当前位置:网站首页>Misc Basic test method and knowledge points of CTF
Misc Basic test method and knowledge points of CTF
2022-07-05 15:10:00 【Golden silk】
One 、 Simple test method
1、 Attribute hiding flag Or some important information , Such as unpacking password
2、 Hexadecimal data of the file ( middle \ ending ) Hide character segments , Those hidden character segments are generally regular , It may take some decoding to arrive flag, Example :Bugku And telnet_l2872253606 The blog of -CSDN Blog
3、 Add file suffix zip unpack , In the unzipped file flag
4、 Complete the file header
5、 Common file types

6、kali Next file Command to view file types
command :file file name
Two 、zip
1、 File format
• Head sign 50 4B 03 04
• Version number , The last four digits of the head logo
• Encryption , The last two digits of the version number ,00 Is unencrypted , The rest are usually encrypted
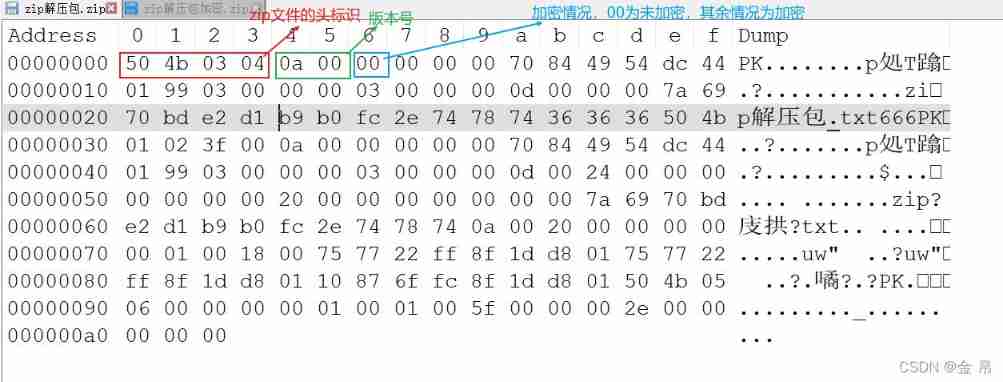
2、 Pseudo encryption , There was no encryption zip file , In artificial modification 16 Base case ( After the version number 00 Get rid of ), I mistakenly thought it was encrypted when decompressing
3、 Code explosion , Using tools ARCHPR Blasting
3、 ... and 、PNG
1、 File format
• Head logo ,89 50 4E 47 0D 0A 1A 0A
• Width bit 0x10-0x13, Don't change it at will , According to CRC Value modification
• Height bit 0x14-0x17, You can change it at will
•CRC Check bit 0x1D-0x20,CRC It is the verification of file data blocks , Modifying the data block will cause the verification to fail , The file cannot be displayed normally
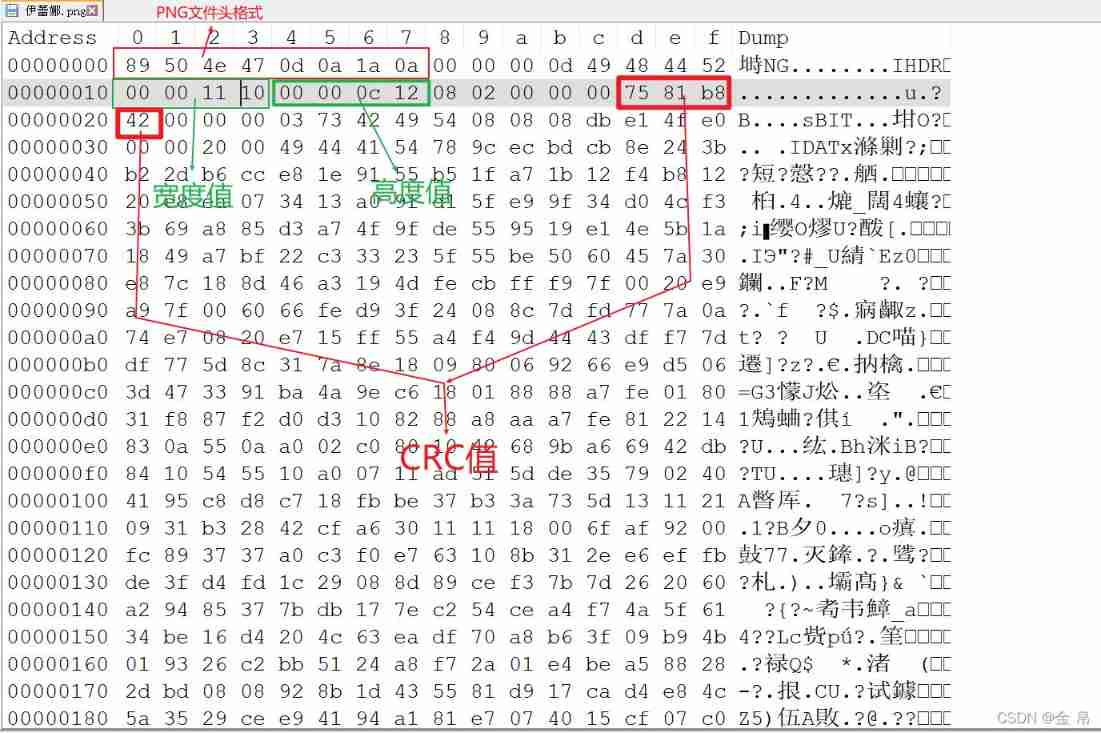
2、 The height display is incomplete , Example :Bugku Steganography _l2872253606 The blog of -CSDN Blog
