当前位置:网站首页>Data security -- 13 -- data security lifecycle management
Data security -- 13 -- data security lifecycle management
2022-07-06 06:35:00 【Follow also】
One 、 Introduction
Data security Lifecycle Management , It starts with the safe collection or generation of data , Secure use of overlay data 、 Secure transport 、 Secure storage 、 Safety disclosure 、 Safe circulation and tracking , The whole process safety guarantee mechanism until safe destruction .
For the privacy lifecycle of data , It is generally divided into the following stages :
● Inform the data subject ( Privacy statement or notice )
● Data subject selection and consent
● Data collection or generation
● The data transfer
● Data storage and retention period management
● Data usage
● Data circulation and exit
● Data disclosure
● Data destruction
Two 、 Inform the data subject
For informing data subjects , Start with data collection , The purpose of the collected data should be clarified 、 Business and product range used 、 Protective measures, etc , Avoid collecting unnecessary user data . In order to protect the right to know of the data subject , And comply with the transparency requirements of laws and regulations , We need to inform the data subject of our privacy policy .
Take the most common website online services as an example , Usually, you need to place a named Privacy policy Hyperlinks for .
3、 ... and 、 Data subject selection and consent
Processing personal data , At least one of the six legal bases is required , These six bases are The user agrees to 、 Contractual obligations 、 Legal obligations 、 The core interests of data subjects or others 、 public interest 、 The legitimate interests of data controllers and third parties .
Among the six legal bases :
● Contractual obligations 、 Legal obligations 、 The core interests of data subjects or others 、 public interest These four bases use very limited scenarios , Not universal .
● Legitimate interests The most controversial 、 Most complaints , It needs to be avoided as much as possible .
therefore , Most commonly used in practice 、 The most important legal basis is The user agrees to .
When it may have a great impact on the data subject , In particular, it is necessary to obtain the effective consent or express consent of the data subject . The so-called effective consent , That is, by default, you cannot check "agree" for users , Users are required to actively check the consent option .
in addition , Different types of businesses should use different privacy policies , Instead of using a blanket privacy policy . Some activities mentioned in the privacy policy that may affect the interests of data subjects , For example, personalized advertising push , Switch options should be set , And it cannot be opened by default .
In order to effectively manage the consent of data subjects , The background needs to record the consent record of each data subject to each privacy policy version , When the privacy policy version is updated , The data subject needs to agree again .
Four 、 Secure collection or generation of data
After the user agrees , Should be informed in accordance with the privacy policy , Minimize collection . For the received data , Its data classification and classification should be determined . Data classification and classification determine what measures should be taken to protect it .
To prevent personal information disclosure , Appropriate pretreatment should be taken after data collection , Or measures to reduce privacy sensitivity , Upload to the server , There is no need to transmit original sensitive information .
5、 ... and 、 Secure transmission of data
The transmission of information should use HTTPS Or other encrypted channels . Transmit on the Internet , The preferred HTTPS Encrypted transmission mechanism , It is recommended to use a unified access gateway , Unified management of certificate private key , Enable uniformly HTTPS. Transmit on Intranet , Consider RPC The encrypted 、HTTPS Equal mechanism , Encrypted transmission of sensitive data .
6、 ... and 、 Safe storage and retention period management of data
Generally, encrypted storage measures are taken for the following data :
● password 、 secret key , Include database 、 Passwords and keys in the configuration file .
● Sensitive personal privacy data .
● alive UGC data ( User generated content ).
As for business data , You need to weigh , Especially involving retrieval 、 Sort 、 Sum calculation and other scenarios .
In terms of retention period , It mainly involves two types of data .
● The first is the identity data of the data subject , It is usually collected once , If there is no need to correct , Then it will be stored for a long time , Until the product goes offline or the user cancels the account , Delete the corresponding data .
● The second type is generated during the activity after registration , Such as pay / Records of consumption 、 Sports records, etc , According to the set retention period , Automatically delete or delete the corresponding encryption key when it expires .
