当前位置:网站首页>How to encapsulate distributed locks more elegantly
How to encapsulate distributed locks more elegantly
2020-11-06 01:19:00 【Yin Jihuan】
Distributed locks usually have many choices , be based on Redis Of , be based on Zookeeper Of , Based on database and so on .
Redis For caching data , It's used in projects , So use Redis There will be a little more distributed locks .
If you use Redis To make a lock , You can use open source solutions directly , such as redisson.
The most common uses are as follows :
RLock lock = redisson.getLock("anyLock");lock.lock();run();lock.unlock();
Get lock object , call lock() Lock , Execute business logic , call unlock() Release the lock .
Although the framework provides a very simple way to use it , But we still need to do a layer of packaging for the lock . The purpose of packaging is to improve scalability and ease of use .
Abstract interface
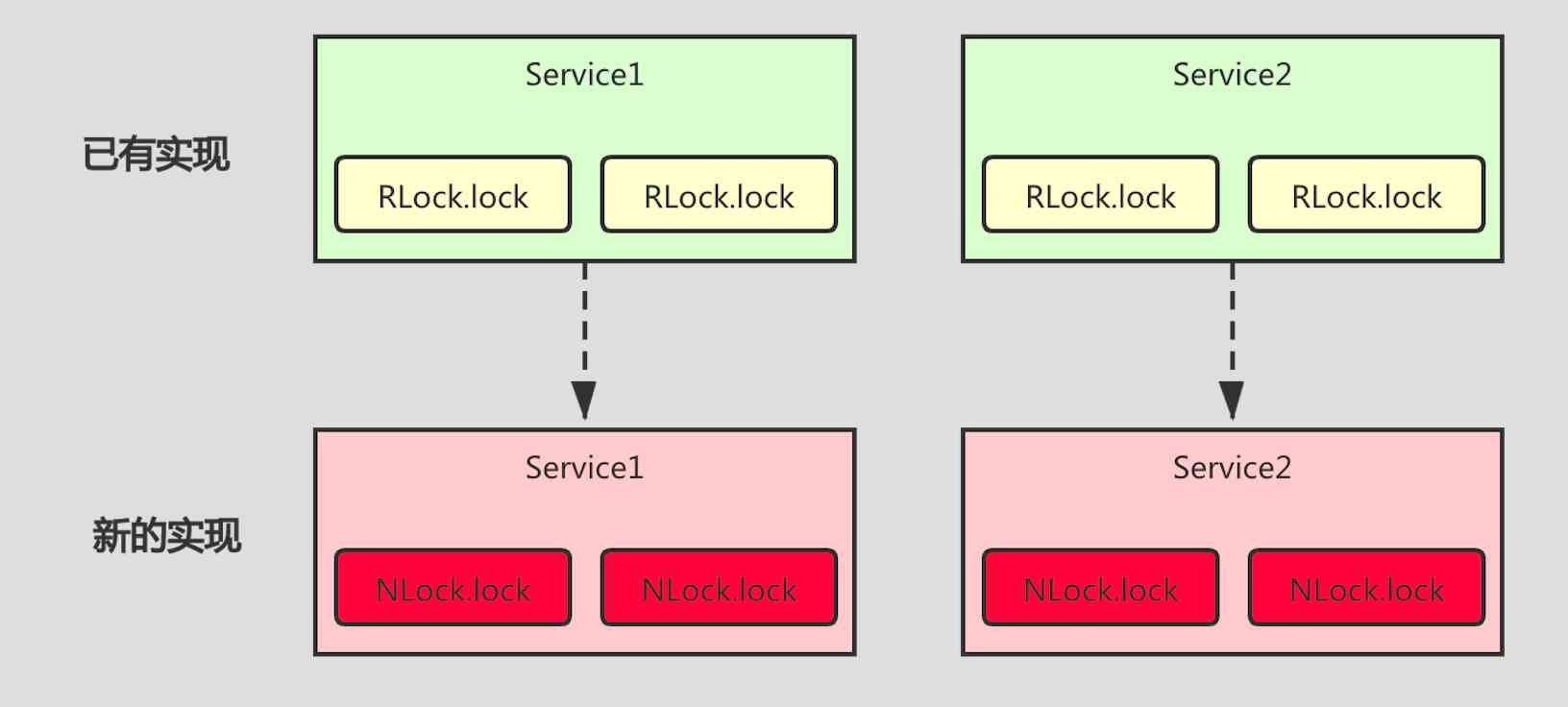
If we use it directly redisson The native API Make locks , So many places will appear RLock Related code , And then one day , For some reason , The lock needs to be replaced , At this time, the scope of change is relatively large . Each uses RLock Everything has to be changed .
