当前位置:网站首页>Cisp-pte XSS Foundation
Cisp-pte XSS Foundation
2022-06-11 09:55:00 【beirry】
The same-origin policy
Baidu : The same-origin policy (Same origin policy) It's a convention , It is the core and most basic security feature of the browser , If the same origin policy is missing , The normal functions of the browser may be affected . so to speak Web Is built on top of the same origin policy , The browser is simply an implementation of the same origin policy .
Cognate means domain name , agreement , The same port . Client scripts from different sources (JavaScript,actionscript) Without explicit authorization , Can't read or write the other person's resources .
If two pages agreement , Port and domain name All the same , The two pages have the same source .
Take Baidu for example :https://www.baidu.com
| URL | Is it homologous | reason |
|---|---|---|
| https://www.baidu.com/s?wd=1 | yes | agreement , port , The domain names are the same |
| http://www.baidu.com/s?wd=1 | no | Different agreements |
| https://www.sougou.com/s?wd=1 | no | Domain name is different |
| https://www.baidu.com:8080/s?wd=1 | no | Different ports |
utilize XSS Loophole , We can execute our own scripts on the target website (JavaScript Script ), So as to break through the restriction of homology strategy .
XSS
XSS The attack is to embed malicious script code in the web page , These codes are usually written in javascript Language writing .
We can use XSS Attack and steal the user's account and password 、Cookie, Change the content of the page ,URL Jump , Water pit attack, etc .
XSS type
XSS It can be roughly divided into three types : reflective , Storage type ,DOM type .
I went straight through the shooting range (DVWA) To give you an intuitive explanation
reflective XSS
open DVWA, stay DVWA Security Adjust the difficulty to low, Then click the reflection type xss, You can see such a page .
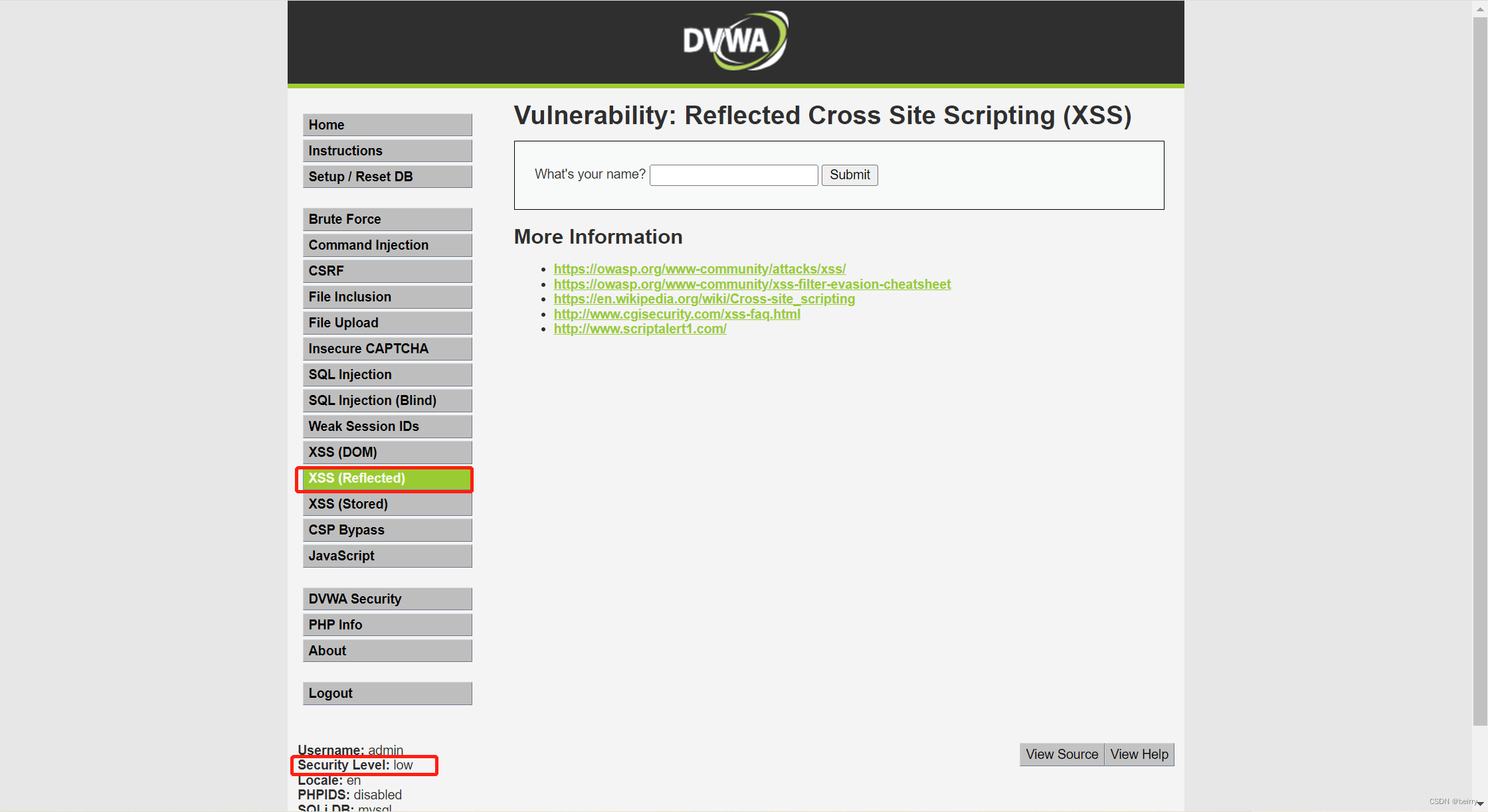
You can see that there is an input field here , We use it F12 Take a look at the label properties of its input box , Find it with name Variable to receive the value we entered , Then look up , It can be seen that it is used GET Pass values to transfer variables .