3、 The width display is incomplete , According to the... Of blasting documents CRC Value changes the width , Otherwise, it will fail to open the file
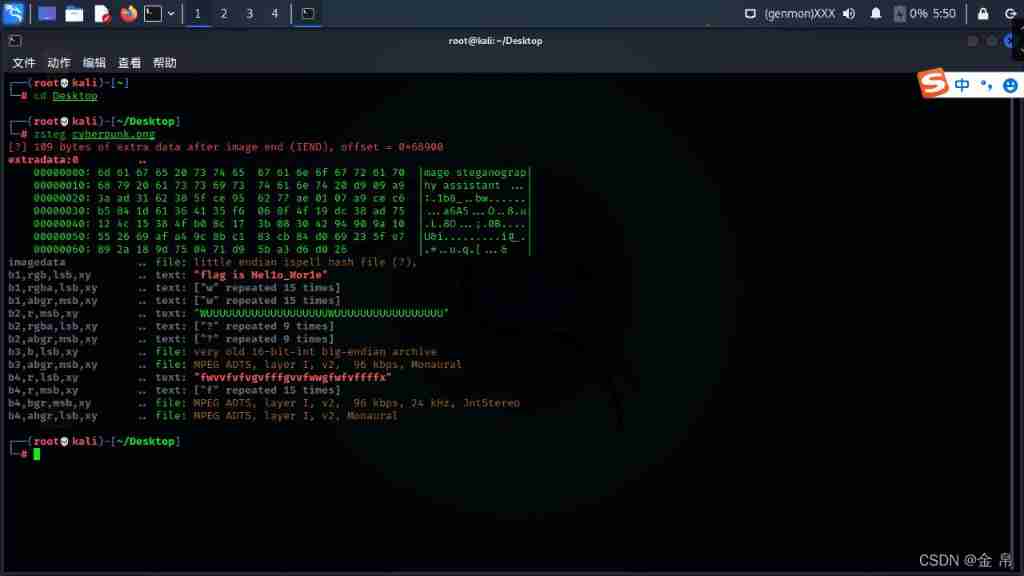
4、LSB Steganography , Using tools stegsolve Or is it kali see ,kali Watch it all ,
Example :Bugku Cyberpunk _l2872253606 The blog of -CSDN Blog
• use stegsolve see
For documents stegsolve open ,Analyse,Date Extract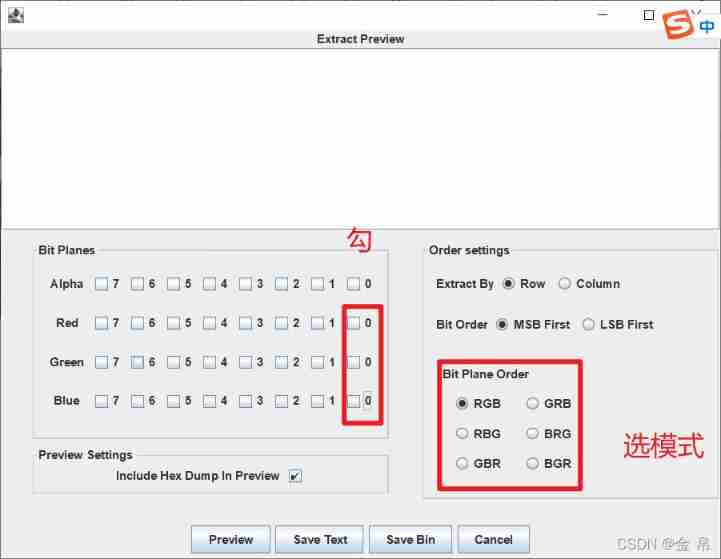
Check the last three 0, The mode is generally RGB, If you don't find it , You can try another mode
Point again Preview, Drag the data to the top
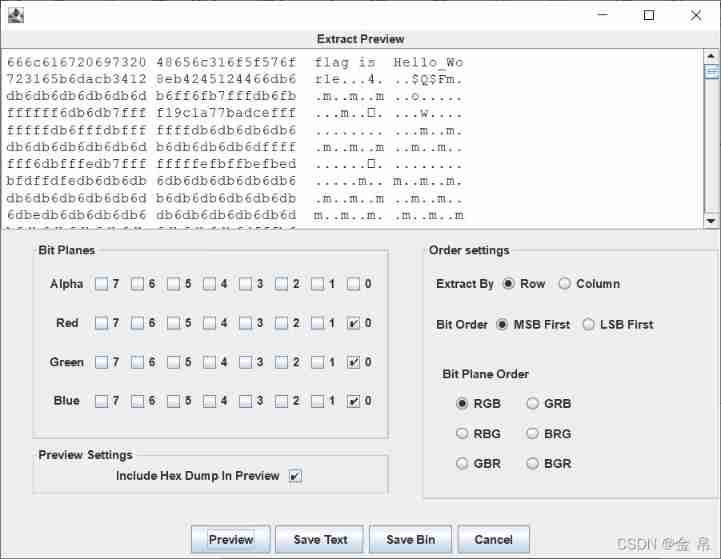
Find out flag
• use kali see
You have to download zsteg Tools , Specific method Baidu , Drag the file into kali
Enter the command zsteg file name
You can view the hidden content
Four 、JPG
1、 File format
• Head logo ,FF D8
• Tail marker ,FF D9
2、 Modification of width and height
3、base64 Source code to picture
5、 ... and 、GIF
1、 File format
• Head sign ,47 49 46 38(GIF8)
2、flag Hidden in a frame , use stegsolve see
6、 ... and 、 File separation
Sometimes a file may hide many files , At this time, we have to use tools to separate
1、 Automatically analyze files and automatically separate files
use kali System
• Analyze documents binwalk file name
• Separate files binwalk -e file name
• Separate files foremost file name -o Directory name
2、 Manual file separation
Automatic separation is used when it doesn't work , Specific operation Baidu
3、 Example :Bugku And easy_nbt_l2872253606 The blog of -CSDN Blog
边栏推荐
- P1451 calculate the number of cells / 1329: [example 8.2] cells
- Run faster with go: use golang to serve machine learning
- No one consults when doing research and does not communicate with students. UNC assistant professor has a two-year history of teaching struggle
