当前位置:网站首页>Final review of information and network security (full version)
Final review of information and network security (full version)
2022-07-06 17:21:00 【bestkasscn】
Information and network security
The following link is based on the notes given by the teacher , Students can refer to Key notes
List of articles
- Information and network security
- Chapter one summary
- Chapter two Information encryption technology
- The third chapter Digital signature technology
- Chapter four Information Hiding Technology
- The fifth chapter Application layer security technology
- Chapter six Computer virus and prevention
- Chapter vii. A firewall
- Chapter viii. intrusion detection system
- Chapter nine Network security protocol
- Chapter ten VPN technology
- Chapter 11 Wireless network and security evaluation
Chapter one summary
1.1 Basic concepts
Information security Refers to the hardware in the information network 、 The data in the software and its system is protected , Not damaged by accidental or malicious causes 、 change 、 Let the cat out of the 、 Deny, etc , The system operates continuously, reliably and normally , Information services are uninterrupted .
Information security threats It refers to certain factors ( people 、 matter 、 event 、 Such method ) Possible harm to the safe use of information system .
1.2 attack
Concept
attack : Only when the intrusion is completely completed , And the behavior that the intruder has entered the target network is called attack . But a more positive view is : All actions that may damage a network are called attacks . That is, from the moment when an intruder starts working on the target plane , The attack begins .
classification
- Leak information : It refers to the intentional or unintentional leakage or loss of sensitive data .
- Destroy information : Steal the right to use the data by illegal means , Delete 、 modify 、 Insert or resend some important information , To get a response that benefits the attacker ; Malicious addition , Modifying data , To interfere with the normal use of users .
- Denial of service : It constantly interferes with the network service system , Affect the use of normal users , Even legal users are excluded from entering the computer network system or getting corresponding services .
Common means
- Password intrusion
- Backdoor software means
- Monitoring method
- E-mail technology
- Electronic deception
- DoS attack ( Denial of service attacks )
1.3 The purpose of information security
Three core elements of information security ( Also known as CIA Three elements )
- Confidentiality
- integrity
- Usability
Typical technology of information security
- Information encryption technology ( Based on cryptography )
- Firewall technology
- Vulnerability scanning technology
- Intrusion Detection Technology
- Anti virus technology
- Network security tunnel technology (VPN)
Chapter two Information encryption technology
2.1 Information security and cryptography
Basic concepts of cryptography
cryptography (Cryptology) It's a combination of Mathematics 、 Computer science 、 It is an interdisciplinary subject integrating electronics and communication , The science of information system security . Originated from secure communication technology . In particular , A science that studies the security and authentication of information systems .
cryptography It's information security The core and key technology
History of cryptography
Classical code
- Manual password
- Mechanical code
Modern code
1976 Public key encryption system was proposed in
Modern code
2.2 Classic examples of cryptography
Classical code
Replace password : Rearrange the plaintext according to certain rules , Break the structural characteristics of plaintext . Its characteristic is to keep all characters of plaintext unchanged , It just disrupts the position and order of plaintext characters .
A typical example :
Caesar( Caesar code )
principle ¶
Caesar code (Caesar) When encrypting, the Every letter All in alphabetical order back ( Or forward ) Move a fixed number ( Cyclic movement ) As a cipher . for example , When the offset is shifted left 3 When ( The key for decryption is 3):
Plaintext alphabet :ABCDEFGHIJKLMNOPQRSTUVWXYZ Ciphertext alphabet :DEFGHIJKLMNOPQRSTUVWXYZABCWhen using , The encryptor looks for the location of each letter in the message to be encrypted in the plaintext alphabet , And write down the corresponding letters in the ciphertext alphabet . The person who needs to decrypt operates in reverse according to the previously known key , Get the original plaintext . for example :
Plaintext :THE QUICK BROWN FOX JUMPS OVER THE LAZY DOG Ciphertext :WKH TXLFN EURZQ IRA MXPSV RYHU WKH ODCB GRJExample
The ciphertext is known as vzsx, The displacement is 3, Ask for clear text ? Explain : First step , Write the corresponding position of the letters in the ciphertext ( Subscript ), for instance a First in the alphabet , Write it as 1( Write it down as 0 It's fine too , The last letter z = 25) So we can write v = 22,z = 26,s = 19,x = 24 The second step , Because the displacement is 3, So we reduce all the above figures 3, namely 19,23,16,21 The third step , Restore the above numbers to letters ,19 Corresponding s,23 Corresponding w,16 Corresponding p,21 Corresponding u, We solved plaintext swpu.
Replace the password : Replace , Is to convert one letter in plaintext from other letters 、 Numbers or symbols replace One way .
Common substitution passwords
- Single table substitution (caesar, Affine code ( The exam does not require ))
- Multi table substitution (PlayFair,vigenere( Virginia code ),Hill( The hill code ))
A typical example :
- PlayFair
principle ¶
Playfair password (Playfair cipher or Playfair square) It's a replacement password ,1854 By Charles, an Englishman · Wheatstone (Charles Wheatstone) The invention , The basic algorithm is as follows :
- Select a string of English letters , Remove repeated letters , Add the remaining letters one by one 5 × 5 Within the matrix , The rest of the space is divided by the English letters not added a-z Join in the order of . Be careful , take q Remove , Or will i and j Treat as the same word .
- Divide the plaintext to be encrypted into two groups . If the letters in the group are the same , take X( or Q) Add to the first letter of the group , Regroup . If there is one word left , Also joined X .
- In each group , Find out where the two letters are in the matrix .
- If two letters don't go in the same line, they will be in different columns , Find the other two letters in the matrix ( The line corresponding to the first letter takes precedence ), Make the four letters into the four corners of a rectangle .
- If two letters go together , Take the letter to the right of these two letters ( If the letter is on the right, take the letter on the left ).
- If two letters are in the same column , Take the letter below these two letters ( If the letter is at the bottom, take the letter at the top ).
The newly found two letters are the result of the original two letter encryption .
With playfair example For the key , have to
P L A Y F
I R E X M
B C D G H
K N O Q S
T U V W Z
The message to be encrypted is Hide the gold in the tree stump
HI DE TH EG OL DI NT HE TR EX ES TU MP
Will get
BM OD ZB XD NA BE KU DM UI XM MO UV IF
Human speaking version
Choose a key first , For example, the key is NSSCTF, Then we put this key into a 5x5 In the form of , Don't repeat letters .
N S C T F How to fill the remaining boxes ? According to the alphabet A-Z Fill in in sequence , As usual , Don't repeat letters . There is also a requirement to be met : Or don't Q This letter , Or put I/J Write it together , Just choose one .
N S C T F A B D E G H I/J K L M O P Q R U V W X Y Z That's it
For example, the sentence we want to encrypt is :“Reach the highest City”, Let's group it in pairs
RE AC HT HE HI GH ES TC IT Yhere Y Alone, right ? We'll fill in the letters that fall alone X
Let's look at the relative position of the second group of letters
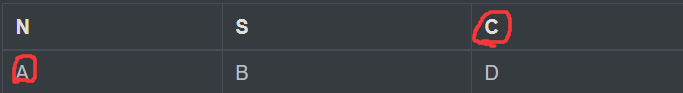
A and C Not in the same row or column, right ? At this time, we need to find two letters to make them connect into a rectangle , This is obviously N,D Two letters , But what is the order ? Because in this group of letters A in front , So we take A This line takes precedence , Follow R The same line is D, So the first group of ciphertext is DN
Let's look at a group of peer examples HI
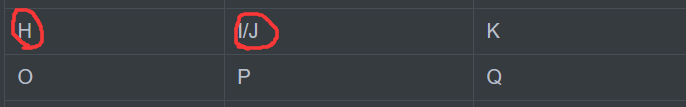
In this case , We'll find the letter after him ,H -> I/J ,I/J -K , So the ciphertext is I/J K
Let's look at a group of examples with the same column RE
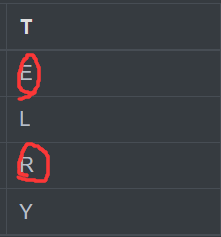
Or go to the letter after him R -> Y,E -> L, The secret is YL
This is it. PlayFair Encryption process
Playfair The advantages of passwords ( Non emphasis )
Playfair Passwords have made great progress compared with simple single letter substitution passwords
Although only 26 Letters , But there are 26×26=676 Two letter pairs , therefore , Identifying letter pairs is much more difficult than individual letters .
There are many possible substitutions of ciphertext letters for a plaintext letter , Makes frequency analysis much more difficult (hs Become BP,hq Become YP)
Playfair Passwords used to be considered unbreakable .
vigenere( Virginia code )
principle ¶
Virginia code (Vigenere) Is an encryption algorithm that USES a series of Caesar codes to form a cipher alphabet , A simple form of a multitable password .

Here is an example
Plaintext :come greatwall secret key :cryptoFirst , Fill the key so that its length is the same as that of plaintext .
Plaintext c o m e g r e a t w a l l secret key c r y p t o c r y p t o c secondly , Look up the table and get the ciphertext

Plaintext :come greatwall secret key :crypto Ciphertext :efkt zferrltznHuman speaking version
It's similar to Caesar's code , First convert the letters into subscript form (a = 0,b = 1…)
For example, plaintext is NSSCTF, The key is SWPU, How to encrypt ?
First turn the letter into the corresponding subscript .( Quote a picture of the teacher )

NSSCTF -> 13 18 18 2 19 5
SWPU -> 18 22 15 20
We write the key under the plaintext , Until it's full
NSSCTF SWPUSWMeet the following formula
Add The secret : c i = p i + k i ( m o d 26 ) Explain The secret : p i = c i − k i ( m o d 26 ) encryption :c_i = p_i + k_i (mod26)\\ Decrypt :p_i = c_i - k_i(mod 26) Add The secret :ci=pi+ki(mod26) Explain The secret :pi=ci−ki(mod26)
What does that mean , Didn't we just turn letters into numbers , Let's calculate , The first letter of the ciphertext is (13 + 18) % 26 = 5 -> FThe second letter is (18 + 22) % 26 = 14 -> O
…
The final ciphertext is FOHWLB
How to decrypt , Let's use the decryption formula to calculate .
The first letter of the plaintext is (5 - 18)% 26 = 13 -> N, The second letter is (14 - 22) % 26 = 18 -> S
…
The final clear text is NSSCTF
Hill( The hill code )
principle ¶
The hill code (Hill) Use the order of each letter in the alphabet as its corresponding number , namely A=0,B=1,C=2 etc. , Then convert the plaintext to n Dimension vector , With one n × n Matrix multiplication of , Then the result is modeled 26. Note the matrix used for encryption ( The key ) stay Zn26
It must be reversible , Otherwise, it is impossible to decode . Only the determinant of the matrix and 26 Coprime , Is reversible . Here's an example
Plaintext :ACTTake Ming culture as a matrix .
[ 0 2 19 ] \begin{bmatrix} 0\\ 2\\ 19\\ \end{bmatrix} ⎣⎡0219⎦⎤
Suppose the key is :
[ 6 24 1 13 16 10 20 17 15 ] \begin{bmatrix} 6 & 24 & 1\\ 13 & 16&10\\ 20 & 17 & 15\\ \end{bmatrix} ⎣⎡6132024161711015⎦⎤The encryption process is :
[ 6 24 1 13 16 10 20 17 15 ] [ 0 2 19 ] = [ 67 222 319 ] ( m o d 26 ) = [ 15 14 7 ] \begin{bmatrix} 6 & 24 & 1\\ 13 & 16&10\\ 20 & 17 & 15\\ \end{bmatrix} \begin{bmatrix} 0\\ 2\\ 19\\ \end{bmatrix} = \begin{bmatrix} 67\\ 222\\ 319\\ \end{bmatrix} (mod 26) = \begin{bmatrix} 15\\ 14\\ 7\\ \end{bmatrix} ⎣⎡6132024161711015⎦⎤⎣⎡0219⎦⎤=⎣⎡67222319⎦⎤(mod26)=⎣⎡15147⎦⎤The ciphertext is
Ciphertext :POHMaybe some students forget how to calculate linear algebra , Let's calculate it here
We multiply the plaintext matrix by the first row of the key matrix , Namely 6*0 + 24*2 + 1*19 = 67 The second line multiplies the plaintext matrix :13*0 + 16*2 + 10*19 = 222 The third line multiplies the plaintext matrix :20*0 + 17*2 + 15*19 = 319 The matrix is 3 * 3 X 3 * 1 = 3 * 1 So the final matrix is a matrix with three rows and one column , And then to 26 The number obtained by modulo is the subscript of the letter .
