当前位置:网站首页>Database -- acid of transaction -- introduction / explanation
Database -- acid of transaction -- introduction / explanation
2022-07-02 10:01:00 【It blade out of sheath】
brief introduction
This article introduces the transaction of database ACID.
The transaction is ACID Four features : Atomicity (Atomic)、 Uniformity (Consistent)、 Isolation, (Isolation)、 persistence (Duration).
Atomicity (Atomic)
explain
Transaction must be atomic unit of work , Modify the data , All or nothing , All or nothing .
Uniformity (Consistent)
explain
The transaction is completed , All data must be kept consistent .
Example
user A And the user B The sum of the two is 700, No matter A and B How to transfer money between banks , The money of two users must add up to 700, This is consistency .
Isolation, (Isolation)
explain
Changes made by concurrent transactions must be isolated from changes made by any other concurrent transactions .
Detailed explanation
In a concurrent environment , When different transactions manipulate the same data at the same time , Each transaction has its own full data space . Changes made by concurrent firms must be isolated from changes made by any other concurrent firms .
When transactions view data updates , The state of the data is either the state of another transaction before it was modified , Or another transaction changes its state , Transactions do not see data in the intermediate state .
persistence (Duration)
explain
After the transaction completes , The status change of the corresponding data in the database should be Permanence Of , It will not be rolled back .
Detailed explanation
If the transaction has been committed , But data is also persistent , At this time, the system is powered off or down , You can also re operate the non persistent data according to the transaction log , Put it recovery To the state that the transaction ends successfully .
Pre written logs (Write-ahead logging, abbreviation WAL) Mechanism
Many databases use pre written logs (Write-ahead logging, abbreviation WAL) Mechanism , To ensure transaction persistence and data integrity , At the same time, the frequent data refresh based on transactions is avoided to a great extent IO Impact on performance .
In the use of WAL In the system , All changes are written to the log first , Then it is applied to the system state . Let's say a program loses power while it's doing something . On reboot , The program may need to know whether the operation performed at that time was successful or partially successful or failed . Program can check log file , Compare the planned operation content with the actual operation content in case of sudden power failure . On the basis of this comparison , The program can then decide whether to undo the action or continue to complete the action , Or keep it as it is .
边栏推荐
- Fragmenttabhost implements the interface of housing loan calculator
- C language programming problems
- Alibaba cloud SLS log service
- QT signal slot summary -connect function incorrect usage
- Mobile mall app solution: how much is it to make an app? Detailed explanation of APP mall development content
- Navicat remote connection MySQL reports an error 1045 - access denied for user 'root' @ '222.173.220.236' (using password: yes)
- 2837xd code generation - stateflow (2)
- 2837xd code generation module learning (4) -- idle_ task、Simulink Coder
- Alibaba / popular JSON parsing open source project fastjson2
- Personal experience & blog status
猜你喜欢

