当前位置:网站首页>Information Security Experiment 2: using x-scanner scanning tool
Information Security Experiment 2: using x-scanner scanning tool
2022-07-07 09:22:00 【Not enough to eat】
One 、 Purpose and requirements of the experiment
1. Be familiar with the principle of scanning the port of the computer ;
2. Skillfully use X-SCANNER The scanning tool scans the port of the computer .
3. Use port scanning to scan a host , And show the results ( Which ports are open on a host ). For a network segment IP scanning , Show the results ( Which hosts in a network segment are powered on ).
Two 、 Experimental content
1. Skillfully use X-SCANNER Interface of scanning tool
2. View port information
Open the scanning results to check whether there are machines with shared resources that can be invaded , Check common ports such as 21、23、139 Whether it is open .
3. Discover system vulnerabilities
Discover the of the target system CGI Loophole 、IIS Loophole 、RPC Loophole 、SQL Server Loopholes and FTP Weak password vulnerability .
3、 ... and 、 Experimental environment
function Windows XP/2000 The computer of the operating system .
Four 、 Experimental steps and result analysis
1. Install scan tool X-Scan , Click on the run
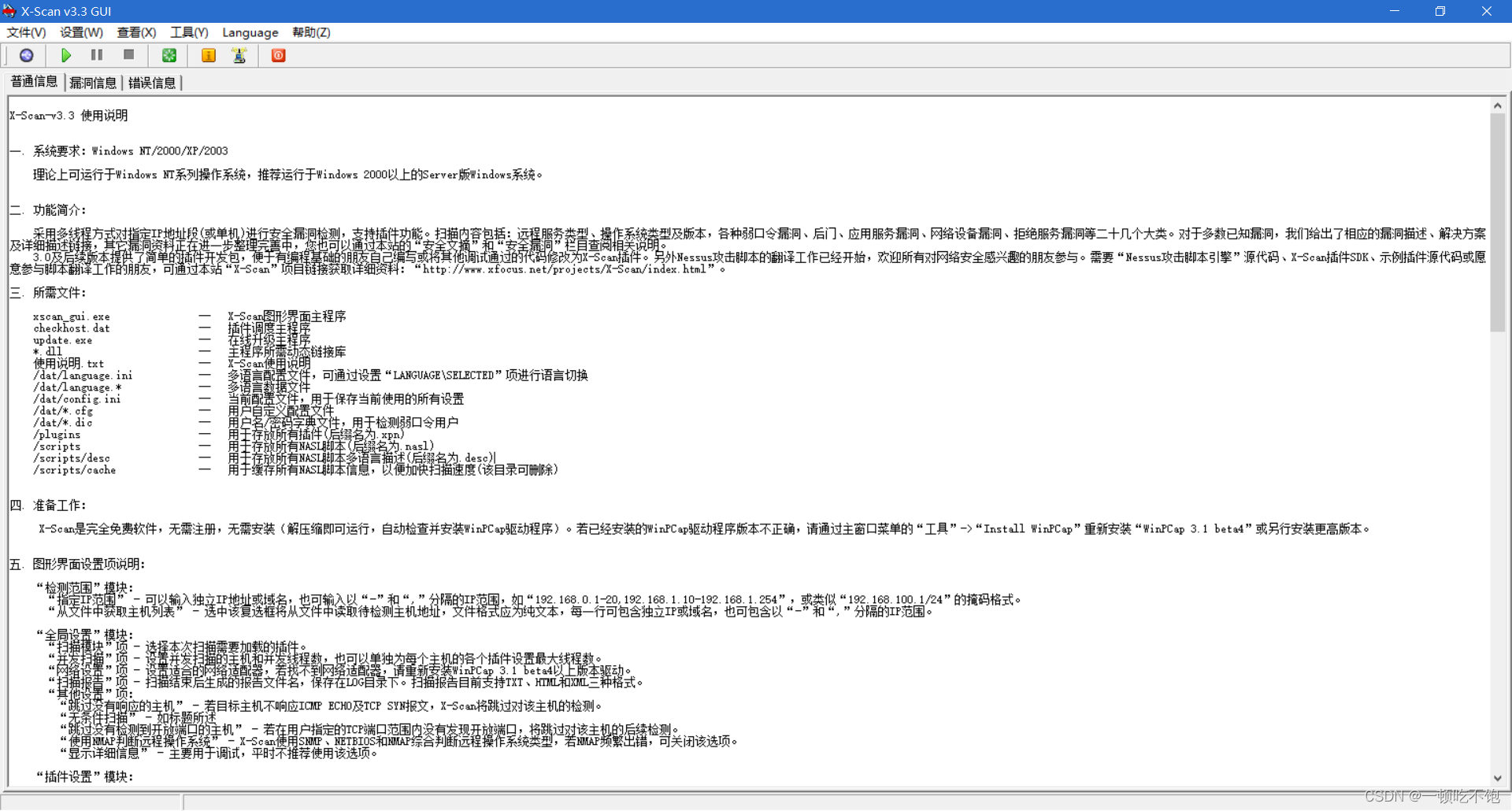
2. Set scanning parameters in settings , Perform a local scan
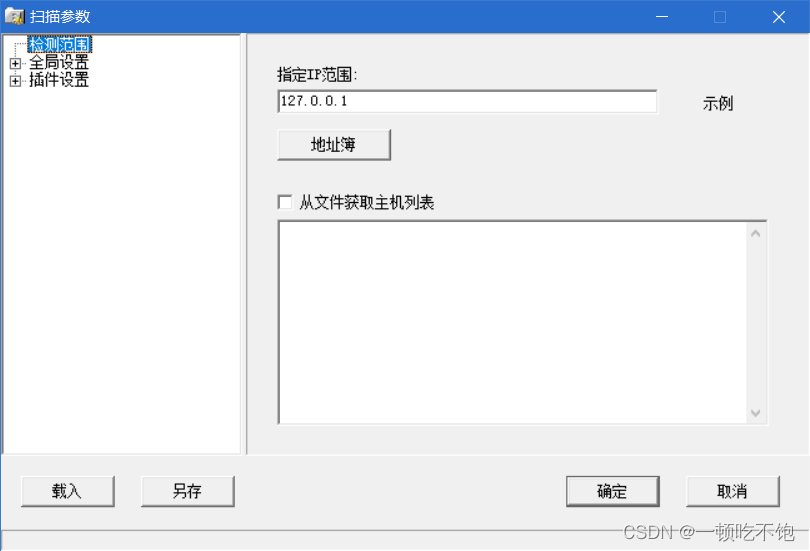
