当前位置:网站首页>Buried point 111
Buried point 111
2022-07-05 10:44:00 【Code Bruce Lee】
Buried point
1、 What is burying point
1.1 Concept
Burying points can be understood as a toll station , The user's behavior is like driving on the highway , When there is no burying point , We can only know that someone is running on the highway , But which highway does the user run , Where did you go , We don't know what happened on the highway ; But after the burying point , It's like building a toll station on the highway , As long as users pass through the toll station, we will know , This is the burial point . The buried point data is when the user passes the toll station , What we want to know about users
1.2 classification
Code buried point
advantage : High controllability , Meet all needs
shortcoming : High R & D cost , High design cost
Easy to understand : We hired a construction team , This construction team is under your command , And build a toll station according to your designated location on the highway , This kind of construction is brick by brick
Visual burying point
advantage : It is easy to operate , Quick layout
shortcoming : Poor adaptability , Latitude matching factor ’ road ’ But different
Easy to understand : We will mold the toll station we need to build , Just place the mold at the specified position , Pour cement directly into the mold , The toll station is directly formed
Full burial point
advantage : We all know the user's every move
shortcoming : There is a large amount of data transmission , Data needs secondary cleaning , Occupy a lot of real-time resources for data transmission
2、 Type of buried point
03.png
2.1 Front buried point
It refers to the embedding point on the visual interface , As long as there is a visual operation page, we can regard it as a front-end embedding point
In the front-end embedding point, we mainly focus on user behavior , What the user browsed on the page 、 What did you click on , We can well understand the impact of page content on users' perception
2.2 Rear buried point
It refers to embedding points in back-end services that users cannot see or touch , such as : Order generation 、 Calculation of the amount 、 Triggering of conditions, etc
Pay more attention to business and logic in the back-end embedding point , After the user initiates behavioral interaction , Record the interactive data , for example : What is the content of the search 、 The result of the search ; From the data obtained, we can better optimize the strategy
3、 Front buried point
3.1 Automatic trigger
We often use the front-end embedding point PV( Page views , Focus on the number of page views , Open calculation once )/UV( User views , Focus on the number of browsing users , Record the number of open browsing users )
PV
Generally, pages have a life cycle , This life cycle is often 4 Stages , With VUE( Domestic front-end R & D framework ) Examples are : establish 、 load 、 to update 、 The destruction , this 4 The three stages represent the user from clicking open to browsing the web page to clicking close to exit the web page . Under normal circumstances, the user enters the page , First render some simple styles (html and css), Then load and update the data , Finally, the user clicks close to exit the page , If we subdivide it, it can be divided into pre creation 、 After creation 、 Before loading 、 After loading 、 Before updating 、 After the update 、 Before destruction 、 After destruction .
In our process PV/UV When we bury them , Even if the same latitude (PV/UV) Choose different stages for burying , And the results will be different . Under normal circumstances , Technology likes to make the burying point in loading , Update this 2 Stages . In this way, users need to see and see the data of buried points completely ( Will trigger the burying point ), But in special cases , Some users have poor network conditions , I can't load the page for half a day , Meet the white screen we often say , such PV The trigger of will be uncontrollable .
Because it's hard for us to know because of the problem of the network , Whether he touched our burial point or not . So in this situation , We can PV The trigger of is placed in “ establish ” This position , When the page is created successfully, the buried point data is triggered
Buried point
characteristic
establish
1、 Open a new page to calculate
2、 Will not count again because of refresh
load
1、 Only when data is loaded for the first time
2、 It will not be calculated again because of refresh
to update
1、 Every time the page is refreshed
UV
UV and PV The way of burying points is the same , The only difference is UV Need to be in PV Based on the unique identification .
Count the number of unique signs UV The number of , Generally, the only common signs are as follows
cell-phone number : After the user logs in to the page, he will make statistics according to his bound mobile phone number , But if the user is not logged in, it will not be able to count ;
cookie: Through cookie As the only indication , But because cookie It is easy to be modified in the user browser ;
localStorage: By storing a long-term unique identifier locally in the browser , But it can be cleaned manually ;
IP: By visiting the page ip Distinguish between addresses , If ip Changes will be calculated separately ;
seesionStorae: It is represented by the information of the server , Effective .
