当前位置:网站首页>First issue of JS reverse tutorial
First issue of JS reverse tutorial
2022-07-07 09:35:00 【Little w who learns programming】
JS The first issue of reverse tutorial
Project brief introduction
- This article is suitable for novice crawlers js Read in reverse , Preliminary contact JS reverse , Not very familiar with reverse operation , This article can be used as a reference , First step , If there's a big guy , Criticism and correction are also welcome
- This article takes Enterprise name Technology Take this website as an example , A preliminary introduction JS Reverse basic operation
Environmental preparation
- This project involves JS Debugging verification of , So there needs to be Chrome browser ,Nodejs(js Operating environment ),WebStorm(IDE)
- nodejs Download and install it directly from the official website , After installation, enter node --version, If the version number appears, the installation is successful .
- WebStorm Activation is required after installation , There are many Baidu activation tutorials , Search by yourself , if necessary , You can also comment or send me a private letter to get the tutorial .
The analysis process
First , Go to the website https://www.qimingpian.cn/finosda/project/pinvestment:
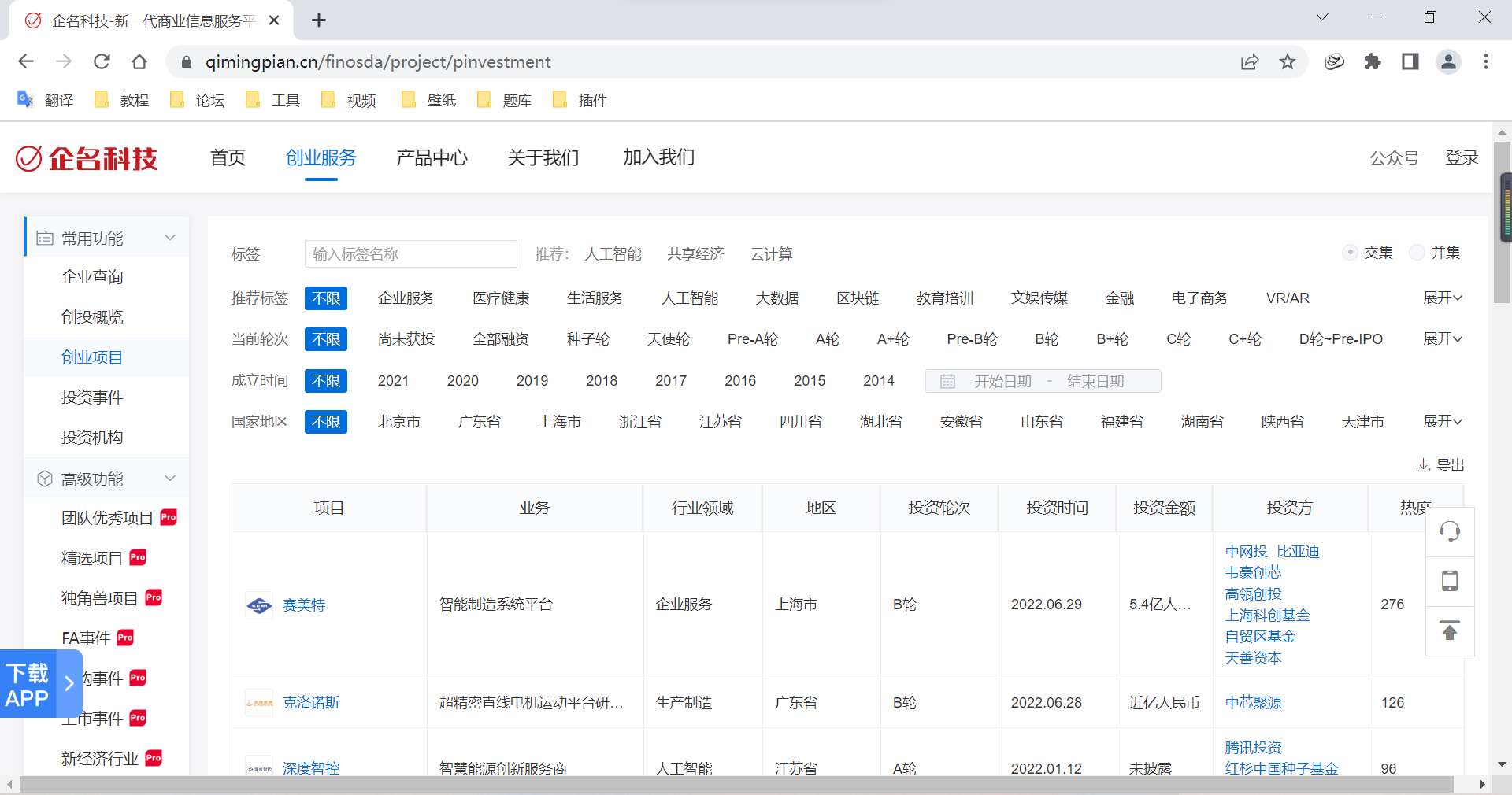
View the source code :
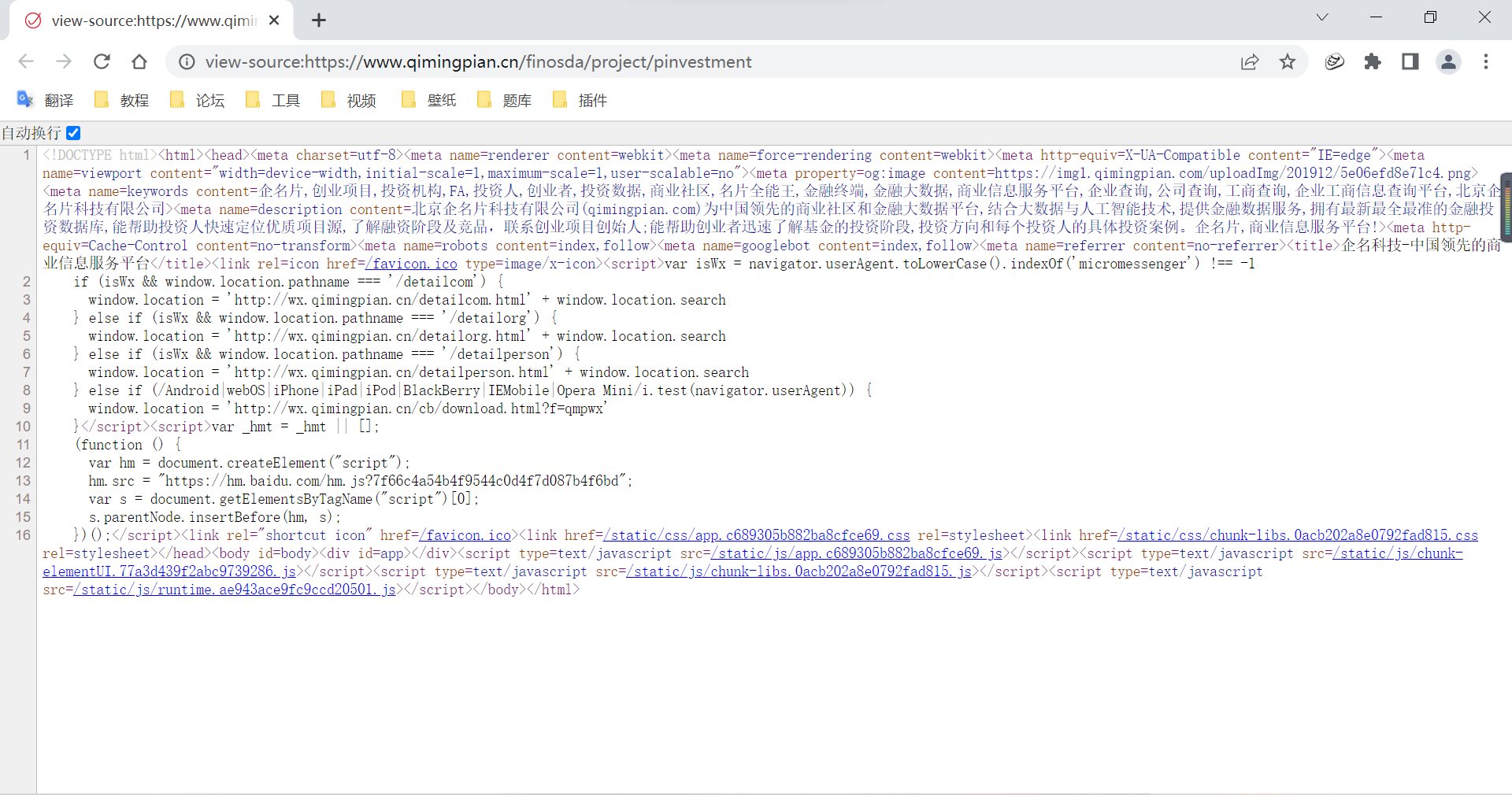
It's all js A file called , Data cannot be obtained directly through source code . Open developer tools , Carry out the bag , choice Fetch/XHR And documentation , To view the requests sent by the website :
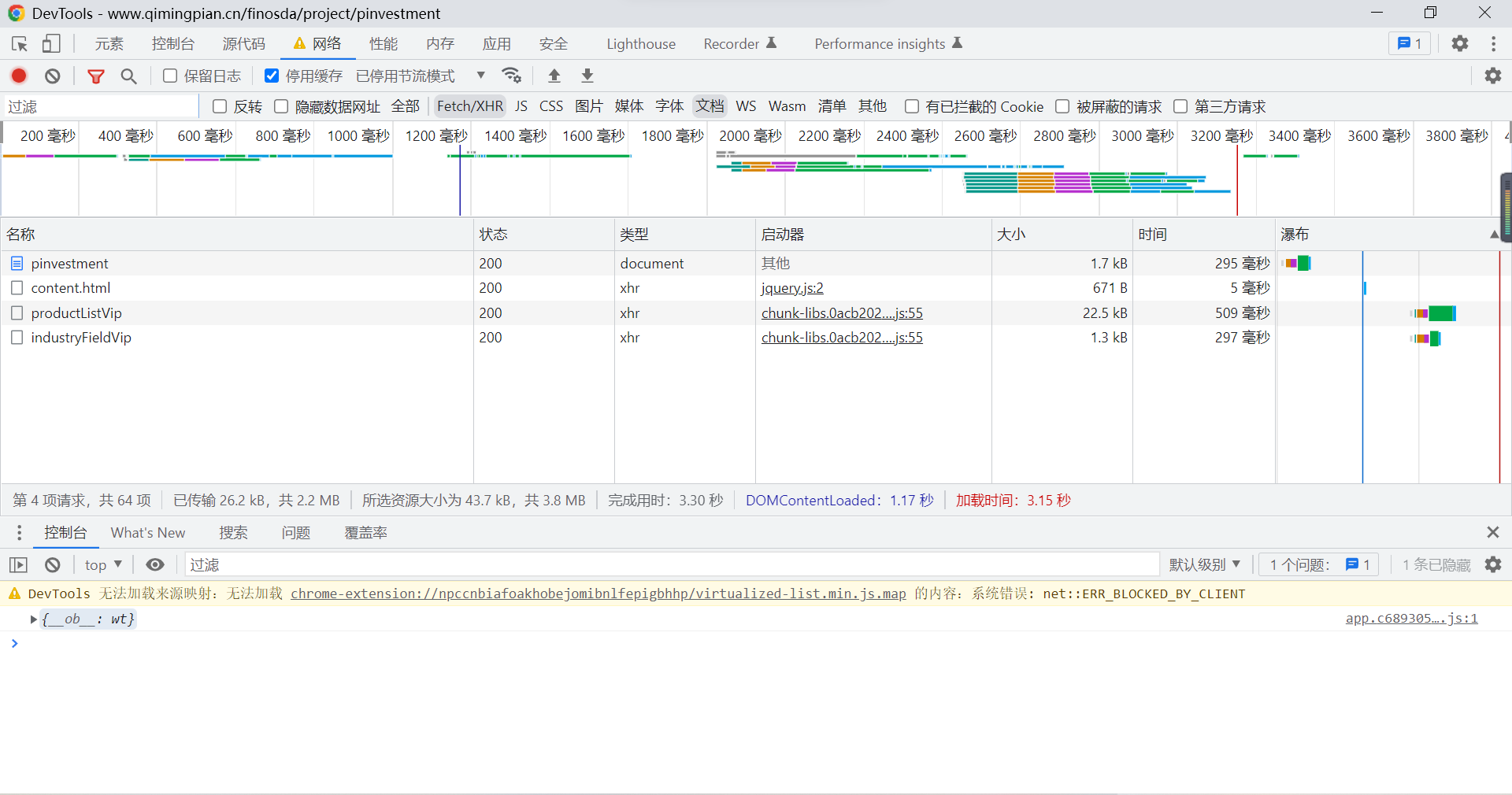
You can see that there is productListVip and industryFiledVip Two documents , Blind guess the first file is the tag list of the page , The second file is the company data of the page *-.-*, Click the first file and find that there is data encrypt_data, But it's encrypted data , So you need to js Document analysis :
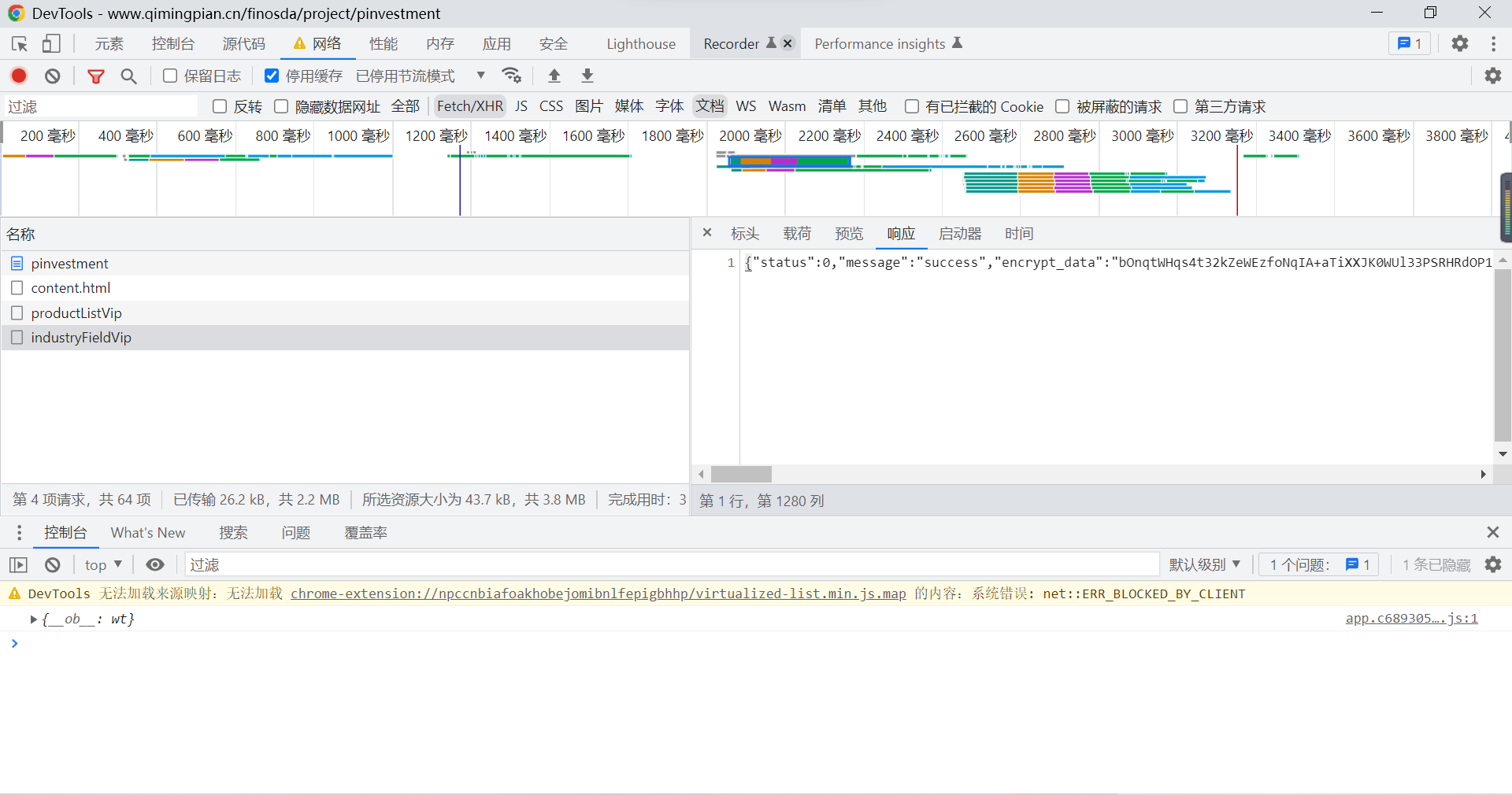
First , We can blindly guess that the data is the data we need , Then we can run for the purpose of decrypting the data js debugging ,
First , since js There is a code that encrypts the data in the file , Then there must be code to decrypt the data , Because at last, it will be displayed again html Come on , If not decrypted , How to display it ?
