当前位置:网站首页>What is information security? What is included? What is the difference with network security?
What is information security? What is included? What is the difference with network security?
2022-07-05 23:59:00 【Xingyun housekeeper】
In life, we often hear that we need to protect our own or enterprise information security . What exactly is information security ? What content does information security contain ? What's the difference with network security ? Today, let's take a closer look at .
What is information security ?
Information security is defined as follows : Technology established and adopted for data processing system 、 Management security , To protect computer hardware 、 Software 、 Data is not destroyed by accidental and malicious reasons 、 Changes and leaks .
What content does information security contain ?
1、 Hardware security : That is, the security of network hardware and storage media . We should protect these hard facilities from damage , Be able to work normally .
2、 software security : That is, computers and their networks r All kinds of software will not be tampered with or destroyed , Not be operated illegally or by mistake , The function will not fail , Not illegally copied .
3、 Running service security : That is, each information system in the network can operate normally and exchange information through the network . Through the monitoring of the operating conditions of various equipment in the network system , If unsafe factors are found, it can alarm in time and take measures to change the unsafe state , Ensure the normal operation of the network system .
4、 Data security : That is, the security of existing and circulating data in the network . To protect the data in the network from tampering 、 Illegal addition and deletion 、 Copy 、 Decrypt 、 Show 、 Use, etc . It is the most fundamental purpose to ensure network security .
