当前位置:网站首页>PhD battle-11 preview | review and prospect backdoor attack and defense of neural network
PhD battle-11 preview | review and prospect backdoor attack and defense of neural network
2022-07-02 16:57:00 【Aitime theory】
Click on the blue words

Pay attention to our
AI TIME Welcome to everyone AI Fans join in !
7 month 9 Japan 20:00-21:30, In this issue PhD Debate Xiang Zhen, a doctoral student from the Department of electronic engineering at Pennsylvania State University, was invited to the live broadcast room 、 Li Yiming, a doctoral student of Tsinghua University 、 Zeng Yi, a doctoral student in Computer Engineering at Virginia Tech, and Shen Guangyu, a doctoral student in computer science at Purdue University , With you Review and prospect the backdoor attack and defense of neural network .
1. In recent years , Backdoor attacks against neural networks have attracted widespread attention . Features of existing backdoor attacks , The difficulty of design , And what are the future research directions ?
2. Both backdoor attack and counter attack need to modify the sample in the prediction process , Backdoor attack and counter attack are also two important directions of neural network security research nowadays , How do you see the differences and similarities between these two directions ?
3. Characteristics of existing backdoor defense , The difficulty of design , And what are the future research directions ?
4. How to view and design backdoor attack and backdoor defense on new missions ?

Bili Bili live channel
Sweep yards attention AITIME Bli bli official account reservation live broadcast
* Guest profile *

Xiang Zhen :
Ph. D. candidate, Department of electronic engineering, Pennsylvania State University , Learn from David J. Miller as well as George Kesidis. The main research direction is reliable artificial intelligence ( Including backdoor attacks , Poison attack , And avoiding attacks in many directions ) And statistical signal processing . stay TNNLS,Computer&Security,Neural Computation Etc , as well as ICLR,ICASSP,ICCV He has published many academic papers and held many international conferences 、 The reviewer of the Journal .

Li Yiming :
The fourth year of Tsinghua University is a doctoral student , Under the guidance of Xia Shutao and Jiang Yong . Its research direction is AI Security , It mainly includes back door learning 、 Against learning and data privacy protection . Its presence ICCV、 ICLR、 AAAI、IEEE TNNLS、 Pattern Recognition etc. AI Many academic papers were published in relevant top conferences and journals . Was invited to serve as AAAI 2022 Member of the high procedure Committee of the conference ,NeurIPS、ICML、ICLR Wait for the members of the meeting procedure Committee , as well as IEEE TPAMI、IEEE TDSC、IEEE TNNLS Wait for the reviewer of the Journal . Tsinghua University ‘ Futurist ’、 tencent ‘ Rhinoceros elite talent ’ Such as the honor . Personal home page :http://liyiming.tech

Zeng Yi :
A second year doctoral student in Computer Engineering at Virginia Tech , Learn from Ruoxi Jia. My main interest is artificial intelligence security . His thesis was awarded the th 20 the ICA3PP International Conference best paper award . His papers are mainly published in the computer field ( Such as ICLR、ICCV、IJCAI、AsiaCCS) And the top issue ( for example IEEE TII、IEEE TC、IEEE Access etc. ). Personal home page :https://www.yi-zeng.com/

Shen Guangyu :
Second year doctoral student in computer science, Purdue University , Learn from Xiangyu Zhang. Its research direction is AI Security , Backdoor attacks included in different modal Neural Networks , Detection and defense ( Like computer vision , natural language processing ) stay CVPR, ICML, S&P He has published an academic paper and served as the reviewer of the top conference for many times . Personal home page : https://www.cs.purdue.edu/homes/shen447/
* host *

Maohaitao :
A first-year doctoral student at Michigan State University , I studied under Professor Tang Jiliang , Once got CIKM2021 best short paper award, Was invited to serve as NeurIPS,ICML Wait for the members of the meeting procedure Committee .
After the live broadcast, you can ask questions in the group , Please add “AI TIME Little helper ( WeChat ID :AITIME_HY)”, reply “PhD-5”, Will pull you into “AI TIME PhD Communication group -5”!
AI TIME Wechat assistant

