当前位置:网站首页>What are CSRF, XSS, SQL injection, DDoS attack and timing attack respectively and how to prevent them (PHP interview theory question)
What are CSRF, XSS, SQL injection, DDoS attack and timing attack respectively and how to prevent them (PHP interview theory question)
2022-07-05 14:58:00 【Back end regular developers】
PHP Interview theory questions
CSRF、XSS、SQL Inject 、DDOS attack 、 What are sequential attacks and how to prevent them
1、CSRF
(1) CSRF brief introduction :
CSRF(Cross-site request forgery) Cross-site request forgery , Also known as “One Click Attack” perhaps Session Riding, Commonly abbreviated as CSRF perhaps XSRF, Is a malicious use of the site .
(2) CSRF The harm of the attack
The main harm comes from , The attacker embezzles the user's identity , Send a malicious request . such as : Simulate users to send mail , Send a message , And pay 、 Transfer, etc .
XSS It mainly uses the trusted users in the site , and CSRF By disguising requests from trusted users , To take advantage of trusted websites . And XSS Compared to attack ,CSRF More dangerous .
(3) prevent CSRF Solutions for
- Important data interaction adopts POST Receive , Of course POST It's not everything , Forge a form The form can be cracked .
- Use verification code , As long as the data interaction is involved, the verification code shall be verified first , This method can completely solve CSRF.
- But for the sake of user experience , Web site can not give all the operations together with a verification code . So the verification code can only be used as an auxiliary means , Not as a major solution .
- verification HTTP Referer Field , This field records this HTTP The source address of the request , The most common application is the image anti-theft chain .
- Add a token for each form token And verify .
2、XSS
(1) XSS brief introduction
Cross site scripts (cross site script) Referred to as XSS, It's a common occurrence in web Computer security vulnerabilities in application , It's also web The most popular way to attack .
XSS It refers to the defect that the malicious attacker uses the website to escape the data submitted by the user or to filter the data insufficiently , And then add some code , Embedded in web Go to , So that other users access will execute the corresponding embedded code .
(2) XSS The harm of the attack
- Stealing user data , such as : Login account 、 Online banking account number, etc
- Use user identity , Read 、 Tampering 、 add to 、 Delete data, etc
- Steal important commercial materials
- Illegal transfer
- Mandatory E-mail
- Website hanging horse
- Control the victim's machine to attack other websites
(3) prevent XSS Solutions for
- XSS The root cause of is that the data submitted by the client is not completely filtered , So the key is to filter the information submitted by users .
- Will be important cookie Marked as http only, In this case js Medium document.cookie Statement cannot get cookie 了 .
- Only allow users to enter the data we expect . for example :age User age only allows users to enter numbers , All characters except numbers are filtered out .
- On data Html Encode Handle : When users submit data HTML code , Convert the corresponding symbols into entity names, and then proceed to the next step .
- Filter or remove special Html label .
- Filter js Label of event . for example “οnclick=”, “onfocus” etc. .
3、SQL Inject
(1) SQL Introduction to injection
SQL Injection is one of the most common network attacks , Mainly through SQL Command insert into Web Form submit or input the query string of domain name or page request , Realize no account login , Even tampering with the database .
(2) SQL The harm of injection attack
- Database information leakage : The disclosure of the user's privacy information stored in the database ;
- Webpage tampering : Tamper with specific web pages by operating the database ;
- The database was maliciously manipulated : The database server was attacked , The system administrator account of the database has been tampered with ;
- The server is remotely controlled , The rear door is installed ;
- Delete and modify database table information .
(3) SQL The way of Injection
Usually ,SQL Injection locations include :
- Form submission , Mainly POST request , Also include GET request ;
- URL Parameter submission , Mainly for GET Request parameters ;
- Cookie Parameter submission ;
- HTTP Some modifiable values of the request header , such as Referer、User_Agent etc. ;
(4) prevent SQL Injected solutions
- Verify the user's input , Use regular expressions to filter the incoming parameters ;
- Use parameterized statements , Do not splice sql, You can also use secure stored procedures ;
- Do not use a database connection with administrator privileges , Use limited database connections for each application ;
- Check the data storage type ;
- Important information must be encrypted ;
4、DDOS
(1) DDOS brief introduction
- DOS attack (Denial of Service Denial of service attacks ): Any attack means that users cannot continue to use normal services due to insufficient network security protection measures , Can be called a denial of service attack , Its purpose is to consume network broadband or system resources , Make the network or computer unable to provide normal services .