2.3 Basic concepts of cryptography
Cryptography
- The basic idea of cryptography is to disguise information .
- Camouflage is to apply a reversible mathematical transformation to data , The data before camouflage is called plaintext , The camouflaged data is called ciphertext , The process of camouflage is called encryption , The process of removing the disguise and recovering the plaintext is called decryption . The process of encryption and decryption should be carried out under the control of the key .
- cryptography (Cryptology): Study the science of information system security . It contains two branches :
- Cryptography
- Cryptanalysis
Explanation of some terms in cryptography
A password ( encryption ) The system consists of plaintext 、 Ciphertext 、 encryption algorithm 、 Decryption algorithm 、 The key consists of five parts .
- Plaintext M: The original information as encrypted input , That is, the original form of the message
- Ciphertext C: The result of encrypted transformation of plaintext , That is, the form of the message after being encrypted
- secret key K: Is the parameter involved in password transformation
- encryption algorithm E: Is a transformation function that transforms plaintext into ciphertext , The corresponding transformation process is called encryption , That is, the process of coding
- Decryption algorithm D: Is the transformation function that restores the ciphertext to plaintext , The corresponding transformation process is called decryption
Data security is based on the key rather than the confidentiality of the algorithm ( This is the point )
For a cryptosystem , Its algorithm can be disclosed , Let everyone use 、 Research . But for the key used in a certain encryption process , Is confidential .
Classified by the way the key is used
Asymmetric encryption ( Public key cryptosystem )
The key used for encryption is different from the key used for decryption , And the decryption key cannot be deduced from the encrypted key .
Use public key KP Encrypting plaintext can be expressed as :EKP(M)=C
Use the corresponding private key KS Decryption of ciphertext can be expressed as :DKS=M
Symmetric encryption
The key used to encrypt data is the same as the key used to decrypt data , Or there is a definite mathematical relationship between the two .
encryption :EK(M)=C
Decrypt :DK=M
2.4 Symmetric cryptography
Concept
To put it bluntly, the encryption key is the same as the decryption key .
Security
- The encryption algorithm is secure enough
- Key security ( If the key is too simple , It can be easily exploded by the computer )
Advantages and disadvantages
advantage : Fast encryption and decryption 、 High confidentiality
shortcoming : How to securely transfer keys ( If the key is intercepted on the network GG)、 The number of keys needed for multi person distribution will increase rapidly
classification
Sequence code
For a single bit of plaintext ( Or bytes ) Algorithm for operation , Also known as stream cipher
It should be noted that , At present, stream encryption is symmetric encryption .
The more random the sequence generated by the pseudo-random number generation algorithm is , The statistical features in plaintext are better covered .
Stream encryption and decryption is very simple , In the case of known plaintext , It's very easy to get the key stream .
The key of stream cipher is to design a good pseudo-random number generator . Generally speaking , The basic construction module of pseudo-random number generator is feedback shift register . Of course , There are also some specially designed stream ciphers , such as RC4.
Group password
Divide the plaintext information into different blocks ( Or groups ) structure , For each block ( Or groups ) Encryption and decryption
Actually , We can also understand block encryption as a special alternative password , But each time it replaces a large piece . And because of a big piece , The clear text space is huge , And for different keys , We can't make a table to correspond to the corresponding ciphertext , So there has to be complex Encryption and decryption algorithm to encrypt and decrypt ciphertext .
And at the same time , Plaintext can often be very long or very short , Therefore, two assistants are often needed in block encryption
- padding, namely padding To the specified grouping length
- Packet encryption mode , That is, the way of plaintext block encryption .
So block cipher has the following requirements
- The packet length is large enough
- The key volume space is large enough
- Encryption transformation is complex enough
- Encryption and decryption operations are simple , Generally, addition 、 Multiplication 、 Simple operations such as XOR and shift
- The logical structure of encryption and decryption should be consistent .
2.5 Symmetric encryption algorithm
DES、AES
It's too hard for me to ..
2.6 Asymmetric ( Public key ) encryption algorithm
The basic principle
Based on one-way trapdoor function
What is a one-way trapdoor function ? take RSA Examples of algorithms , Give you two prime numbers , It's easy for you to calculate their product , But if you are given a number to calculate its two prime factors, it is very difficult , You can write your own code to realize , This is the one-way trapdoor function , It's easy to calculate forward , The reverse is difficult , The security of public key cryptography is based on such a mathematical problem
The specific implementation steps are as follows RSA Algorithm as an example
Application scenarios
- Protect data confidentiality
- Achieve authentication / Message integrity ( Digital signature algorithm )
- Solve the problem of key distribution
RSA
Introduce
RSA Encryption algorithm is an asymmetric encryption algorithm . In public key cryptography and e-commerce RSA Widely used .RSA yes 1977 Ronald · Levister (Ron Rivest)、 ADI · Samore (Adi Shamir) And Leonard · Adelman (Leonard Adleman) Put forward together .RSA It's a combination of the three of them .
RSA The reliability of the algorithm is determined by the difficulty of maximum integer factor decomposition . In other words , The more difficult it is to factorize a large integer ,RSA The more reliable the algorithm . If someone finds a fast factorization algorithm , Then use RSA The reliability of encrypted information is bound to decline dramatically . But the possibility of finding such an algorithm is very small . Now , Only short ones RSA The key can be broken in a powerful way . To 2017 In so far , There are no reliable attacks yet RSA The way of the algorithm .
The basic principle
Generation of public and private keys ¶
- Randomly select two different large prime numbers p and q, Calculation N=p×q
- According to the Euler function , Get φ(N)=φ§φ(q)=(p−1)(q−1)
- Choose one less than φ(N) The integer of e, send e and φ(N) Coprime . And get e About φ(N) The modulo inverse elements of , Name it d, Yes ed≡1(modφ(N))
- take p and q Of records destroyed , here ,(N,e) It's the public key ,(N,d) It's the private key .
Message encryption
c = m^e mod N
m = c^d mod N
Explanation of some mathematical terms
Prime number ( prime number ): It can only be 1 And the number divisible by itself
Euler function φ(N): Is equal to (p-1)*(q-1)
Modular arithmetic
Modular operation is somewhat similar to the basic four operations , Except division . The rules are as follows :
(a + b) % p = (a % p + b % p) % p
(a - b) % p = (a % p - b % p) % p
(a * b) % p = (a % p * b % p) % p
a ^ b % p = ((a % p) ^ b) % p
Associative law
- ((a + b) % p + c) = (a + (b + c) % p) % p
- ((a * b) % p * c) = (a * (b * c) % p) % p
Commutative law
- (a + b) % p = (b + a) % p
- (a * b) % p = (b * a) % p
Distributive law
- (a + b) % p = (a % p + b % p) % p
- ((a + b) % p * c) % p = ((a * c) % p + (b * c) % p
Module inverse element
Inverse element refers to the group in the field of Mathematics G Any element in a, All in G There is a unique inverse element in a’, Have the quality of a · a’ = a’ · a = e ( · Operations defined for this group ). among ,e Is the unit element of the group . The inverse element is actually the expansion of the inverse number in addition and the reciprocal in multiplication .
In modular operations , The unit yuan is 1.
a mod p The inverse of can make a * a’ mod p = 1 Minimum a’.
because b’ by b Inverse element ,b * b’ mod p = 1;
therefore (a / b) mod p = (a * b’) mod p , But ask for a | b;
So we can apply (a * b) % p = (a % p * b % p) % p This property reduces the intermediate operation result .
Take the code for example
We use it python To realize the encryption and decryption process
from Crypto.Util.number import *
import gmpy2
# Select two large prime numbers p,q
p = getPrime(128)
q = getPrime(128)
# To calculate the N
N = p * q
# Calculating Euler function phiN
phiN = (p - 1) * (q - 1)
# Choose a prime number e, requirement e and phiN Coprime (phiN Not divisible e)
e = 17
# Calculate private key d, In fact, the extended Euclidean algorithm is used here to solve the modular inverse , Later on
d = gmpy2.invert(e, phiN)
# This is the plaintext we want to encrypt
m = 'this is a test'
# We first convert the plaintext to byte type , Then convert it into decimal digits
m = bytes_to_long(m.encode())
# To encrypt c = m^e mod N
c = pow(m, e, N)
print(c)
# To decrypt m = c^d mod N
m = pow(c, d, N)
# At this time, the plaintext is of decimal number type , Convert to byte type
m = long_to_bytes(m)
print(m)
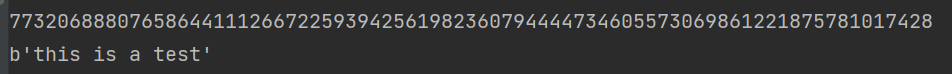
d How to ask for ?
We already know d The solution of is based on this formula :ed≡1(modφ(N)), First ≡ What does this symbol mean ? This is the congruence symbol in number theory , It means two integers divided by the same integer , If you get the same remainder , Then two integers are congruent , If this formula is to be translated into something that people can understand , How to transform it ? For scenes with small numbers , You can use this formula ed + phiNy = 1, among y Is a negative integer ,d As a positive integer , It can be downloaded from y = -1 Start , To solve d Whether it is a positive integer , Take the last assignment as an example
It is designed to be used by both sides of communication RSA Encryption system , The public key of the receiver is (n, e) = (35,5), The received ciphertext is C = 10, Ask for clear text M.
n = 35 , The result of multiplying two prime numbers is 5*7, Calculating Euler function phiN = (5-1)*(4-1) = 24, At this time, use our above formula to solve d
namely ed+phiNy = 1 -> 5*d + 24*y = 1
take y = -1,z Then the equation becomes 5*d - 24 = 1 -> d = 5
d It happens to be a positive integer 5, And then according to the formula m = c^d mod N -> M = 10^5 mod 35 = 5
If the number is a little larger , We need to use extended Euclidean algorithm
extended euclidean algorithm
Take the teacher as an example ppt Take the example above as an example
e = 1234 ,phiN = 11111, seek d=?
First , If this d exist , We use it phiN Divide e( Reserved remainder ) namely 11111 / 1234 = 9 ...5 -> 11111 = 9*1234 + 5
Count again 1234 / The remainder of the last time 5 = 246 ...4 -> 1234 = 246*5 + 4
5 / 4 = 1...1 -> 5 = 4*1 + 1
Divide by 1 It's over , Then we write this string of expressions in reverse
1 = 5-1*4
4 = 1234-246*5
5 = 11111-9*1234
Take it in and you'll get 1 = (5-1*(1234-246*5))
according to ed = 1 mod phin
namely 1234*d = (5-1*(1234-246*5)) mod phin
Simplify
Wrong version !!!