7、 ... and 、 Safe use of data
In data usage 、 Retain 、 In the process of storage , Necessary safety control measures need to be taken , To ensure the security of personal data , This part usually includes :
● Access to data requires authorization based on identity 、 Access control 、 Audit mechanism .
● to grant authorization , For example, in addition to the users themselves , Authorize their friends to view their circle of friends information .
● Access control , For example, prevent the database from being directly opened to the public or have weak passwords .
● Retention period management , For payment / Records of consumption 、 Sports records, etc , According to the set retention period , Automatically delete or delete the corresponding encryption key when it expires .
● Data display , Some data cannot be displayed , Like passwords 、 Biometrics for identity authentication , Some data need desensitization , Such as name 、 Phone number 、 Address 、 Bank card number, etc .
● Data disclosure , Data before disclosure , Strict desensitization should be taken 、 To mark words and other measures 、 Due diligence and signing should be carried out before disclosure to data processors DPA.
8、 ... and 、 Data circulation and exit
For the safe flow of data , It is recommended not to provide raw data , It is encapsulated as a data service , Insert a tracking field that can be uniquely located to a specific business , Provide desensitization data query interface , Establish corresponding accounts for other businesses and authorize them 、 Limit the query frequency 、 Record the query log . If you have to provide raw data , Consider inserting some fake data that can uniquely locate the other party's business , It is used to locate the party responsible for the leakage of data in batches .
Provide data to other businesses through data interface , Other business demanders need to promise or sign confidentiality agreements , Disable caching 、 It is forbidden to delete tracking fields , And check the implementation when the other party's business goes online .
If the data is collected or generated domestically , By default, it should be stored in China . If you want to transfer abroad , It needs to be strictly evaluated , And consult the legal department of the enterprise .
If it's a cell phone APP And other scenes directly involving personal data exit , At least get the express consent of the user . Express consent is included in the privacy statement to actively and clearly inform 、 The user actively checks agree .
Nine 、 Data destruction
In practice , It is still quite difficult to truly destroy or make it unusable in the sense of security , In general , When the user requests deletion , You can delete the key of the corresponding record , Make the original encrypted data in the backup no longer available .
For retired hard disks , Generally, low-level formatting is required 、 Degaussing 、 Physical bending destruction and other means for destruction .
边栏推荐
- How much is the price for the seal of the certificate
- Play video with Tencent video plug-in in uni app
- Error getting a new connection Cause: org. apache. commons. dbcp. SQLNestedException
- The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
- 云服务器 AccessKey 密钥泄露利用
- Making interactive page of "left tree and right table" based on jeecg-boot
- 模拟卷Leetcode【普通】1061. 按字典序排列最小的等效字符串
- LeetCode每日一题(971. Flip Binary Tree To Match Preorder Traversal)
- 论文摘要翻译,多语言纯人工翻译
- Biomedical localization translation services
猜你喜欢
Luogu p2089 roast chicken
keil MDK中删除添加到watch1中的变量
oscp raven2靶机渗透过程
Apple has open source, but what about it?