Here's the picture : quite a lot Service Are used to RLock.lock() Method , When we need to replace locks , All the classes and methods involved have to be modified , The change points are shown in the red section .
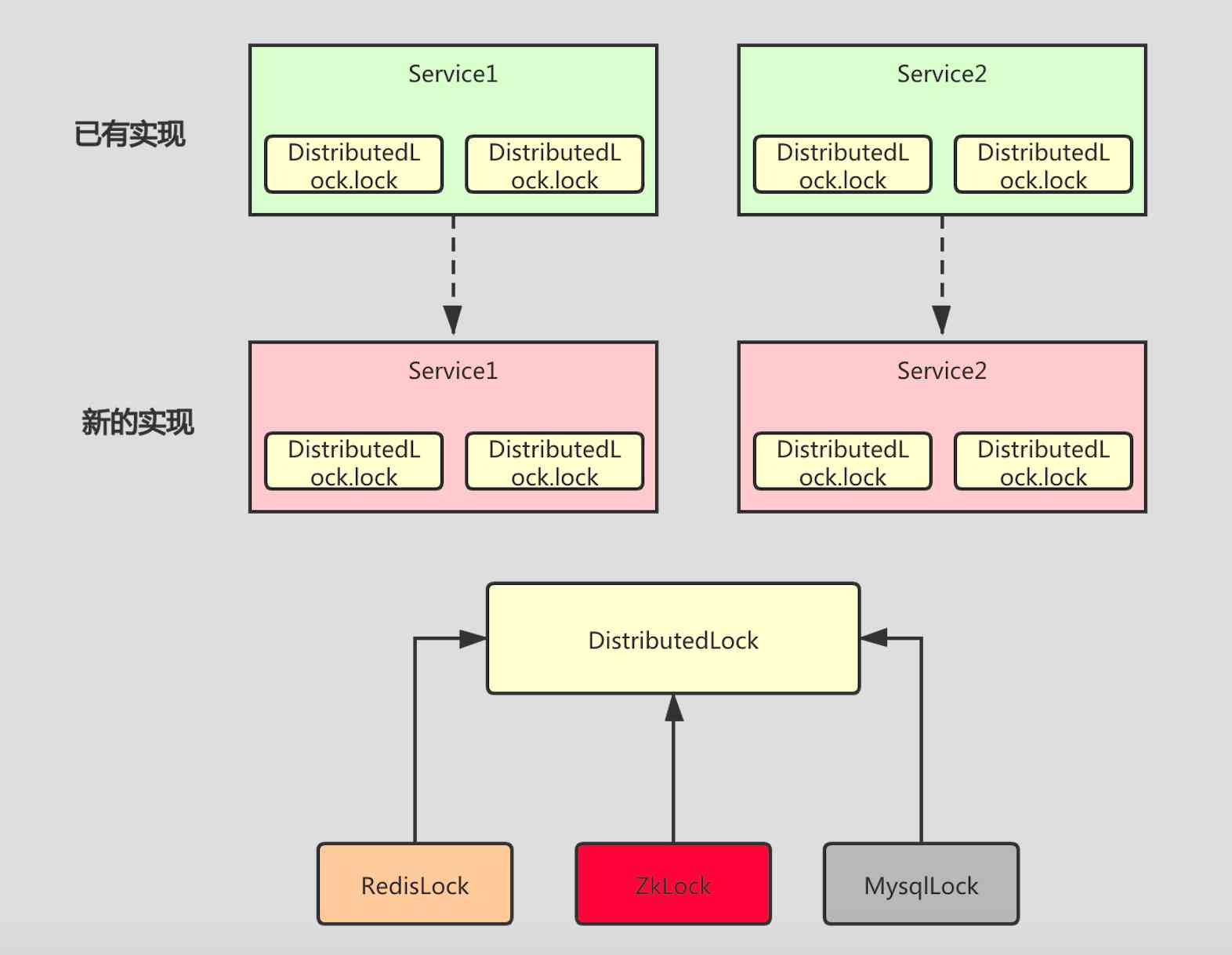
So we need to do a layer of abstraction , You can define a DistributedLock Interface to provide lock related capabilities , Provides multiple implementations , This makes it easy to replace and expand .
Here's the picture : Every Service It's all for DistributedLock Interface to lock , When we need to replace the lock implementation , It doesn't need to be changed , Just replace DistributedLock The realization of .