1234 ∗ d = ( 5 − 1 ∗ ( 1234 − 246 ∗ 5 ) ) m o d p h i n = ( 5 − 1234 + 246 ∗ 5 ) m o d p h i n = ( 247 ∗ 5 − 1234 ) m o d p h i n = [ 247 ∗ ( 11111 − 9 ∗ 1234 ) − 1234 ] m o d p h i n = ( 11111 ∗ 247 − 9 ∗ 247 ∗ 1234 − 1234 ) m o d p h i n = ( 11111 ∗ 247 − 2224 ∗ 1234 ) m o d p h i n ∵ p h i n = 11111 , 11111 ∗ 247 m o d 11111 = 0 ∴ 1234 ∗ d = − 2224 ∗ 1234 m o d 11111 this in I Write wrong 了 Brother brother People ! ! most after One Step yes Yes − 2224 take model d = 2224 yes wrong Of ! ! \begin{aligned} 1234*d &= (5-1*(1234-246*5))\ mod \ phin\\ &=(5-1234+246*5)\ mod \ phin\\ &=(247*5 - 1234) \ mod \ phin\\ &=[247*(11111-9*1234) - 1234] \ mod \ phin\\ &=(11111*247-9*247*1234-1234) \ mod \ phin\\ &=(11111*247 - 2224*1234) \ mod \ phin\\ &\because phin\ = 11111,11111*247 \ mod \ 11111 = 0\\ &\therefore \ 1234*d= -2224*1234 \ mod \ 11111\\ & I made a mistake here, brothers !!\\ & The last step is to -2224 modulus \\ d &=2224 It's wrong. !! \end{aligned} 1234∗dd=(5−1∗(1234−246∗5)) mod phin=(5−1234+246∗5) mod phin=(247∗5−1234) mod phin=[247∗(11111−9∗1234)−1234] mod phin=(11111∗247−9∗247∗1234−1234) mod phin=(11111∗247−2224∗1234) mod phin∵phin =11111,11111∗247 mod 11111=0∴ 1234∗d=−2224∗1234 mod 11111 this in I Write wrong 了 Brother brother People !! most after One Step yes Yes −2224 take model =2224 yes wrong Of !!
Negative modulo
x m o d y = x − y ∗ [ x y ] ( towards Next take whole ) = − 2224 − 11111 ∗ ( − 2224 11111 ) = − 2224 + 11111 = 8887 ∴ d = 8887 \begin{aligned} x \ mod \ y &= x - y * [\frac{x}{y}]( Rounding down )\\ &= -2224 - 11111 * (\frac{-2224}{11111})\\ &= -2224 + 11111\\ &= 8887\\ \therefore d&=8887 \end{aligned} x mod y∴d=x−y∗[yx]( towards Next take whole )=−2224−11111∗(11111−2224)=−2224+11111=8887=8887
Thank you for pointing out your mistakes
How to calculate m^emod n
Use fast power modular algorithm , I haven't studied the principle , We're not going to teach you how to do it , Take the teacher as an example ppt Take the example above as an example
Use the fast modular exponential algorithm to find c1=m1^e(mod n) =104^13 mod 2537 Value ?
Let's interpret this code
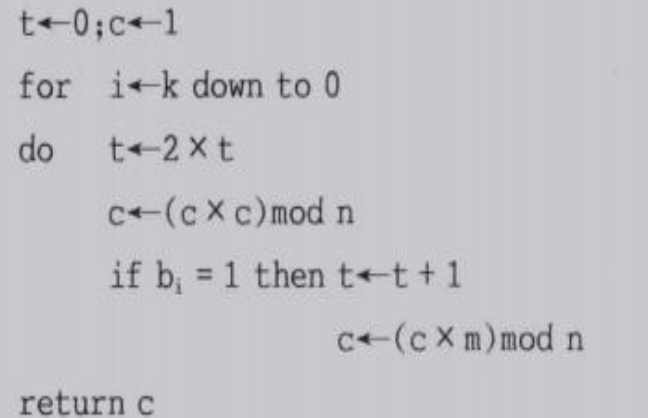
First round code
t = 0 , c = 1 , i = 3 t = t ∗ 2 ( t = 0 ) c = c ∗ c m o d 2537 ( c = 1 ) i f b 3 = = 1 ( full foot ) : t = t + 1 ( t = 1 ) c = 1 ∗ 104 m o d 2537 ( c = 104 ) \begin{aligned} &t=0,c=1,i=3\\ &t = t*2\ (t=0)\\ &c = c*c \ mod \ 2537 \ (c=1)\\ &if \ b_3 == 1( Satisfy ):\\ &t = t+1 \ (t=1)\\ &c = 1*104\ mod\ 2537\ (c=104)\\ \end{aligned} t=0,c=1,i=3t=t∗2 (t=0)c=c∗c mod 2537 (c=1)if b3==1( full foot ):t=t+1 (t=1)c=1∗104 mod 2537 (c=104)
Second round code
t = 1 , c = 104 , i = 2 t = t ∗ 2 ( t = 2 ) c = c ∗ c m o d 2537 ( c = 668 ) i f b 2 = = 1 ( full foot ) : t = t + 1 ( t = 3 ) c = 668 ∗ 104 m o d 2537 ( c = 973 ) \begin{aligned} &t=1,c=104,i=2\\ &t = t*2\ (t=2)\\ &c = c*c \ mod \ 2537 \ (c=668)\\ &if \ b_2 == 1( Satisfy ):\\ &t = t+1 \ (t=3)\\ &c = 668*104\ mod\ 2537\ (c=973)\\ \end{aligned} t=1,c=104,i=2t=t∗2 (t=2)c=c∗c mod 2537 (c=668)if b2==1( full foot ):t=t+1 (t=3)c=668∗104 mod 2537 (c=973)
Third round code
t = 3 , c = 973 , i = 1 t = t ∗ 2 ( t = 6 ) c = c ∗ c m o d 2537 ( c = 428 ) i f b 1 = = 1 ( No full foot ) : \begin{aligned} &t=3,c=973,i=1\\ &t = t*2\ (t=6)\\ &c = c*c \ mod \ 2537 \ (c=428)\\ &if \ b_1 == 1( dissatisfaction ):\\ \end{aligned} t=3,c=973,i=1t=t∗2 (t=6)c=c∗c mod 2537 (c=428)if b1==1( No full foot ):
Fourth round code
t = 6 , c = 428 , i = 1 t = t ∗ 2 ( t = 12 ) c = c ∗ c m o d 2537 ( c = 520 ) i f b 1 = = 1 ( full foot ) : t = t + 1 ( t = 13 ) c = 520 ∗ 104 m o d 2537 ( c = 803 ) \begin{aligned} &t=6,c=428,i=1\\ &t = t*2\ (t=12)\\ &c = c*c \ mod \ 2537 \ (c=520)\\ &if \ b_1 == 1( Satisfy ):\\ &t = t+1 \ (t=13)\\ &c = 520*104\ mod\ 2537\ (c=803)\\ \end{aligned} t=6,c=428,i=1t=t∗2 (t=12)c=c∗c mod 2537 (c=520)if b1==1( full foot ):t=t+1 (t=13)c=520∗104 mod 2537 (c=803)
At this point, the code is running ,c Is our final result 803, We use it python Check it out
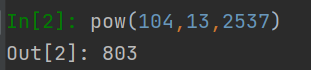
Correct .
RSA The security of the algorithm
RSA The security of the algorithm is a difficult problem based on Large Integer Decomposition , So the attack method is also very simple and rough , Because the public key is public ,n = p*q,e It is known that ,e * d = 1 mod phiN, So as long as we can decompose N Is two prime numbers p,q, Can crack d, Here are some common attack methods ( I don't think I can pass the exam , Those of you who are interested can take a look )
Violent decomposition
have access to yafu This tool , Use as follows :
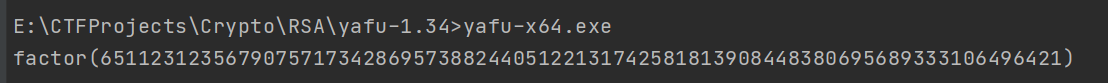
factor() function , The parameter is the number you want to decompose ,
Decomposition results
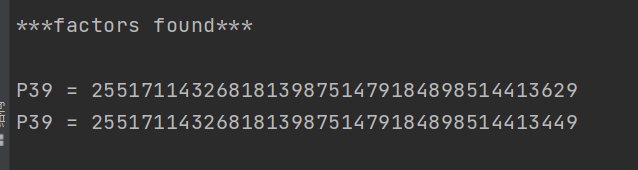
Common mode attack
Attack conditions ¶
When two users use the same module N、 Different private keys , Common mode attack exists when the same plaintext message is encrypted .
Attack principle ¶
Let the public keys of two users be e1 and e2, And the two are reciprocal . The clear text message is m, The ciphertext is :
c1=m^e1modN
c2=m^e2modN
When the attacker intercepts c1 and c2 after , Plaintext can be recovered . Use the extended Euclidean algorithm to find re1+se2=1modn Two integers of r and s, It can be obtained. :
cr1cs2≡mre1mse2modn
≡m(re1+se2)modn
≡mmodn
Code implementation
import gmpy2 from Crypto.Util.number import * import sys import binascii sys.setrecursionlimit(1000000) def egcd(a, b): if a == 0: return b, 0, 1 else: g, y, x = egcd(b % a, a) return g, x - (b // a) * y, y def modinv(a, m): g, x, y = egcd(a, m) if g != 1: raise Exception('modular inverse does not exist') else: return x % m e1=11085119 e2=9190891 c1=95802654515220808092268214474187396521084451096344242384608341887872702782290828816410697000941719590683107309925626046620976811737721800675450679405244429986569795481605454039209952126809031130572473139930816538229894404952230488471032140646478701800056893148667212842612771202600961005473843628543807576281789895225835535784697736508073945719275038557487868878529515390772120147529559169015697350455629223009240723598393858545457969371930544199690993535334876475403150437839542800975521617422860338848091674741969911523078015503201576312728495586541524742813914511874800249782937376857844116922101278519019905656 c2=3416491037051012037012939467509239901806773704813403690354665798385393352563464881951974370241490158340518054254272653945115953885714558484209218930263157351532115665285897349811123032115674114898665575574766463243374363257317681664993192800007993550862200779683771913077545068424882032234253291268535634268961963331194864584762384909221320182259740507346013284854960761334127762166029934217852574313390086250095835456562558784241431962078316429891165585256316059135820341820577055463538905611710942258927193841136883208222189378113731075034150942645682604044709019188371375927920059650896388569726047796473642120516 n=14129293489067735497835891913264472598235466604403612336006623107595438847067174121647397164285682966224208717924641463649550121959767200641904319708499428189547128930841593746541543006588640663582633284897803861765348725014771273881669308132805898675778540187033021154036594235144466199756659779020003038086388668345228666342476638806787610903886102447352152686433249208463728111915471444774767068270174477504938000592014963263451887545807532838102764510144961264142596092689778866428703620285541772740910077089202507682976490982442688834900108765694679294561760962915865812857912066376963510711262436193703892095683 s = egcd(e1, e2) s1 = s[1] s2 = s[2] if s1 < 0: s1 = - s1 c1 = modinv(c1, n) elif s2 < 0: s2 = - s2 c2 = modinv(c2, n) m = (pow(c1, s1, n) * pow(c2, s2, n)) % n print(long_to_bytes(m)) m = gmpy2.iroot(m, 9)[0] print(long_to_bytes(m))e And phiN Immutability
p and q The difference is too large or too small
Is the example of violent decomposition ,p and q Very close
Small plaintext attack
If the plaintext is too small , Resulting in plaintext e The power is still less than n, Modulus at this time n It doesn't work , We're right c open e Power can get plaintext m
Code implementation
from Crypto.Util.number import * import gmpy2 while True: try: p = getPrime(128) q = getPrime(128) m = 'abc' e = 3 n = p * q phin = (p - 1) * (q - 1) d = gmpy2.invert(e, phin) break except: pass m = bytes_to_long(m.encode()) c = pow(m, e, n) # Crack m = gmpy2.iroot(c, e)[0] print(long_to_bytes(m))
Low encryption index broadcast attack
It's about the same as above ,e Getting too little leads to m Of e The power is still less than n
Coppersmith partial information attack
It is known that p High or low , Use Coppersmith Crack the low position to achieve the purpose of attack
Here is a math tool sage Code for
n=113432930155033263769270712825121761080813952100666693606866355917116416984149165507231925180593860836255402950358327422447359200689537217528547623691586008952619063846801829802637448874451228957635707553980210685985215887107300416969549087293746310593988908287181025770739538992559714587375763131132963783147 p4=7117286695925472918001071846973900342640107770214858928188419765628151478620236042882657992902# It is known that P The high e=65537 pbits=512 #P Original digits kbits=pbits - p4.nbits() print (p4.nbits()) p4 = p4 << kbits PR.<x> = PolynomialRing(Zmod(n)) f = x + p4 roots = f.small_roots(X=2^kbits,beta=0.4) # After the above functions ,n and p Has been transformed into 10 Base number if roots: p= p4 + int(roots([0])) print ("n",n) print ("p",p) print ("q",n/p)wiener attack
e When it's too big , An algorithm based on the continued fraction theorem can be used to quickly solve d Value . because e If it is too large, the expression is the private key d It will be very small
github There is open source attack code on https://github.com/pablocelayes/rsa-wiener-attack
The third chapter Digital signature technology
3.1 brief introduction ( Quote from ctfwiki)
In everyday life , When we participate in an activity , You may need to sign , In order to prove that we were there ,,, Prevent the guide or something , Do you know ... But actually , This kind of signature can easily be forged , Find someone to sign for you , Or find someone who can imitate others' handwriting to help sign . In the computer world , We may need an electronic signature , Because we will use electronic documents in most cases , What to do at this time ? Of course , We can still choose to use our own names . But there is another way , That is to use digital signature , This kind of signature is more difficult to forge , More credible . The main purpose of digital signature is to ensure that the message really comes from the person who claims to produce the message .
digital signature (digital signature) Mainly used for digital messages (digital message) To sign , In case the message is forged or tampered with , It can also be used for identity authentication of both sides of communication .