Select scan module in global settings , Include 、IIS Loophole 、RPC Loophole 、SQL Server Loopholes and FTP Weak password vulnerability
 Set port related settings in plug-in settings
Set port related settings in plug-in settings

Click OK after configuration , Then click the run button

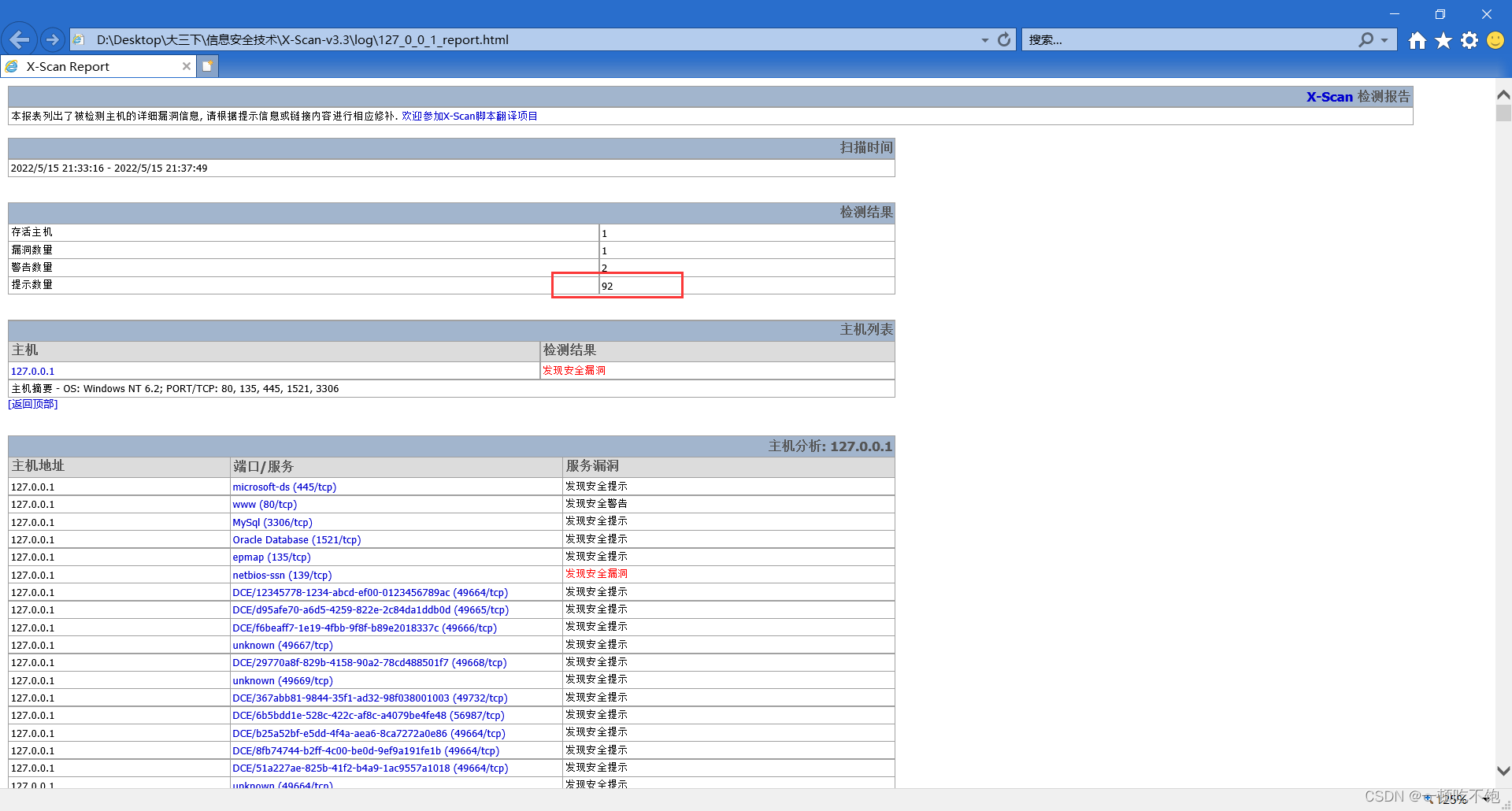
Scan complete , The report found 92 A loophole
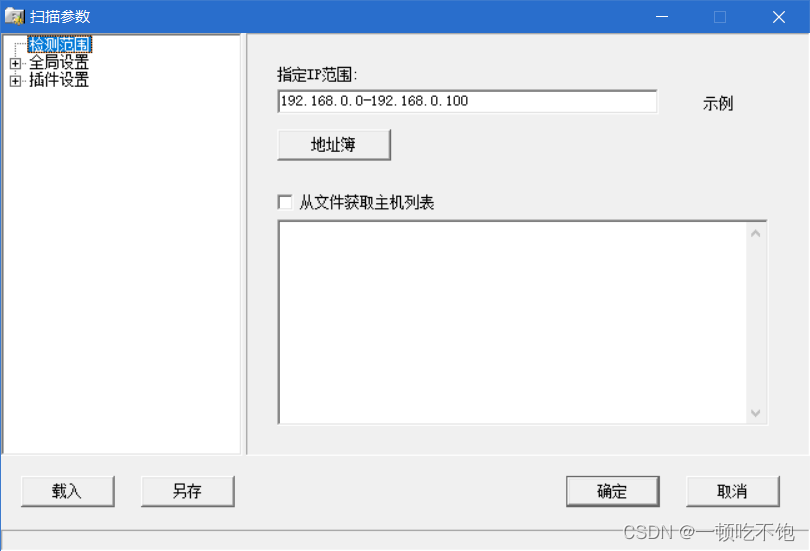
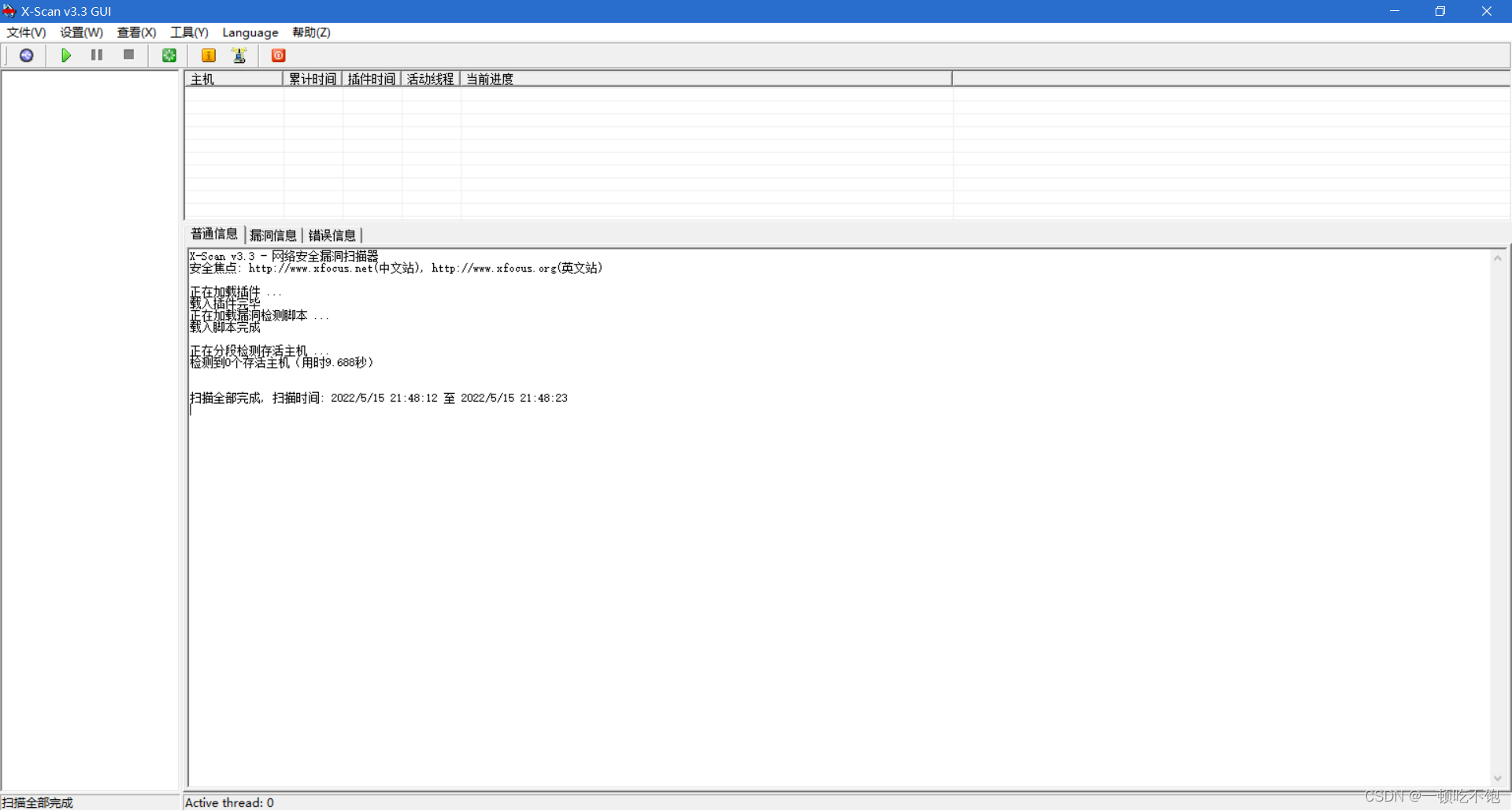