3.2 Interactive
It is common for users to click buttons and slide pages . We count the buttons (pv) And weight removal (uv), In this way, we can understand the usage of this function button , In this way, we can support some simple functions ab test
Or we can combine it with users' sliding behavior to bury points . Technology can monitor the sliding position of the user , To decide whether to trigger the burying point , This is also what we often call exposure and burial point
Exposure point
This kind of embedding point is usually used for user goods 、 Content recommendation . When we set the recommended products or content on the first screen , At the same time, the user enters the page for the first time , Then we can choose to use according to our own business pv or uv Pretend their exposure , But this is limited to fixed goods and content , In this way, when multiple commodities are exposed in rotation , It will be difficult to confirm the exposure of a single commodity because of the rotation mechanism of commodities , So generally, when we broadcast and expose multiple products in rotation , For the time being, only the exposure of this round robin module is counted , For the commodities in the module, we often use the exposure conversion rate . The calculation method is a bit like that of the carousel , Click volume of a single product ( Button pv/uv)/ Overall module exposure (pv/uv)= The conversion rate of a single commodity ; This kind of using page pv/uv As a way to calculate module and product exposure , Only modules with fixed exposure on the first screen . If the module or product that calculates the exposure is not on the first screen , So we use this method but it is unscientific 、 Not desirable