Lord do :AI TIME
Associated Media :AI Data pie 、 Academic headlines
partners : Wisdom spectrum ·AI、 Chinese Academy of Engineering Zhiling live 、 School Online 、 Kou enjoys academic 、AMiner、 Ever Chain action 、 Scientific research cloud
Excellent articles in the past are recommended
Remember to pay attention to us ! There is new knowledge every day !
About AI TIME
AI TIME From 2019 year , It aims to carry forward the spirit of scientific speculation , Invite people from all walks of life to the theory of artificial intelligence 、 Explore the essence of algorithm and scenario application , Strengthen the collision of ideas , Link the world AI scholars 、 Industry experts and enthusiasts , I hope in the form of debate , Explore the contradiction between artificial intelligence and human future , Explore the future of artificial intelligence .
so far ,AI TIME Has invited 600 Many speakers at home and abroad , Held more than 300 An event , super 210 10000 people watch .

I know you.
Looking at
Oh
~

Click on Read the original Reservation live broadcast !
边栏推荐
- Easy language ABCD sort
- John blasting appears using default input encoding: UTF-8 loaded 1 password hash (bcrypt [blowfish 32/64 x3])
- 渗透工具-内网权限维持-Cobalt strike
- Penetration tool - intranet permission maintenance -cobalt strike
- Role and function of uboot
- Leetcode1380: lucky numbers in matrix
- vscode设置删除行快捷键[通俗易懂]
- A week of short video platform 30W exposure, small magic push helps physical businesses turn losses into profits
- Headline | Asian control technology products are selected in the textile and clothing industry digital transformation solution key promotion directory of Textile Federation
- 618 reprise en profondeur: la méthode gagnante de la famille Haier Zhi
猜你喜欢
Configure MySQL under Linux to authorize a user to access remotely, which is not restricted by IP

Privacy computing technology innovation and industry practice seminar: Learning

MOSFET器件手册关键参数解读
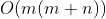
Leetcode1380: lucky numbers in matrix
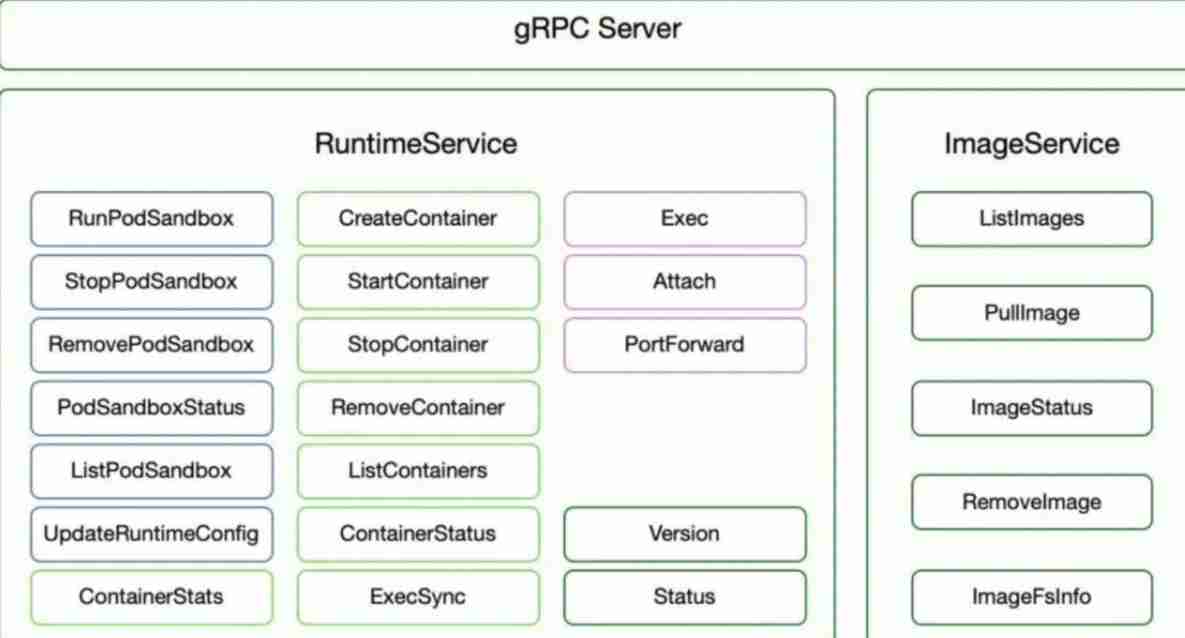
Kubernetes three open interfaces first sight