- DDOS(Distributed Denial of Service , Distributed denial of service ), Any attacker who controls the puppet host on the network , At the same time, the way they launch denial of service attacks against the target host is called distributed denial of service attack .
(2) DDOS The harm of the attack
- Make the customer's business unavailable 、 Loss of interest
- A service in the customer network is attacked , Customer networking is blocked in an all-round way , All businesses are paralyzed , Serious chain reaction
- The political impact of the attack 、 The pressure of public opinion brings reputation loss to the enterprise
(3) How to defend DDOS attack
- Update system patches in time
- Install software and hardware for killing , Update virus database in time
- Set complex passwords , Reduce the possibility of the system being controlled
- Close unnecessary ports and services
- Often detect the vulnerability of the network , Find problems and fix them in time .
- For important web The server can establish multiple images to realize load balancing , Reduce to a certain extent DDOS Hazards of
5、 Timing attacks
(1) Introduction to timing attack
In cryptography , Timing attack is a side channel attack , The attacker attempts to deduce the password after analyzing the time execution of the encryption algorithm . Each logical operation takes time to execute in the computer , Different according to the input , Accurately measure the execution time , Reverses the password according to the execution time .php
If it is ordinary == To compare , Then the two strings are compared one by one from the first bit , If you find something different, return immediately false, After calculating the return speed, you can know which one started different , In this way, the scene of cracking passwords by bits, which often appears in movies, is realized .
(2) How to defend against sequential attacks
php In order to deal with this situation , Able to use hash_equals function .
Extract a passage from php Information in the manual :
hash_equals ( string $known_string , string $user_string ) : bool
Compare two strings , Whether they are equal or not , The time consumption of this function is constant .