therefore , We can... Again source Find the... Used by the page in the panel js Code file :
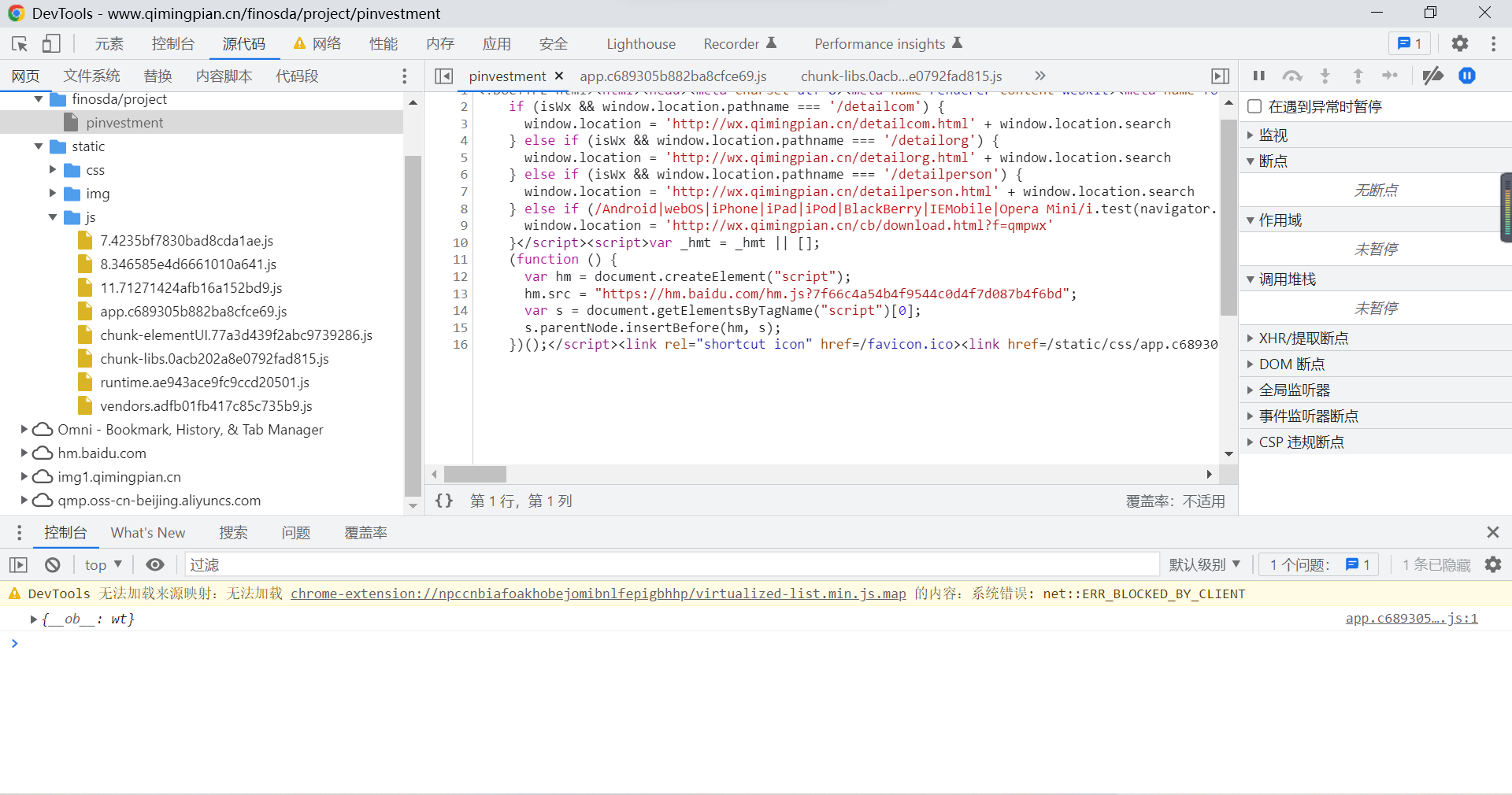
Choose what we need to debug js file , Check the source code of the previous page , We can choose first app.c68… This js File debugging , On the right side of the source code page “XHR/ Extract breakpoints ”, Its function is to request data on the page , Stop it . If the code is stacked on one line , You can click {} Format symbols .