Digital signatures rely on asymmetric passwords , Because we have to make sure that one side can do something , And the other side can't do such a thing . Its basic principle is as follows
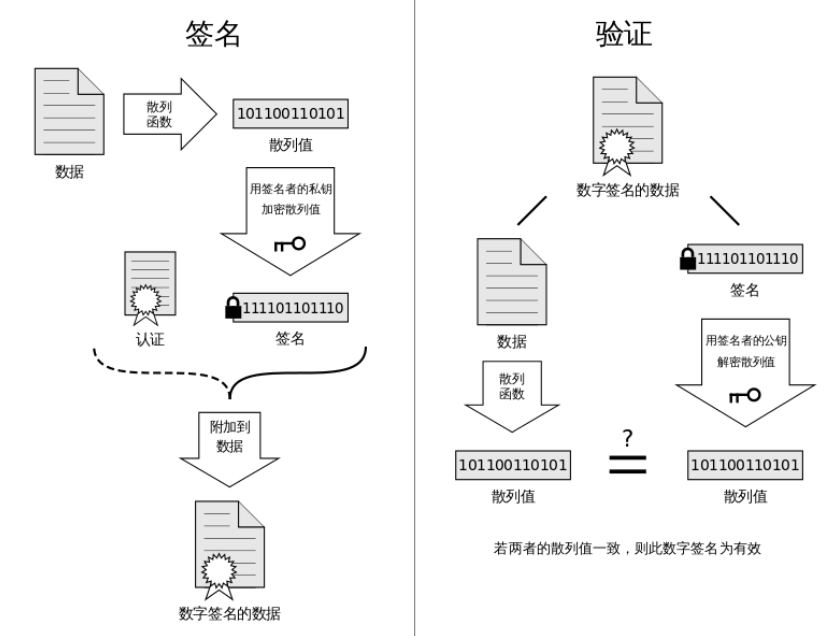
Digital signature should have the following characteristics :
(1) The signature is authentic : Anyone can verify the validity of the signature .
(2) Signatures are not forgeable : In addition to the legal signer , It is difficult for anyone else to forge their signature .
(3) Signatures are not reproducible : The signature of one message cannot be changed into the signature of another message by copying . If the signature of a message is copied from elsewhere , Then anyone can find the inconsistency between the message and the signature , Thus, signed messages can be rejected .
(4) Signed messages are immutable : Signed messages cannot be tampered with . Once the signed message is tampered with , Then anyone can find the inconsistency between the message and the signature .
(5) The signature is undeniable : The signer cannot deny his signature afterwards .
3.2 RSA Signature algorithm

Chapter four Information Hiding Technology
Concept
Information hiding is to hide secret information in another unclassified carrier information , Deliver over a common channel . The attacker has no way to judge whether there is secret information , Nor can secret information be extracted or removed . The biggest advantage of information hiding is that it does not limit the access to the main signal , But committed to the security and confidentiality of signature signals
Main application
- Covert communication
- Data integrity
- Image self recovery
- copyright protection
- Bill security
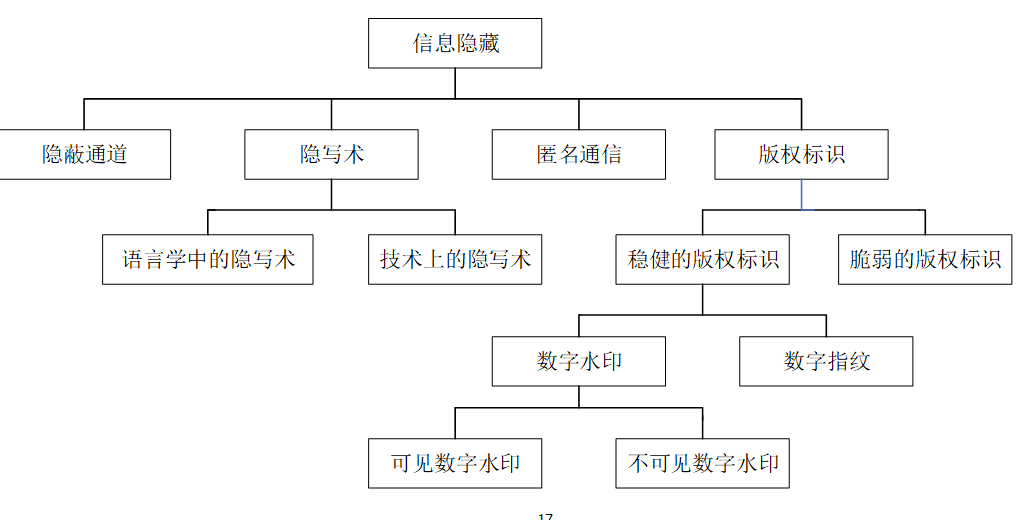 My guess
My guess
The main possibility is to examine the difference between information hiding and information encryption
difference :
Different goals : Encryption only hides the content of the information ; Information hiding not only hides the information content , It also masks the existence of information .
Different ways of implementation : Encryption relies on mathematical operations ; Information hiding makes full use of the redundant space of the carrier .
Different applications : Encryption only focuses on the security of encrypted content , Information hiding also focuses on the relationship between carrier and hidden information .
contact : Borrow from each other in theory , Complementary in application . The information is encrypted first , And hide .
The fifth chapter Application layer security technology
5.1 web Safety technology
Concept
Web Service is Internet One of the most basic services in , It is not only used to build information release 、 Information Service 、 Electronic Commerce 、 E-government and so on Web Website , It is also used as a file transfer service 、 Streaming services 、 The mail service 、 Operation platform of network services such as system update service . therefore ,Web The security of services determines the security of various network services , It also determines the whole Windows Security of the system .
Question
What is? IIS(Internet Information Service)?
IIS namely Internet information service , It is used to configure application pool or website 、FTP Site 、SMTP or NNTP Site tools , Very powerful . utilize IIS Manager , Administrators can configure IIS Security 、 Performance and reliability functions , You can add or delete sites , start-up 、 Stop and pause the site , Backup and restore server configuration , Create virtual directories to improve content management .( frequently-used IIS There is a pagoda Linux, Students who have blogged may have used ), It looks like this
5.2 Email security
Concept
Email on e-mail, I don't need to say much here
System composition
- Client software UA(User Agent): Used to process mail , Such as the preparation of emails 、 Reading and managing ( Delete 、 Sort, etc ).
- Server software TA(Transfer Agent): Used to deliver mail .
among , Email is not end-to-end communication , But there is one “ Middleman ” Responsible for forwarding .
Receiving and dispatching process
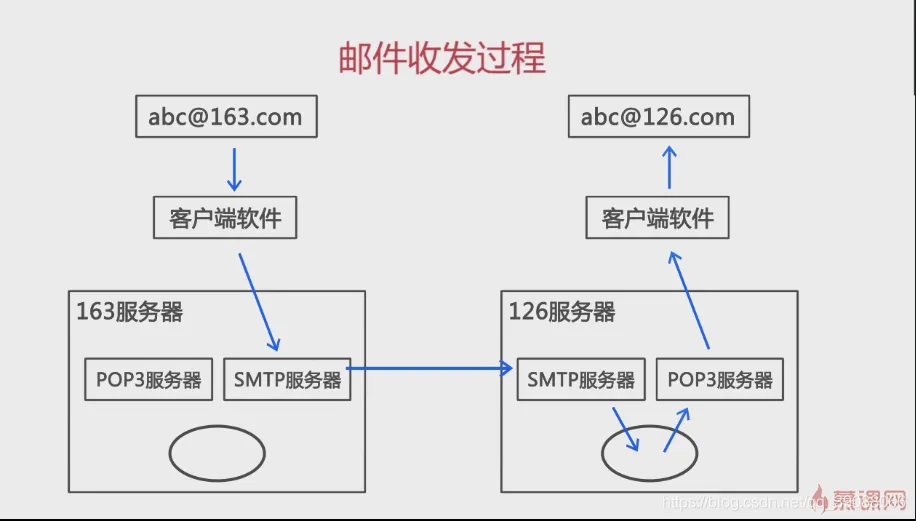
What is a mail gateway
That's what I said “ Middleman ”, It can calculate what is important information in the message , Such as the theme 、 sender 、 The receiver , And translate them into the format required by other systems .
besides , He is also responsible for the communication between internal and external mail systems . The gateway in the computer network does the same thing . Take the application layer gateway as an example
for example , A host performs ISO E-mail standard , Another host performs Internet E-mail standard , If the two hosts need to exchange e-mail , Then the protocol must be converted through an e-mail gateway , This email gateway is an application gateway .
Main functions of mail gateway
- Preventive function
- Monitoring function
- Tracking function
- Accounting management
- Classified statistics
- Email Backup
Mail gateways by purpose
- Ordinary mail gateway
- Mail Filtering Gateway : The mail filtering gateway is an independent hardware system for centralized detection of toxic mail , It has nothing to do with the user's mail system type , And support SMTP authentication .
- Anti spam gateway : Anti spam gateway is a server based email filtering and transmission system , It can help enterprises effectively manage the mail system , Prevent unauthorized mail from entering or sending , It is also used to block spam 、 Prohibit email forwarding and prevent email bombs . It eliminates unwanted emails , Effectively reduce the waste of network resources .
Interpretation of Mail Transfer Protocol
( Speaking version )
SMTP agreement
To put it bluntly, it's the rules you need to follow when you go to the post office to post a letter
POP3 agreement
It's the rule you need to follow when you go to the post office to pick up the letter
( Official edition )
SMTP agreement
SMTP(Simple Mail Transfer Protocol) Simple Mail Transfer Protocol , It's a set of rules for sending mail from source to destination , Used to control the transfer mode of letters .
SMTP The agreement belongs to TCP/IP Application layer protocol of protocol family , It helps each computer find its next destination when it sends or relays messages . adopt SMTP Server specified by protocol , We can E-mail To the recipient's server .
SMTP The server follows SMTP Protocol sending mail server , Used to send or transfer email .
POP3 agreement
POP The agreement is the post office agreement (Post Office Protocol) Abbreviation , It is a protocol that allows users to send and receive mail from the mail server .
POP3(Post Office Protocol 3) That is to say, No 3 A version , It specifies how to connect a personal computer to Internet Email server and electronic protocol for downloading email , Is the first offline protocol standard for Internet e-mail .
