当前位置:网站首页>Transport layer protocol ----- UDP protocol
Transport layer protocol ----- UDP protocol
2022-07-05 23:54:00 【Key knocker of shubihu】
Here's the catalog title
Transport layer
Talk about port number again
1. effect : It's actually an identifier , Used to distinguish different processes in the application layer .
But in communication , The port number is very important . A five tuple information is a necessary information in communication , The port number accounts for two , The success of a communication , Five tuples are indispensable , Therefore, you must know both the source port number and the opposite port number .
2. Representation of port number : The port number is represented by 16 Bit by bit , That is to say 2 Bytes , The scope of identification is 0~65535.
among : There are different divisions for different intervals .
- Be familiar with port number :0~1023. stay IANA( Internet address code distribution organization ) These port numbers are assigned to TCP\IP Some important application protocols in the architecture .( for example :FTP The port number of the protocol is 20/21,HTTP The port number of the protocol is 80,HTTPS The port number of the protocol is 443,DNS The port number of the protocol is 53 And so on. )
- Registration port number :1024~49151. Use for applications that are not familiar with port numbers . And if you want to use these port numbers , Must be in IANA Go up and register according to the prescribed procedures , Prevent mixing .
- Short port number :49152~65535. Left to the customer process for a short time . When a customer communicates , The system will automatically assign an unused port number to the customer in this data ( This is what we did before tcp Socket programming and udp Socket programming , Reason for not binding port number to client ). When the server process receives the message sent by the client process , We know the dynamic port number used by the client process . And after the communication , This port number can be used by other customers in the future .
Be careful : The port number only has local meaning , Just to identify the processes of the application layer of this computer , And on the Internet , It doesn't matter if you have the same port number in different computers .
3. Except for the port number , In fact, there is an agreement number 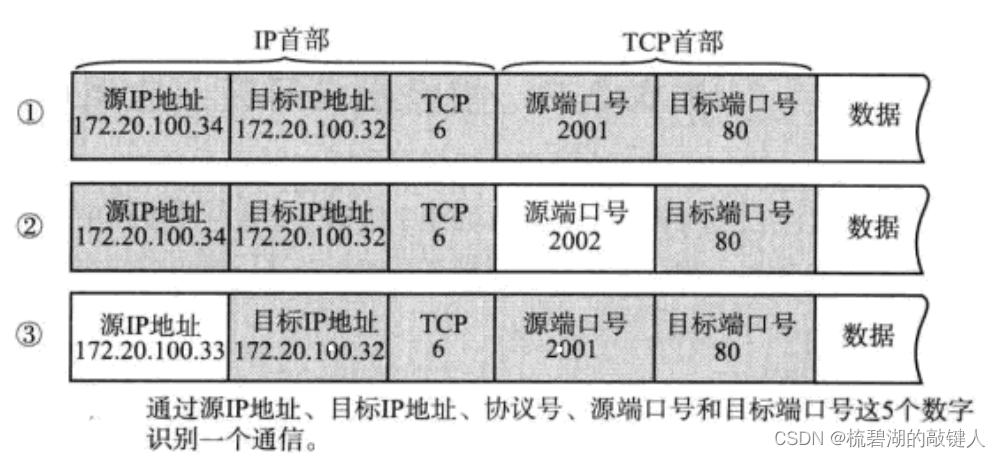
Pass the above figure , You can see it ,ip In addition to the source ip Address and destination ip Out of address , One more TCP6, And this TCP6 Medium 6 Namely TCP Protocol fields for .( namely ,6 Namely tcp The agreement number of )
And for UDP agreement , Its agreement number is actually 17.
You can see from the above figure that , Port number in ip Duan disappeared , And in the tcp In the datagram , Therefore, the port number exists between the application layer and the transport layer , For the agreement number , It exists between the transport layer and the network layer .