When we type xss When the sentence is , See how it works , Enter the popup statement in the input box :<script>alert(1)</script>, The function of this sentence is to pop up the window to display the numbers 1, Here's the picture :

Let's have a deeper understanding of reflection xss, Let's check the Internet , Find the file for this page , View the response , Find the... We entered xss sentence , Found to be xss The statement has the corresponding package . And you can see the statement we entered ,<script> Be recognized by the browser as a label for rendering . That's why xss Statement executed .
 Next, we randomly click on a page , Then return to the reflection type xss On the page , There is no pop-up window .
Next, we randomly click on a page , Then return to the reflection type xss On the page , There is no pop-up window .

So we can summarize the following features here :
1, reflective xss Most use GET Pass value , The value is passed through the back end ( Because the response package contains js sentence ).
2, reflective xss The code is only one-time , Not persistent ( From randomly clicking on a page to return with theout pop-up window, we can see ).
3, reflective xss Vulnerabilities typically focus on where values can be passed ( Similar to the input field ) lookup , Maybe there is xss There's a leak .
So how to use the reflection type xss Attack , First of all, we found that the page has reflection type xss Loophole , Then construct a malicious xss sentence , Forward the link to normal users , Let the user click on the link in some way , Then the attack succeeds .
Storage type XSS
Access storage XSS page , You can see a message board page .

Let's see what we use to transfer values .

Through the positioning operation, you can see that POST Pass value ,POST Value transfer is relative to GET There are several benefits of value transfer :
1, Than GET It is safer to transfer values .
2,GET There is a limit on the size of the value , and POST No, .
3,GET The value entered by value transfer is in the URL in , and POST The value is passed in the message body .
Next write xss Pop up statement <script>alert(1)</script>.

Click on sign Guestbook, Find the pop-up window .

You can see the message we entered in the message board , But the content is empty. Let's check the response package , It is found that there is a xss sentence , Why is our message empty ? Because the browser takes it as a tag and executes the content in the tag , That is, the pop-up window we see .

Then we click on other pages to return to the storage type XSS, I found that this time the window would pop up .

