当前位置:网站首页>Natapp intranet penetration
Natapp intranet penetration
2022-07-07 09:44:00 【Not enough to eat】
Intranet through
One 、 Introduce
1. Concept
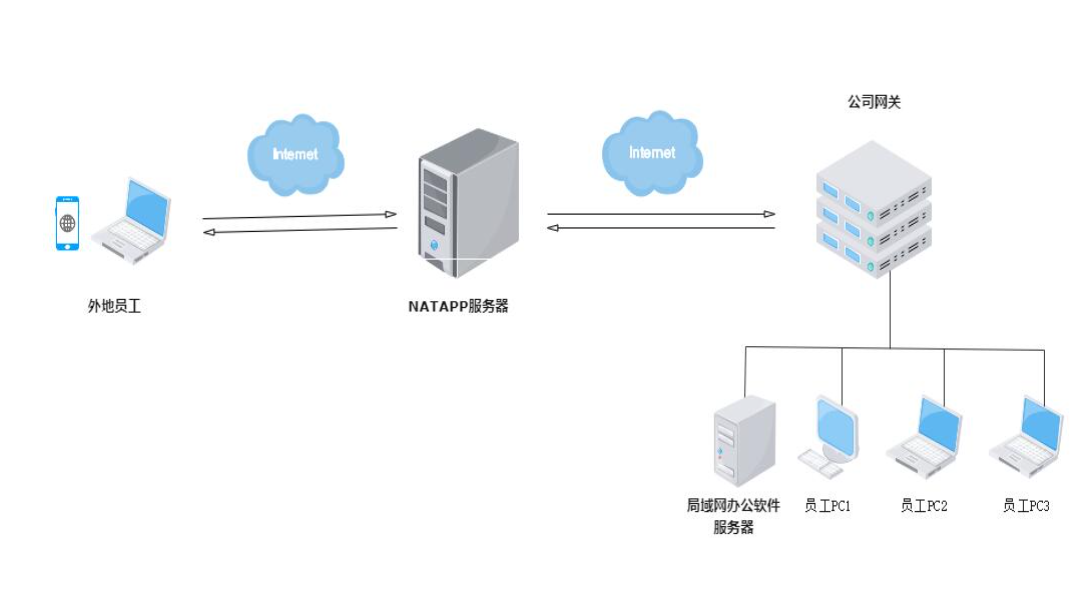
Intranet penetration is simply to put the intranet and extranet through natapp The tunnel opened , Let the data in the intranet be accessible to the Internet . For example, common office software and so on , Usually in the office or at home , Dial up the Internet , In this way, office software can only be accessed in the local LAN , So here comes the question , If it's on a cell phone , Or office workers outside the company , How to access office software ? This requires natapp Intranet penetration tool . function natapp After the tunnel ,natapp Will assign an exclusive domain name / port , Office software is already on the public network , Office workers in the field can enjoy visiting office software anywhere
2. effect
The office software illustrated above
Raspberry pie at home , The server etc. , Remote required ssh management , This is how to get through the server 22 Ports can be remotely accessed ssh Operating the server .
WeChat / Alipay and other local development . Now wechat / Alipay and other applications , The server is required to receive wechat / Callback information sent by Alipay , However, if you develop programs locally , You have to upload it to the server in real time , To support wechat / Callback information of Alipay , If used natapp Intranet penetration Software , Set the callback address to natapp Address provided , The callback data is immediately passed back to the local , In this way, it is very convenient to debug the program in real time locally , There is no need to constantly upload servers and other cumbersome and meaningless steps .
Some enterprise internal databases , Due to safety and other reasons , Unwilling to put it on the cloud server , You can put the database locally in the office , And then through natapp Of tcp Tunnel mapping , This ensures safety , And ensure that the public network can be accessed normally .
Some development board monitoring and other information , Each equipment runs a tunnel , It is convenient to manage and monitor the operation of various devices .
Some local Games , Want to play online with good friends , A command runs natapp You can realize online games .