We set up XHR The breakpoint :
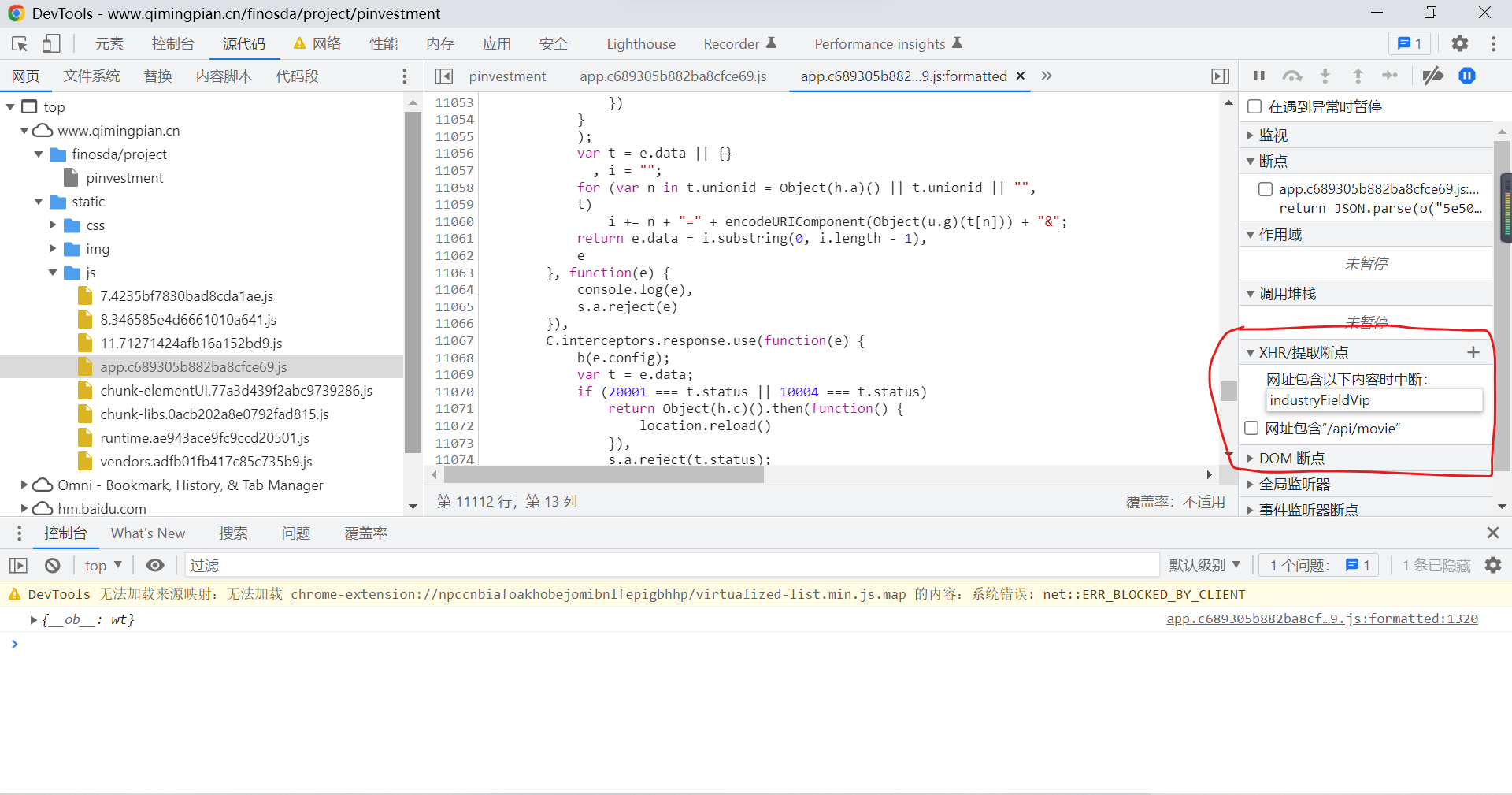
When the request data URL contains industryFiledVip Time is truncated , Refresh the page , You can find that debugging has started :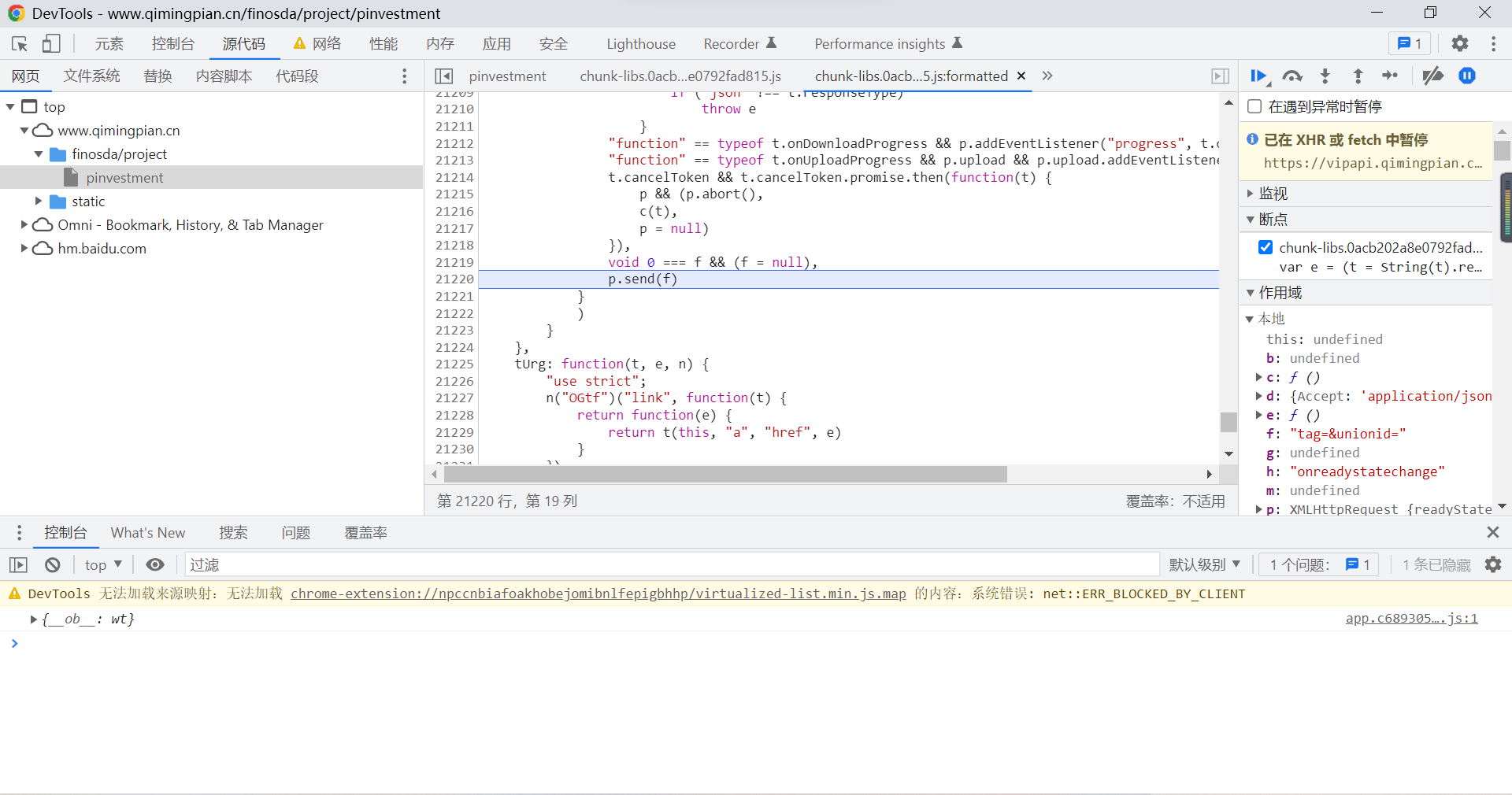
We can keep going , If you find suspicious code , You can place the mouse over the variable to view the value of the variable :
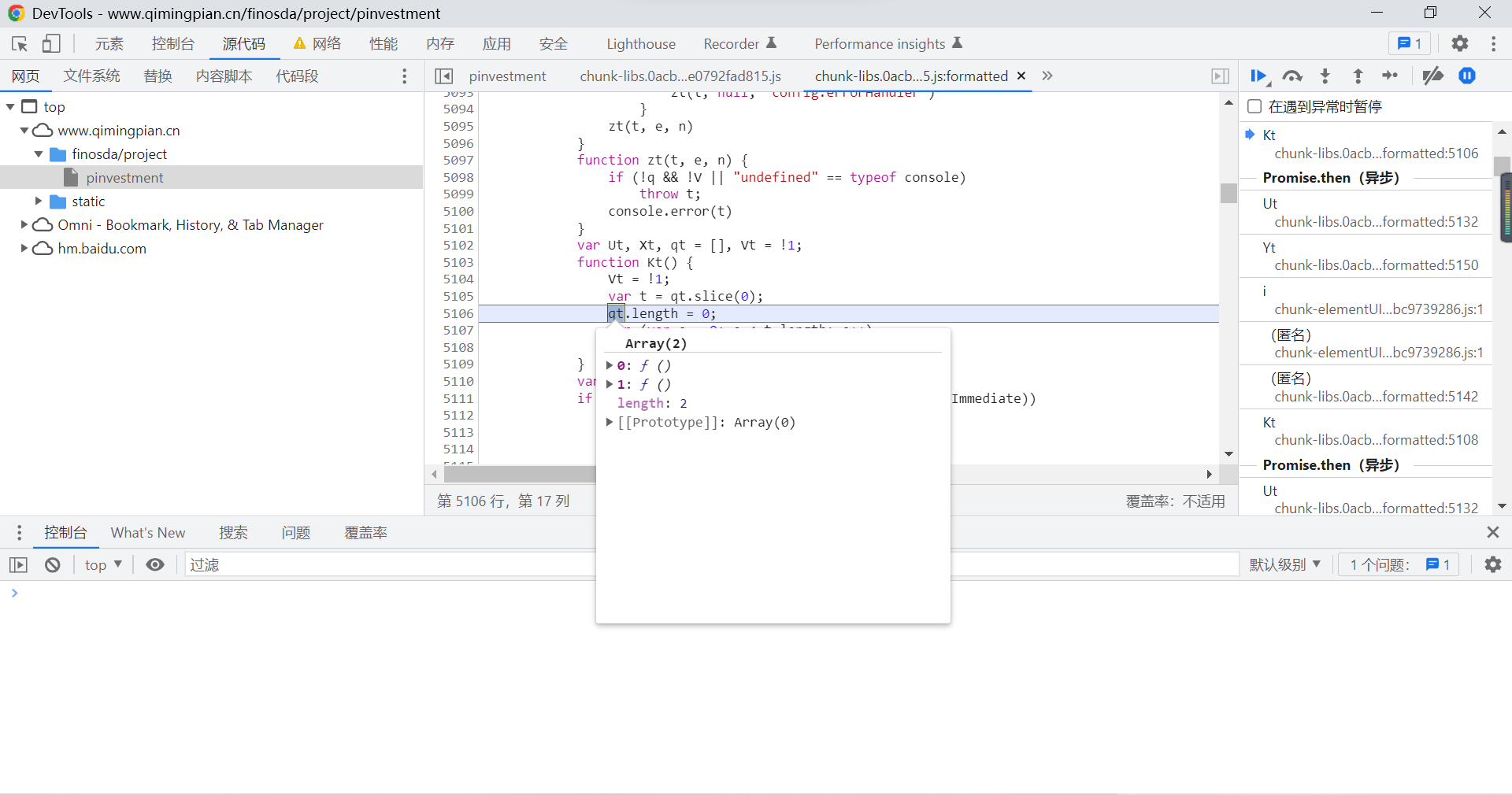
You can also output the value of this variable directly on the console :