Automatic release
Automatic release refers to after locking , After the execution of business logic, the lock needs to be closed automatically . In front of Redisson We need to manually call unlock() To release the lock held .
Of course Redisson It also provides the function of timeout release , Under normal circumstances, the lock must be released after the completion of business execution , The next request for the same lock can continue to be processed .
The most common problem with manually releasing resources is forgetting to release , So in JDK7 Introduced in try-with-resources To release resources automatically , I believe everyone is familiar with .
So when we encapsulate , Try not to let the user release it manually , Reduce the probability of error . For those with results, we can use Supplier To deliver your logic , For those that do not return results, you can use Runnable To deliver your logic .
/*** Lock* @param key lock Key* @param waitTime Try to lock , Waiting time (ms)* @param leaseTime Failure time after locking (ms)* @param success The logic of successful lock execution* @param fail Logic of lock failure execution* @return*/<T> T lock(String key, int waitTime, int leaseTime, Supplier<T> success, Supplier<T> fail);
Use :
String result = distributedLock.lock("1001", 1000, () -> {System.out.println(" Came in ....");try {Thread.sleep(1000);} catch (InterruptedException e) {e.printStackTrace();}return "success";}, () -> {System.out.println(" Locking failed ....");return "fail";});
Disaster recovery
Another issue to note is the availability of locks , In case the corresponding Redis Something is wrong. , This time to lock is bound to fail , If nothing is done , It will affect normal business operations , Make the business unavailable .
In addition to realizing Redis Outside the lock of , Other locks can be implemented , Like database locks . When Redis When a lock is not available, it is demoted to a database lock , Although performance has an impact , But it doesn't affect the business .
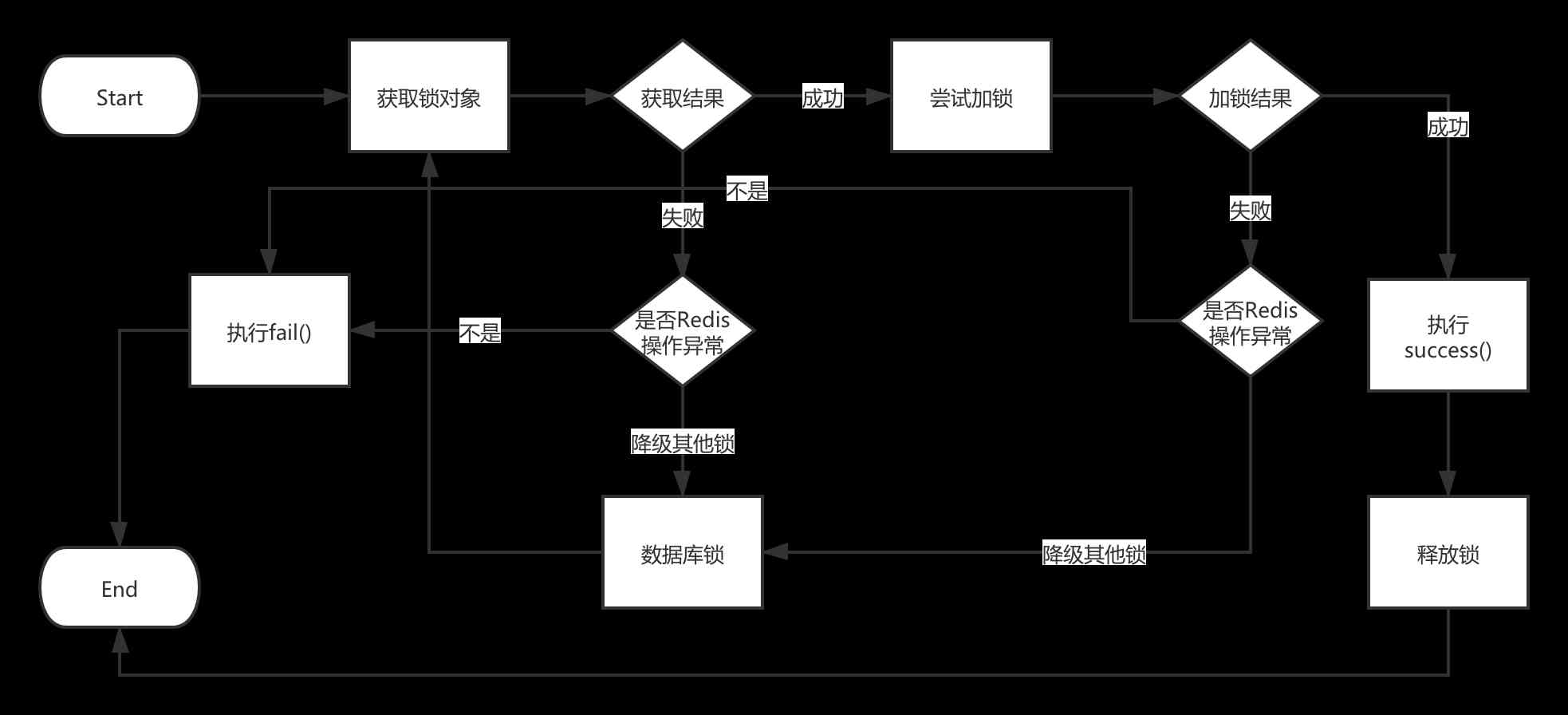
If the database lock is not available ( Digression : It's very unlikely that everything will be available ), It's better to let business operations fail . Because we use the lock scene , It must be to prevent problems caused by concurrent scenarios , If the lock is not available , You're going to spend abnormally , Let business operations continue , There may be business problems without locking .