What is the difference between information security and network security ?
Information security is mainly about the security of computer systems and the protection of various protocols , As long as there are some relevant signs in the system that can threaten information security , Information security will provide overall security protection . and Network security It is aimed at the security of computers in the network environment , The devices for information security and network security are different , The emphasis of the two is also different , They all have their own advantages .
Knowledge development : Several measures for enterprises to improve information security
1、 Strengthen the management of office environment and physical security , Install anti-virus software uniformly ;
2、 Beware of phishing emails , Important matters should be verified and confirmed ;
3、 Set complex passwords , And replace it regularly ;
4、 Protect your privacy , Guard against telecommunications fraud ;
5、 Do a good job of data backup , Implement data security measures ;
6、 Pay attention to the safety protection measures of mobile terminals such as mobile phones ;
7、 Protect your personal information assets during business trips ;
8、 Comply with laws, regulations and safety policies .
边栏推荐
- el-cascader的使用以及报错解决
- 用列錶初始化你的vector&&initializer_list簡介
- Breadth first search open turntable lock
- DEJA_ Vu3d - cesium feature set 055 - summary description of map service addresses of domestic and foreign manufacturers
- Single merchant v4.4 has the same original intention and strength!
- Open3D 点云随机添加噪声
- 如何获取localStorage中存储的所有值
- [binary search tree] add, delete, modify and query function code implementation
- C reflection and type