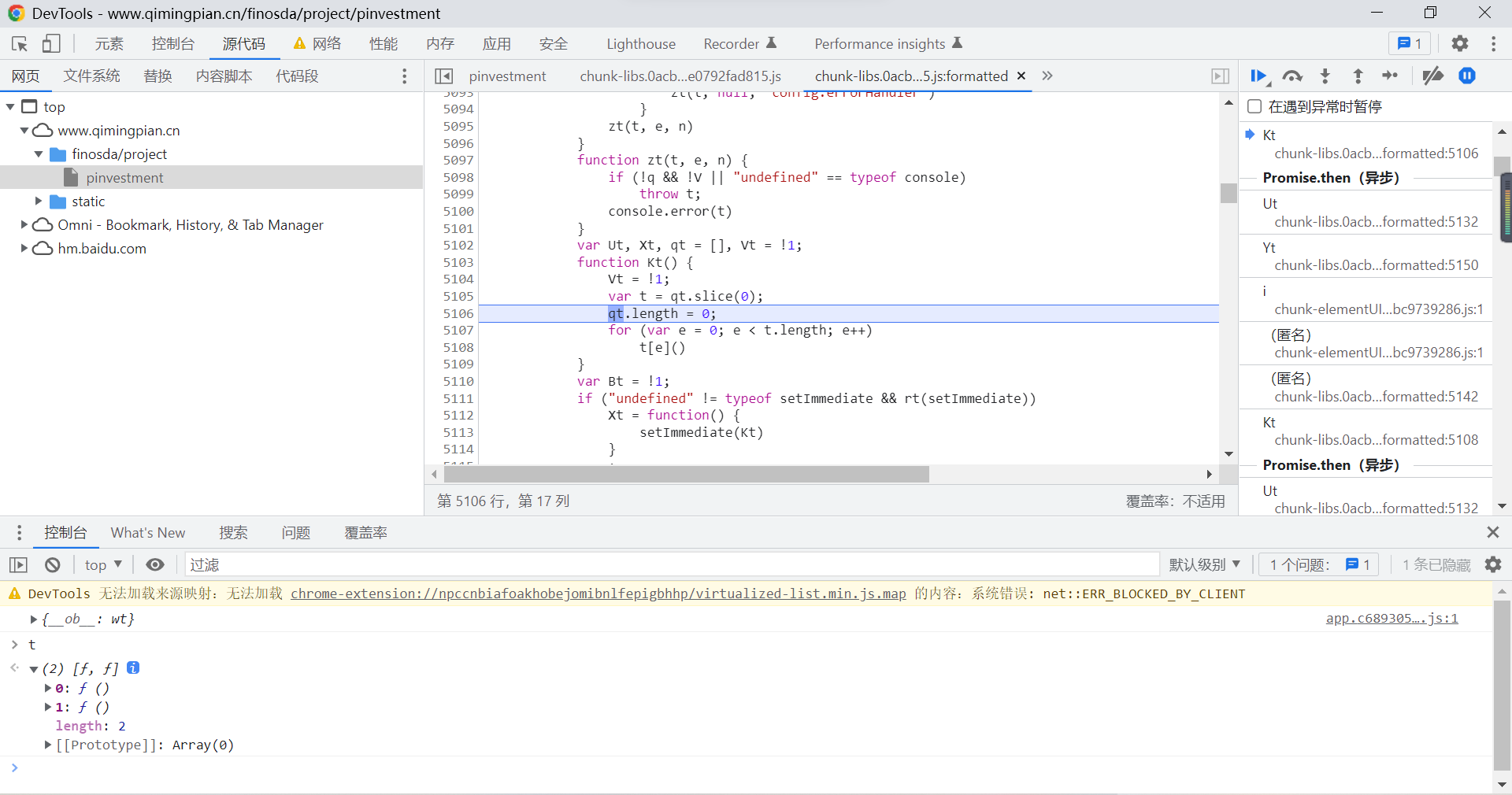
here , We debugged , You can locate suspicious data in the statement in the following figure :
Output this parameter , View the data :
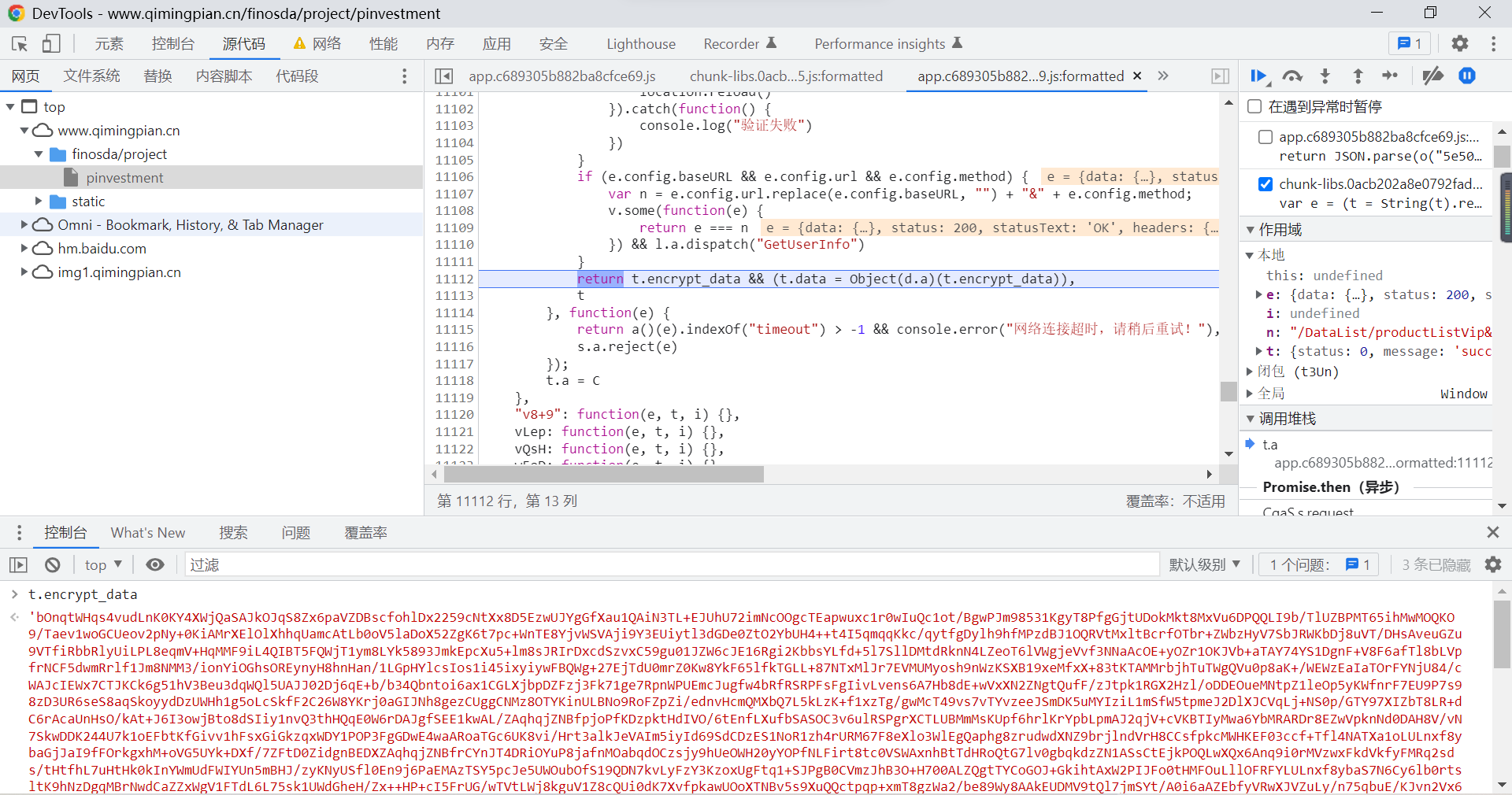
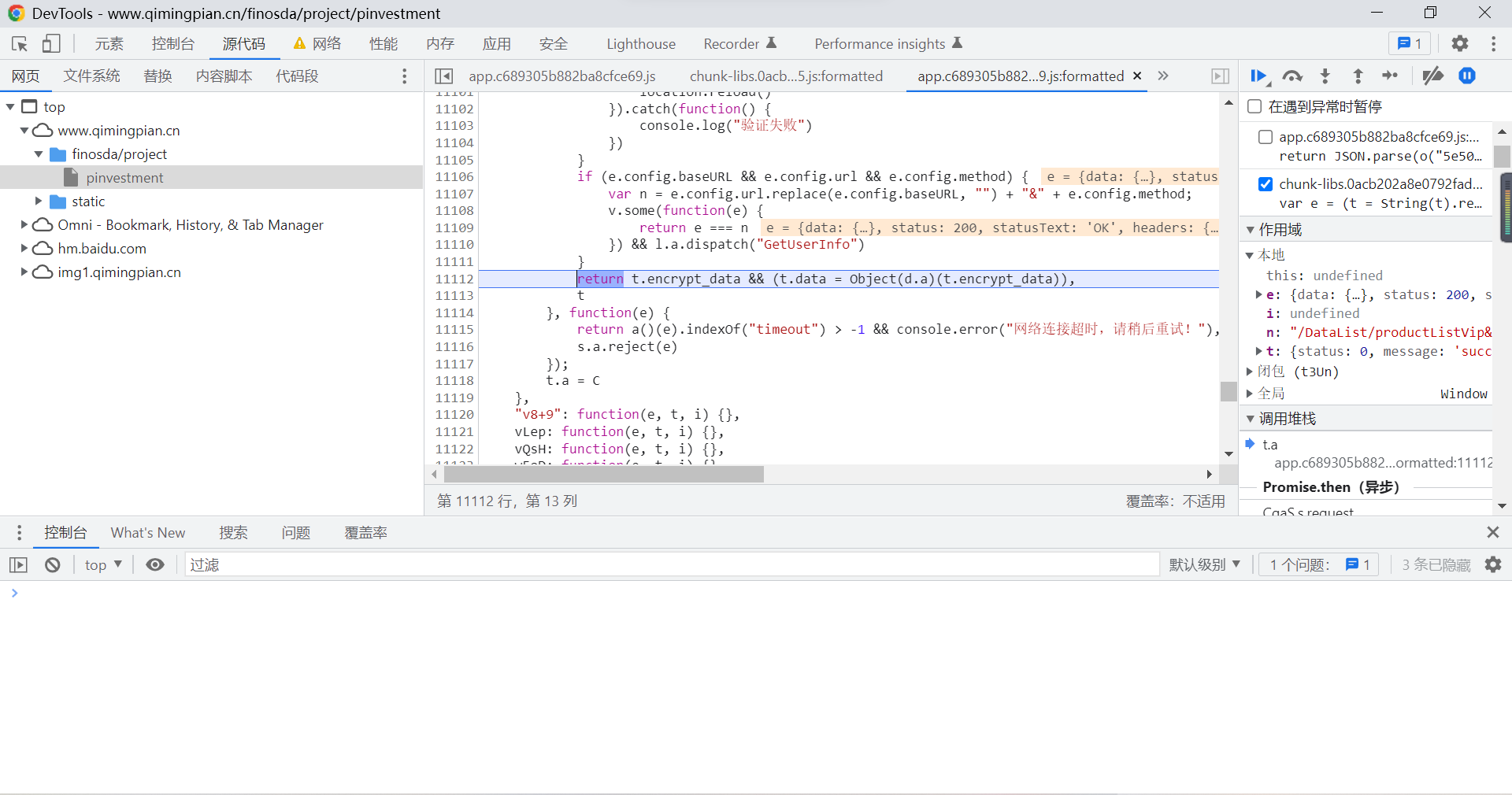
You can find , This data seems to be what we need industryFiledVip In the document encrypt_data Parameters , At this point, our goal is very clear , Is to find the function that decrypts this parameter .
