当前位置:网站首页>Hcip first day notes sorting
Hcip first day notes sorting
2022-07-07 09:49:00 【Yunyinqi mountain】
HCIA---- Huawei junior network engineer certification
HCIP---- Senior Network Engineer under Huawei certification system
Abstract language --- code
code --- Binary system
Binary system --- Electrical signals
Process electrical signals
agreement , standard , application , service
OSI( Open system interconnection ) Reference model ---OSI/RM---ISO---1979 year
application layer --- Provide various application services , Convert abstract language into code , Provide an interface for others to interact
The presentation layer --- Convert the encoding to binary
The session layer --- Maintain session links between web applications and web servers
Transport layer --- Realize end-to-end communication --- Port number ---0 - 65535--- among 0 It is not used as the port number of the transport layer , therefore , The real value range of the port number is 1 - 65535--- among 1 - 1023 It's called a well-known port number ---SPORT,DPORT
The network layer --- Use IP Address realizes logical addressing between hosts ---SIP,DIP
obtain DIP Address method :
1. Know the server directly IP Address
2. Access the server through the domain name
3. Access the server through the application
4. radio broadcast
Data link layer --- Control physical hardware , Convert binary to electrical signal --- In Ethernet , The data link layer needs to pass MAC Address for physical addressing ---48 Bit binary structure ---1、 The only global ;2、 use the same pattern ---SMAC,DMAC
obtain DMAC Methods ---ARP agreement --- Address resolution protocol
positive ARP--- adopt IP The address for MAC Address
First , The host sends... In the form of broadcast ARP request , Based on the known IP Address , request MAC Address . All devices in the broadcast domain can receive request packets , All devices that receive packets will record the source in the packet IP Address and source MAC The correspondence of the address is related to the local ARP The cache table . after , Look at the request IP Address , If it's local IP Address , Will be performed ARP The reply , Local MAC Address inform . If it's not local IP Address , The packet will be discarded directly , after , When sending data again , Give priority to local ARP Cache table , If there are records in the table , Then the information will be sent directly according to the record , If there is no record , Then send ARP Request package acquisition MAC Address .
reverse ARP--- adopt MAC Address past IP Address
free ARP---1、 Self introduction. ;2、 Detect address conflicts .
The physical layer --- Handle the transmission of electrical signals
TCP/IP Model
TCP/IP Protocol cluster
TCP/IP The standard model --- Four layer model
TCP/IP peer model --- Five layer model
PDU--- Protocol data unit
L1PDU
L2PDU
...
L7PDU
application layer --- The data packet
Transport layer --- Data segment
The network layer --- Data packets
Data link layer --- Data frame
The physical layer --- Bit stream
Encapsulation and de encapsulation
application layer --- There is encapsulation in the application layer , Depending on the application
Transport layer --- Port number ---TCP,UDP
The network layer ---IP Address ----IP
Data link layer ---MAC Address --- Ethernet protocol
The physical layer
TCP/IP The model supports cross layer encapsulation , And in the OSI Not in the middle .--- Cross layer encapsulation is generally used to send information between short-range direct connected devices , It can improve the forwarding efficiency .
1、 Cross four layer packaging ---OSPF
2、 Span three 、 Four layer package
SOF--- Frame header delimiter
DSAP--- Indicate what protocol the upper layer of the device receiving the data frame uses to process the data
SSAP--- Indicates the protocol generated by the upper layer of the device that sends the data frame
Control---1、 Connectionless mode ;2、 Connection oriented pattern --- It can realize the fragment reorganization of data packets
IP Address
IPV4---32 Bit binary structure --- dotted decimal
IPV6---128 Bit binary structure --- It's hexadecimal
Network bit --- The network bits are the same , It means in the same broadcast domain
Host bit --- In the same broadcast domain , Use the host bit to distinguish different hosts
Subnet mask --- Continuous 1 And continuous 0 form ,1 On behalf of network bit ,0 Represents the host bit
A,B,C--- Unicast address --- That is, it can be used as a source IP Address , It can also be a goal IP Address .
