当前位置:网站首页>From the perspective of technology and risk control, it is analyzed that wechat Alipay restricts the remote collection of personal collection code
From the perspective of technology and risk control, it is analyzed that wechat Alipay restricts the remote collection of personal collection code
2022-07-05 12:49:00 【QQ541645121】
Currently on the market Frequent runs 、 gambling 、 Telecommunications fraud and other violations , In these cases , From the perspective of risk control , Personal wechat 、 Alipay's QR code collection code , Undertake an important part of the capital transition . And there must be “ Strong concealment 、 The capital is scattered 、 Difficult supervision, etc ” Salient features , At the same time, it is also given to relevant law enforcement agencies , Bring huge regulatory difficulties . This has also led to the repeated prohibition of the above illegal acts .
Tencent and Alibaba are giant enterprises that undertake social responsibility , We must make a difference in it . Cooperate with regulators , Cut off the capital transition link of these illegal acts from the source or the capital chain .
I think , Known in history “ The strictest supervision !2022 year 3 month 1 The date of , Wechat Alipay personal collection code cannot be used as business collection !” Important reasons for implementation .

Even if , The implementation of these measures is expected , It will be given to many individual operators 、 Personal studio 、 Individual entrepreneurs bring huge collection trouble , But then it must be enforced .
Implementation of measures , Never take into account everyone : Or adapt to change , Or be eliminated .
If the measures are implemented immediately , are you ready ?You can send me a private message to exchange good solutions .
边栏推荐
- How to connect the API interface of Taobao open platform (super detailed)
- 《信息系统项目管理师》备考笔记---信息化知识
- JSON parsing error special character processing (really speechless... Troubleshooting for a long time)
- Introduction to relational model theory
- 奔跑,开路
- 滴滴开源DELTA:AI开发者可轻松训练自然语言模型
- Correct opening method of redis distributed lock
- Distributed solution - Comprehensive decryption of distributed task scheduling platform - xxljob scheduling center cluster
- Simply take stock reading notes (4/8)
- Detailed structure and code of inception V3
猜你喜欢
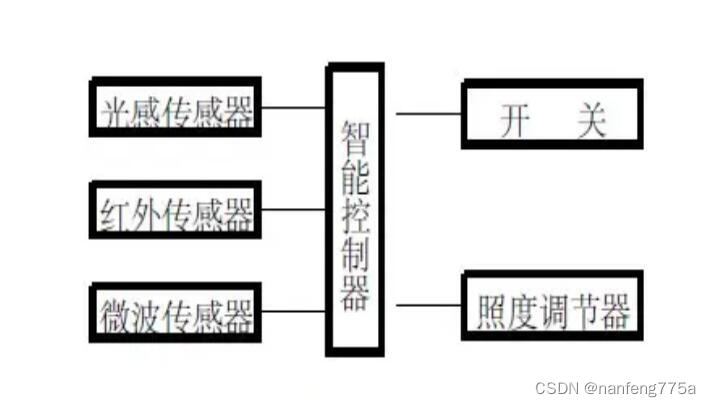
Distance measuring sensor chip 4530a used in home intelligent lighting
The relationship between the size change of characteristic graph and various parameters before and after DL convolution operation
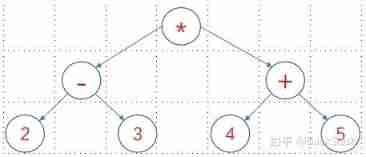
Constructing expression binary tree with prefix expression