At this time, function call execution , Check the function called in this statement :
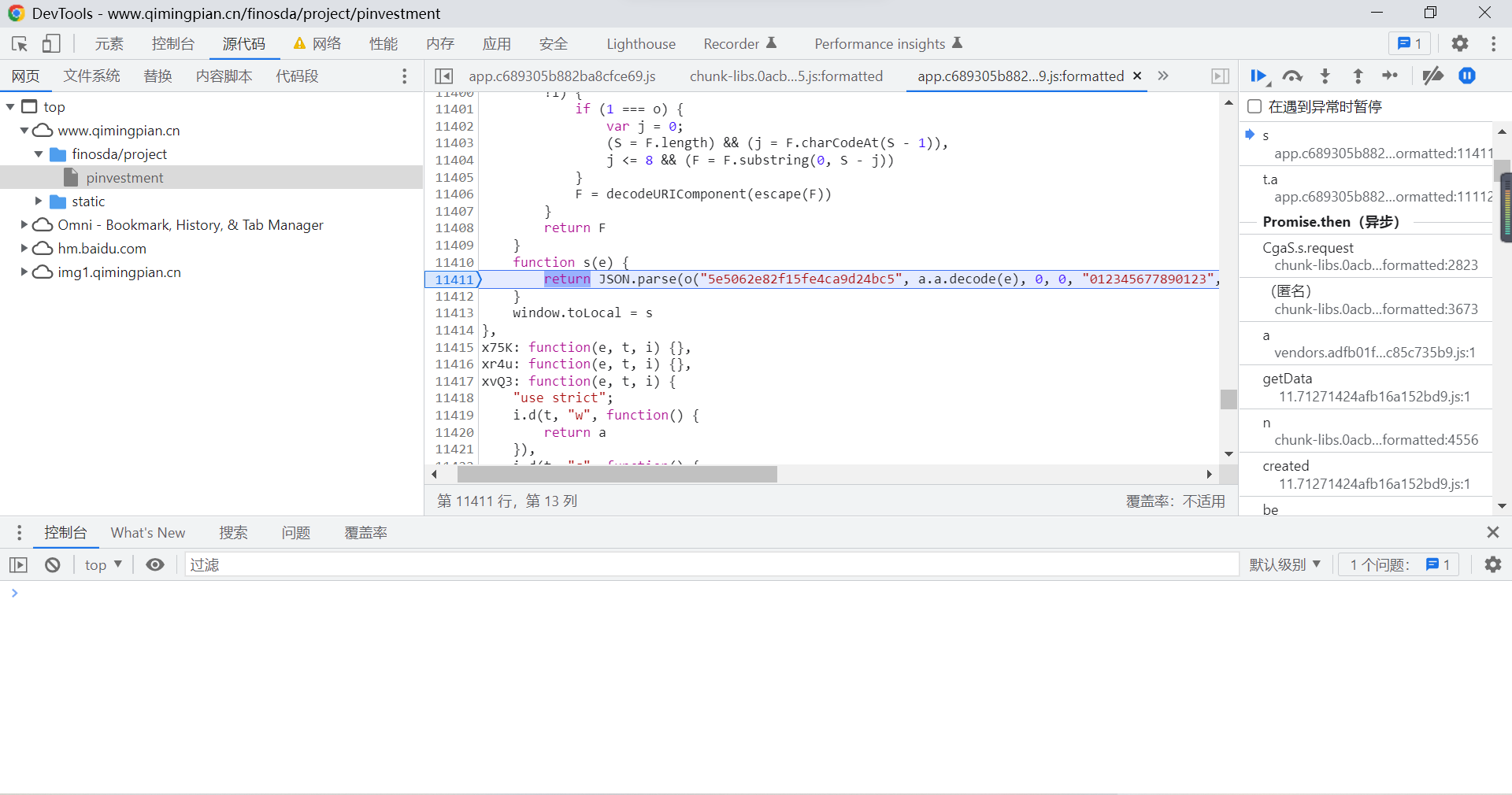
At this time, we can see that there is a s(e) function , There are pairs json Code for parsing , At this time, we output this on the console s(e) The result of function execution :
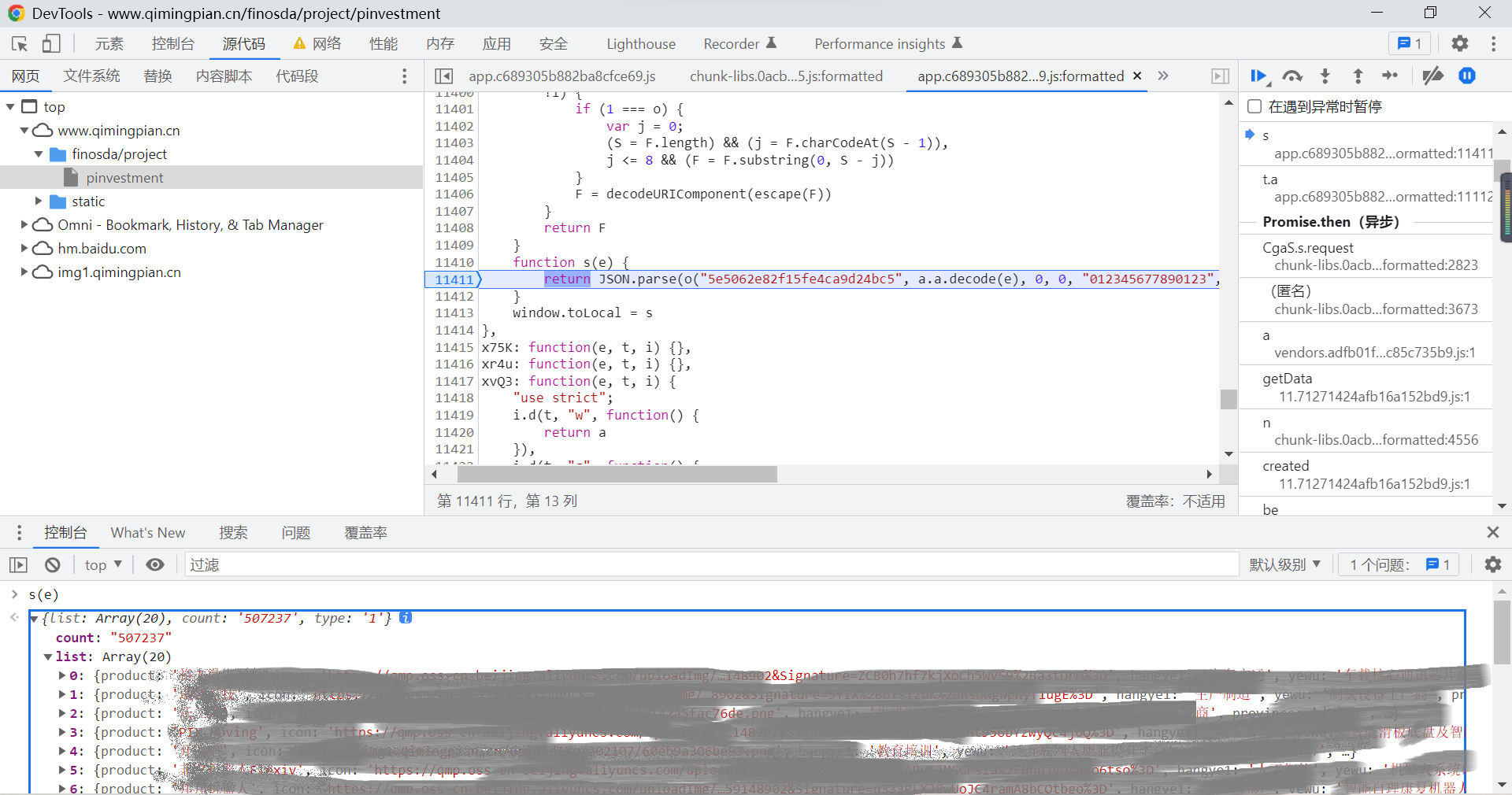
here , We can see it clearly , The return value of this function is the data we want , That is, the result of decrypting the previously encrypted data , So this function is internal o() The function must be used to decrypt encrypted data , And only one of the parameters is the result of function execution , The rest are written dead .