A:255.0.0.0
B:255.255.0.0
C:255.255.255.0
D--- Multicast address --- Only as a target IP Address using , Cannot be used as a source IP Address using
E--- Reserved address
A:0XXX XXXX---(0-127)1-126
B:10XX XXXX---128-191
C:110X XXXX---192-223
D:1110 XXXX---224-239
E:1111 XXXX---240-255
unicast --- One to one communication
Multicast --- One to many ( The same multicast group )
radio broadcast --- A pair of all ( All in the broadcast domain )
stay IP In the address space , Part of it IP The address is called private IP Address ( The private network IP Address ), The rest is called public IP Address ( Public network IP Address )--- We habitually use private networks IP The network built by address is called private network , Use the public network IP The network built by address is called public network .--- Private address can be reused , However, uniqueness must be guaranteed within the private network .
A:10.0.0.0-10.255.255.255 amount to 1 individual A Class segment
B:172.16.0.0-172.31.255.255 amount to 16 individual B Class segment
C:192.168.0.0-192.168.255.255 amount to 256 individual C Class segment
special IP Address
1,127.0.0.1-127.255.255.254--- Loopback address
2,255.255.255.255--- Restricted broadcast address --- Only as a target IP Use
3, All the hosts 1---192.168.1.255/24--- Direct address --- Only as a target IP Address using
4, All the hosts 0---192.168.1.0/24--- Network segment ( network address , network number )
5,0.0.0.0---1, No, IP Address ;2, therefore IP Address
6,169.254.0.0/16--- Local link address / Automatic private address
VLSM--- Variable length subnet mask
192.168.1.0/24
192.168.1.00000000---192.168.1.0/25
192.168.1.10000000---192.168.1.128/25
CIDR--- No inter domain routing
Take the same , Go different --- For binary
192.168.0.0/24
192.168.1.0/24
192.168.2.0/24
192.168.3.0/24
192.168.0.0/22---- HYPERNET
172.16.0.0/24
172.16.1.0/24
172.16.2.0/24
172.16.3.0/24
172.16.0.0/22--- Summary
Generation conditions of direct route ---1, Dual interface UP;2, The interface must be configured IP Address
Get unknown route information of network segment
Static routing : Routing entries manually configured by the network administrator
Dynamic routing : All routers run the same routing protocol , after , Routers communicate with each other , Exchange and calculate the routing information of the unknown network segment .
Advantages of static routing ---1, The choice of route is more reasonable ;2, safer ;3, No additional occupation is required Source
shortcoming ---1, Large amount of configuration ;2, Static routing cannot automatically converge based on changes in topology
Basic configuration method of static routing :
Method 1 :[r1]ip route-static 192.168.3.0 24 192.168.2.2---- You need to recursively find the interface
Method 2 :
Extended configuration of static routing
1, Load balancing --- When a router accesses the same target with multiple paths with similar overhead , You can split the traffic and take multiple paths at the same time , Play the effect of superimposing bandwidth .
2, Manual summary --- When a router can access multiple consecutive subnets , If they all pass the same next jump , These network segments can be summarized and calculated , Directly write a static route to the summary network segment , You can reduce the number of routing table entries , Improve forwarding efficiency .
3, Routing black holes --- In summary , If the network segment that does not actually exist in the network is included , It may cause the flow to have no return , Waste link resources .
4, Default route --- A route that does not limit the destination , When looking up the table , If all routes do not match , The default route will be matched .
5, Empty interface routing --- Prevent routing black holes and default routes from meeting and leaving the ring .