This function can be used in string comparison scenarios that need to prevent timing attacks , for example , Can be used to compare crypt() The scenario of password hash value .
<?php
$expected = crypt('12345', '$2a$07$usesomesillystringforsalt$');
$correct = crypt('12345', '$2a$07$usesomesillystringforsalt$');
$incorrect = crypt('apple', '$2a$07$usesomesillystringforsalt$');
var_dump(hash_equals($expected, $correct));//true
var_dump(hash_equals($expected, $incorrect));//false
?>
Reproduced in :
https://www.cnblogs.com/tudou1223/p/11506574.html
https://blog.csdn.net/LuHai3005151872/article/details/121903785
边栏推荐
猜你喜欢
Crud of MySQL

Crud de MySQL
Topology visual drawing engine
想进阿里必须啃透的12道MySQL面试题
【leetcode周赛总结】LeetCode第 81 场双周赛(6.25)
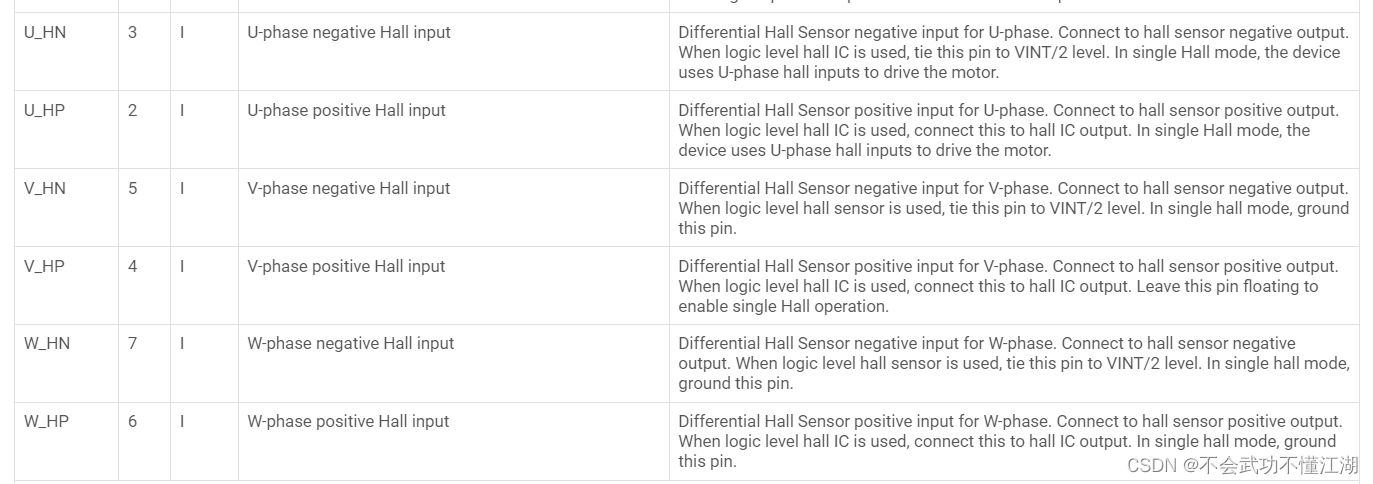
Drive brushless DC motor based on Ti drv10970
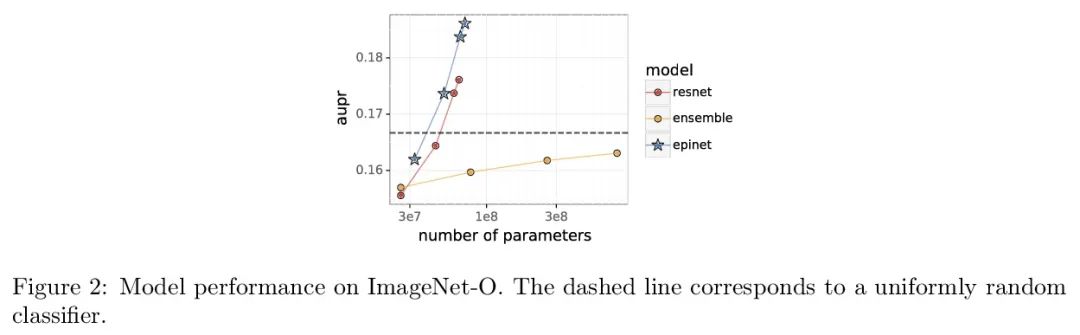
爱可可AI前沿推介(7.5)
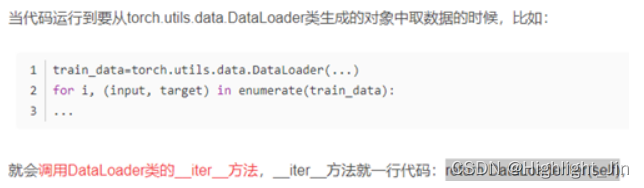
浅谈Dataset和Dataloader在加载数据时如何调用到__getitem__()函数
1330:【例8.3】最少步数

Differences between IPv6 and IPv4 three departments including the office of network information technology promote IPv6 scale deployment
随机推荐
实现一个博客系统----使用模板引擎技术
easyOCR 字符識別
MySQL之CRUD
Run faster with go: use golang to serve machine learning
启牛学堂班主任给的证券账户安全吗?能开户吗?
黑马程序员-软件测试-10阶段2-linux和数据库-44-57为什么学习数据库,数据库分类关系型数据库的说明Navicat操作数据的说明,Navicat操作数据库连接说明,Navicat的基本使用,
当代人的水焦虑:好水究竟在哪里?
Isn't it right to put money into the external market? How can we ensure safety?
Is the securities account given by the head teacher of qiniu school safe? Can I open an account?
CPU设计实战-第四章实践任务二用阻塞技术解决相关引发的冲突
STM32+BH1750光敏传感器获取光照强度
Ecotone technology has passed ISO27001 and iso21434 safety management system certification
What are the domestic formal futures company platforms in 2022? How about founder metaphase? Is it safe and reliable?
CPU design related notes
Two policemen were shot dead in a "safety accident" in Philadelphia, USA
mysql8.0JSON_ Instructions for using contains
Talking about how dataset and dataloader call when loading data__ getitem__ () function
How to open an account of qiniu securities? Is it safe to open an account?
[summary of leetcode weekly competition] the 81st fortnight competition of leetcode (6.25)
Interview shock 62: what are the precautions for group by?