3. For network segment 192.168.0.0-192.168.0.100 scan
Scan complete , There is no loophole
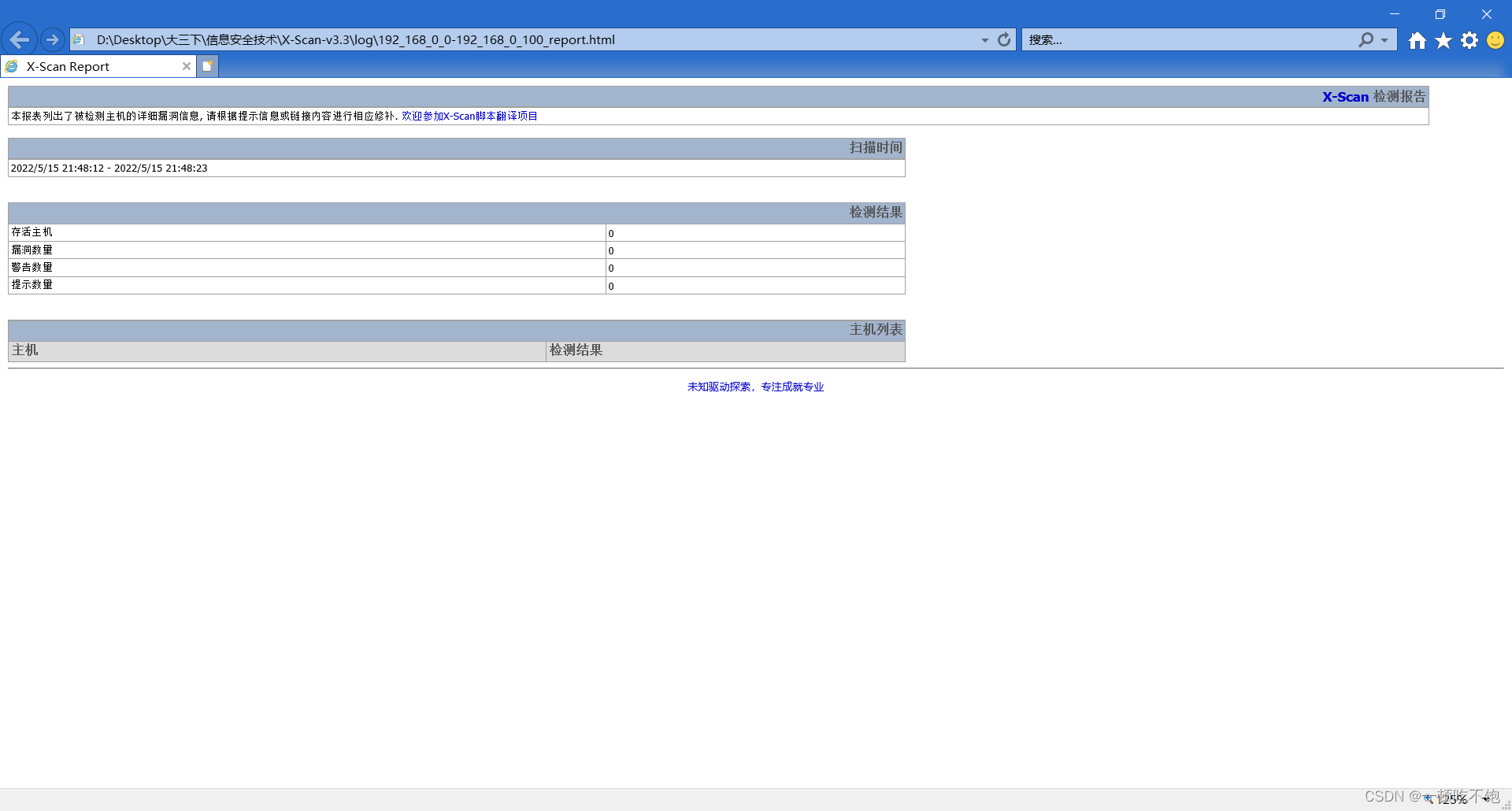
5、 ... and 、 Summarize and analyze
When installing software and using software for port scanning , Close the firewall and real-time protection of the system , Otherwise, it will be forcibly stopped as malware . Through this experiment , I got hold of X-Scan How to use , And how to configure and scan ports .