Here is a summary of the characteristics of the storage type :
1, Storage type XSS There are usually message boards , post , Personal information pages , These pages are likely to be stored xss Loophole .
2, Storage type xss Malicious statements will be saved to the database through the back end ( our xss Statements can be stored permanently , Because our code is stored in the database , Normal users access this page , The back end will take our xss Malicious statements are sent to the user , Make the user suffer xss attack ).
3, Relative to others xss type , Storage type xss Is more secretive , Because others need to click on the link constructed by the attacker , The storage type does not need .
Using storage xss The attack is simple , Just find the message board of the page , post , Pages that store values in a database, such as personal information , Monitoring if present xss Loophole , The insert xss Loophole , Just wait for the user to visit this page or trick the user to visit this page .
DOM type XSS
open DOM type xss page , Click on select.

You can see url There is one of them. default The value of the , The value is English.
We change the value to xss Pop up statement <script>alert(1)</script>
Enter after typing , Trigger the pop-up window .

View response package , lookup xss sentence , I didn't find .
explain DOM type XSS The vulnerability will not xss Statement is passed into the back end .
adopt F12 Location code , You can see default Value defined in the front end , The value we enter will be in <script> The code in the tag is output after passing through . stay <script> In the tag, we enter xss Statement is output directly to the browser , After the browser renders it as a label , Carry out our xss sentence .
Click on other pages , Back again DOM type XSS Vulnerability page , Find that you can't pop up .
Sum up DOM type XSS Characteristics :
1, The value entered does not go through the back end , Instead, it executes in the front end .
2, use URL Pass value , The construction method is the same as that of reflection type .
3,xss The statement is one-time , Same as reflex type .
The attack method is also the same as that of reflection type . The only difference is the reflective type payload It goes through the back end , and DOM The model is at the front .
Differences among the three
| XSS type | reflective | Storage type | DOM type |
|---|---|---|---|
| The trigger principle | User access with XSS Of the statement URL | User access carries xss Statement page | User access with XSS Of the statement URL |
| data storage | Store in URL in | Stored in a database | Store in URL in |
| Passing position | Back end | Back end , database | front end |
| Output location | HTTP Respond to | HTTP Respond to | DOM node |
Above is xss Basic content of , If there is a cousin who needs to be supplemented or amended , Please send me a private message ~
边栏推荐
- Drink at night, 50 classic SQL questions, really fragrant~
- DENISON液压泵用什么液压油?有哪些要求
- How do we connect to WiFi?
- 整型提升例题
- Where is it safer to open an account for soda ash futures? How much do you need to buy at least?
- Before applying data warehouse ODBC, you need to understand these problems first
- oracle 11g rac 磁盘组有空间无法增加数据文件?
- 【Objective-C】结构体和类的区别
- Q1营收超预期,满帮为何赢得逆风增长?
- Jmeter的使用(模拟高并发)
猜你喜欢

Technical practice of dolphin dispatching in kubernetes system

Reconstruction des composants Oracle XDB

Ora-00059 exceeds DB_ Files limit

对于力士乐电磁换向阀的功能与作用,你知道多少

How do online app stores of laundry chain stores do?

ESP8266_GET请求天气预报、json解析

Analysis of high frequency interview questions in massive data processing

BeanFactory 与FactoryBean的区别

锐意进取,砥砺前行,JASMINER持续深耕品牌实力

整型提升例题
随机推荐
js中关键字this的理解
The ins-30131 installer failed to verify the required initial settings
DENISON液压泵用什么液压油?有哪些要求
Flask (VII) - static file
Understanding polymorphism?
GDB debugging common commands
Leetcode brushing questions - hand tearing binary tree
ESP8266_接入百度物联网核心套件、使用MQTT协议通信
Rebuilding Oracle XdB components
ESP8266_SmartConfig
[TiO websocket] IV. the TiO websocket server implements the custom cluster mode
一万字彻底学会堆和二叉树
ESP8266_ SmartConfig
The difference and relation between machine learning and statistics
2022 must have Chrome extension - browser plug-in to double your Internet efficiency
What is the difference between an interface and an abstract class?
JS foundation - array object
Image quality evaluation including Matlab source code
Flask (IV) -- URL construction
Tenthousand words thoroughly learn heap and binary tree