Two 、 How to perform intranet penetration
1. Buy tunnels
Tunnel technology : A way of transferring data between networks by using the infrastructure of the Internet , Including data encapsulation 、 The whole process including transmission and unpacking . Using tunnel data ( Or load ) It can be data frames or packets of different protocols .
There are many free platforms for intranet penetration , What we use here is NATAPP website :NATAPP- Intranet through be based on ngrok Domestic high-speed intranet mapping tool
Enter the official website to register , Click to buy tunnel , Buy free tunnels
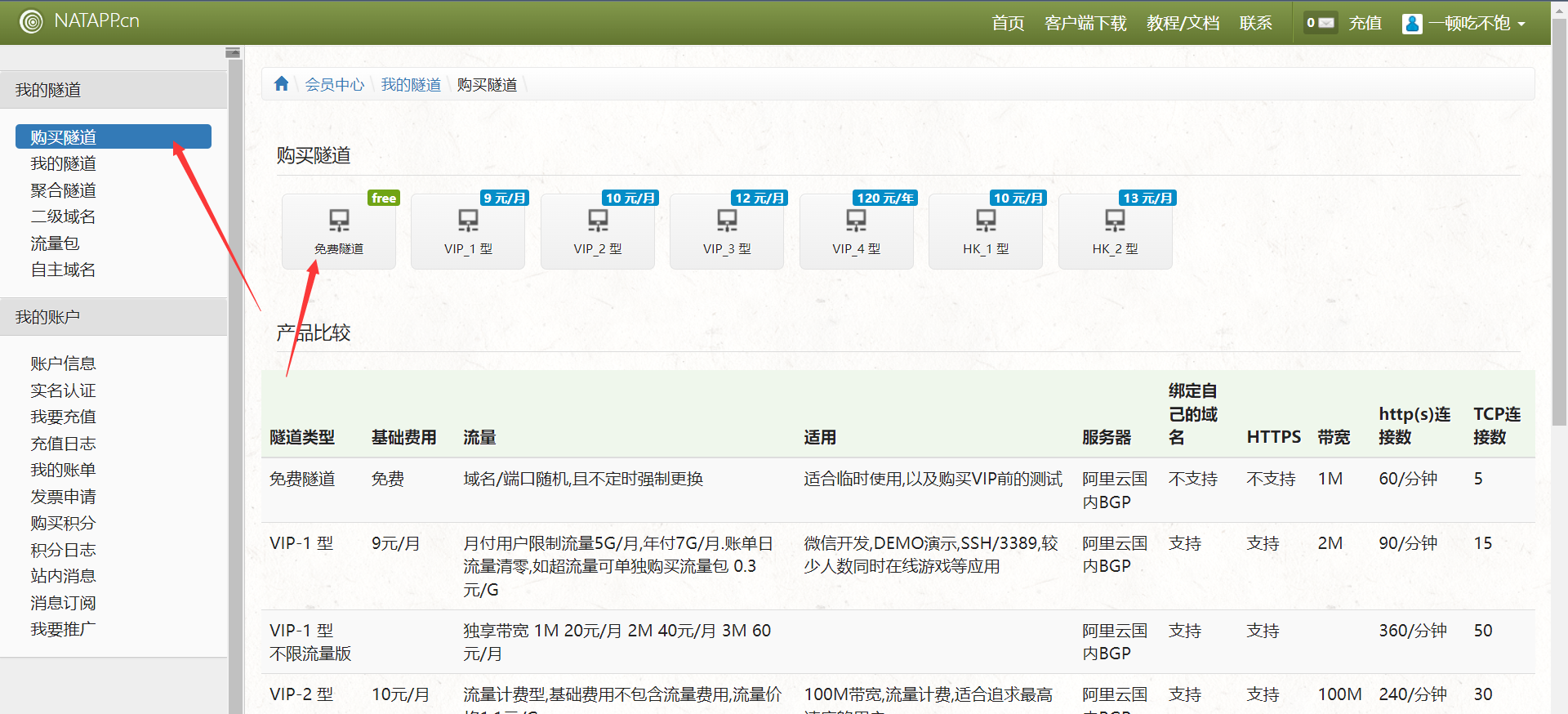
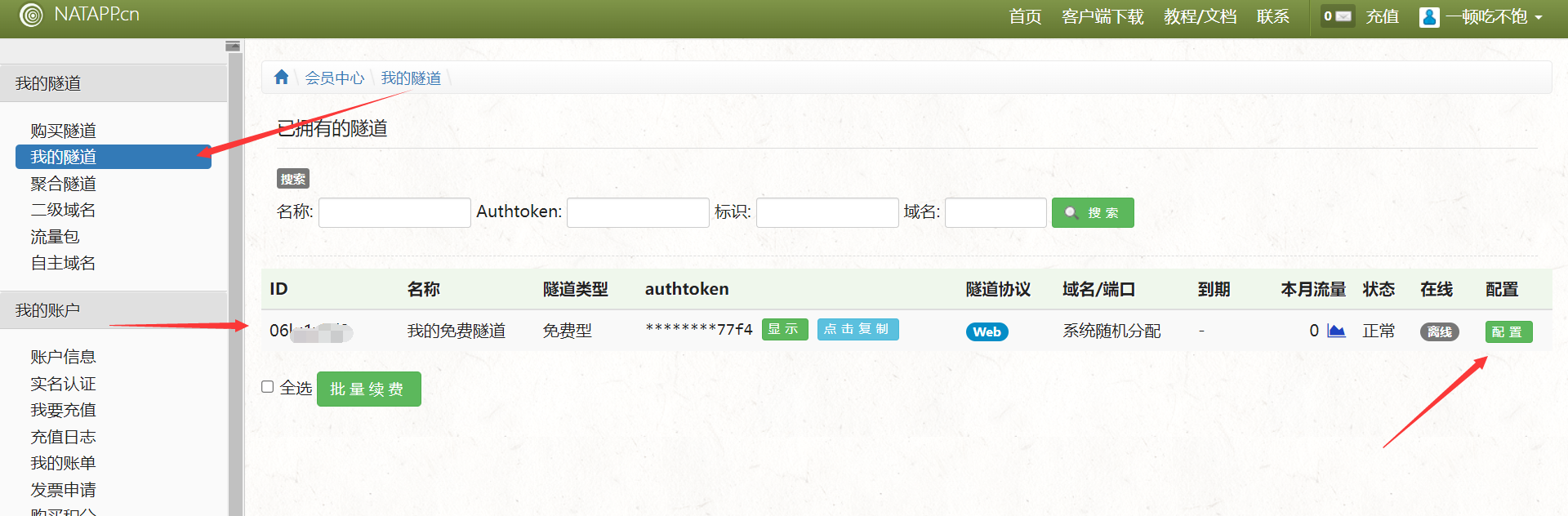
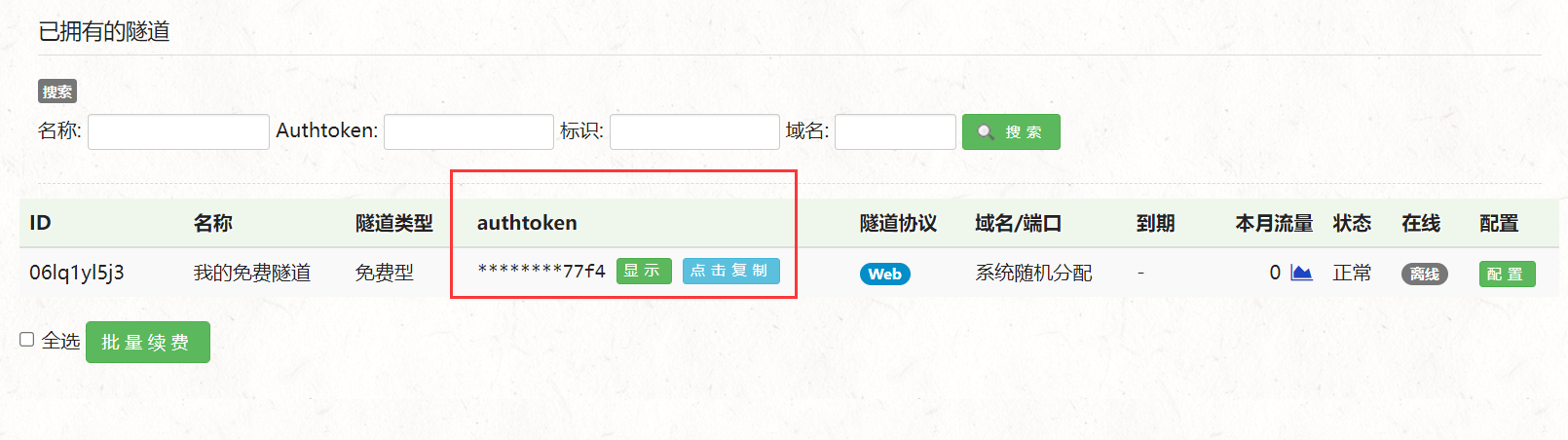
Check my tunnel interface after purchase , Tunnel configuration
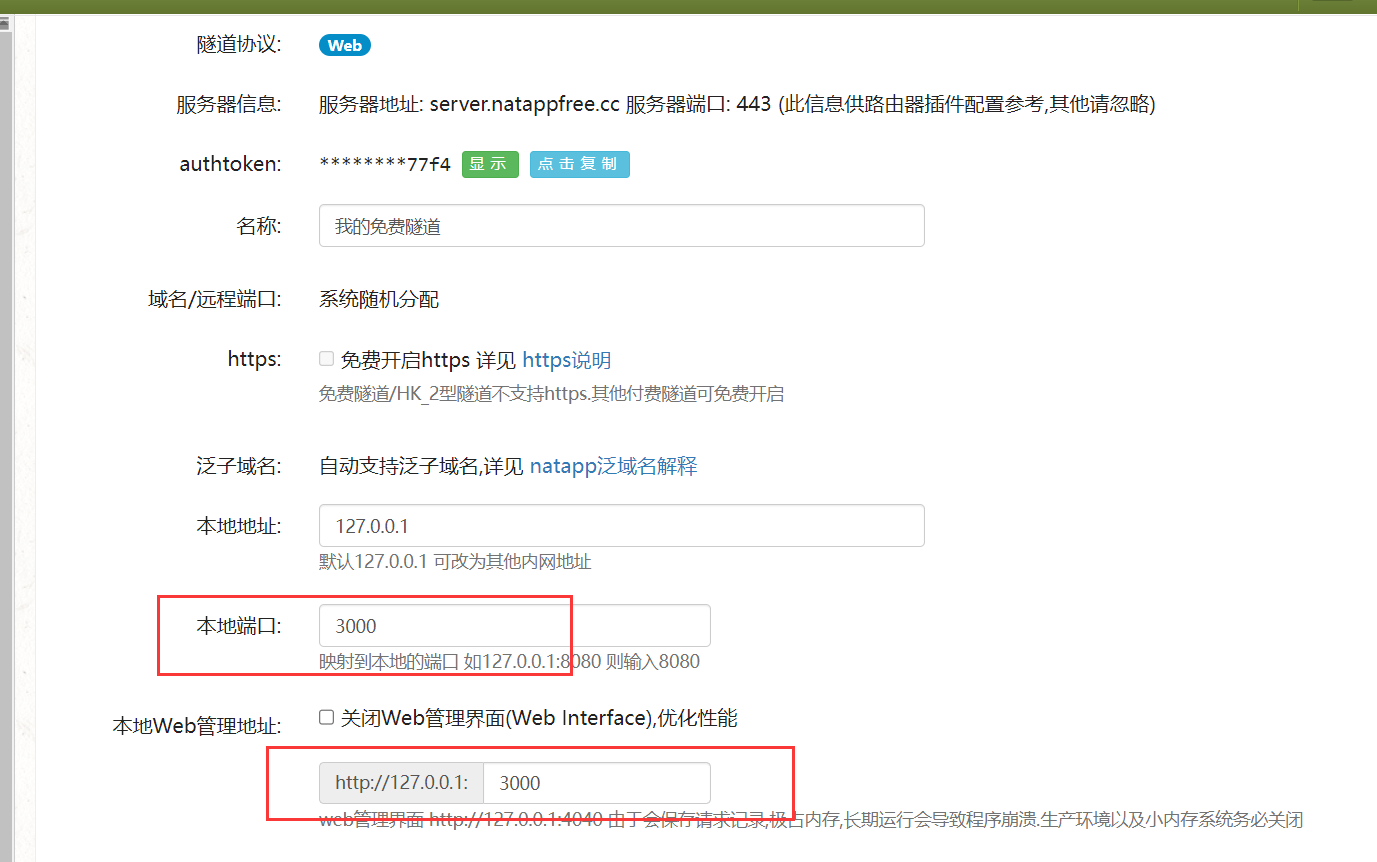
Configure according to your own needs , Mainly configure the port number
2. Download client
Download the corresponding client