1、NULL 0 --- If the outgoing interface of a route points to an empty interface , The datagram matching this route information will be discarded
2、 Matching principle of routing table --- The longest match principle ( The principle of exact match )
6, Floating static routing
边栏推荐
- Netease cloud wechat applet
- **Grafana installation**
- Write VBA in Excel, connect to Oracle and query the contents in the database
- Loxodonframework quick start
- Nested (multi-level) childrn routes, query parameters, named routes, replace attribute, props configuration of routes, params parameters of routes
- Can't connect to MySQL server on '(10060) solution summary
- 12、 Sort
- Main (argc, *argv[]) details
- 小程序实现页面多级来回切换支持滑动和点击操作
- CDZSC_2022寒假个人训练赛21级(2)
猜你喜欢

小程序实现页面多级来回切换支持滑动和点击操作
How to speed up video playback in browser
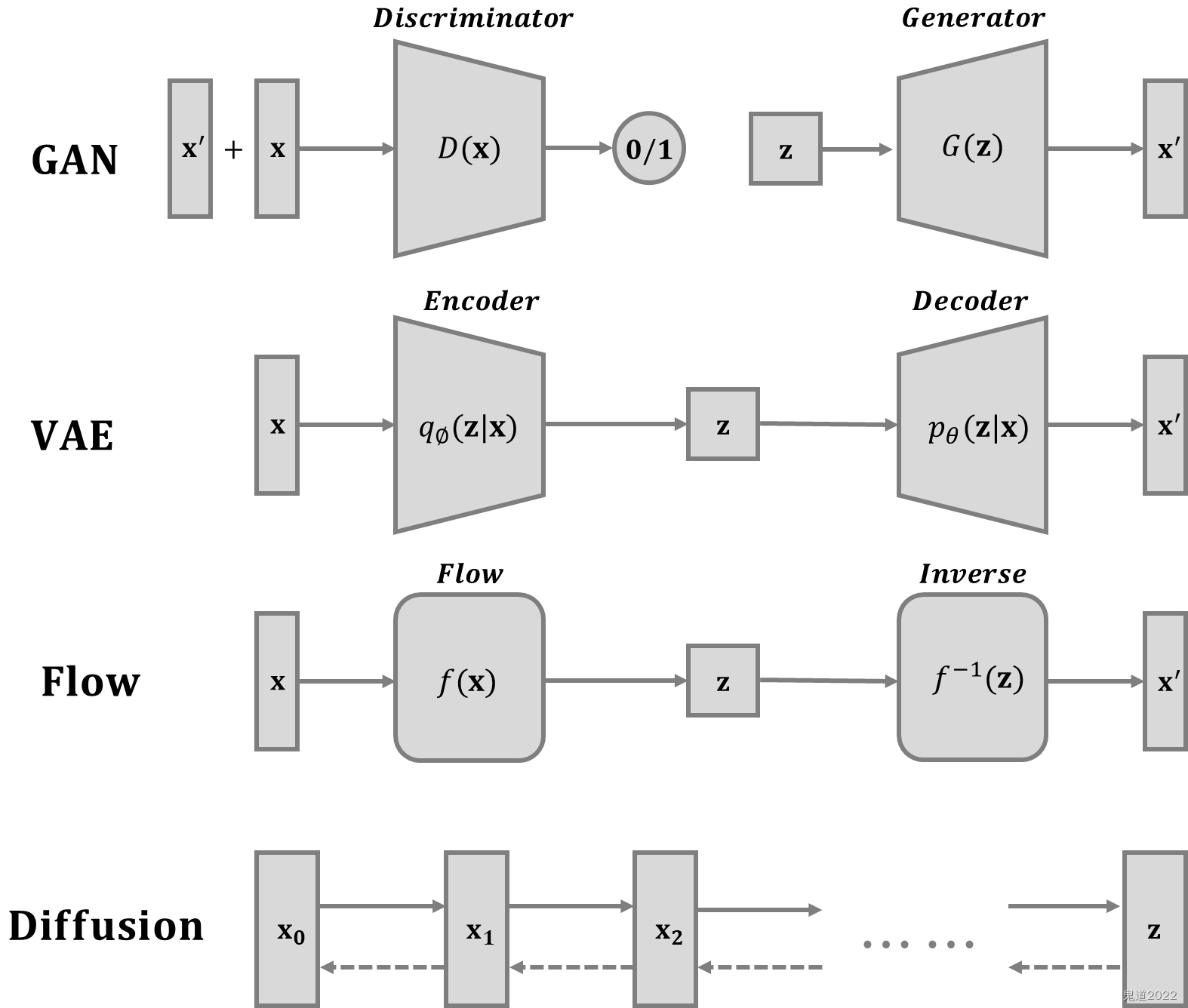
Diffusion模型详解
![[4G/5G/6G专题基础-147]: 6G总体愿景与潜在关键技术白皮书解读-2-6G发展的宏观驱动力](/img/21/6a183e4e10daed90c66235bdbdc3bf.png)
[4G/5G/6G专题基础-147]: 6G总体愿景与潜在关键技术白皮书解读-2-6G发展的宏观驱动力
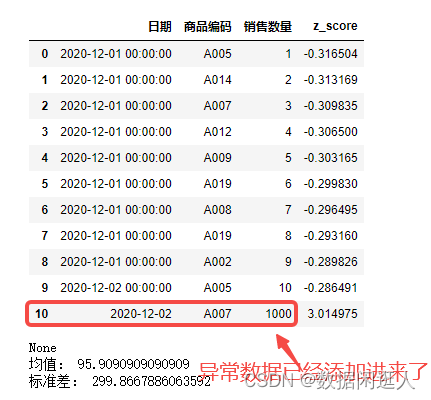
数据建模中利用3σ剔除异常值进行数据清洗

The applet realizes multi-level page switching back and forth, and supports sliding and clicking operations
