number inquiry
![FPGA knowledge accumulation [6]](/img/db/c3721c3e842ddf4c1088a3f54e9f2a.jpg)