4. Reuse of sender and reuse of receiver
Here's the picture :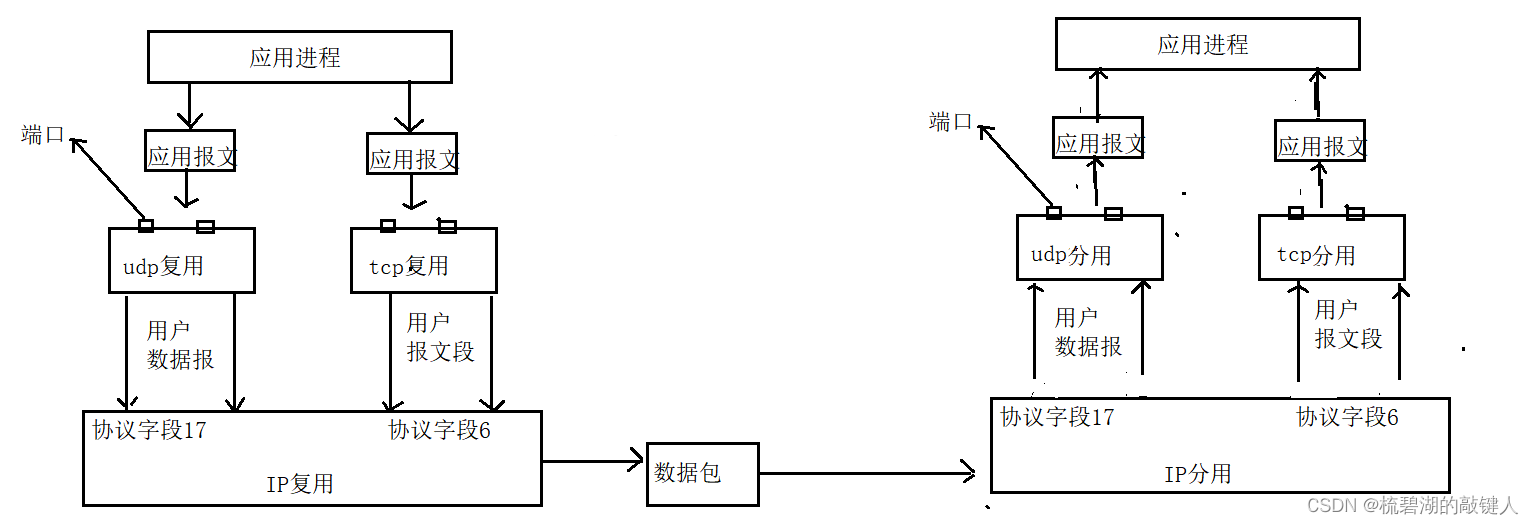
among : For the picture , On the left is the sender , On the right is the receiver , The sender multiplexes the data according to the transmitted protocol , The receiving party divides the data according to the received data , Finally get the result you want .
Know the well-known port number
above , Some well-known port numbers have been introduced , In fact, there are many , Many of the port numbers we often use are as follows :
- ssh The server :22 port
- ftp The server :21 port
- telnet The server :23 port
- http The server :80 port
- https The server :443 port
There are still a lot of it , We can query the well-known port number through this command :cat/etc/services
The query results are as follows :
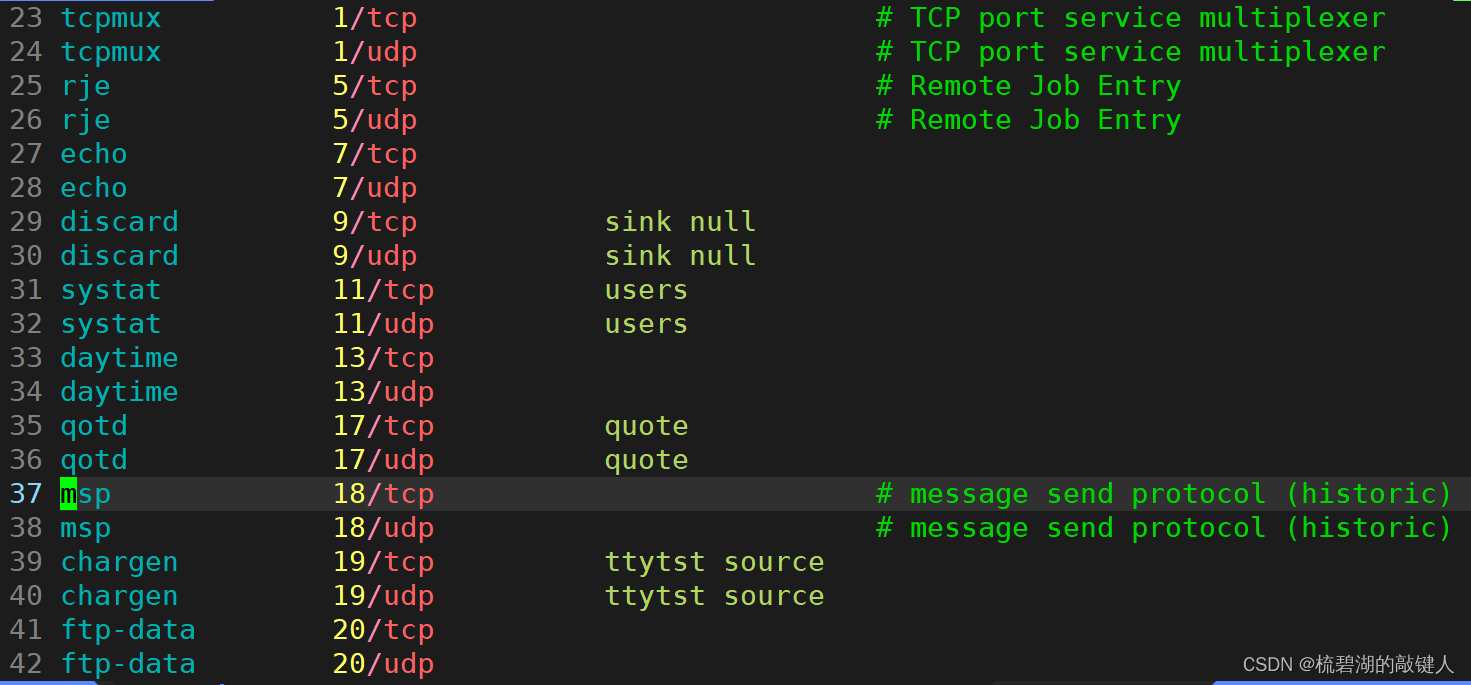
therefore , If we want to write a program to use the port number , We should try our best to avoid using the fixed port number of others , Prevent conflicts .
Two questions
1. A process can bind How many port numbers ?
answer : A process can bind multiple port numbers .
reason : Because multiple file descriptors can be opened in one process , And each file descriptor corresponds to a port number , So a process can bind multiple port numbers .
2. Whether a port number can be used by multiple processes bind Well ?