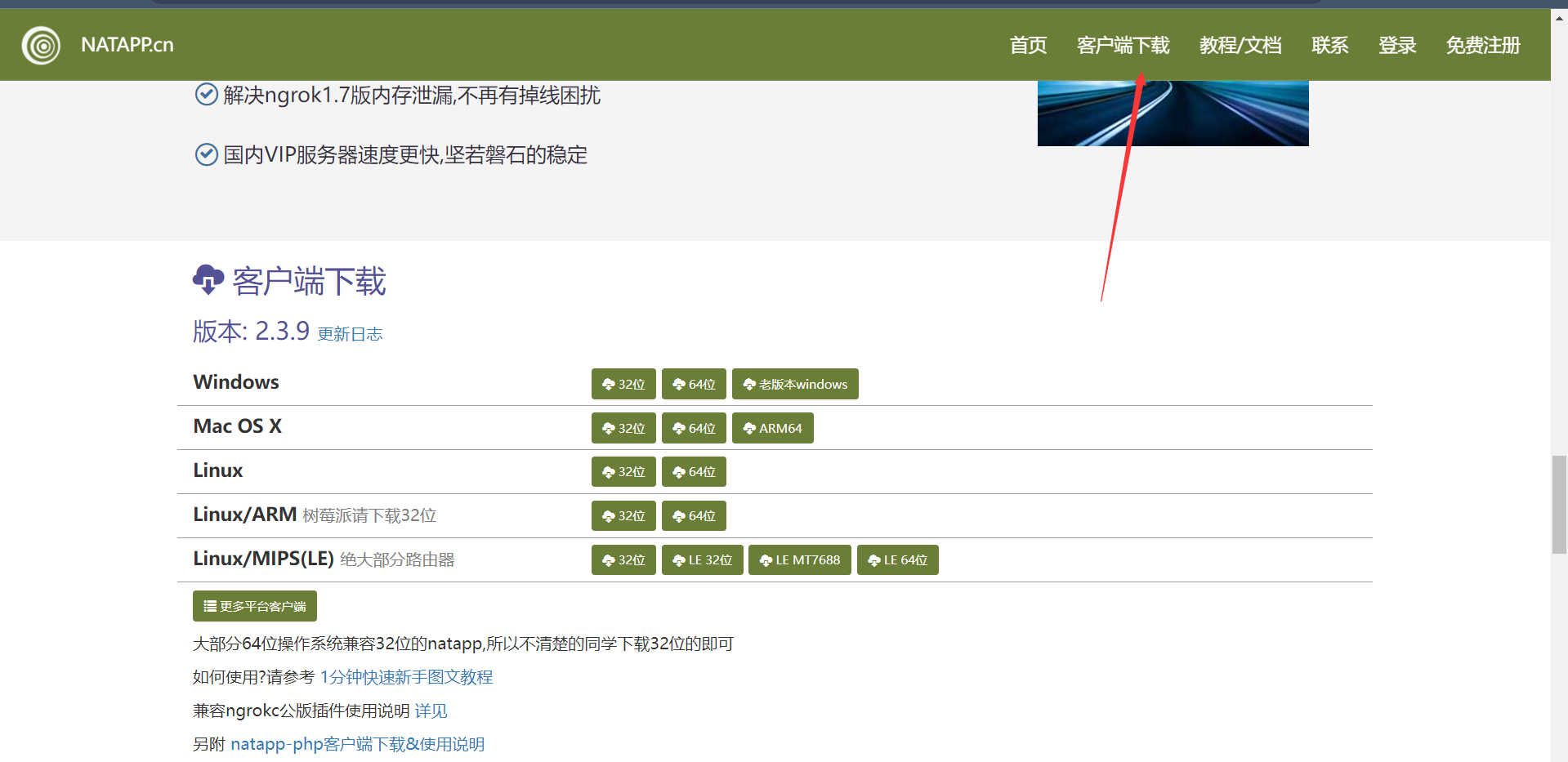
Unpack the installation
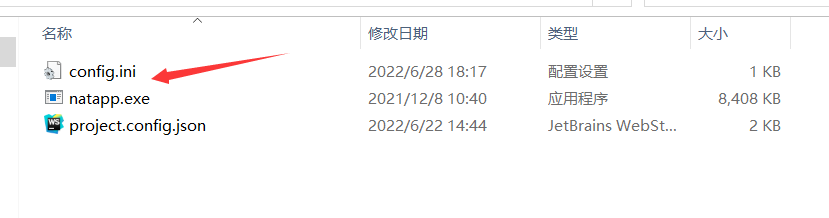
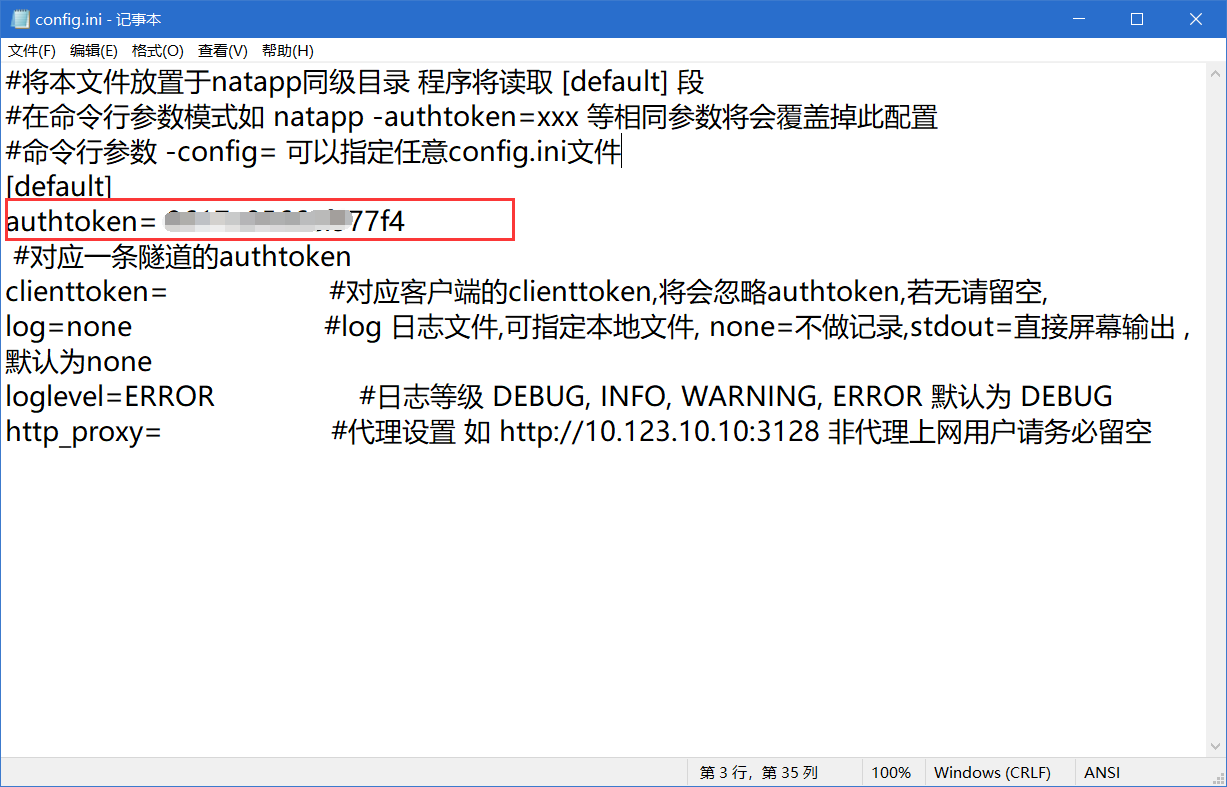
To configure config.ini, Change to your own authtoken
###3. Perform intranet penetration
Run after configuration exe file
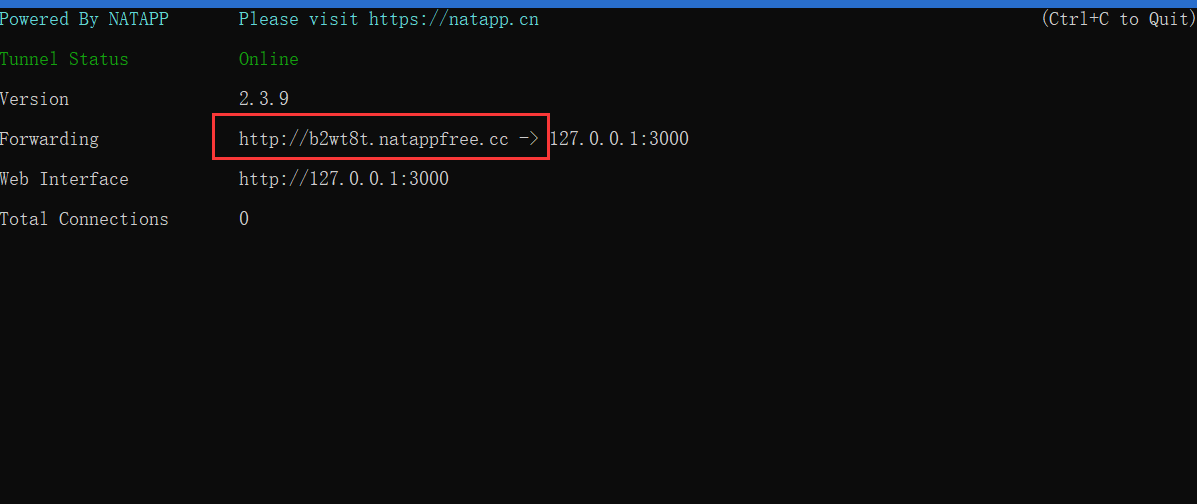
Forwarding Is the current penetration URL , That is, the website we can visit on the Internet , Then you can put the website where you need it