- Common PHP interview questions (1) (written PHP interview questions)
- P6183 [USACO10MAR] The Rock Game S
- 百亿按摩仪蓝海,难出巨头
- Redis distributed lock principle and its implementation with PHP (2)
- Drive brushless DC motor based on Ti drv10970
- maxcompute有没有能查询 表当前存储容量的大小(kb) 的sql?
- 亿咖通科技通过ISO27001与ISO21434安全管理体系认证
猜你喜欢
How can I quickly check whether there is an error after FreeSurfer runs Recon all—— Core command tail redirection
Super wow fast row, you are worth learning!
NBA赛事直播超清画质背后:阿里云视频云「窄带高清2.0」技术深度解读
Selection and use of bceloss, crossentropyloss, sigmoid, etc. in pytorch classification
Interpretation of Apache linkage parameters in computing middleware
MySQL之CRUD

超越PaLM!北大硕士提出DiVeRSe,全面刷新NLP推理排行榜
![1330: [example 8.3] minimum steps](/img/69/9cb13ac4f47979b498fa2254894ed1.gif)
1330: [example 8.3] minimum steps
Two Bi development, more than 3000 reports? How to do it?
1330:【例8.3】最少步数
随机推荐
Anaconda uses China University of science and technology source
Reconnaissance des caractères easycr
Select sort and bubble sort
CPU design related notes
Two Bi development, more than 3000 reports? How to do it?
爱可可AI前沿推介(7.5)
[recruitment position] infrastructure software developer
maxcompute有没有能查询 表当前存储容量的大小(kb) 的sql?
超越PaLM!北大硕士提出DiVeRSe,全面刷新NLP推理排行榜
easyOCR 字符識別
Can gbase 8A view the location of SQL statement history?
CODING DevSecOps 助力金融企业跑出数字加速度
Ctfshow web entry information collection
基于TI DRV10970驱动直流无刷电机
sql server char nchar varchar和nvarchar的区别
Interview shock 62: what are the precautions for group by?
MySQL----函数
数据库学习——数据库安全性
Redis distributed lock principle and its implementation with PHP (2)
[detailed explanation of Huawei machine test] character statistics and rearrangement