Of course, monitoring is also very necessary ,Redis, Database monitoring . When something goes wrong , There's a timely intervention .
Monitoring system
Redis, database ,Zookeeper The monitoring of these middleware supporting distributed implementation is definitely necessary . Another monitoring is the fine-grained monitoring of the lock action .
For example, the time to lock , Time to release lock , Time to execute business in a lock , Lock concurrency , Number of executions , The number of lock failures .
These data indicators are very important , It can help you find problems in time . such as 10 Hundreds of lock failures per second , All demoted to database locks , This is when you get an alert , It's easy to see Redis Something is wrong. , Timely solution .
The way of monitoring is just as casual , Every company is different , You can expose data to Prometheus Grab , You can also integrate Cat Do a good job , As long as you can monitor , Just give an alarm .
About author : Yin Jihuan , Simple technology enthusiasts ,《Spring Cloud Microservices - Full stack technology and case analysis 》, 《Spring Cloud Microservices introduction Actual combat and advanced 》 author , official account Ape world Originator .
I have compiled a complete set of learning materials , Those who are interested can search through wechat 「 Ape world 」, Reply key 「 Learning materials 」 Get what I've sorted out Spring Cloud,Spring Cloud Alibaba,Sharding-JDBC Sub database and sub table , Task scheduling framework XXL-JOB,MongoDB, Reptiles and other related information .

版权声明
本文为[Yin Jihuan]所创,转载请带上原文链接,感谢
边栏推荐
- Elasticsearch database | elasticsearch-7.5.0 application construction
- High availability cluster deployment of jumpserver: (6) deployment of SSH agent module Koko and implementation of system service management
- Don't go! Here is a note: picture and text to explain AQS, let's have a look at the source code of AQS (long text)
- GDB除錯基礎使用方法
- 10 easy to use automated testing tools
- (1) ASP.NET Introduction to core3.1 Ocelot
- Calculation script for time series data
- 深度揭祕垃圾回收底層,這次讓你徹底弄懂她
- 采购供应商系统是什么?采购供应商管理平台解决方案
- PN8162 20W PD快充芯片,PD快充充电器方案
猜你喜欢
随机推荐
Elasticsearch database | elasticsearch-7.5.0 application construction
Aprelu: cross border application, adaptive relu | IEEE tie 2020 for machine fault detection
“颜值经济”的野望:华熙生物净利率六连降,收购案遭上交所问询
条码生成软件如何隐藏部分条码文字
CCR炒币机器人:“比特币”数字货币的大佬,你不得不了解的知识
Asp.Net Core學習筆記:入門篇
Network security engineer Demo: the original * * is to get your computer administrator rights! 【***】
从海外进军中国,Rancher要执容器云市场牛耳 | 爱分析调研
速看!互联网、电商离线大数据分析最佳实践!(附网盘链接)
合约交易系统开发|智能合约交易平台搭建
DevOps是什么
《Google軟體測試之道》 第一章google軟體測試介紹
git rebase的時候捅婁子了,怎麼辦?線上等……
Network programming NiO: Bio and NiO
Not long after graduation, he earned 20000 yuan from private work!
ipfs正舵者Filecoin落地正当时 FIL币价格破千来了
Skywalking series blog 1 - install stand-alone skywalking
中国提出的AI方法影响越来越大,天大等从大量文献中挖掘AI发展规律
Filecoin的经济模型与未来价值是如何支撑FIL币价格破千的
It's so embarrassing, fans broke ten thousand, used for a year!