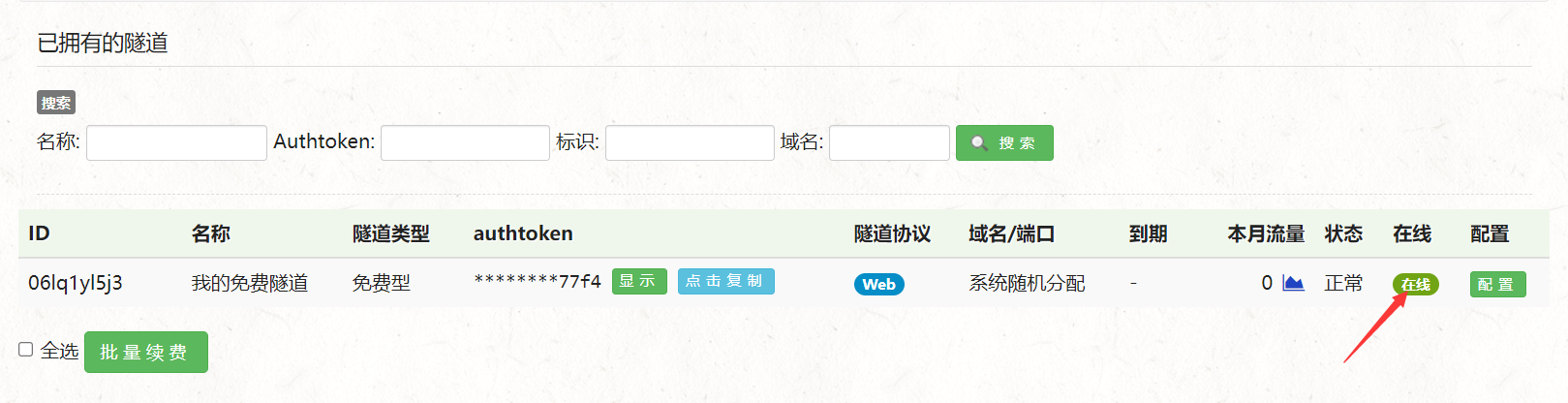
Now we can see that , The state of the tunnel becomes online
边栏推荐
- How does mongodb realize the creation and deletion of databases, the creation of deletion tables, and the addition, deletion, modification and query of data
- Unity uses mesh to realize real-time point cloud (II)
- sql 里面使用中文字符判断有问题,哪位遇到过?比如value<>`无`
- [4G/5G/6G专题基础-146]: 6G总体愿景与潜在关键技术白皮书解读-1-总体愿景
- Information Security Experiment 3: the use of PGP email encryption software