- What are the functions of Yunna fixed assets management system?
猜你喜欢
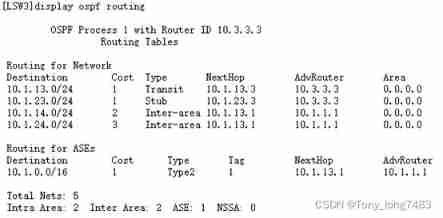
NSSA area where OSPF is configured for Huawei equipment
openssl-1.0.2k版本升级openssl-1.1.1p

Spire. PDF for NET 8.7.2
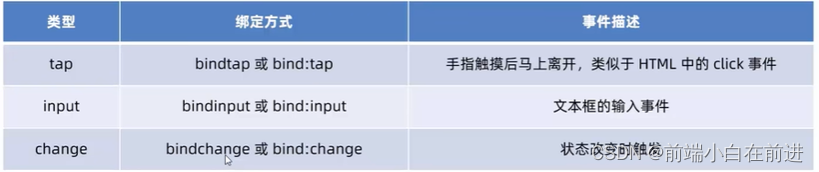
Wechat applet -- wxml template syntax (with notes)
![[binary search tree] add, delete, modify and query function code implementation](/img/38/810a83575c56f17a7a0ed428a2e02e.png)
[binary search tree] add, delete, modify and query function code implementation
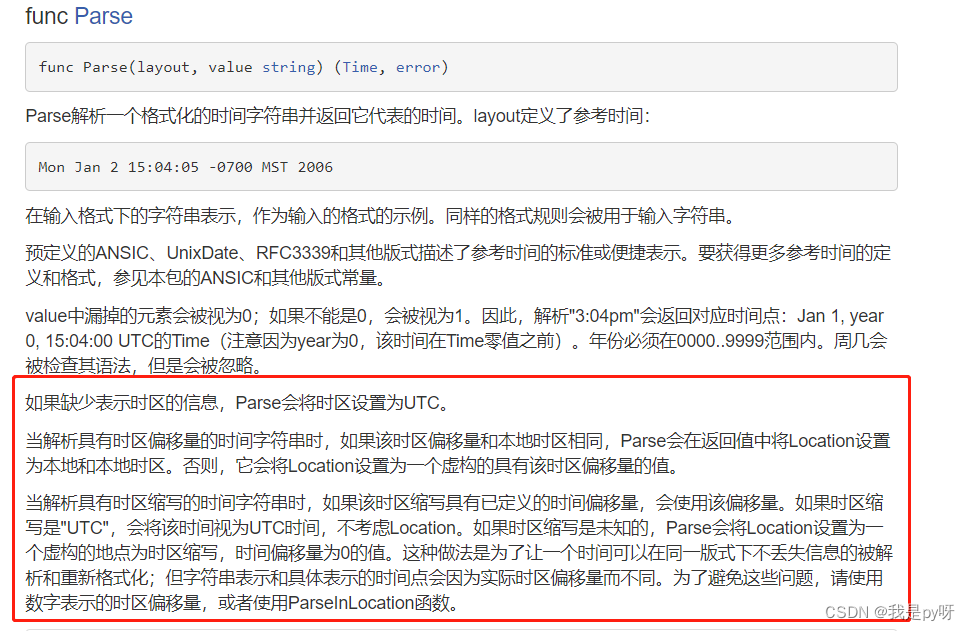
The difference of time zone and the time library of go language
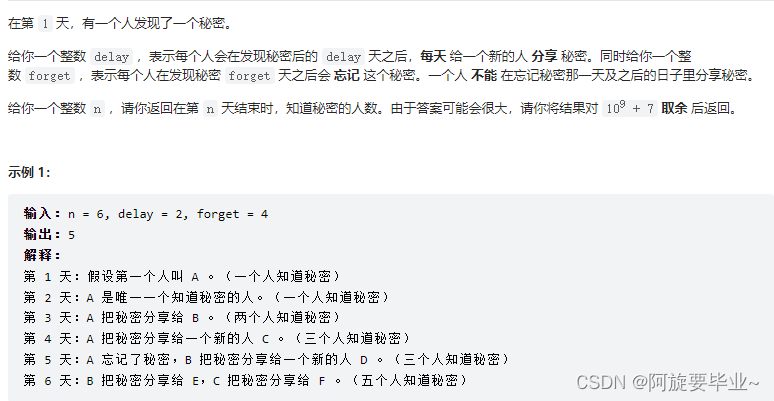
20220703 周赛:知道秘密的人数-动规(题解)
认识提取与显示梅尔谱图的小实验(观察不同y_axis和x_axis的区别)
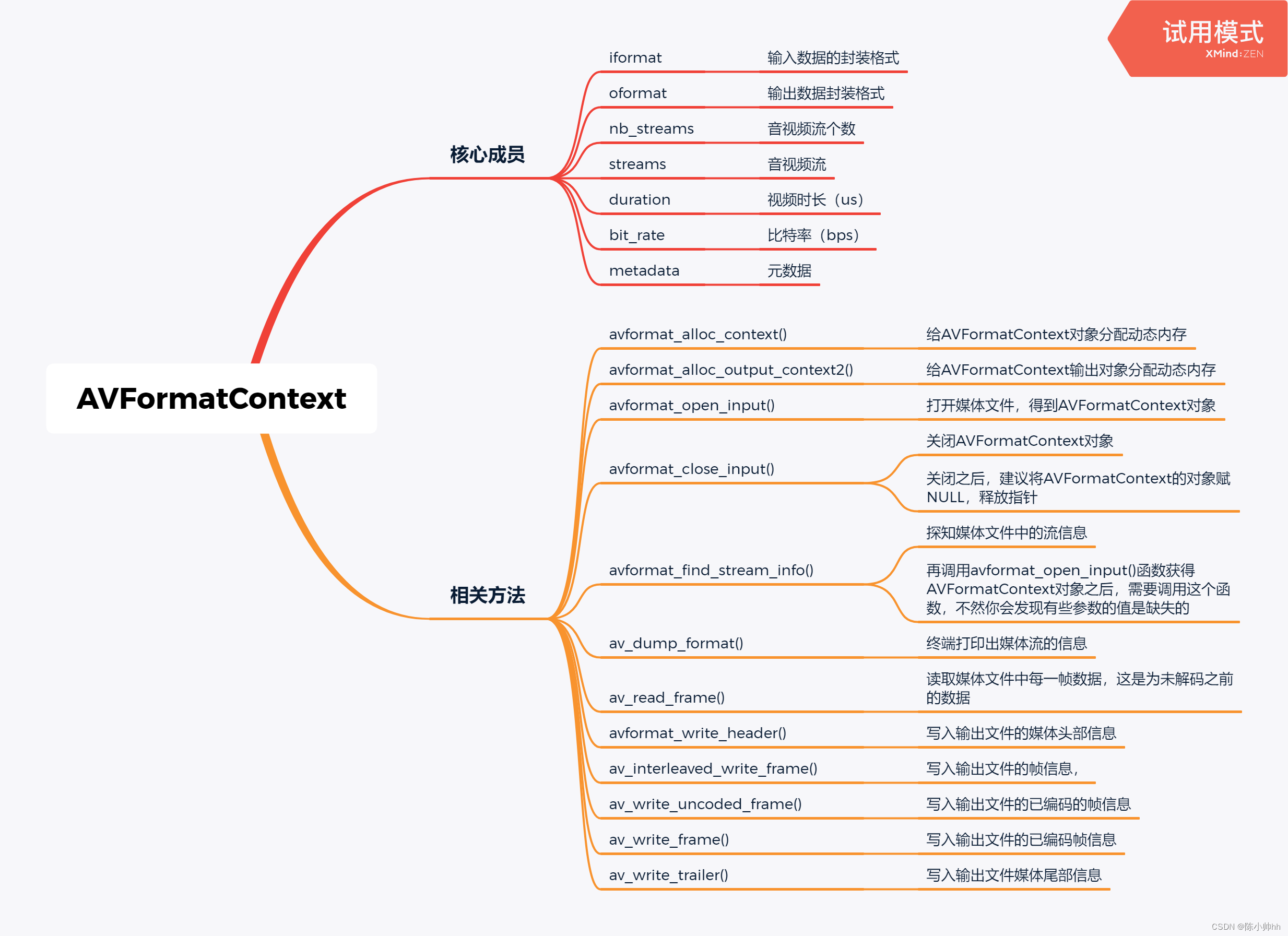
FFMPEG关键结构体——AVFormatContext
Bao Yan notes II software engineering and calculation volume II (Chapter 13-16)
随机推荐
openssl-1.0.2k版本升级openssl-1.1.1p
Make a short video clip number of we media film and television. Where can I download the material?
14 MySQL view
[Luogu p3295] mengmengda (parallel search) (double)
PV静态创建和动态创建
Bao Yan notebook IV software engineering and calculation volume II (Chapter 8-12)
【NOI模拟赛】Anaid 的树(莫比乌斯反演,指数型生成函数,埃氏筛,虚树)
Convert Chinese into pinyin
20220703 week race: number of people who know the secret - dynamic rules (problem solution)
GFS分布式文件系統
14 MySQL-视图
Laser slam learning record
C file and folder operation
Wechat applet -- wxml template syntax (with notes)
CloudCompare&PCL 点云随机添加噪声
There is no network after configuring the agent by capturing packets with Fiddler mobile phones
18. (ArcGIS API for JS) ArcGIS API for JS point collection (sketchviewmodel)
关于结构体所占内存大小知识
DEJA_ Vu3d - cesium feature set 055 - summary description of map service addresses of domestic and foreign manufacturers
Biased sample variance, unbiased sample variance