当前位置:网站首页>buuctf misc USB
buuctf misc USB
2022-07-07 04:13:00 【[mzq]】
USB
题目地址 : https://buuoj.cn/challenges#USB
题目一共两个文件一个233.rar 一个key.ftm 文件,先解压rar文件得到一个flag.txt 来自作者的嘲讽
用010editor 打开发现 rar的文件块应该是74 而不是7A ,把7A修改为74
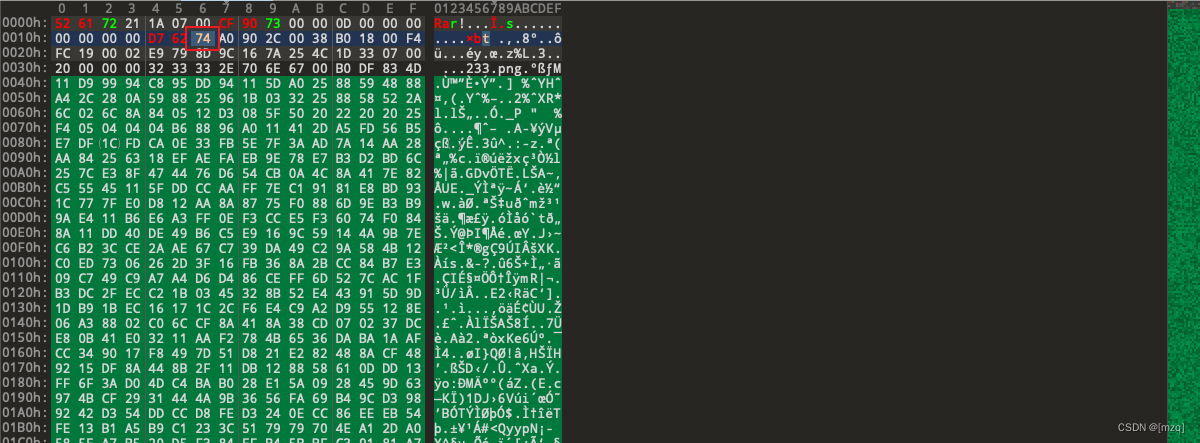
修复完解压后得到一个 233.png ,用stegsolve打开, 发现二维码
扫码得到
ci{v3erf_0tygidv2_fc0}

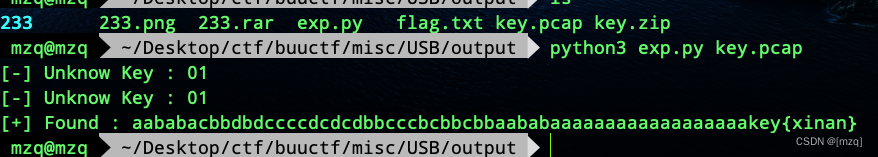
在 key.ftm 文件中发现zip文件,提取zip压缩包解压得到key.pcapng
用UsbKeyboardDataHacker 解密usb流量
#!/usr/bin/env python
import sys
import os
DataFileName = "usb.dat"
presses = []
normalKeys = {
"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", "09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j", "0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o", "13":"p", "14":"q", "15":"r", "16":"s", "17":"t", "18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y", "1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4", "22":"5", "23":"6","24":"7","25":"8","26":"9","27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\","32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".","38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
shiftKeys = {
"04":"A", "05":"B", "06":"C", "07":"D", "08":"E", "09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J", "0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O", "13":"P", "14":"Q", "15":"R", "16":"S", "17":"T", "18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y", "1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$", "22":"%", "23":"^","24":"&","25":"*","26":"(","27":")","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"<NON>","33":"\"","34":":","35":"<GA>","36":"<","37":">","38":"?","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
def main():
# check argv
if len(sys.argv) != 2:
print("Usage : ")
print(" python UsbKeyboardHacker.py data.pcap")
print("Tips : ")
print(" To use this python script , you must install the tshark first.")
print(" You can use `sudo apt-get install tshark` to install it")
print("Author : ")
print(" WangYihang <[email protected]>")
print(" If you have any questions , please contact me by email.")
print(" Thank you for using.")
exit(1)
# get argv
pcapFilePath = sys.argv[1]
# get data of pcap
os.system("tshark -r %s -T fields -e usb.capdata 'usb.data_len == 8' > %s" % (pcapFilePath, DataFileName))
# read data
with open(DataFileName, "r") as f:
for line in f:
presses.append(line[0:-1])
# handle
result = ""
for press in presses:
if press == '':
continue
if ':' in press:
Bytes = press.split(":")
else:
Bytes = [press[i:i+2] for i in range(0, len(press), 2)]
if Bytes[0] == "00":
if Bytes[2] != "00" and normalKeys.get(Bytes[2]):
result += normalKeys[Bytes[2]]
elif int(Bytes[0],16) & 0b10 or int(Bytes[0],16) & 0b100000: # shift key is pressed.