Alibaba cloud SLS log service
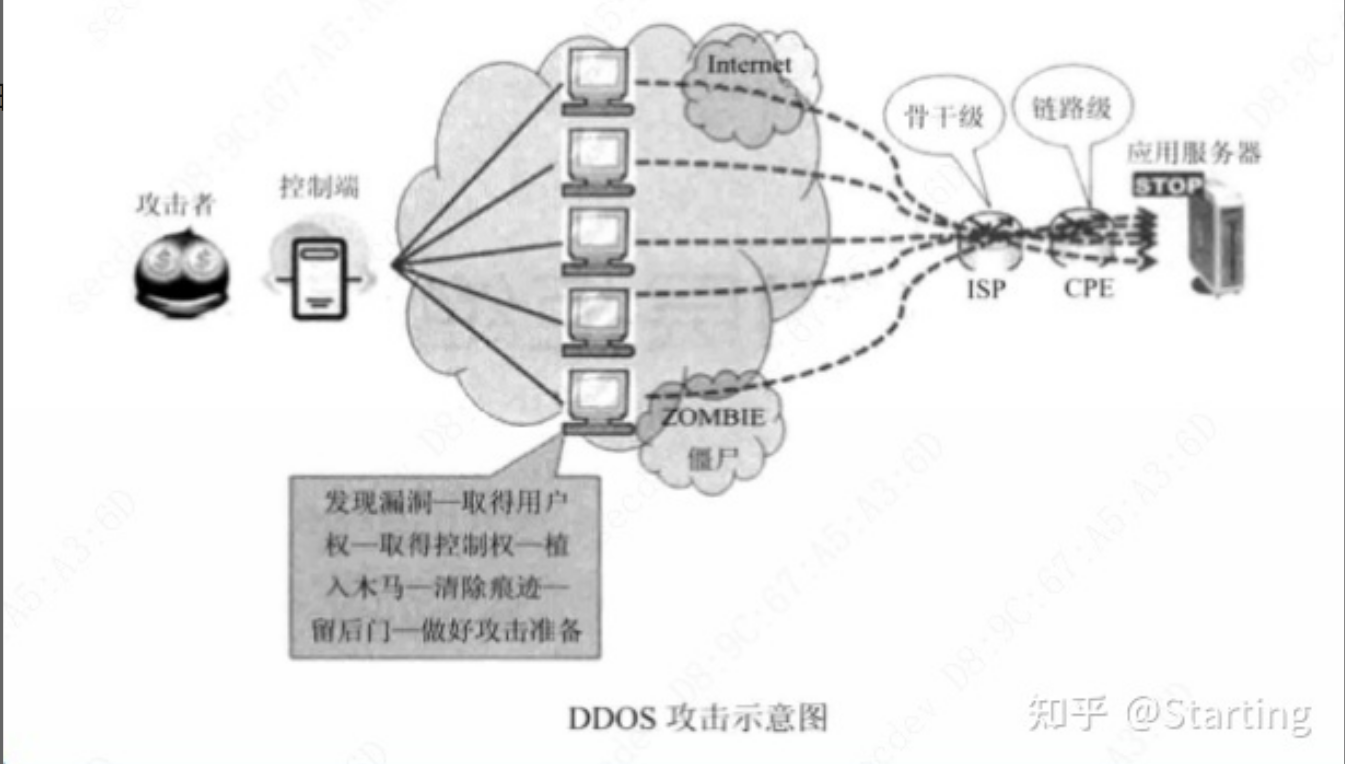
滲透測試的介紹和防範

2837xd 代码生成——StateFlow(3)
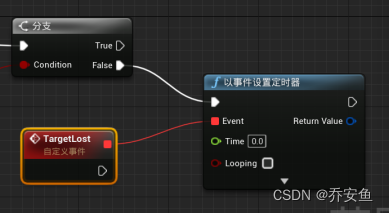
Ue5 - ai Pursuit (Blueprint, Behavior tree)

Kinect DK obtains color RGB images in cv:: mat format (used in openpose)

MySQL default transaction isolation level and row lock

三相逆变器离网控制——PR控制

Introduction et prévention des essais de pénétration
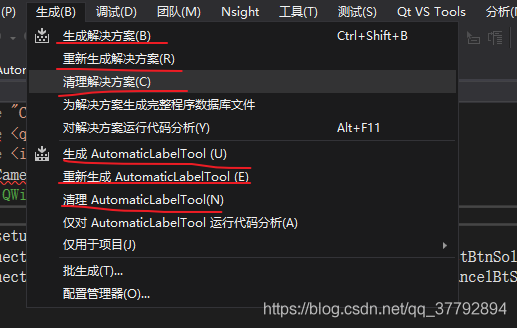
vs+qt 设置应用程序图标

Bugkuctf-web24 (problem solving ideas and steps)
随机推荐
Because of hard work, the fruit goes with fate
Save video opencv:: videowriter
2837xd代码生成模块学习(2)——ADC、ePWM模块、Timer0
2837xd code generation - Summary
Blender多镜头(多机位)切换
Error reporting on the first day of work (incomplete awvs unloading)
Bugkuctf-web21 (detailed problem solving ideas and steps)
Skywalking理论与实践
C language strawberry
Web security and defense
Junit5 supports suite methods
2837xd 代码生成——补充(1)
C language: making barrels
C语言之最小数
Failed to configure a DataSource: ‘url‘ attribute is not specified and no embedd
【虚幻】过场动画笔记
Off grid control of three-phase inverter - PR control
A model can do two things: image annotation and image reading Q & A. VQA accuracy is close to human level | demo can be played
2837xd 代码生成——补充(3)
Alibaba / popular JSON parsing open source project fastjson2