POP3 Allow users to store messages from the server to the local host , Also delete messages saved on the mail server .
POP3 The server follows POP3 Protocol receiving mail server , Used to receive emails .
And SMTP Combination of protocol ,POP3 Is currently the most commonly used e-mail service agreement .
What is spam
Everyone has received spam , Not much here
- Anonymous forwarding ( No sender information )
- Email spoofing ( A new layer of vest )
- E-mail bomb ( Equivalent to the effect of SMS bombing )
Anti spam Technology
Filtration technology
(1) Keyword filtering
(2) Black and white list
(3)HASH technology
(4) Filter based on rules
(5) Intelligent and probabilistic systems
Verify query
Challenge
Cryptography
(1) At present, email is used in transmission SMTP agreement , It does not provide encryption services , An attacker can intercept data in the mail transmission .
(2) Two end-to-end security technologies :PGP(Pretty Good Privacy) and S/MIME(Secure Multi-Part Intermail Mail Extension).
(3) The main function is Authentication of identity and Encryption of transmission data .
PGP technology
We used to do experiments , It is to encrypt the sent information before sending it , So that attackers can not easily crack our data , Secure information , Its encryption algorithm includes many aspects .
Concept
PGP Is an application based on public key encryption algorithm , The creativity of this program lies in RSA The convenience of public key system is combined with the high speed of traditional encryption system , And in the digital signature and key authentication management mechanism has clever design .
characteristic
- Fast encryption
- Excellent portability
- The source code is free
5.3 database security
The biggest threat to database security is sql Inject 了 , It is also the most harmful in the whole network security system , The most influential vulnerability .
elementary analysis sql Inject
question
What is? sql Inject ?
sql To put it bluntly, back-end programmers are writing sql Statement does not restrict the user's input, so the user can construct some sql Statement is then brought to the database for joint query , Expose the information of the database , Seriously, it will also lead to the deletion of the database , Modify the information of the database, etc .
We are here to sqli-lab Take a question on as an example , have a look sql How exactly is injection implemented . This is the core part of the source code of that problem
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result);Although it's for php Written , But let's look at this sentence sql
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";In theory , The logic here is that you enter a id, Then the back-end goes to the database to check this id Corresponding user information, right ?
The front page looks like this
Let's try id=1 Will find out what
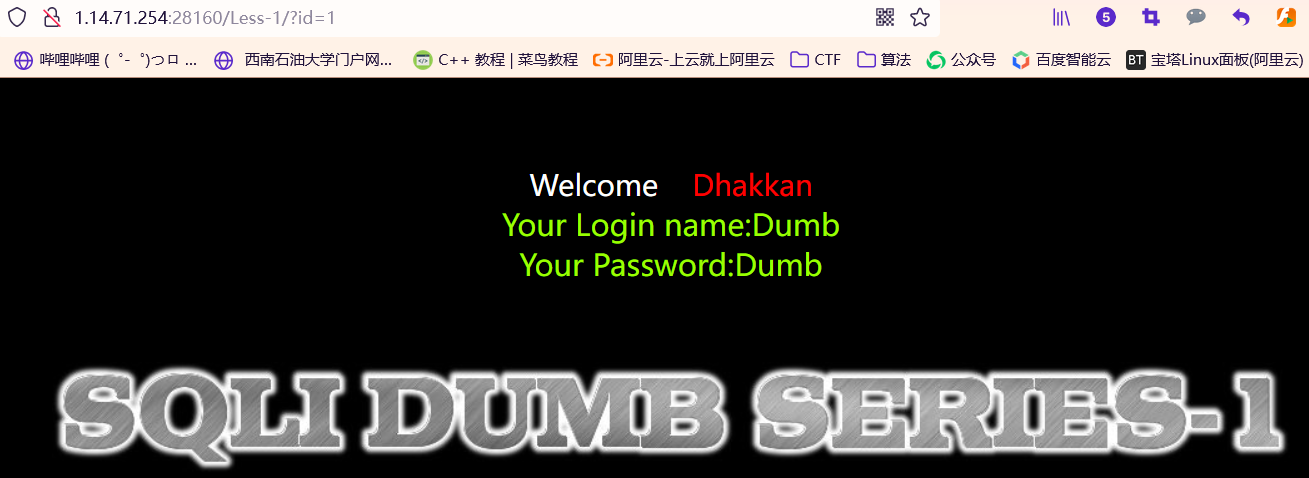
No problem, right , Let's try SQL Inject
http://1.14.71.254:28160/Less-1/?id=1'Be careful , We are 1 There's an extra one in the back ’, So now sql What has the sentence become ?
$id="1'"; $sql = "SELECT * FROM users WHERE id='1' ' LIMIT 0,1";see sql In the sentence id That place , Our single quotation marks close the previous single quotation marks , If we add another # Comment out the following words ,sql The sentence becomes like this
$sql = "SELECT * FROM users WHERE id='1'";It looks normal here, doesn't it , What if we add a joint query ?
$id="1' union select * from users #";// In fact, we don't know the actual table name in the database , Here's just a demonstrationsql This is what the statement will look like
$sql = "SELECT * FROM users WHERE id='1' union select * from users";Will this joint query put user All the information of the table is returned ?sql The purpose of injection is achieved .
The exam is not so difficult , Here is just for the students to see the actual sql What exactly is the injection process .
How to prevent sql Inject ?
We saw it before sql The reason for injection is that there is no restriction on user input , So the prevention method is also very simple , Restrict user input .
- Filter the text box ( User input ), take SQL Special symbols used in , Such as “’”,“-”,“%”,”;” etc. , use Replace() Method filtering out .
- Limit the length of input characters in the text box
- Check the validity of user input
- Use... With parameters SQL Statements in the form of : Ensure that values received from external sources are passed only as values , Instead of acting SQL Part of the transmission .
- Keep abnormal information private .
Chapter six Computer virus and prevention
6.1 Overview of computer viruses
Definition
Similar to biological viruses , Destructive , And copy 、 Strong broadcasting ability , The essence is a program , An executable code .
characteristic
- Cannot be run as a stand-alone executable
- Copy yourself
- Activate the virus by executing the host program
- Cross platform
classification ( By function )
- Infectious virus : The greatest harm
- worm-type virus : There are many communication carriers , Strong communication ability
- Backdoor program : Remote control
- Trojans : hide 、 steal
- Virus tools : Internet media
- Virus generator : Building block form
- Funny program : to fool
harm
Needless to say, everyone knows the harm of viruses
6.2 VBS Viruses
Concept
be based on VBScript This programming language , By calling some public Windows object , Components , It can be directly applied to the file system , Registry, etc .
characteristic
1. Write simple , A virus lover who knows nothing about viruses before can make up a new virus in a very short time .
2. It's destructive . Its destructive power is not only manifested in the destruction of user system files and performance . He can also crash the mail server , The network is seriously blocked .
3. Strong appeal . Because the script is interpreted and executed directly , And it doesn't need to be like PE Like viruses , Need to do complicated PE File format processing , Therefore, this kind of virus can directly infect other similar files through self replication , And self exception handling becomes very easy .
4. Spread widely . This kind of virus passes htm file ,Email Attachment or other means , It can be spread all over the world in a very short time .
5. The virus source code is easy to obtain , There are many varieties . because VBS Virus interpretation execution , Its source code is very readable , Even after the virus source code is encrypted , Its source code acquisition is still relatively simple . therefore , There are many variants of this kind of virus , Change the structure of the virus a little , Or modify the eigenvalue , Many anti-virus software may be powerless .
6. Deceptive . Script virus in order to get the chance to run , They often use various means to make users pay little attention , for example , The attachment name of the email adopts double suffixes , Such as .jpg.vbs, Because the system does not display the suffix by default , such , When the user sees this file , Would think it was a jpg Picture file .
7. It makes the implementation of virus production machine very easy . The so-called virus production machine , That is, according to the wishes of users , Machines that produce viruses ( Of course , This refers to the program ), Current virus production machines , The reason why most of them are script virus producers , The most important point is that scripts are interpreted and executed , It's very easy to implement , Details will be discussed later .
principle
- First, assign the computer virus's own code to the string variable VBscopy.
- Overwrite this string to the target file and create a file name prefix with the target file name , With vbs Is a copy of the file with the extension , Finally, delete the target file .
- adopt scan() The function mainly searches for files that meet the conditions , And generate a copy of the computer virus of the corresponding file
- Traverse the entire directory and files by recursion .
6.3 worm-type virus
Concept
Worm is a common computer virus , yes No computer user intervention You can run Independent procedure , It spreads by constantly gaining some or all control of computers with vulnerabilities in the network . A computer virus refers to a virus compiled or inserted into a computer program that destroys computer functions or destroys data . A set of computer instructions or program codes that affect the use of a computer and can be copied by itself .( Panda burning incense is a classic worm virus )
characteristic
- Strong independence
- Find system vulnerabilities and carry out active attacks
- Spread more , It's spreading faster
- Use clever methods to camouflage and hide
- Use advanced technology
6.4 Trojan horse
Concept
Trojan horse is called Trojan horse , From ancient Greek mythology . Trojans are installed by deception or deception , And hidden in the user's computer to achieve the purpose of controlling the user's computer . yes With remote control 、 information theft 、 Malicious code that destroys functions such as
characteristic
- Deception
Trojans are very deceptive , Execution is usually carried out by the attacker himself - Concealment
- Unauthorized
It is not authorized by the user to perform malicious operations - Interactivity
Attackers outside the host can interact with the host in some way
Classic example :php In a word, Trojans , If you are interested, you can have a try
<?php @eval($_GET["cmd"]); ?>
6.5 Computer virus prevention
Common methods
- anti-virus software
- Don't browse irregular websites
- Cultivate a conscious awareness of information security
- use Windows Update The function is patched in the whole system
Chapter vii. A firewall
7.1 Firewall Overview
Concept
- “ A firewall ”, It refers to an intranet and public access network ( Such as Internet) The way of separation , It's actually a kind of Isolation technology .
- Firewall is an access control standard that is implemented when two networks communicate , It is used to protect computer networks from unauthorized personnel , Prevent hackers from invading .
Basic attributes
- Firewall is the information flow between different networks or network security domains The only access , All bidirectional data flows must pass through it .
- Only authorized legal data , That is, the data allowed by the security policy in the firewall system , To get through .
- logically , Firewall is a separator 、 One Limiter , It's also an analyzer , He effectively monitored the intranet and Internet All activities between , Ensure Intranet Security .
7.2 The function of firewall
Network security barrier
Strengthen network security strategy
Based on the following four technologies
- Service control —— Determine the types of network services that can be accessed . The firewall can be in IP Address and TCP Filter traffic based on port number .
- Direction control —— Determine the direction in which specific service requests flow through the firewall .
- User control —— Access to a service is controlled according to which user tries to access the service .
- behavior control —— Control how specific services are used .
Monitor and audit network access and access
Prevent internal information leakage
Protect Intranet Security
7.3 The limitations of firewalls
- Firewall meeting Limit useful Web Services .
- Firewall cannot protect Inside Attacks by network users .
- Firewalls cannot prevent attacks through other ways than firewalls .
- Firewalls cannot prevent Transmit infected virus Software or files .
- Firewalls cannot prevent data-driven attacks .
- Firewalls cannot prevent new network security problems .
Because firewall is essentially a virus library , He can only compare whether there is a virus in his library in your computer , And he is a passive defense , So I won't take the initiative to find new computer viruses .
7.4 Basic principle of firewall
- The realization of all firewall functions depends on checking the relevant information of packets passing through the firewall , And the more items to check 、 The deeper the level , The more secure the firewall .
- For a firewall , If you know that it runs in OSI Which layer of the reference model , You can know its architecture , What are the main functions .
It is to check the data packets of each layer in the computer network , The more layers you check, the more secure the firewall .
7.5 Distributed firewall
Concept
- Distributed firewall is a host resident security system , It is used to protect the key node servers in the enterprise network 、 Data and workstations are protected from illegal intrusion .