边栏推荐
- Final keyword
- Zen - batch import test cases
- Mysql database index study notes
- Kubernetes cluster capacity expansion to add node nodes
- 寄存器地址名映射
- Sublime Text4 download the view in bower and set the shortcut key
- What is the rating of Huishang futures company? Is it safe to open an account? I want to open an account, OK?
- How long does the PMP usually need to prepare for the exam in advance?
- C语言指针(中篇)
- JVM 内存结构 详细学习笔记(一)
猜你喜欢
信息安全实验一:DES加密算法的实现

Expérience de port série - simple réception et réception de données
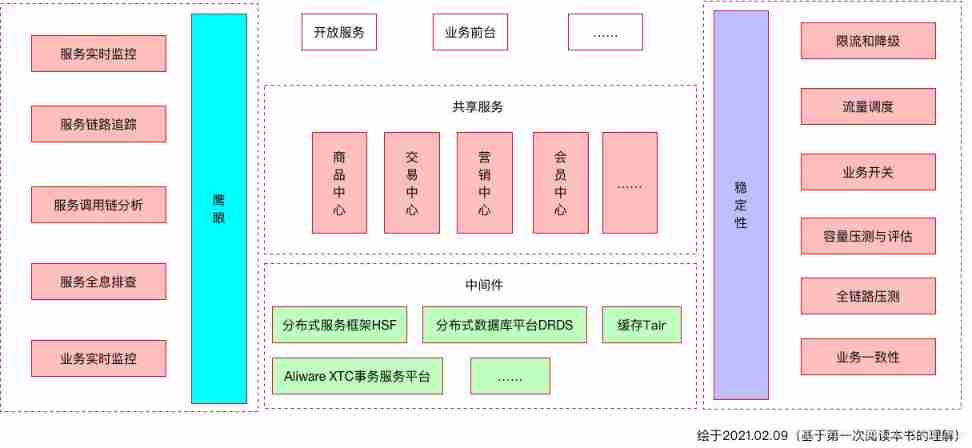
Reflections on the way of enterprise IT architecture transformation (Alibaba's China Taiwan strategic thought and architecture practice)