Now we turn it on WebStorm, Create a new one js file , Copy all the functions involved to js In file :
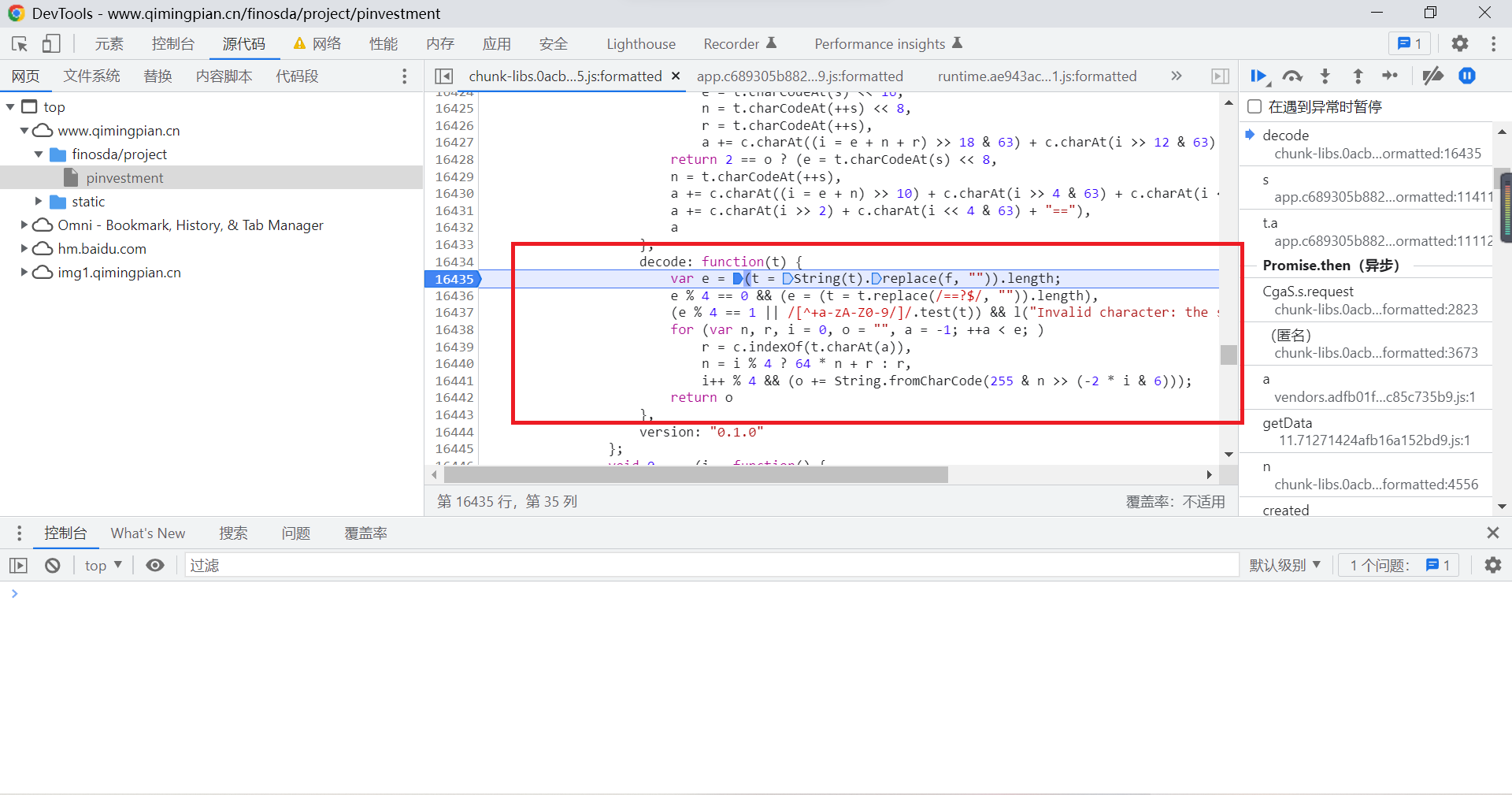
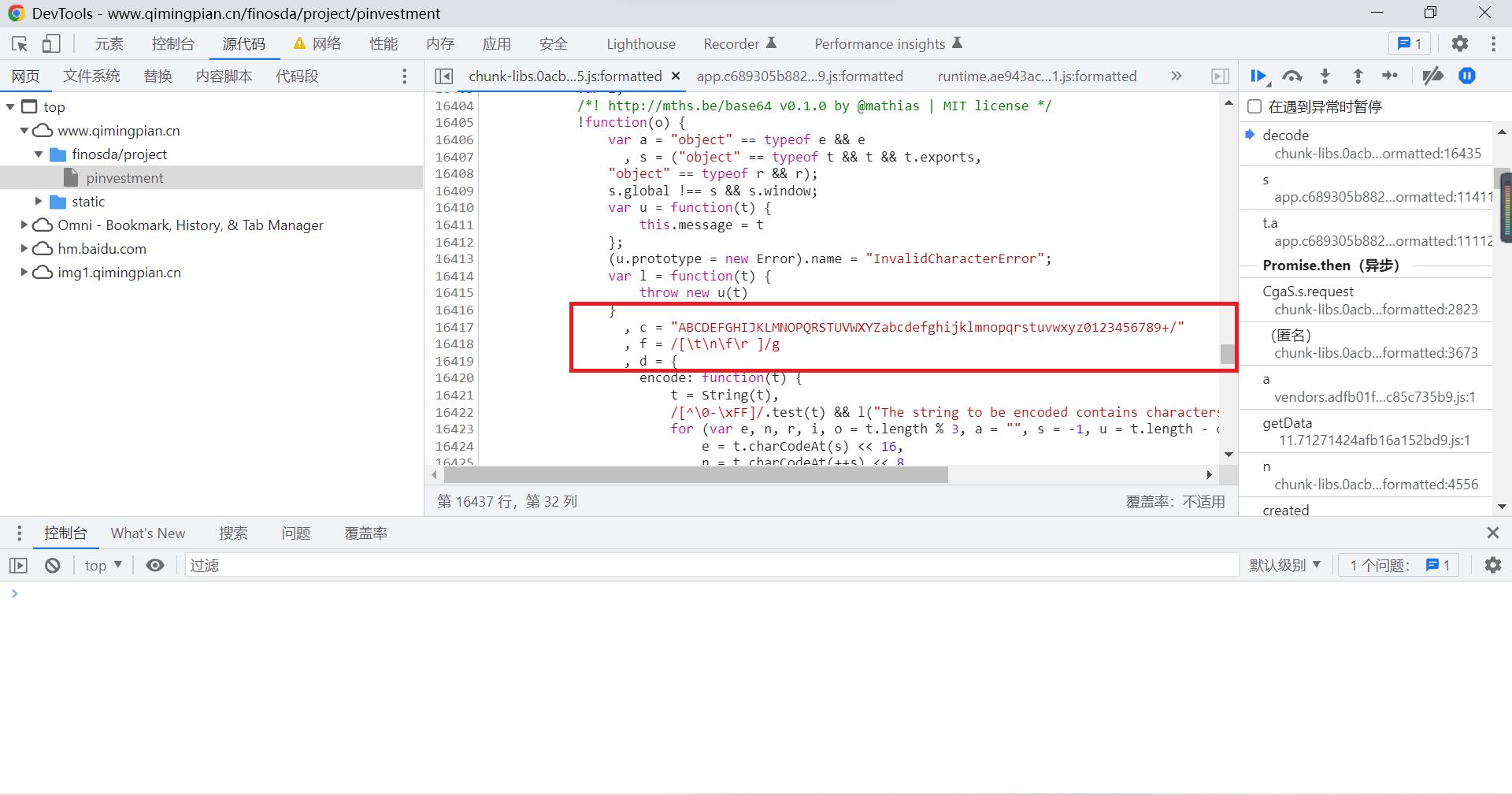
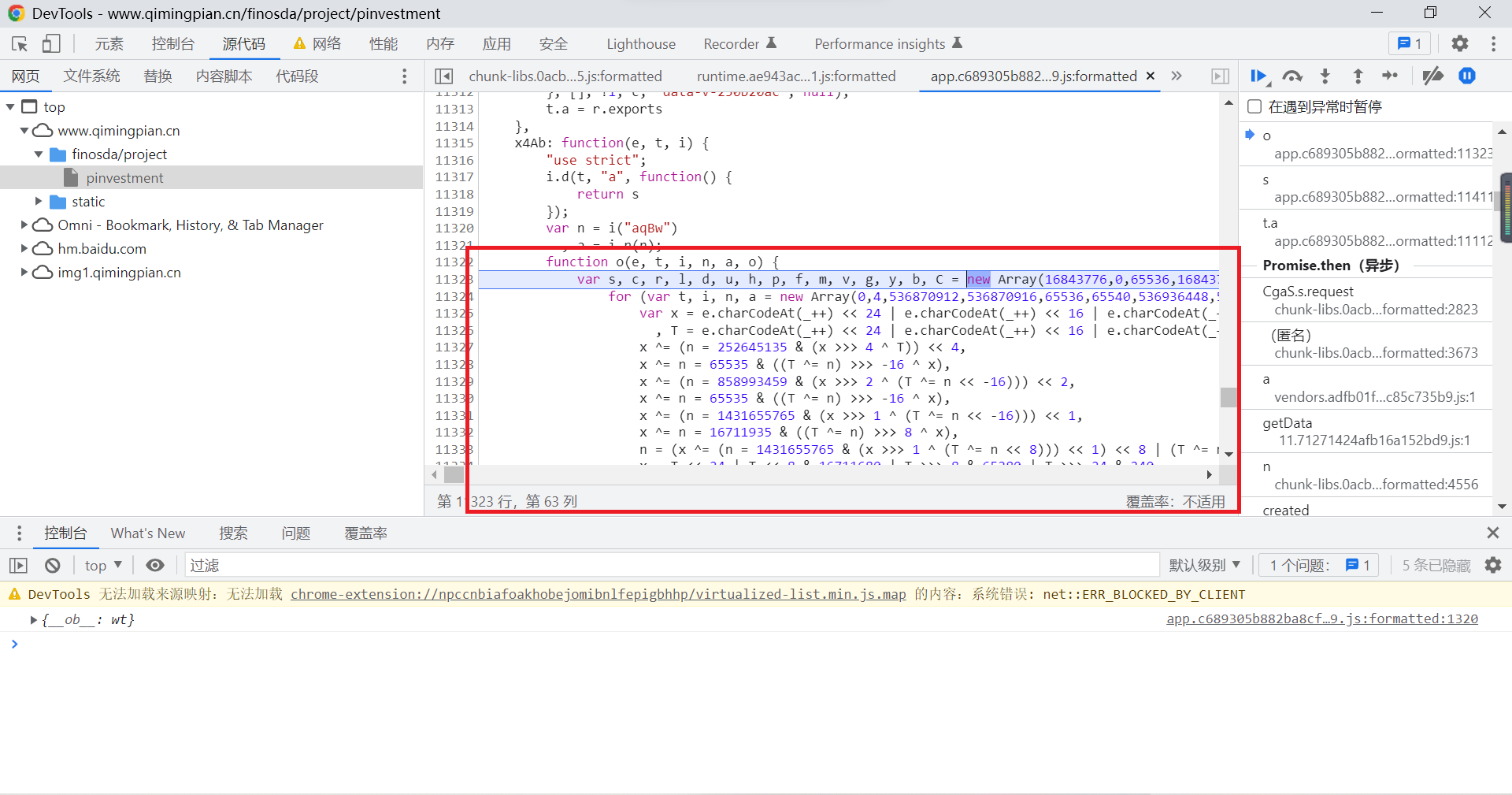
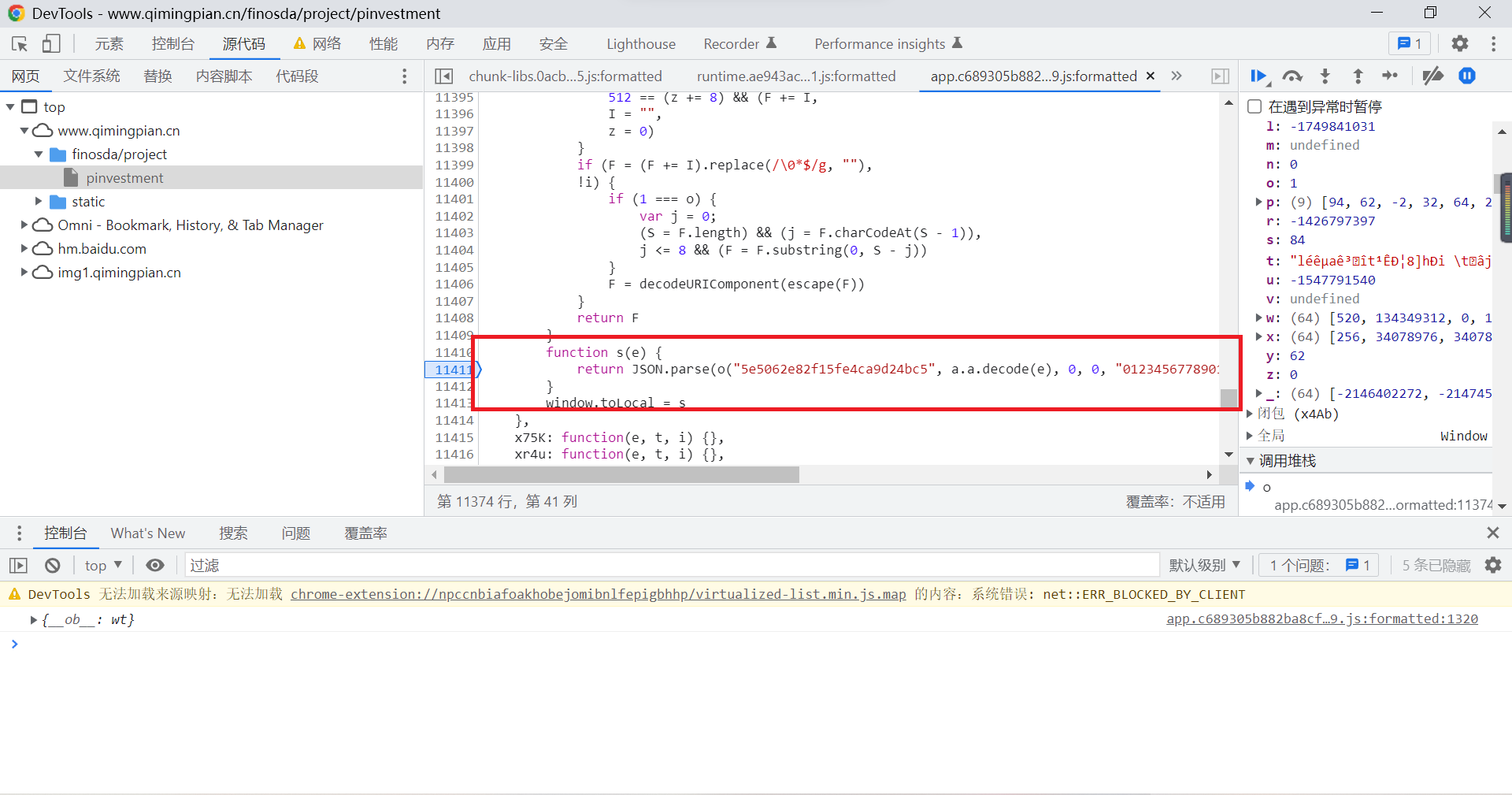
The final will be entry_data Bring it into the function to perform the operation , You can get the data you want , You can proceed to the next step :
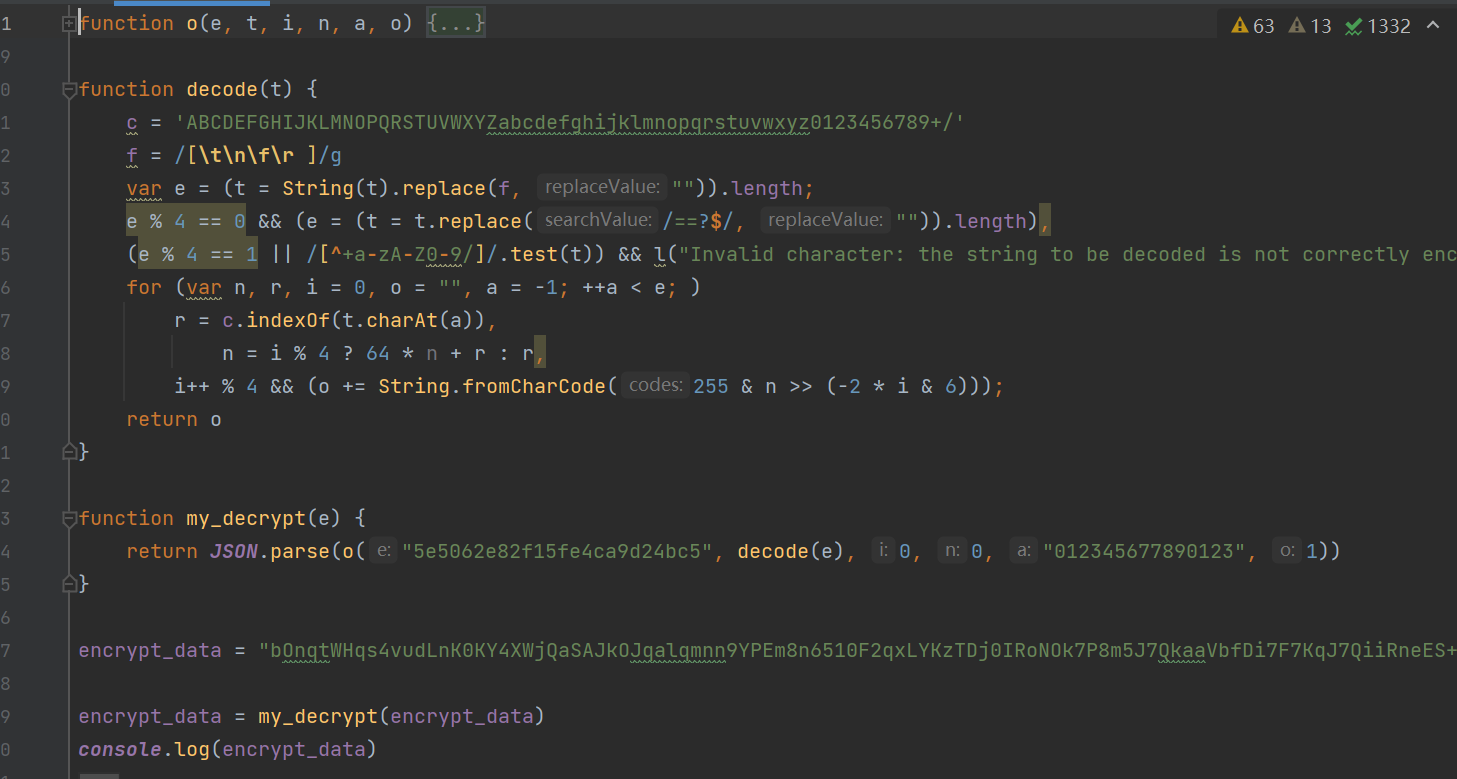
thus , This time, it is relatively simple js Reverse is the end , Welcome to criticize and correct .(*.*)
边栏推荐
猜你喜欢
Run can start normally, and debug doesn't start or report an error, which seems to be stuck
Pycharm create a new file and add author information
Yapi test plug-in -- cross request
Dynamics 365Online ApplicationUser创建方式变更
What development models did you know during the interview? Just read this one
Connecting mobile phone with ADB
信息安全实验三 :PGP邮件加密软件的使用
