当前位置:网站首页>网络安全-联合查询注入
网络安全-联合查询注入
2022-07-07 21:50:00 【IT之一小佬】
边栏推荐
- OC variable parameter transfer
- This time, let's clear up: synchronous, asynchronous, blocking, non blocking
- Explain in detail the communication mode between arm A7 and risc-v e907 on Quanzhi v853
- 行测-图形推理-6-相似图形类
- 行測-圖形推理-4-字母類
- Are the microorganisms in the intestines the same as those on the skin?
- Line measurement - graphic reasoning -9- line problem class
- Gbu1510-asemi power supply special 15A rectifier bridge gbu1510
- Leetcode1984. Minimum difference in student scores
- 每日一题——PAT乙级1002题
猜你喜欢
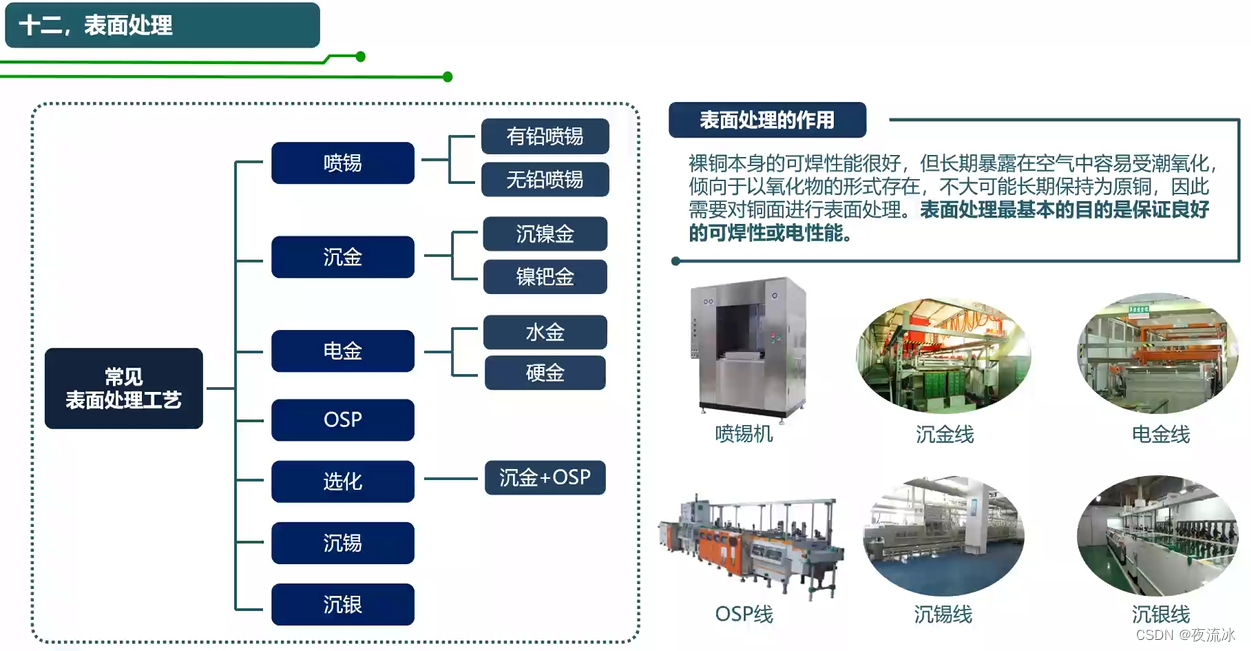
知识点滴 - PCB制造工艺流程

Sword finger offer 28 Symmetric binary tree
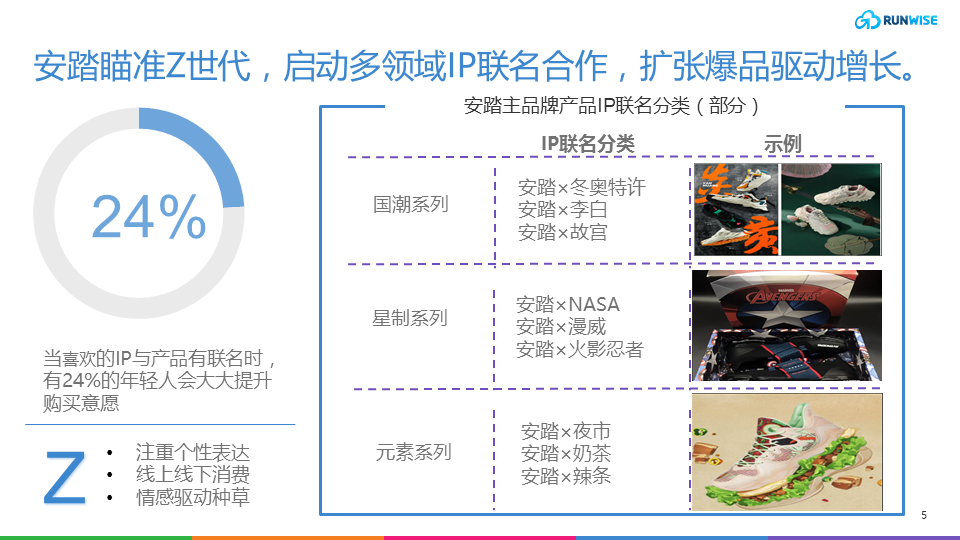
Anta DTC | Anta transformation, building a growth flywheel that is not only FILA