answer : A port number cannot be bound by multiple processes . namely : A port number can only be bound by one process .( But the above also has some special points , It is a parent process, which is bound with a port number , But he also fork A sub process comes out , This subprocess also has this port number . So in this way, multiple processes are bound to the same port number . however , Different processes that are not parent-child processes , It is absolutely impossible to bind the same port number )
reason : Because the binding of port number only occurs on the server , In general , The server has multiple ports , One port only corresponds to one service . And most of the time ( With the exception of the parent-child process mentioned above ), A service corresponds to a process , There are no two processes serving a port number at the same time .
netstat and pidof
1.netstat command
①: grammar :netstat [ Options ]
②: function : Check the network status .
Common options :
- -n: Reject alias , Can display all of the numbers into numbers .
- -l : Only those with LISTEN( Monitoring ) Service status .( be based on TCP signal communication )
- -p: Displays the name of the program that established the relevant connection .
- -t : Show only tcp Related options .
- -u: Show only udp Related options .
- -a: Show all options , Default not to show LISTEN dependent .
Examples are as follows :
see tcp process 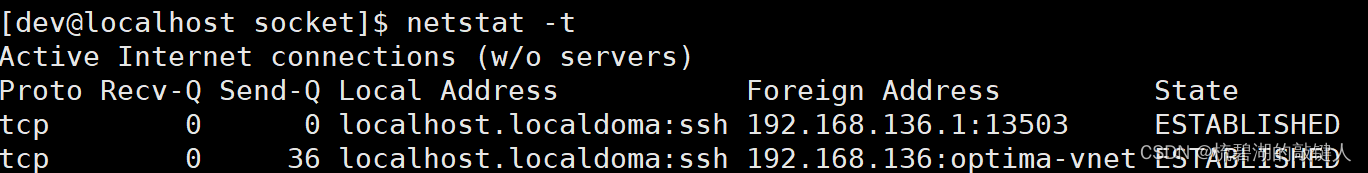
see udp The process is as follows :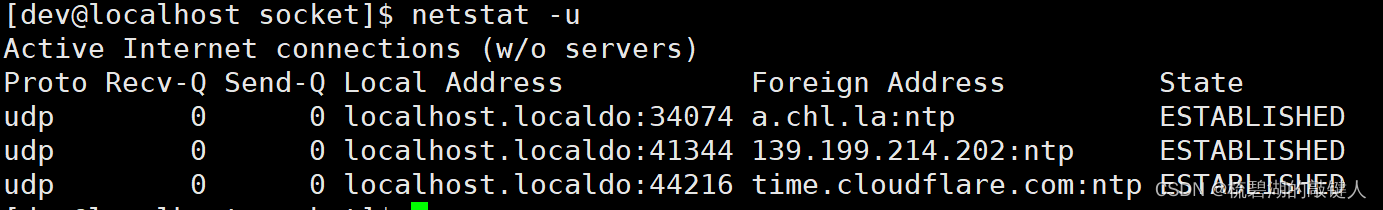
among : Above picture
①Proto: It represents the protocol type .
