当前位置:网站首页>[C language] General method of expression evaluation
[C language] General method of expression evaluation
2022-07-31 03:19:00 【rookieﻬ°】
How expressions are evaluated:
- The expression is evaluated to see if there is a shaping promotion or arithmetic conversion, and then the calculation is performed
- When the expression is actually calculated, first look at the priority of the adjacent operators to decide who is calculated first
- In the case of the same priority of adjacent operators, the calculation order is determined by the associativity of the operators
Of course, bad input methods will cause the program to have multipleAs a result, we should therefore write the calculation formula without an uprising.For example, the following code has different results in different compilation environments:
#include Different compilation environments can get the following results:
- 10
- 12
- 9
Therefore, we must pay attention to develop a good code input method.
边栏推荐
猜你喜欢
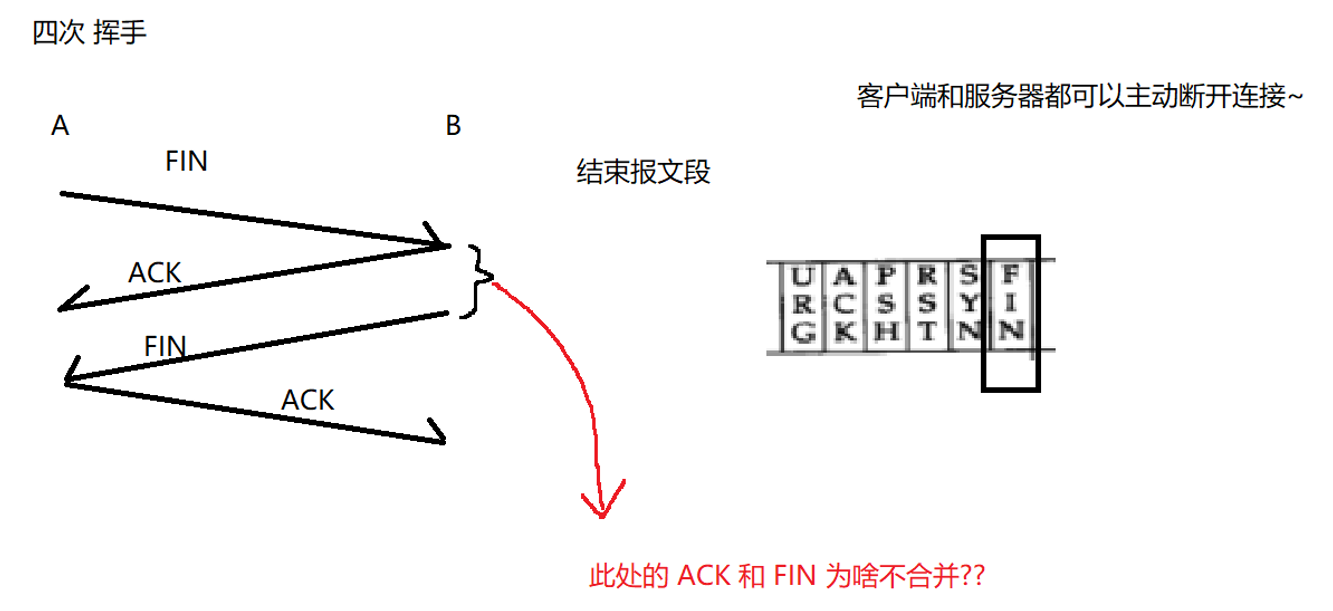
TCP详解(一)
Crypto Firms Offer Offer To Theft Hackers: Keep A Little, Give The Rest

VS QT——ui不显示新添加成员(控件)||代码无提示

SIP Protocol Standard and Implementation Mechanism
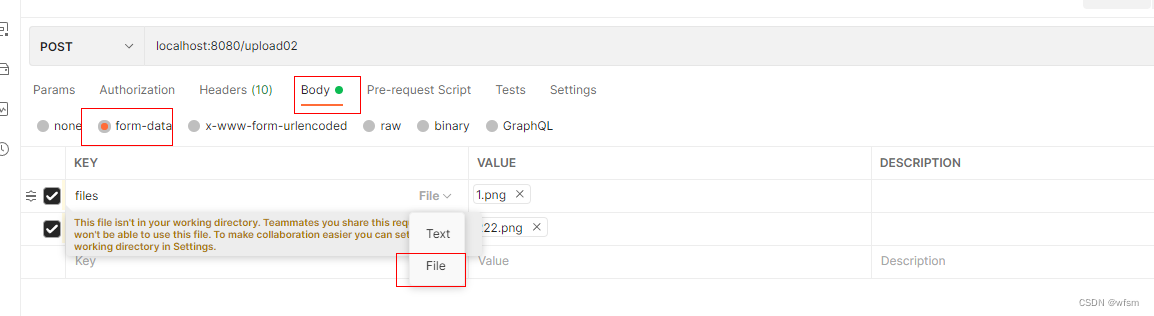
MultipartFile文件上传
Chapter 9 SVM Practice
STM32 problem collection

SIP协议标准和实现机制

Detailed explanation of TCP and UDP
Local area network computer hardware information collection tool
随机推荐
IDEA comment report red solution
WebSocket Session is null
Analysis summary - self-use
Distributed locks and three implementation methods
原子操作 CAS
刚出道“一战成名”,安全、舒适一个不落
VS QT——ui不显示新添加成员(控件)||代码无提示
Day32 LeetCode
Detailed explanation of TCP (2)
Redis implements distributed locks
【C语言】三子棋(经典解法+一览图)
Key Technologies of Interface Testing
[Compilation principle] Design principle and implementation of recursive descent parsing
遗留系统的自动化策略
MultipartFile file upload
LeetCode simple problem to find the subsequence of length K with the largest sum
LeetCode简单题之两个数组间的距离值
SQL injection Less46 (injection after order by + rand() Boolean blind injection)
PMP WeChat group daily exercises
Database implements distributed locks