linux下配置Mysql授权某个用户远程访问,不受ip限制

OpenPose的使用
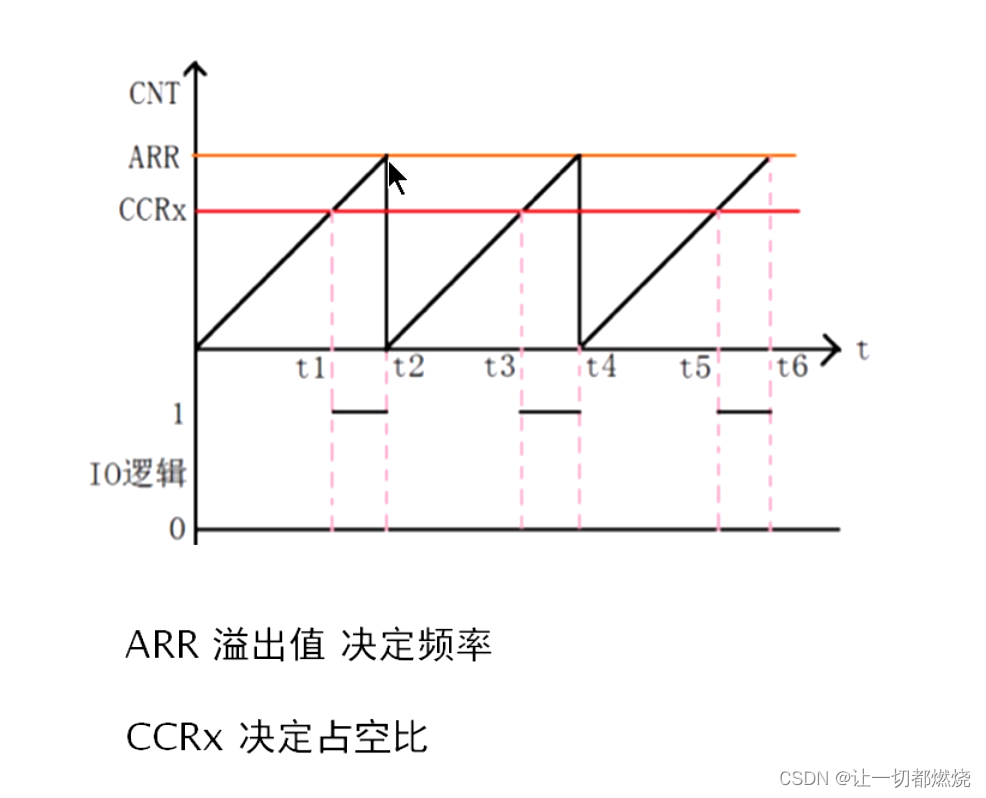
PWM breathing lamp
![john爆破出现Using default input encoding: UTF-8 Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])](/img/4c/ddf7f8085257d0eb8766dbec251345.png)
john爆破出现Using default input encoding: UTF-8 Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])

pwm呼吸燈
随机推荐
unity Hub 登录框变得很窄 无法登录
Student course selection system (curriculum design of Shandong Agricultural University)
Vscode setting delete line shortcut [easy to understand]
pwm呼吸灯
2322. 从树中删除边的最小分数(异或和&模拟)
Unity uses ugui to set a simple multi-level horizontal drop-down menu (no code required)
SQL solves the problem of continuous login deformation holiday filtering
<四> H264解码输出yuv文件
Configure ARP table entry restrictions and port security based on the interface (restrict users' private access to fool switches or illegal host access)
学习周刊-总第60期-2022年第25周
易语言abcd排序
Download blender on Alibaba cloud image station
Global and Chinese markets for airport baggage claim conveyors 2022-2028: technology, participants, trends, market size and share Research Report
Privacy computing technology innovation and industry practice seminar: Learning
Deep learning image data automatic annotation [easy to understand]
Aike AI frontier promotion (2.15)
john爆破出現Using default input encoding: UTF-8 Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Day 18 of leetcode dynamic planning introduction
Yyds dry goods inventory # look up at the sky | talk about the way and principle of capturing packets on the mobile terminal and how to prevent mitm
PCL least median square method fitting plane