- Kernel mode
- Filtering and restricting all information can prevent illegal intrusion , It also has intrusion detection and protection functions
structure
- Mainly in the form of software
- “ Three layers ” Filter check
- The central policy management server is responsible for setting security policies
- Different from the boundary of traditional firewall
- Distributed firewall is a complete system , Instead of a single product , According to the function, it can be divided into the following parts : Network firewall , Host firewall , Center management software .
characteristic
- Host resides
- Embedded operating system ( Front end unit )
- Similar to personal firewall
7.6 Comparison of advantages and disadvantages of different types of firewalls
The traditional firewall is insufficient
- Structural constraints : The concept of internal and external networks is not easy to distinguish .
- Guard against the outside but not the inside : Limited function .
- The efficiency problem : It is easy to form a network bottleneck .
- Trouble problem : A single point of failure
Advantages of distributed firewall
- Applicable to server hosting ( Big data center )
- Enhanced system security ( Intrusion detection )
- Eliminate structural bottlenecks , Improved system performance ( A single access point )
- Expand with the system ( Distributed features )
- It is more widely used and supports VPN signal communication
Chapter viii. intrusion detection system
8.1 Introduction to intrusion detection system
Basic concepts of intrusion detection
Intrusion detection is Detection of intrusion . It through the computer network or computer system in a number of key points To collect information And analyze it , thus Find out Is there any behavior violating the security policy or being attacked in the network or system Sign . And firewall is different .
intrusion detection system (IDS) Basic concepts
intrusion detection system (Intrusion Detection System,IDS) It is the software or hardware that detects computer network attacks . As a reasonable supplement to firewall , It can help network administrators detect intrusion into the network , So as to expand the security management ability of the system administrator .
IDS The main function
- Monitor and analyze user and system activities
- Check system configuration and vulnerabilities
- Evaluate the integrity of key resources and data files of the system
- Identify known attacks
- Statistical analysis of abnormal behavior
- Operating system log management , And identify user activities that violate security policies
Why is it necessary to have a firewall IDS
- Firewall policy can not meet the requirements of high security
- Complementary functions :“ The guards ” And “ Patrol ”
IDS The general model of CIDF
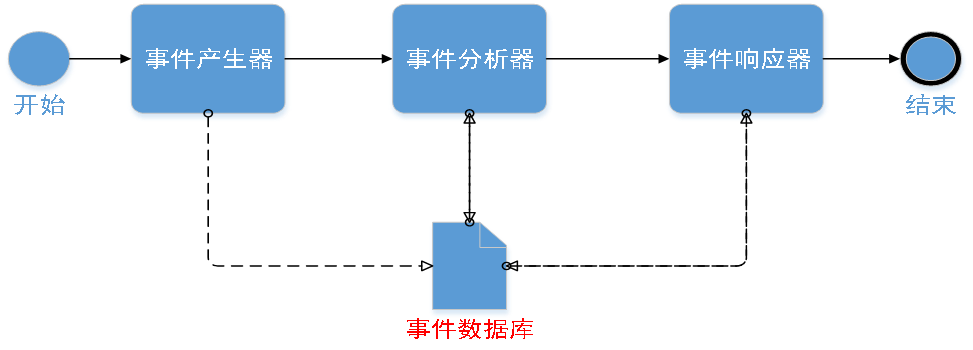
The main module :
- Event generator (Event Generators)
- Event analyzer (Event Analyzers)
- Response unit (Response Units)
- Event database (Event Databases)
Classification of responsibilities
information gathering
Location : Several different key points in computer network system ( Different network segments and different hosts ) To collect information .
(1) Expand the detection range
(2)“ Uniformity ” testing
Content : Including systems 、 The Internet 、 Status and behavior of data and user activities
quality : Information correctness and reliability
Intrusion detection information source
System and network log files : The use of system and network log file information is a necessary condition for intrusion detection .
Undesired changes in directories and files : Restrict access to or modify system log files under normal circumstances .
Unexpected behavior in program execution
Intrusion information in physical form
(1) Unauthorized connection to network hardware
(2) Authorized access to physical resources
IDS Signal analysis means
- Pattern matching : Compare the collected information with the known database of network intrusion and system misuse patterns .
- advantage : accuracy 、 Efficient
- shortcoming : Need to keep updating , Unable to detect an attack that has not occurred
- Statistical analysis : First, create a statistical description for the system object , Count some measurement properties in normal use . Any observation outside the normal range , It is considered that an invasion has occurred .
- advantage : Unknown and more complex intrusions can be detected
- shortcoming : False positives 、 High underreporting rate
- Integrity analysis : Integrity analysis focuses on whether a file or object has been changed , Strong encryption mechanisms are usually used ( Such as Hash function ) To identify small changes .
- advantage : Can detect any changes to files or objects caused by the attack
- shortcoming : Unable to respond in real time , Can only be analyzed afterwards
- Pattern matching : Compare the collected information with the known database of network intrusion and system misuse patterns .
IDS Common response processing
- Warning and event reporting .
- Terminate the process , Force user to exit .
- Cut off the Internet connection , Modify firewall settings .
- Disaster assessment , Automatic recovery .
- Find and locate attackers .
8.2 IDS classification
according to ** Monitoring location ( Data sources )** To classify :
be based on The Internet Of IDS
Web based IDS Yes Data packets Analyze to detect attacks against the network , such IDS Sniff network packets , And will Data flow and characteristics of known intrusion behavior Compare .
- advantage :(1) Whole network monitoring (2) Meet various performance requirements
- shortcoming :(1) Bandwidth requirements : Traffic < The processing capacity of the detector (2) Unable to process encrypted data
be based on host Of IDS
Check relevant information on the host or operating system to detect intrusion , such IDS adopt system call , The audit log and error message Wait to analyze the host .
- advantage :(1) Determine whether an attack is successful .(2) Use the host's own IP Protocol stack to defend against packet fragmentation and reorganization 、 Change the life time and other network-based IDS It is difficult to deal with such attacks .
- shortcoming :(1) The scope of network monitoring is limited : Cannot monitor port scans for hosts (2) Challenge : Must run on all operating systems in the network
According to intrusion detection technology classification :
feature detection
For feature-based detection technology , First of all Define the characteristics of events that violate security policies , Such as some header information of network packets . Testing mainly Determine whether such features appear in the collected data .
Anomaly detection
Anomaly based detection technology is First define a set of systems “ normal ” The value of the situation , Then compare the value of the system running time with the defined “ normal ” The situation is quite , Find out whether there are signs of being attacked . The core of this detection method is How to define the so-called “ normal ” situation .( It's similar to going to the hospital to check blood routine )
Comparison of these two detection techniques
- The conclusion is very different
- The core of feature-based detection technology is to maintain a knowledge base , For known attacks , It can be detailed 、 Accurately report the type of attack , But the ability to detect unknown attacks is very limited , And the knowledge base must be constantly updated .
- Anomaly based detection technology can not accurately identify the means of attack , But it can distinguish a wider range 、 Even undetected attacks .
Classify according to the detection principle :
- Anomaly detection : Model based detection
- Classify from model type : rule-based ( A priori experience )–> Based on statistical sampling –> Based on artificial neural network
- Classify from the implementation mode : Self learning system and programming system
- Rule base detection : feature detection
- Mixed detection
- ( clear ) Analyze the normal behavior of the system
- ( Suspicious ) Observe suspicious intrusions
- Judgment is more comprehensive 、 accuracy 、 reliable
8.3 IDS challenges
- Improve IDS The detection speed of , To meet the requirements of network communication
- Reduce IDS Missing and false positives , Improve its safety and accuracy
- Improve IDS Interactive performance , So as to improve the safety performance of the whole system .
Chapter nine Network security protocol
9.1 Overview of security protocols
Security protocols (Security protocol, Also known as cryptographic protocol ,Cryptographic protocol). Security protocol is an interactive communication protocol based on cryptosystem , It uses cryptographic algorithm and protocol logic to achieve the goals of authentication and key distribution . The reason is that some early protocols did not encrypt data, resulting in a series of security problems .
9.2 Common network security architecture
TCP/IP Security architecture
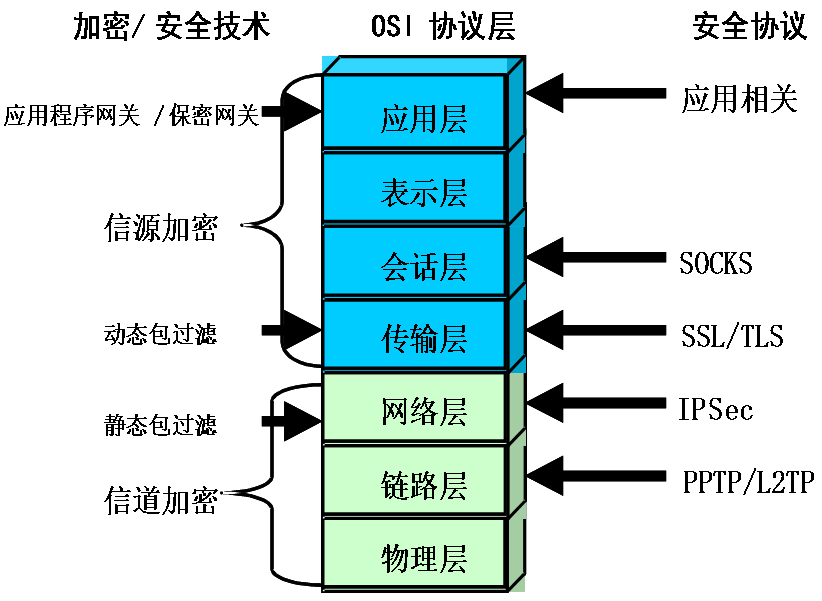
IPSec The architecture of the protocol family
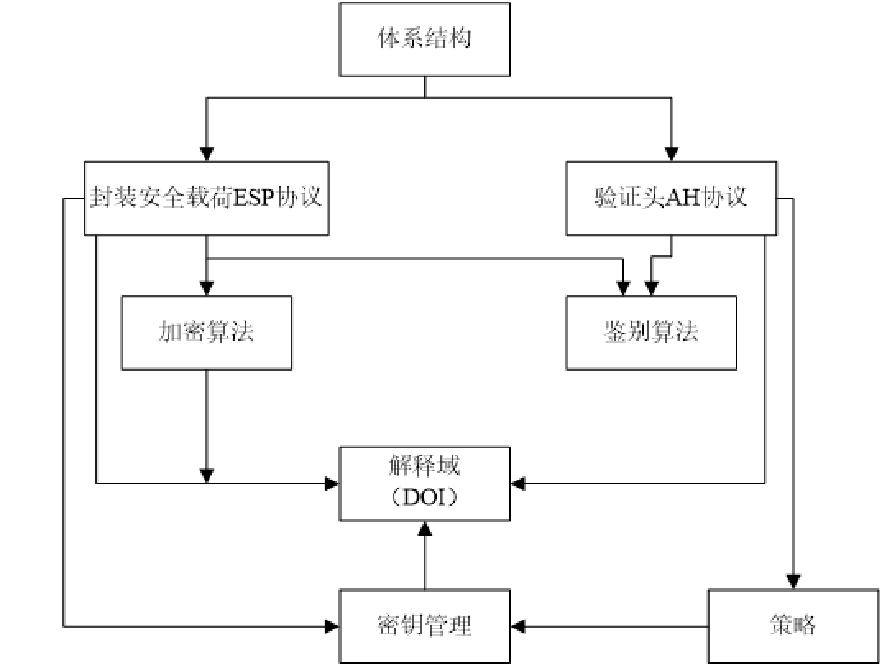
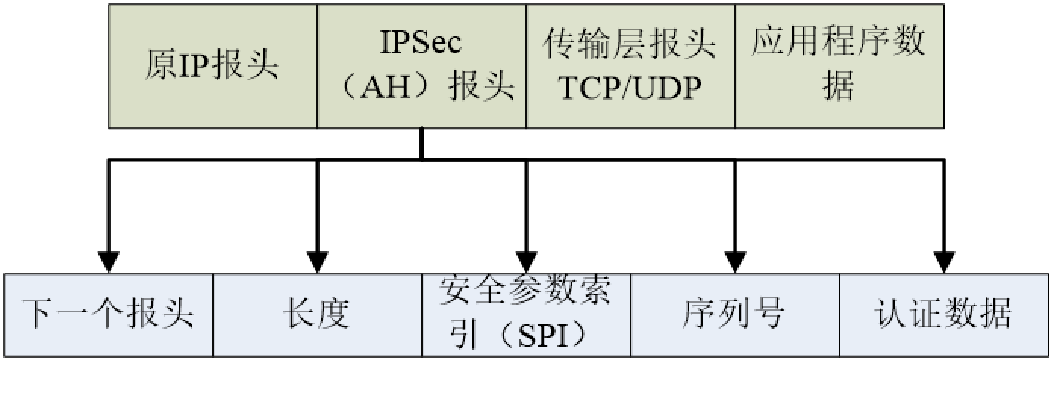
AH( Certification head ) agreement
IPsec Authentication header protocol (IPsec AH) yes IPsec One of the main protocols in Architecture , It's for IP Datagrams provide connectionless integrity and data source authentication , And provide protection to avoid replay . Once a secure connection is established , The receiver may choose the latter service . AH As far as possible IP Header and upper layer protocol data provide enough authentication .