We need to trigger the exposure buried point in combination with the user's sliding screen , When the user slides to what position , When you can see this module , We triggered the burying point when we saw the module ; This is the time , We can consider using trigger times (pv) Or trigger person times (uv) To calculate
边栏推荐
- 爬虫(9) - Scrapy框架(1) | Scrapy 异步网络爬虫框架
- Workmanager Learning one
- Activity enter exit animation
- 各位大佬,我测试起了3条线程同时往3个mysql表中写入,每条线程分别写入100000条数据,用了f
- [JS] array dimensionality reduction
- 2022年T电梯修理操作证考试题及答案
- Secteur non technique, comment participer à devops?
- 基于昇腾AI丨爱笔智能推出银行网点数字化解决方案,实现从总部到网点的信息数字化全覆盖
- C语言实现QQ聊天室小项目 [完整源码]
- websocket
猜你喜欢
【js学习笔记五十四】BFC方式

How did automated specification inspection software develop?
2022年T电梯修理操作证考试题及答案

【Vite】1371- 手把手开发 Vite 插件
重磅:国产IDE发布,由阿里研发,完全开源!
Workmanager learning 1
Go-3-第一个Go程序
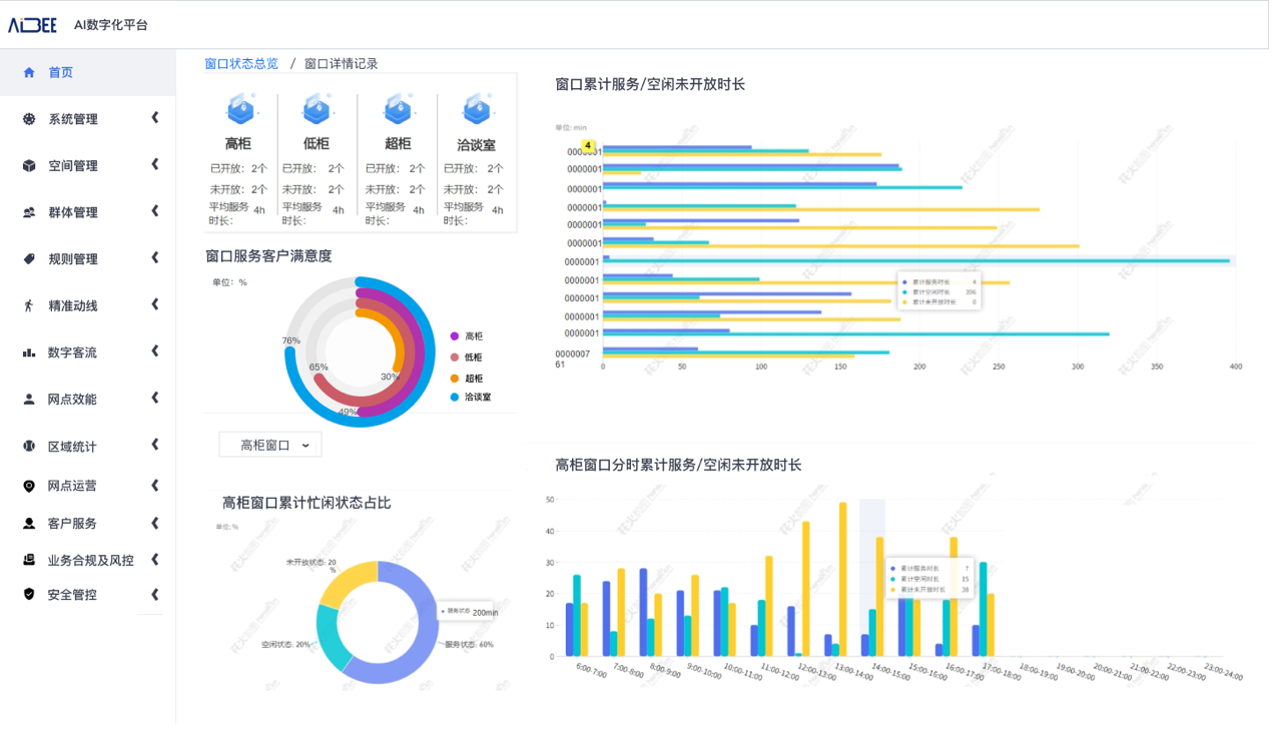
基于昇腾AI丨爱笔智能推出银行网点数字化解决方案,实现从总部到网点的信息数字化全覆盖
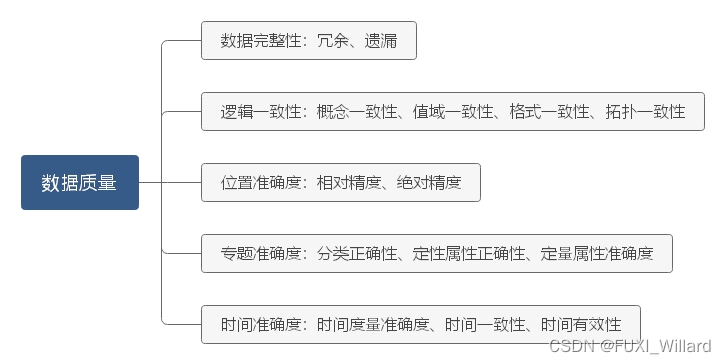
Learning notes 5 - high precision map solution
![C language QQ chat room small project [complete source code]](/img/4e/b3703ac864830d55c824e1b56c8f85.png)
C language QQ chat room small project [complete source code]
随机推荐
Go-2-Vim IDE常用功能
Go语言-1-开发环境配置
各位大佬,我测试起了3条线程同时往3个mysql表中写入,每条线程分别写入100000条数据,用了f
第五届 Polkadot Hackathon 创业大赛全程回顾,获胜项目揭秘!
PHP solves the problems of cache avalanche, cache penetration and cache breakdown of redis
SAP ui5 objectpagelayout control usage sharing
DDOS攻击原理,被ddos攻击的现象
2022年危险化学品经营单位主要负责人特种作业证考试题库及答案
Flink CDC cannot monitor MySQL logs. Have you ever encountered this problem?
AtCoder Beginner Contest 258「ABCDEFG」
WorkManager的学习二
The first product of Sepp power battery was officially launched
Pseudo class elements -- before and after
5g NR system architecture
谈谈对Flink框架中容错机制及状态的一致性的理解
WorkManager学习一
BOM//
Timed disappearance pop-up
使用bat命令一键启动常用浏览器
数据类型、