②Local Address: It means the source side ip Address and source port number .
③Foreign Address: It means the destination ip Address and destination port number .
④State: Indicates the current established state .
3.pidof command
① grammar :pidof [ Process name ].
② function : View by process name id.
for example :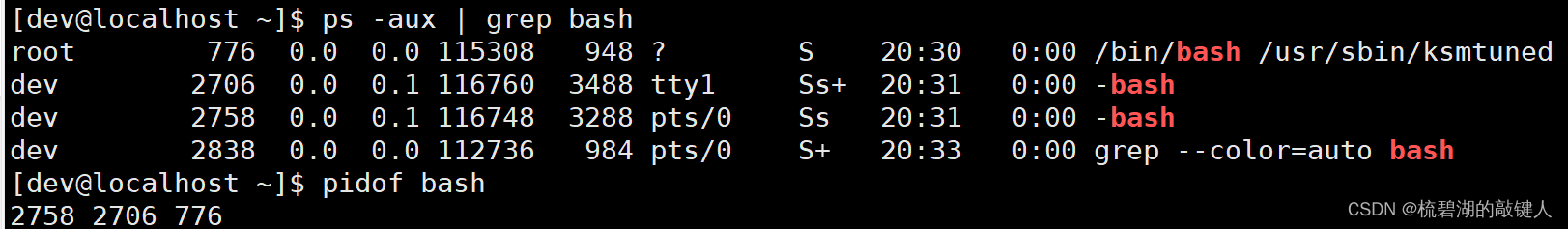
Upper figure , adopt bash, Check their pid Number .
UDP agreement
UDP Protocol segment format
Please look at the chart below. :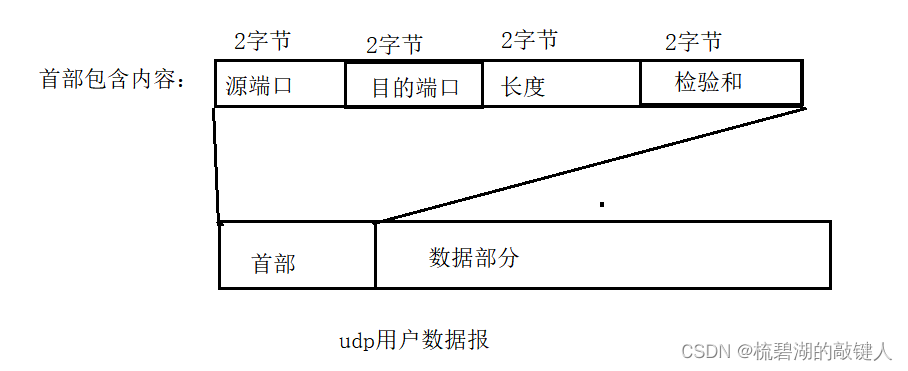
For one udp Simulation diagram of user datagram , among udp The bytes occupied by the header are 8 byte , And it contains four components : Source port , Destination port , length , Inspection and . Every possession 2 Bytes .
among :
- Source port : Where does the data come from .
- Destination port : Where does the data go .
- length : Length of data .( The whole datagram contains the first )
- Inspection and : If udp Message check and error , Will discard the message .
The internal structure is as follows :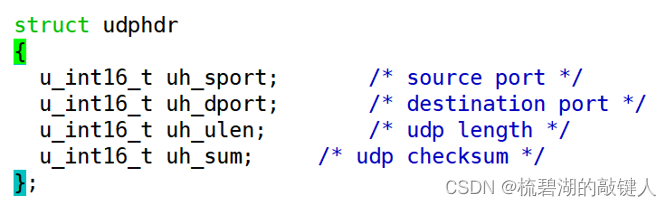
It means these four parts .
UDP Characteristics
UDP The process of transmission , Similar to sending a letter , So it has the following characteristics :
1. There is no connection : When communicating with each other , No connection needed ( Just know each other's addresses ), Just send data directly .( Just like sending a letter , I only know your address , I can send you a letter )
2. Support one-to-one , One to many , Many to one and many to many interactive communication : Use udp In the LAN of the Protocol , Any host can send broadcast information to other main sentences ( That is, all hosts in the LAN can receive ), You can also send multicast to one of the multicast groups ( Multicast group is a group composed of several hosts under the same LAN ), Unicast can also be sent to one of the hosts .