ESP( Load encapsulation ) agreement
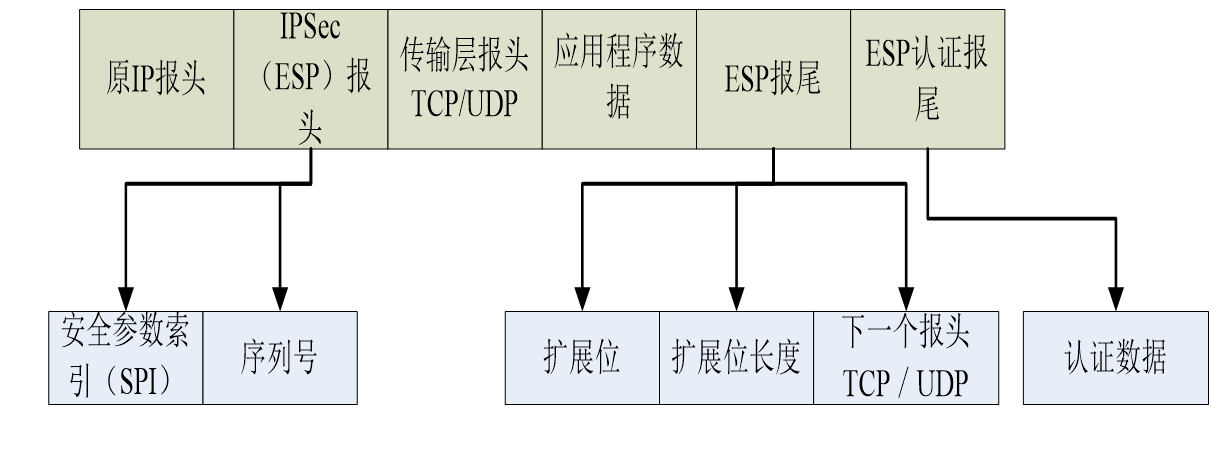
ESP The format of protocol data unit consists of three parts , Except for the head 、 Encrypted data part , An optional tail is also included when implementing certification .
Chapter ten VPN technology
10.1 Common remote connection methods
Use dial-up technology to realize remote connection ( Numbers / simulation )
utilize VPN Realize remote connection
Hardware : Router VPN
Software : Commonly used personal remote assistance software ( Peanut shell , Sunflower ,Teamviewer)
Wireless remote connection
10.2 VPN Concept
- “ fictitious ” (Virtual) It refers to a logical connection ,“ Private or private ”(Private) It refers to an exclusive connection ,“ The Internet ”(Network) A collection of computers that communicate according to a protocol .
- Realize the interconnection of components and resources between different networks
- Provide the same security and functional guarantee as the private network
- One of the remote connection methods
VPN The basic requirements
- User authentication
- Address management
- Data encryption
- Key management
- Multi protocol support
characteristic
- Using encryption 、 Certification and Tunneling Technology , Use part of the public communication network facilities to send private network information .
- Establish a relatively closed 、 Logical private network .
- Only within specific interest groups (VPN Inside ) Establishing a peer-to-peer connection , Ensure the confidentiality of data transmitted in the network .
- It can flexibly use a variety of public telecommunication networks to realize the communication between different internal LANs 、 Remote information exchange between network and host .
advantage
- Cost savings
- Realize network security
- Simplify network structure
- The randomness of the connection
- Master autonomy
10.3 Tunnel technology
Definition
Tunnel technology is a technology that transfers data between networks by using the infrastructure of Internet . Note that tunneling refers to including data encapsulation , The whole process including transmission and unpacking .
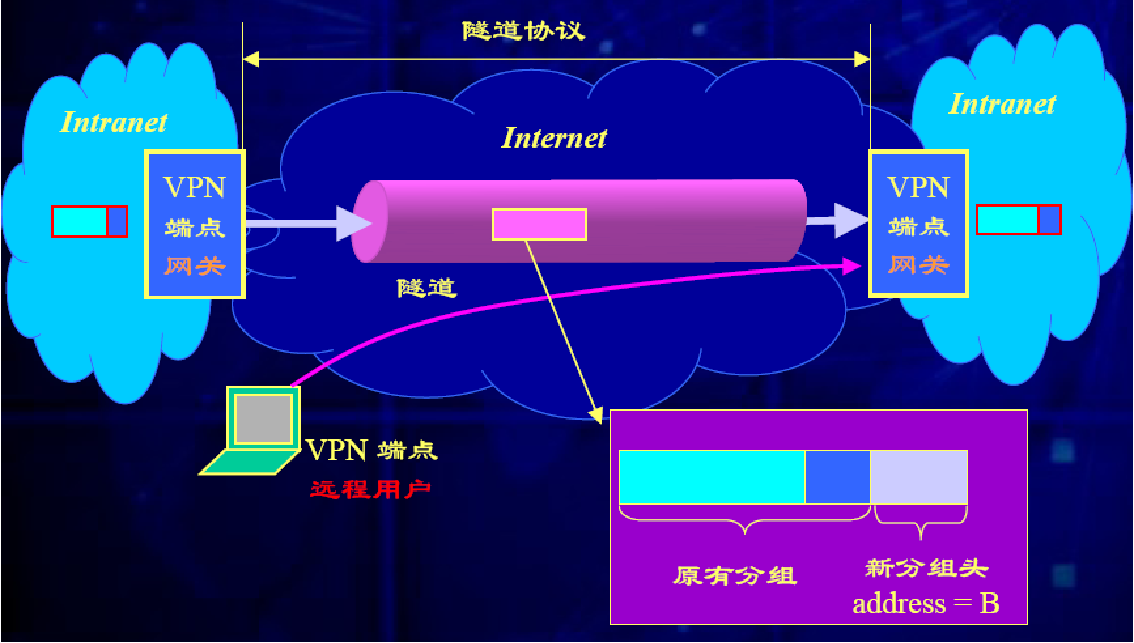
Basic requirements of tunnel :
- User authentication
- Token Card (Tokencard) Support
- Dynamic address assignment
- data compression
- Data encryption
- Key management
- Multi protocol support
Chapter 11 Wireless network and security evaluation
11.1 Overview of wireless network
Concept
WLAN Refers to Wireless channel A computer LAN used as a transmission medium , It is an important supplement and extension of wired networking , And gradually become a vital part of computer networks , It is widely used in fields that need removable data processing or cannot be wired with physical transmission media . At present, the three most popular wireless technologies are WiFi、 Bluetooth and HomeRF
Working mode
Point to point (AD-hoc) Pattern
Point to point mode ( or Peer-to-Peer) It is the simplest way to connect to the wireless network , This mode allows two or more computers to communicate with each other without relying on any control center . Building a AD-hoc Mode of wireless network is very simple , The minimum hardware requirements , Each computer only needs to support the same protocol ( Such as IEEE 802.11) Wireless network card of .
Infrastructure
The best way to build a wireless hotspot is Infrastructure The way , It doesn't need to keep a computer on all the time , At the same time, it also provides a certain security mechanism .
11.2 Wireless network protocol
WEP agreement
WEP(Wired Equivalent Privacy) Agreement is IEEE802.11b The most basic wireless security encryption measure in the protocol , Its main uses include providing Access control , Prevent unauthorized users from accessing the network ; Encrypt data , Prevent data from being eavesdropped by attackers ; Prevent the data from being maliciously altered or forged by the attacker . Besides ,WEP It also provides authentication function .
IEEE 802.11i safety standards
This safety standard is designed to enhance WLAN Data encryption and authentication performance , Defined RSN(Robust Security Network) The concept of , And for WEP Various defects of encryption mechanism have been improved in many aspects .( Than WEP Awesome )
WAPI agreement
WAPI The security mechanism consists of WAI(WLAN Authentication Infrastructure) and WPI(WLAN Privacy Infrastruc-ture) Two parts ,WAI and WPI To achieve the goal of Identification of user identity And for The transmitted data is encrypted .WAPI For users WLAN The system provides comprehensive security protection .WAPI The security mechanism includes Two Part of the .
11.3 Measures to enhance safety
- Use strong passwords .
- Broadcast service identifier (SSID).
- Adopt effective wireless encryption .
- If possible , Use different types of encryption .
- Media access control (MAC) Address control .
- Turn off the wireless network interface .
- Monitor network intruders .
- Ensure the security of the core .
11.4 Information security assessment
11.4.1 Evaluation standards at home and abroad
Network security standard is to ensure network security technology and products , In the design 、 Research and development 、 Building 、 The implementation of 、 Use 、 In the process of evaluation, management and maintenance , Resolve consistency 、 reliability 、 Controllability 、 Technical specifications and basis for progressiveness and compliance . It is also an important means of government macro management , An important part of the information security system .
Foreign evaluation standards
- The United States TCSEC( Orange book )
- U.S. Federal Code (FC)
- The European ITSEC( white paper )
- General evaluation criteria (CC)
- ISO Security architecture standards
Domestic evaluation standards
Classification criteria of system security protection level 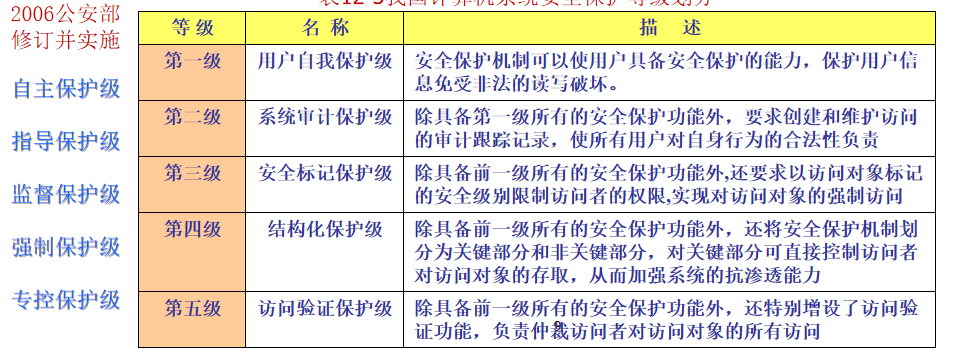
11.4.2 Network security management process PDCA
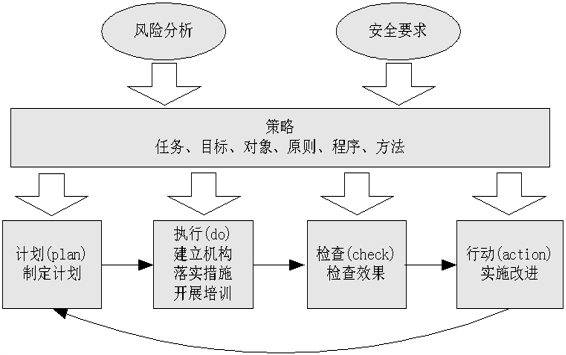
11.4.3 Network information security risk assessment
Definition
From the perspective of risk management , Using scientific methods and means , This paper systematically analyzes the threat and vulnerability of network and information system , Evaluate the possible harm degree in case of safety incident , Put forward targeted protection countermeasures and rectification measures to resist threats .