- First issue of JS reverse tutorial
- [bw16 application] Anxin can realize mqtt communication with bw16 module / development board at instruction
- 小程序实现页面多级来回切换支持滑动和点击操作
- 战略合作|SubQuery 成为章鱼网络浏览器的秘密武器
- **grafana安装**
猜你喜欢
Oracle installation enhancements error
基础篇:带你从头到尾玩转注解

NATAPP内网穿透
Detailed explanation of diffusion model
Arthas simple instructions
Network request process
Integer or int? How to select data types for entity classes in ORM

Kubernetes cluster capacity expansion to add node nodes
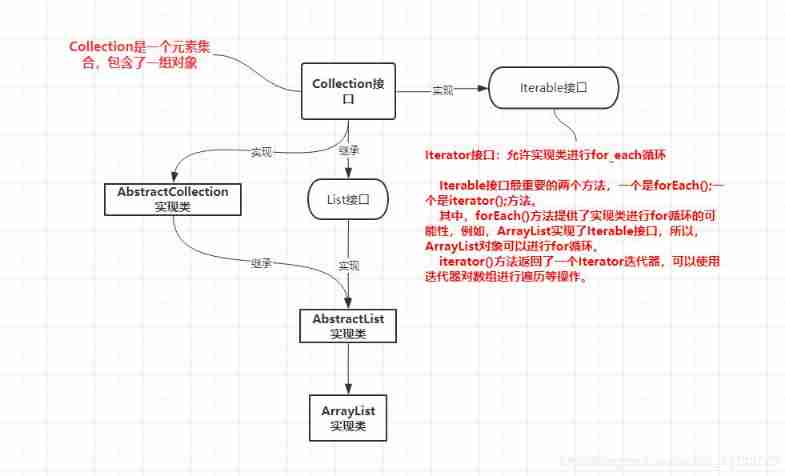
Difference between interface iterator and iteratable
Regular matching starts with XXX and ends with XXX
随机推荐
IIS faked death this morning, various troubleshooting, has been solved
Difference between interface iterator and iteratable
flink. CDC sqlserver. 可以再次写入sqlserver中么 有连接器的 dem
数据库多表关联查询问题
[Frida practice] "one line" code teaches you to obtain all Lua scripts in wegame platform
基础篇:带你从头到尾玩转注解
liunx命令
How to use clipboard JS library implements copy and cut function
thinkphp数据库的增删改查
其实特简单,教你轻松实现酷炫的数据可视化大屏
20排位赛3
Arthas simple instructions
Switching value signal anti shake FB of PLC signal processing series
【无标题】
flinkcdc 用sqlclient可以指定mysqlbinlog id执行任务吗
The configuration and options of save actions are explained in detail, and you won't be confused after reading it
信息安全实验一:DES加密算法的实现
Using JWT to realize login function
面试被问到了解哪些开发模型?看这一篇就够了
根据热门面试题分析Android事件分发机制(二)---事件冲突分析处理