翻译影视剧字幕,这些特点务必要了解
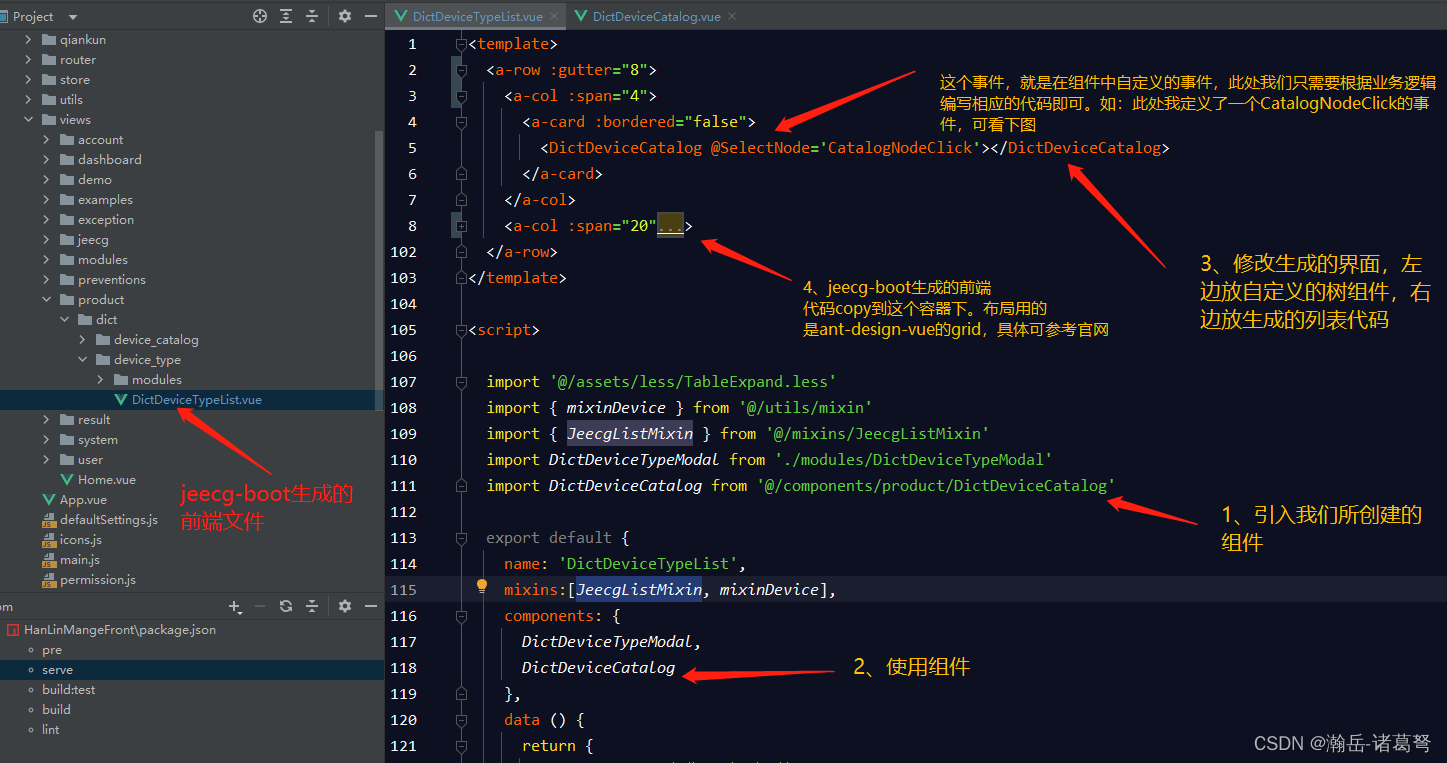
Modify the list page on the basis of jeecg boot code generation (combined with customized components)
MySQL5.72.msi安装失败

如何做好金融文献翻译?

Thesis abstract translation, multilingual pure human translation
MFC on the conversion and display of long string unsigned char and CString
随机推荐
LeetCode每日一题(1870. Minimum Speed to Arrive on Time)
Cobalt Strike特征修改
Basic knowledge of MySQL
Py06 字典 映射 字典嵌套 键不存在测试 键排序
Drug disease association prediction based on multi-scale heterogeneous network topology information and multiple attributes
记一个基于JEECG-BOOT的比较复杂的增删改功能的实现
生物医学本地化翻译服务
Data type of MySQL
模拟卷Leetcode【普通】1249. 移除无效的括号
红蓝对抗之流量加密(Openssl加密传输、MSF流量加密、CS修改profile进行流量加密)
如何做好互联网金融的英语翻译
Simulation volume leetcode [general] 1218 Longest definite difference subsequence
Simulation volume leetcode [general] 1405 Longest happy string
Selenium source code read through · 9 | desiredcapabilities class analysis
Oscp raven2 target penetration process
The internationalization of domestic games is inseparable from professional translation companies
Remember the implementation of a relatively complex addition, deletion and modification function based on jeecg-boot
How much is the price for the seal of the certificate
Technology sharing | common interface protocol analysis
模拟卷Leetcode【普通】1062. 最长重复子串