The significance of risk assessment
Clarify the security status of enterprise information system
Enterprises accurately understand their own networks 、 Security status of various application systems and management systems , So as to clarify the security needs of enterprises
Identify the main security risks of enterprise information systems
The main security risks of enterprise information system can be determined , And let enterprises choose to avoid 、 Reduce 、 Accept other risk disposal measures .
Guide the construction of enterprise information system security technology system and management system
Risk assessment implementation steps
- Preparation of risk assessment
- Asset identification
- Threat identification
- Vulnerability identification
- Confirmation of existing safety measures
- risk analysis
- Risk assessment documentation
11.5 Relevant laws and regulations
China starts from the need of network security regulation and management , State and relevant departments 、 The industry and local governments have successively formulated a number of laws and regulations related to network security . China's network security legislation system is divided into the following three levels :
- The first level : law . It is a legal norm passed by the National People's Congress and its Standing Committee . The laws related to network security in China include :《 legislation law 》、《 The constitution 》、《 The criminal law 》、《 Regulations on punishment of Public Security Administration 》、《 criminal procedure law 》、《 National security law 》、《 The law on Guarding State secrets 》、《 Administrative penalty law 》、《 Administrative Procedure Law 》、《 The decision to maintain Internet Security 》、《 Network security law 》、《 Administrative reconsideration law 》、《 State compensation law 》 etc. .
- The second level : Administrative regulations . It is mainly the legal norms formulated by the State Council for the implementation of the Constitution and laws . Administrative regulations related to network information security include 《 Computer information system security regulations 》、《 Interim Provisions on the administration of international networking of computer information networks 》、《 Measures for the administration of the security protection of the international networking of computer information networks 》、《 Commercial password regulations 》、《 Telecommunications Regulations of the people's Republic of China 》、《 Internet Information Services 》、《 Regulations on the protection of computer software 》 etc. .
- The third level : Local regulations 、 rules 、 Normative documents . Mainly the ministries of the State Council 、 According to laws and administrative regulations and legal norms of the State Council , And save 、 Autonomous region 、 The people's governments of municipalities directly under the central government and larger cities shall, in accordance with the law 、 Administrative regulations and their legal normative documents . Formulated by the Ministry of public security 《 Measures for the administration of testing and sales licenses for special products for computer information system security 》、《 Computer virus prevention and control management measures 》、《 Interim Provisions on the security protection of computer information systems of financial institutions 》 And relevant training requirements for computer security personnel, etc . Formulated by the Ministry of industry and information technology 《 Regulations on the administration of Internet user announcement service 》、《 Software product management measures 》、《 Measures for the administration of computer information system integration qualification 》、《 Administrative measures of the international communications import and Export Bureau 》、《 Regulations on the construction and management of international communication facilities 》、《 Measures for the administration of Internet domain names in China 》、《 Interim Provisions on the administration of interconnection between telecommunication networks 》 etc. .
边栏推荐
- Only learning C can live up to expectations TOP4 S1E6: data type
- CTF逆向入门题——掷骰子
- Akamai talking about risk control principles and Solutions
- DOS 功能调用
- Interpretation of Flink source code (III): Interpretation of executiongraph source code
- Activiti directory (I) highlights
- 8086 memory
- 吴军三部曲见识(四) 大家智慧
- Only learning C can live up to expectations top5 S1E8 | S1E9: characters and strings & arithmetic operators
- Compile homework after class
猜你喜欢
MySQL字符串函数
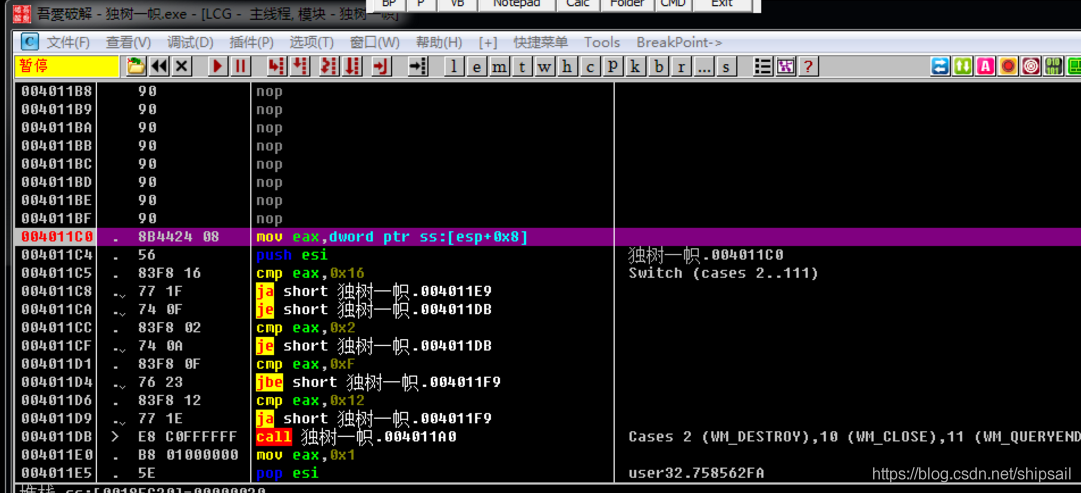
【逆向初级】独树一帜
Install docker under windows10 (through Oracle VM VirtualBox)
C# WinForm系列-Button简单使用
Assembly language segment definition
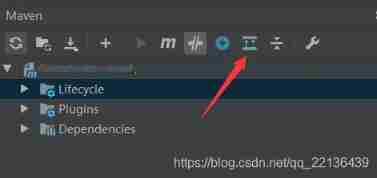
Idea resolving jar package conflicts
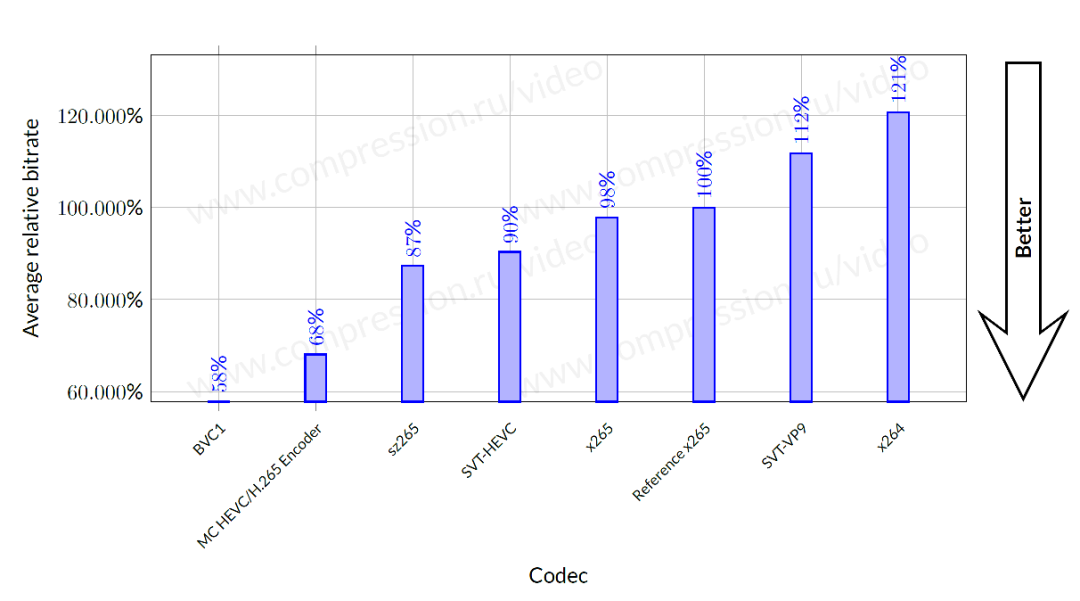
ByteDance overseas technical team won the championship again: HD video coding has won the first place in 17 items
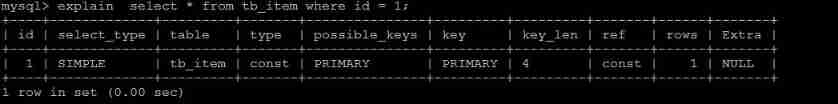
MySQL optimization notes
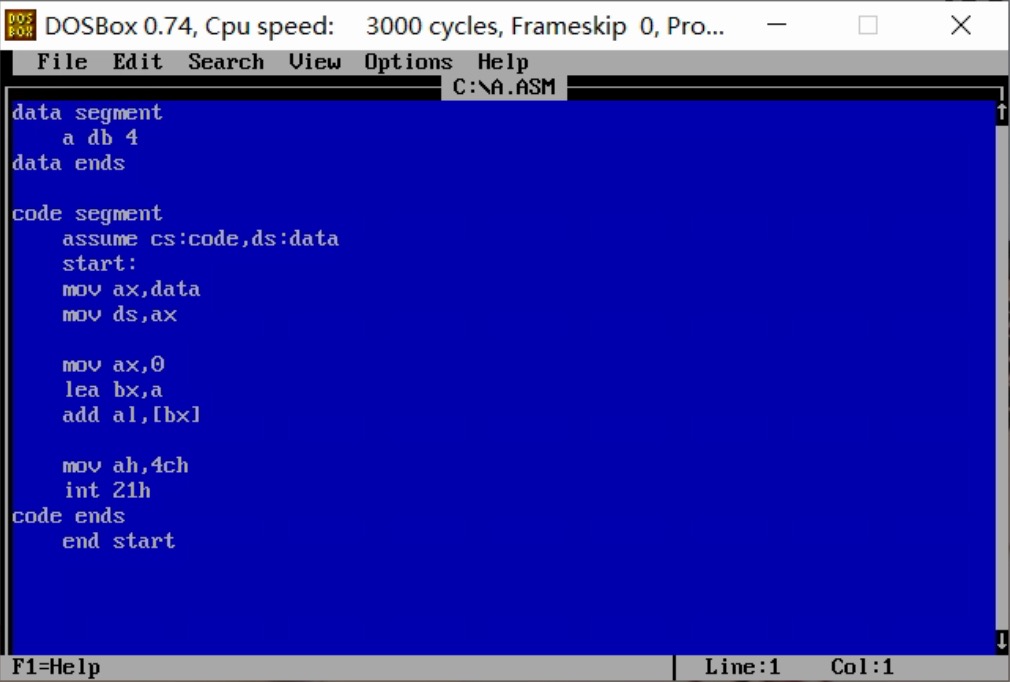
Assembly language addressing mode
JVM class loading subsystem
随机推荐
吴军三部曲见识(七) 商业的本质
Compile homework after class
算数运算指令
Redis installation on centos7
一个数10年工作经验的微服务架构老师的简历
In the command mode in the VI editor, delete the character usage at the current cursor__ Command.
Control transfer instruction
唯有学C不负众望 TOP2 p1变量
Assembly language addressing mode
JVM 垃圾回收器之Serial SerialOld ParNew
List集合数据移除(List.subList.clear)
Serial serialold parnew of JVM garbage collector
华为认证云计算HICA
Only learning C can live up to expectations Top1 environment configuration
Flink 解析(二):反压机制解析
汇编语言寻址方式
唯有学C不负众望 TOP4 S1E6:数据类型
Idea breakpoint debugging skills, multiple dynamic diagram package teaching package meeting.
Prototype chain inheritance
Basic knowledge of assembly language