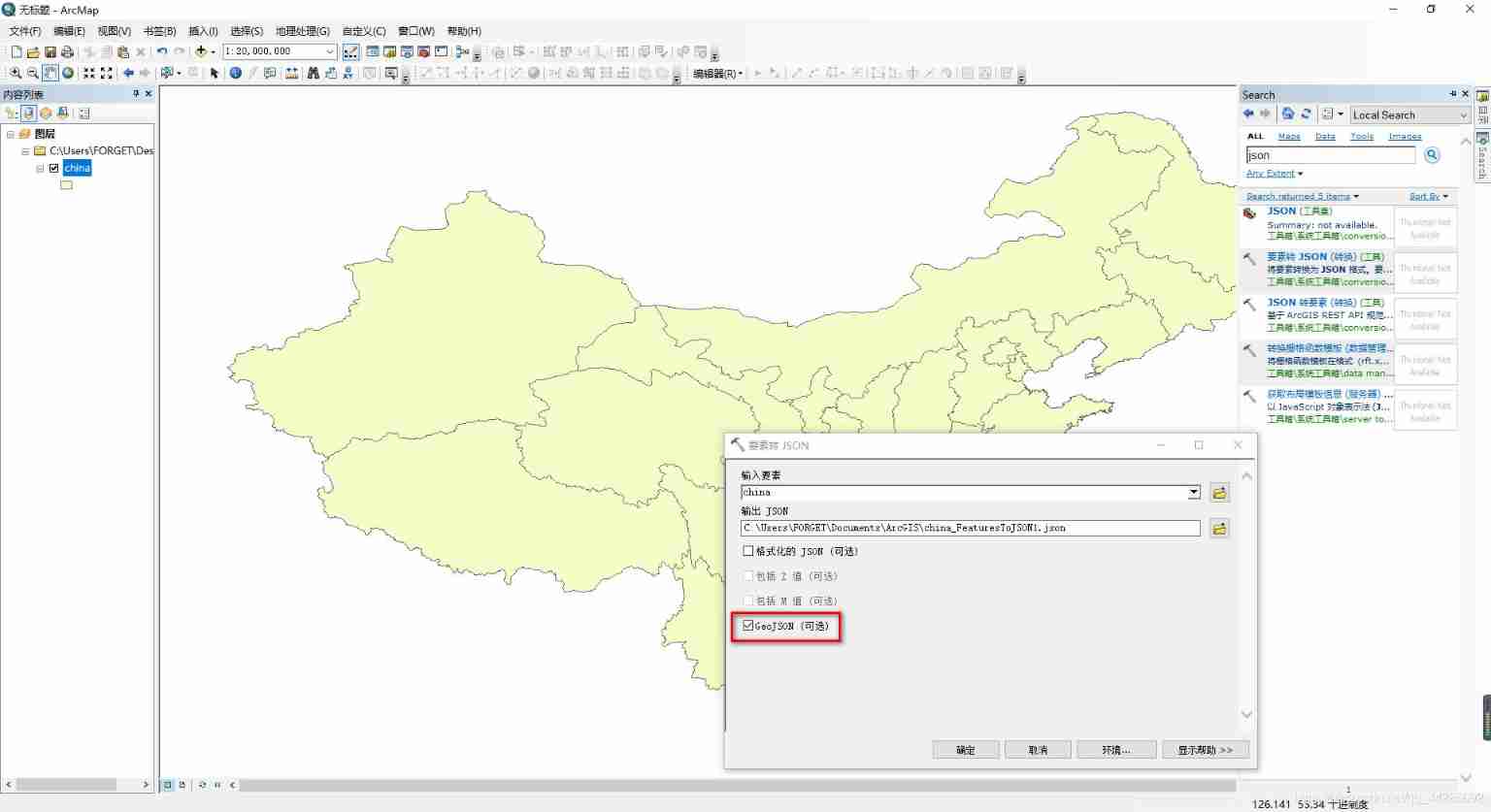
Cesium load vector data
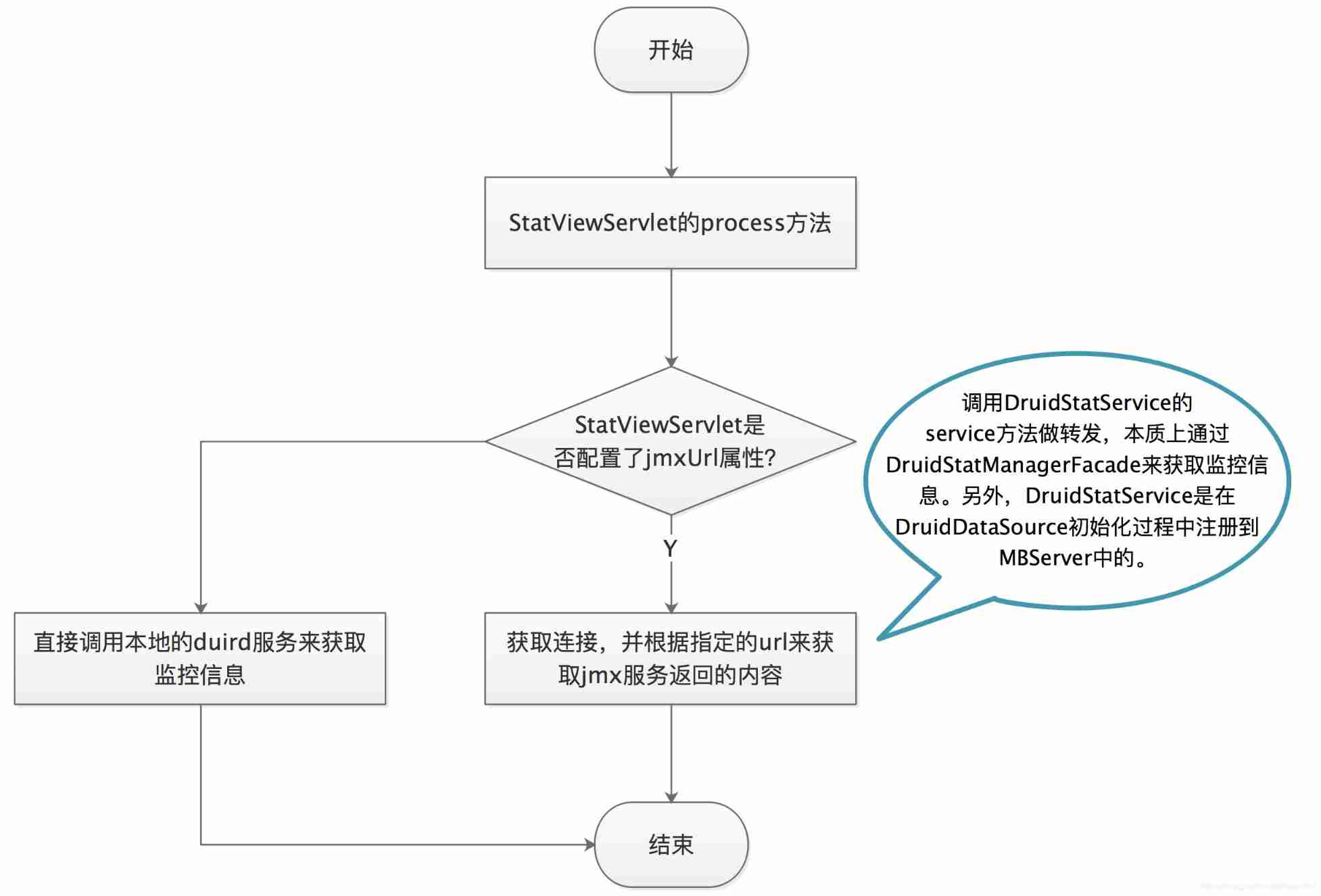
Druid monitoring - Introduction to JMX usage and principle
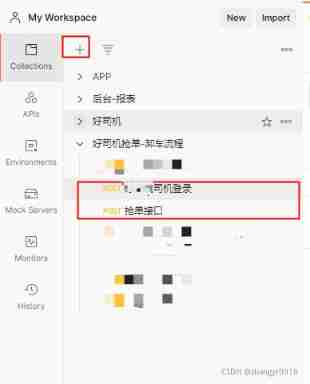
Data association between two interfaces of postman
【云原生】DevOps(一):DevOps介绍及Code工具使用
C language pointer (special article)

How long does the PMP usually need to prepare for the exam in advance?
Regular matching starts with XXX and ends with XXX
随机推荐
網易雲微信小程序
C语言指针(特别篇)
How to pass the PMP Exam in a short time?
Mysql database lock learning notes
Analysis of Hessian serialization principle
Schema-validation: wrong column type encountered in column XXX in table XXX
Final keyword
What is the value of getting a PMP certificate?
Mysql database index study notes
On December 8th, 2020, the memory of marketing MRC application suddenly increased, resulting in system oom
[SVN] what is SVN? How do you use it?
Serial port experiment - simple data sending and receiving
Variable parameter of variable length function
Postman interface test (II. Set global variables \ sets)
Jmeters use
STM32 clock system
What is MD5
C language pointer (special article)
Upgrade Alibaba cloud RDS (relational database service) instance to com mysql. jdbc. exceptions. Troubleshooting of jdbc4.communicationsexception
信息安全实验三 :PGP邮件加密软件的使用