一次搞明白 Session、Cookie、Token,面试问题全稿定
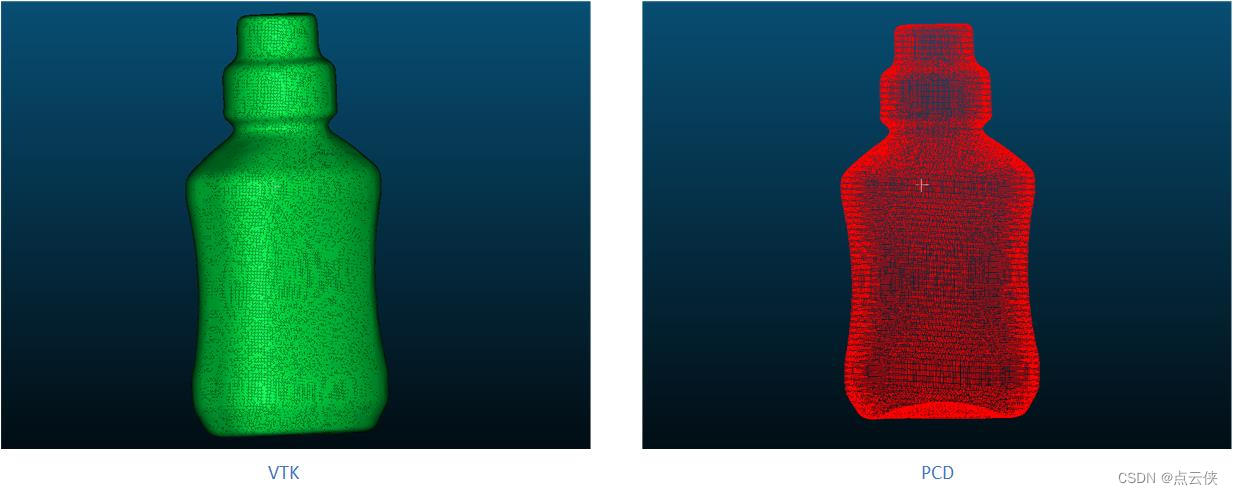
PCL . VTK files and Mutual conversion of PCD
![Leetcode interview question 02.07 Linked list intersection [double pointer]](/img/a5/58b4735cd0e47f1417ac151a1bcca4.jpg)
Leetcode interview question 02.07 Linked list intersection [double pointer]

GBU1510-ASEMI电源专用15A整流桥GBU1510
![Leetcode19. Delete the penultimate node of the linked list [double pointer]](/img/a9/809b93d1ffd11ba4a9074ac8e2bdee.jpg)
Leetcode19. Delete the penultimate node of the linked list [double pointer]
Unity and webgl love each other
XMIND mind mapping software sharing
随机推荐
微信论坛交流小程序系统毕业设计毕设(7)中期检查报告
Leetcode interview question 02.07 Linked list intersection [double pointer]
Cause analysis and solution of too laggy page of [test interview questions]
Debezium series: binlogreader for source code reading
Line measurement - graphic reasoning -9- line problem class
Line test - graphic reasoning -5- one stroke class
7-51 combination of two ordered linked list sequences
This time, let's clear up: synchronous, asynchronous, blocking, non blocking
Leetcode94. Middle order traversal of binary trees
Understand the session, cookie and token at one time, and the interview questions are all finalized
微信论坛交流小程序系统毕业设计毕设(1)开发概要
Explain in detail the communication mode between arm A7 and risc-v e907 on Quanzhi v853
It's no exaggeration to say that this is the most user-friendly basic tutorial of pytest I've ever seen
行测-图形推理-1-汉字类
The wonderful relationship between message queue and express cabinet
PCL .vtk文件与.pcd的相互转换
Why is network i/o blocked?
微信论坛交流小程序系统毕业设计毕设(4)开题报告
Circumvention Technology: Registry
7-18 simple simulation of banking business queue