当前位置:网站首页>Penetration testing methodology
Penetration testing methodology
2022-07-05 14:21:00 【Cwxh0125】
Penetration testing methodology
Penetration test (penetration testing, pentest) It's a safety assessment ( Audit ) The methodology of specific means is to formulate 、 When implementing the information security audit program , Rules to follow 、 Routines and processes . People are evaluating The Internet 、 application 、 System or a combination of the three When the safety condition of , Constantly explore a variety of practical ideas and mature practices , And summed up a set of theories — Penetration testing methodology .
Type of penetration test
Black box testing
During the black box test , The safety auditor does not know the internal technical structure of the tested unit , Evaluate the security of network infrastructure from the outside . At all stages of penetration testing , Black box testing uses real-world hacking techniques , Expose the security of the target , It can even expose security vulnerabilities that have not been exploited by others .
Penetration testers should be able to understand security vulnerabilities , Classify them and rank them according to their risk levels ( high 、 in 、 low ) Sort it out . Generally speaking , The level of risk depends on the size of the harm that may be caused by the relevant weakness . Sophisticated penetration testing can identify all attack modes that can cause security accidents . When the tester has finished all the testing work of the black box test , They organize the necessary information about the security status of the test object , And use business language to describe these identified risks , And then they are summarized into a written report . The market price of black box test is usually higher than that of white box test .
White box testing
The auditor of white box test can obtain all kinds of internal information of the unit under test, and even do not disclose it , Therefore, the vision of penetration testers is broader . If the white box test method is used to evaluate the security vulnerability , Testers can achieve the highest evaluation accuracy with the least amount of work . White box testing starts from the environment of the system under test , Eliminate all internal security issues . This increases the difficulty of penetrating the system from the outside of the unit . Black box testing doesn't do that . White box testing takes as many steps as black box testing . in addition , If you can match the number of steps required by the white box with that of the black box test . in addition , If you can combine white box testing with the regular R & D life cycle , Before an intruder discovers or even exploits a security vulnerability , Eliminate all security risks as early as possible . This makes the white box test time 、 cost , And discovery 、 The technical threshold to address security vulnerabilities is lower than that of black box testing .
Vulnerability assessment and penetration testing
Vulnerability assessment analyzes the situation and degree of security threats to enterprise assets , Evaluate the security of internal and external security controls . This technical information system evaluation , Not only expose the risks in the existing preventive measures , And propose multiple alternative remedial strategies , And compare these strategies . Internal vulnerability assessment can ensure the security of internal system , The external vulnerability assessment is to verify the boundary protection (perimeter defenses) The effectiveness of the . Whether internal vulnerability assessment or external vulnerability assessment , Appraisers will use various attack modes to strictly test the security of network assets , So as to verify the ability of the information system to deal with security threats , Then determine the effectiveness of response measures . Different types of vulnerability assessment require different testing processes 、 Testing tools and automated testing techniques are also different . This can be controlled through integrated security vulnerabilities (vulnerability management) Platform . The current security vulnerability management platform has a vulnerability database that can be updated automatically , Be able to test different types of network devices , And will not affect the integrity of configuration management and change management .
The biggest difference between vulnerability assessment and penetration testing is : Penetration testing should not only identify the weaknesses of the target , It is also designed to exploit vulnerabilities on the target system 、 Privilege promotion and access maintenance . let me put it another way , Although vulnerability assessment can fully find defects in the system , However, we will not consider measuring the harm caused by these defects to the system . in addition , Compared with vulnerability assessment , Penetration tests tend to invade , Will deliberately use various technical means to exploit security vulnerabilities ; Therefore, penetration testing may have a real destructive impact on the production environment . Vulnerability assessment is non intrusive , qualitative 、 Quantitatively identify known security vulnerabilities .
Safety testing methodology
OWASP TOP 10
10 The most serious Web Application security risks
http://www.owasp.org.cn/OWASP-CHINA/owasp-project/OWASPTop102017v1.1.pdf
top ten Web Application security risks
1、 Injections . When untrusted data is sent to the interpreter as part of a command or query , There will be things like SQL,NoSQL,OS and LDAP Injection vulnerabilities such as injection . The attacker's hostile data may induce the interpreter to execute unexpected commands or access the data without proper authorization .
2、 Authentication failed . Application functions related to authentication and session management are often incorrectly implemented , This allows an attacker to break the password , Key or session token , Or use other implementation defects to assume the identity of other users temporarily or permanently .
3、 Sensitive data exposure . many Web Applications and API Unable to properly protect sensitive data , For example, finance , Health care and PII. Attackers may steal or modify these unprotected data , For credit card fraud , Identity theft or other crimes . Sensitive data can be compromised without additional protection , For example, static encryption or encryption in transit , And special precautions need to be taken when exchanging with browsers .