3. The application of direct packet delivery layer : The datagram sent by the sender to the transmission layer , Use UDP The agreement will directly add a UDP The first one is sent .
Be careful :
- Application layer to UDP How long data ,udp Will not split , Will not merge , Add directly udp The first part is then sent directly .
- If the sender calls once sendto, And the one sent is 100 Bytes . Then the corresponding end should only call once recvfrom, Once received 100 Bytes , Instead of cycling ten times , Every time I receive 10 Bytes .
- We noticed that , We talked about , Two bytes are used to save one udp Length of datagram , So one udp The maximum byte length of a datagram is 64k, And it also contains the first . therefore , For the data part , When we transmit , Try to be as small as possible 64k, If the data we want to transmit is greater than 64k, Then you need to subcontract manually at the application layer , Send... Multiple times , And manually assemble at the receiving end .( Based on strict whole transmission , That is, if the buffer of the receiver is too small , There is no room for the data sent by the sender , Then this data will be discarded )
4. Do your best to deliver , It's unreliable : If in the process of transmission , The user datagram receives interference and generates error code , The receiving party will act in accordance with udp Header field calibration information , Check the error code , If there is a bit error , The side discards only this datagram , And nothing else ( Because there is no retransmission mechanism , There is no confirmation mechanism ).
And so udp About the buffer :
- udp There is no real buffer , call sendto Will be handed over directly to the kernel , The kernel transmits the data to the network layer protocol for subsequent transmission .
- udp With buffer , The function of this buffer cannot guarantee the received udp Message sequence and sending udp Report in the same order , And if the buffer is full , Then the newspaper coming later will be discarded .
- udp Of socket, Not only can you read , You can also write , It's a full duplex communication socket.
among :udp The test and error detection method of is binary summation algorithm .
Binary summation algorithm :
①: The sender organizes the data , Set the check and position of the header field to 0, And then from the 0 Bytes ( Including the first , Is the first byte of the first part ) Start to reverse sum each byte , beyond 16 Bit , Then cut off the high order , Let it be low 16 Bits continue to sum .
②: After completion, fill the checksum into the inspection sum field .
③: The receiver receives the data , Sum the data in reverse code from beginning to end , Now , If the data is correct , So the end result should be 0.
UDP The protocol corresponding to the application layer
- NFS: Network file system .
- TFTP: Simple file transfer protocol .
- DHCP: Dynamic Host Configuration Protocol .
- BOOTP: Boot protocol .( Used for setting startup without disk )
- DNS: Domain name resolution .
Of course , It also includes writing by yourself udp The protocol customized at the application layer when the program .
边栏推荐
- 零犀科技携手集智俱乐部:“因果派”论坛成功举办,“因果革命”带来下一代可信AI
- QT a simple word document editor
- 20220703 week race: number of people who know the secret - dynamic rules (problem solution)
- How to improve eloquence
- Why use weak pointers for delegation- Why use weak pointer for delegation?
- CloudCompare&PCL 点云随机添加噪声
- 总结了 800多个 Kubectl 别名,再也不怕记不住命令了!
- Senparc.Weixin.Sample.MP源码剖析
- 2022.6.20-6.26 AI industry weekly (issue 103): new little life
- Spire. PDF for NET 8.7.2
猜你喜欢
随机推荐
Online yaml to CSV tool
Spire.PDF for NET 8.7.2
Zero rhino technology joined hands with the intelligence Club: the "causal faction" forum was successfully held, and the "causal revolution" brought the next generation of trusted AI
【SQL】各主流数据库sql拓展语言(T-SQL 、 PL/SQL、PL/PGSQL)
4点告诉你实时聊天与聊天机器人组合的优势
[day39 literature extensive reading] a Bayesian perspective on magnetic estimation
Zhuan: in the future, such an organization can withstand the risks
14 MySQL view
Redis high availability - master-slave replication, sentinel mode, cluster
15 MySQL stored procedures and functions
TS type declaration
Tips for using pads router
PADS ROUTER 使用技巧小记
GFS distributed file system
21.PWM应用编程
[Luogu cf487e] tours (square tree) (tree chain dissection) (line segment tree)
7.5 装饰器
【二叉搜索树】增删改查功能代码实现
QT a simple word document editor
shardingsphere源码解析