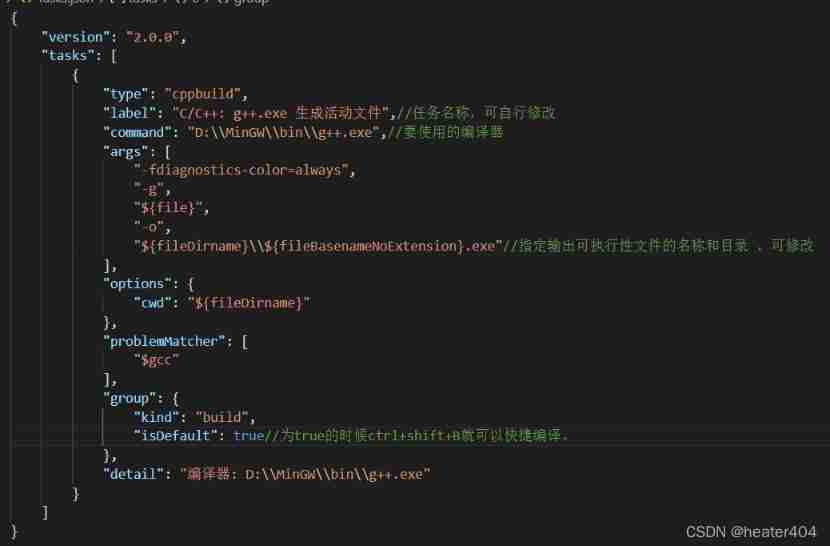
VSCode+mingw64

章鱼未来之星获得25万美金奖励|章鱼加速器2022夏季创业营圆满落幕
Esp8266 uses TF card and reads and writes data (based on Arduino)

How does mongodb realize the creation and deletion of databases, the creation of deletion tables, and the addition, deletion, modification and query of data
随机推荐
Gym - 102219J Kitchen Plates(暴力或拓扑序列)
Communication mode between processes
如何成为一名高级数字 IC 设计工程师(5-3)理论篇:ULP 低功耗设计技术精讲(下)
细说Mysql MVCC多版本控制
How to become a senior digital IC Design Engineer (5-3) theory: ULP low power design technology (Part 2)
Can flycdc use SqlClient to specify mysqlbinlog ID to execute tasks
CDZSC_2022寒假个人训练赛21级(2)
In fact, it's very simple. It teaches you to easily realize the cool data visualization big screen
Unity uses mesh to realize real-time point cloud (II)
小程序实现页面多级来回切换支持滑动和点击操作
Lesson 1: finding the minimum of a matrix
Niuke - Huawei question bank (61~70)
大佬们,有没有遇到过flink cdc读MySQLbinlog丢数据的情况,每次任务重启就有概率丢数
根据热门面试题分析Android事件分发机制(一)
2020浙江省赛
Loxodonframework quick start
[4g/5g/6g topic foundation-146]: Interpretation of white paper on 6G overall vision and potential key technologies-1-overall vision
Difference between process and thread
Upload taro pictures to Base64
20排位赛3