4、XML External entities (XXE). A lot of older or improperly configured XML The processor evaluates XML External entity references in documents . External entities can use files URI The handler , Internal file sharing , Internal port scan , Remote code execution and denial of service attacks to expose internal files .
5、 Access control corrupted . Usually , Restrictions on the actions that an authenticated user is allowed to perform are usually not performed correctly . Attackers can exploit these vulnerabilities to access unauthorized functions and services / Or data , For example, access to other users' accounts , View sensitive files , Modify other users' data , Change access rights, etc .
6、 Security configuration error . Security configuration errors are the most common problem . This is usually due to an insecure default configuration , Incomplete or temporary configuration , Open Cloud Storage , Misconfigured HTTP Headers and detailed error messages containing sensitive information . Not only must all operating systems be configured safely , frame , Libraries and Applications , And it has to be repaired in time / upgrade .
7、 Cross-site scripting XSS. Whenever an application contains untrusted data in a new web page without proper validation or escape , Or you can create HTML or JavaScript Browser API When updating an existing web page with user supplied data , Will happen XSS Loophole .XSS Allows attackers to execute scripts in the victim's browser , These scripts can hijack user sessions , Destroy a website or redirect users to malicious sites .
8、 Unsafe deserialization . Unsafe deserialization usually results in remote code execution . Even if the deserialization defect does not result in remote code execution , They can also be used to perform attacks , Including replay attacks , Injection attack and privilege escalation attack .
9、 Using components with known vulnerabilities . Such as the library , Components such as frameworks and other software modules run with the same privileges as the application . If vulnerable components are used , Such attacks may lead to serious data loss or server takeover . Applications that use components with known vulnerabilities and API May damage application defense , And cause all kinds of attacks and effects .
10、 Insufficient logging and monitoring . Inadequate logging and monitoring , Plus missing or invalid integration of event responses , Allows an attacker to further attack the system , Stay persistent , Turning to more systems and tampering with , Extract or destroy data . Most violation studies show that , Violations were detected for more than 200 God , It is usually detected by external parties rather than by internal processes or monitoring .
* General defect list (CWE)
CWE-79:XSS Loophole
[http://cwe.mitre.org/data/definitions/79.html]
CWE-89:SQLi
[http://cwe.mitre.org/data/definitions/89.html]
* General vulnerability and disclosure (CVE)
[http://cve.scap.org.cn/]
A specific vulnerability
[http://cve.mitre.org/]
MS17-010( Microsoft Security Bulletin )
An announcement corresponds to a vulnerability
KB start
S2-053
strtus2
APACHE Open source development java Framework
* Other methodologies
Open source security testing methodology (OSSTMM)
http://www.isecom.org/research/osstmm.html
Information system security assessment framework (ISSAF)
http://www.oissg.org/issaf
Web Application security joint threat classification (WASC-TC)
http://projects.webappsec.org
Penetration testing process
pets
Penetration test execution standard (PTES) The pioneers are the elites in the penetration testing industry , There are seven stages
- Prior interaction
- Intelligence gathering
- Threat modeling
- Vulnerability analysis
- Exploit
- Deep use
written report
PTES The main features and advantages of are as follows
1、 It is a very comprehensive penetration testing framework, covering the technical aspects and other important aspects of rope penetration testing , Such as scope spread 、 The report 、 And how infiltrators protect themselves
2、 He introduced the specific methods of most test tasks , It can guide you to accurately test the security state of the target system
3、 He gathered a number of day trips ” Seepage “ Extensive experience of penetration testing experts
4、 It contains the most commonly used and rare related technologies
5、 He is easy to understand , You can adjust the corresponding test steps according to the needs of the test work
General penetration testing framework
From the perspective of Technology Management , Following a formal testing framework is extremely important for security testing , The common penetration testing framework covers the typical audit testing work and all stages involved in penetration testing work .
Relevant stage :
- Scoping
- Information gathering
- target recognition
- Service enumeration
- Vulnerability mapping
- social engineering
- Exploit
- Elevated privileges
- Access maintenance
Document report
Scoping
1、 What is the test object ?
2、 What test method should be used ?
3、 What are the conditions to be met in the penetration test ?
4、 What factors may limit the process of test execution ?
5、 How long will it take to complete the test ?
6、 What mission objectives should this test achieve ?
Information gathering
Penetration testers need to use various public resources to obtain relevant information of test objectives as much as possible .
The main channels for collecting information from the Internet are :
Forum | Bulletin board | Newsgroups | The media file | Blog | Social networks | Other commercial or non-commercial websites
In addition, relevant data can be obtained through various search engines .
Such as Google 、 Yahoo 、MSN Bing Ying 、 Baidu, etc
The information collected mainly includes DNS、 The server 、 Routing relationship 、whois、 database 、 E-mail address 、 Phone number 、 Personal information and user accounts .