JSON parsing error special character processing (really speechless... Troubleshooting for a long time)
Transactions on December 23, 2021
Migrate data from Mysql to neo4j database
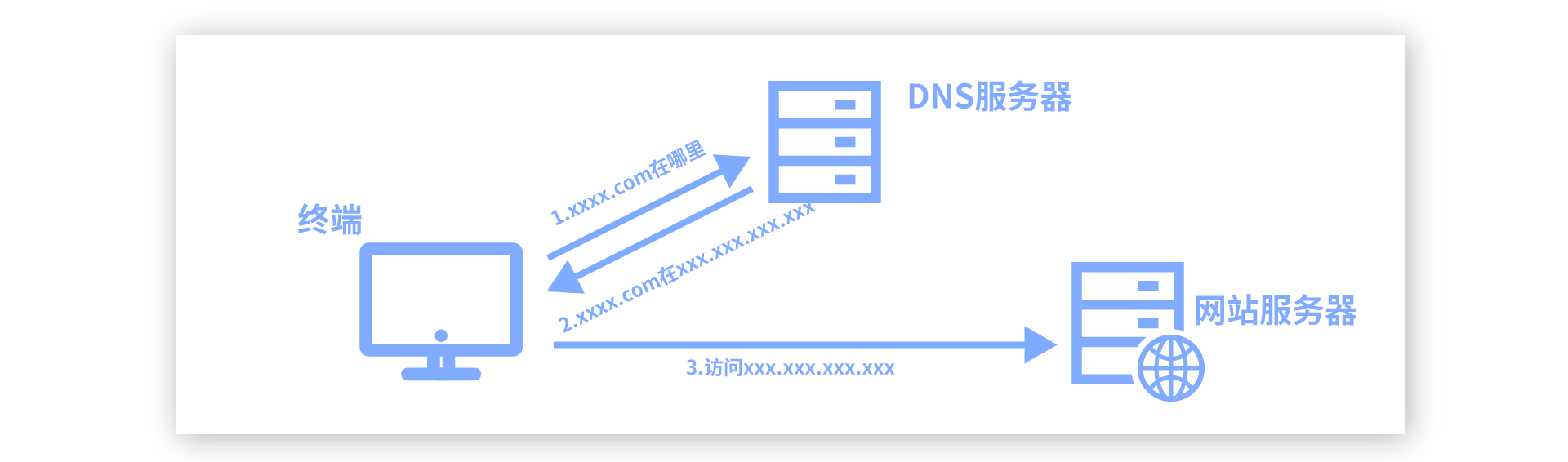
DNS的原理介绍
Notes for preparation of information system project manager --- information knowledge

在家庭智能照明中应用的测距传感芯片4530A
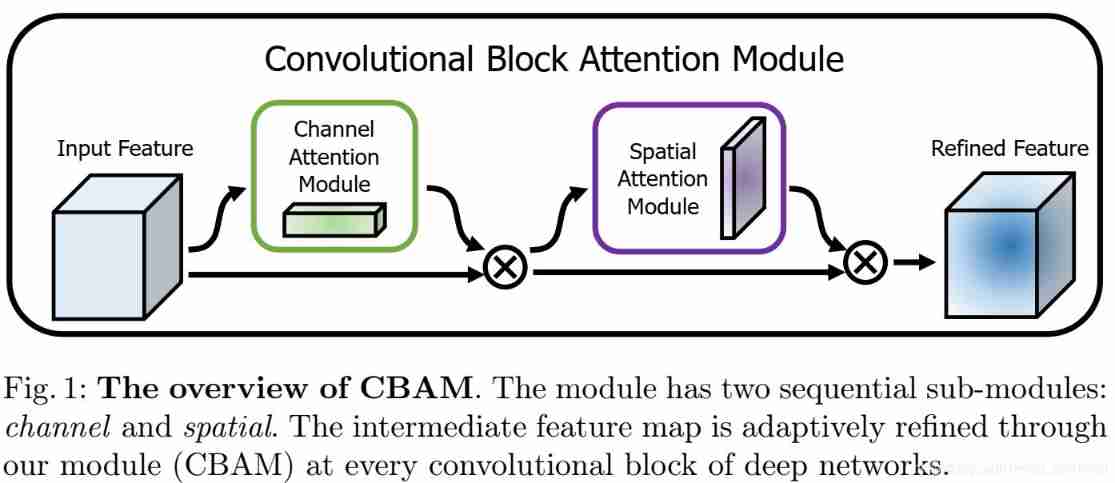
Resnet+attention project complete code learning
随机推荐
C language structure is initialized as a function parameter
Annotation problem and hidden Markov model
非技术部门,如何参与 DevOps?
Introduction to relational model theory
10 minute fitness method reading notes (2/5)
Common commands and basic operations of Apache Phoenix
Kotlin function
Free testing of Taobao tmall API order and flag insertion remark interface
Transactions from December 29, 2021 to January 4, 2022
Distributed solution - distributed lock solution - redis based distributed lock implementation
Research: data security tools cannot resist blackmail software in 60% of cases
A possible investment strategy and a possible fuzzy fast stock valuation method
ZABBIX customized monitoring disk IO performance
Pinduoduo flag insertion remarks API
Array cyclic shift problem
ZABBIX agent2 monitors mongodb nodes, clusters and templates (official blog)
【云原生】Nacos-TaskManager 任务管理的使用
Knowledge representation (KR)
[superhard core] is the core technology of redis
Storage Basics