if Bytes[2] != "00" and normalKeys.get(Bytes[2]):
result += shiftKeys[Bytes[2]]
else:
print("[-] Unknow Key : %s" % (Bytes[0]))
print("[+] Found : %s" % (result))
# clean the temp data
os.system("rm ./%s" % (DataFileName))
if __name__ == "__main__":
main()
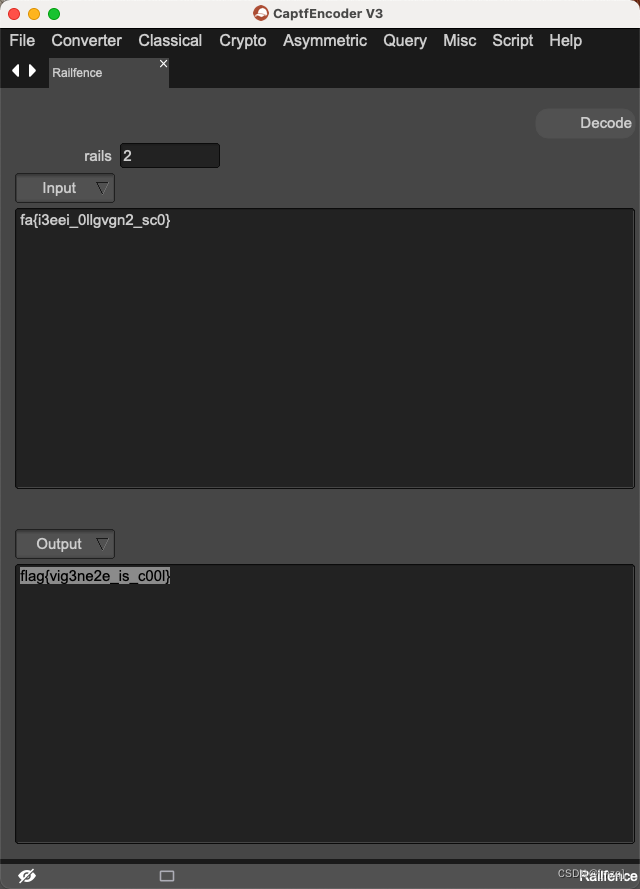
用二维码得到的字符串,进行
Vigenere解码,key是xinan
Vigenere : https://atomcated.github.io/Vigenere/
然后进行 Railfence解密 栏数为2
边栏推荐
- resource 创建包方式
- 1090: integer power (multi instance test)
- 1142_ SiCp learning notes_ Functions and processes created by functions_ Linear recursion and iteration
- leetcode:105. 从前序与中序遍历序列构造二叉树
- 1141_ SiCp learning notes_ Functions abstracted as black boxes
- URP - shaders and materials - simple lit
- 深度学习花书+机器学习西瓜书电子版我找到了
- 242. Bipartite graph determination
- Write CPU yourself -- Chapter 9 -- learning notes
- Tianqing sends instructions to bypass the secondary verification
猜你喜欢
![[ANSYS] learning experience of APDL finite element analysis](/img/bc/dc0742c308816553a80d50d1a990e3.jpg)
[ANSYS] learning experience of APDL finite element analysis
《动手学深度学习》(四) -- 卷积神经网络 CNN
Make a bat file for cleaning system garbage
@component(““)
Role of virtual machine
URP - shaders and materials - light shader lit
Leetcode-226. Invert Binary Tree
知识点滴 - 关于苹果认证MFI
95后CV工程师晒出工资单,狠补了这个,真香...
![[2022 ACTF]web题目复现](/img/e4/ab9a1771489d751ee73a79f151d374.png)
[2022 ACTF]web题目复现
随机推荐
Bi she - college student part-time platform system based on SSM
IO流 file
After 95, the CV engineer posted the payroll and made up this. It's really fragrant
微博发布案例
Make a bat file for cleaning system garbage
L'étape avancée du pointeur de langage C (haut de gamme) pour l'enroulement des cocons
PostgreSQL source code (60) transaction system summary
Cloud backup project
【云原生】内存数据库如何发挥内存优势
idea添加类注释模板和方法模板
Solve could not find or load the QT platform plugin "xcb" in "
Flexible layout (II)
[cloud native] how to give full play to memory advantage of memory database
After 95, Alibaba P7 published the payroll: it's really fragrant to make up this
Modify the jupyter notebook file path
The metauniverse of the platofarm farm continues to expand, with Dao governance as the core
JS small exercise
知识点滴 - 关于苹果认证MFI
leetcode:105. 从前序与中序遍历序列构造二叉树
考研失败,卷不进大厂,感觉没戏了