The more information you collect , The higher the probability of successful penetration test .
target recognition
Identify the status of the target network , Operating system and network architecture .
Service enumeration
This stage is based on the results of the previous stages , Further identify all open disconnects of the target system .
Once all open ports are found , You can list the services running on the target system through these ports .
The open ports on the host have corresponding service programs , After in-depth analysis of this information , Possible vulnerabilities in the target network infrastructure can be further explored .
Vulnerability mapping ( Vulnerability scanning )
According to the discovered open ports and service programs , Find known and unknown vulnerabilities
social engineering
If the target network has no direct access , The art of deception will play an important role in attracting jade .
Targeted attacks on personnel of the target organization , It is likely to help us find the entrance to the target system .
for example , A malicious program that entices users to install a backdoor , It may form a breakthrough in the penetration of auditors .
The penetration of social engineering can be divided into many different forms .
Pretend to be a network administrator , Ask users to improve their account information by phone ; Send phishing email to hijack the user's bank account ; Even induce someone to appear somewhere , These are social engineering attacks
It should be noted that before deceiving the target to achieve the penetration target , In most cases, it takes a long time to study the psychology of the target person
in addition , We need to study whether local laws allow
Exploit
After discovering the vulnerability , You can use the existing vulnerability exploitation program to penetrate the target system
The main task of this stage is to control the target system
This process can be divided into three steps , Before the attack 、 attack 、 Related actions after the attack
Elevated privileges
The penetration tester is based on their access rights , Play at will in the target system ,
Raise the right , Is to upgrade the ordinary user's permission to the administrator's permission
Access maintenance ( Bury the back door )
Most of the time , Auditors need to maintain their access to the target system for a period of time .
That is to bury the back door ( Clear the back door when you leave )
Document report
Auditors should record 、 Report and demonstrate on site what has been identified 、 Verified and exploited security vulnerabilities .
And fix all existing security vulnerabilities according to these documents 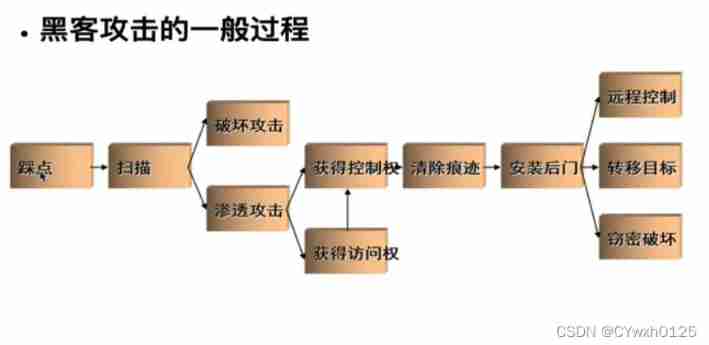
边栏推荐
猜你喜欢
Thymeleaf th:classappend属性追加 th:styleappend样式追加 th:data-自定义属性

世界环境日 | 周大福用心服务推动减碳环保
日化用品行业智能供应链协同系统解决方案:数智化SCM供应链,为企业转型“加速度”
Tiflash compiler oriented automatic vectorization acceleration

The IPO of Ruineng industry was terminated: the annual revenue was 447million and it was planned to raise 376million

软件测试人在深圳有哪些值得去的互联网公司【软件测试人员专供版】
申请代码签名证书时如何选择合适的证书品牌?
How does redis implement multiple zones?

Qingda KeYue rushes to the science and Innovation Board: the annual revenue is 200million, and it is proposed to raise 750million
Loop invariant
随机推荐
Tidb DM alarm DM_ sync_ process_ exists_ with_ Error troubleshooting
R语言ggplot2可视化:可视化折线图、使用theme函数中的legend.position参数自定义图例的位置
Oneconnect listed in Hong Kong: with a market value of HK $6.3 billion, ye Wangchun said that he was honest and trustworthy, and long-term success
R language uses boxplot function in native package (basic import package, graphics) to visualize box plot
Thymeleaf 常用函数
mysql8.0JSON_CONTAINS的使用说明
如何将 DevSecOps 引入企业?
TiCDC 6.0原理之Sorter演进
SSL证书错误怎么办?浏览器常见SSL证书报错解决办法
Faire un clip vidéo auto - média deux fois, comment clip n'est pas considéré comme une infraction
Thymeleaf 使用后台自定义工具类处理文本
LeetCode_ 2 (add two numbers)
Loop invariant
[learning notes] stage test 1
ASP.NET大型外卖订餐系统源码 (PC版+手机版+商户版)
Solution of commercial supply chain collaboration platform in household appliance industry: lean supply chain system management, boosting enterprise intelligent manufacturing upgrading
Assembly language
软件测试人在深圳有哪些值得去的互联网公司【软件测试人员专供版】
Principle and performance analysis of lepton lossless compression
Time to calculate cron expression based on cronsequencegenerator