Cesium does not support 4490 problem solution and cesium modified source code packaging scheme

面试被问到了解哪些开发模型?看这一篇就够了
其实特简单,教你轻松实现酷炫的数据可视化大屏
随机推荐
Record of structured interview
超十万字_超详细SSM整合实践_手动实现权限管理
信息安全实验四:Ip包监视程序实现
Final keyword
SAP MM STO单据的外向交货单创建后新加ITEM?
如何成为一名高级数字 IC 设计工程师(1-6)Verilog 编码语法篇:经典数字 IC 设计
Where is the answer? action config/Interceptor/class/servlet
Unity uses mesh to realize real-time point cloud (I)
Postman setting environment variables
Windows starts redis service
如何成为一名高级数字 IC 设计工程师(5-2)理论篇:ULP 低功耗设计技术精讲(上)
Vs2013 generate solutions super slow solutions
Some pit avoidance guidelines for using Huawei ECS
IIS redirection redirection appears eurl axd
esp8266使用TF卡并读写数据(基于arduino)
Using JWT to realize login function
进程间的通信方式
Leetcode daily questions (2316. count unreachable pairs of nodes in an undirected graph)
嵌套(多级)childrn路由,query参数,命名路由,replace属性,路由的props配置,路由的params参数
Implementation of corner badge of Youmeng message push