当前位置:网站首页>A new understanding of how to encrypt industrial computers: host reinforcement application
A new understanding of how to encrypt industrial computers: host reinforcement application
2022-07-04 06:49:00 【CNSINDA_ HK】
Mainframe reinforcement
Recently, the concept of host reinforcement has been heated , The function of host reinforcement is also being concerned by those who are committed to server security .
So what is host reinforcement ?
Host reinforcement is actually a security mark for the system 、 Access control and other multi-layer and three-dimensional protective measures , Make up for operating system defects .
It can be understood as putting a lock on the main machine , Redefine the functions of each module of the operating system , Build an independent identity authentication system , When anti-virus software 、 When the firewall doesn't work , The host can still be protected , Prevent viruses and Trojans from invading , Prevent core data from being peeped 、 Be destroyed 、 Be tampered with 、 Stolen ! By guarding against external attacks , Prevent internal active disclosure , Solve abnormal behaviors such as unauthorized access , Make up for the security shortcomings of traditional information security solutions in the host layer , Improve the overall security protection ability of the operating system .
To make a long story short , Host reinforcement and anti-virus software are two completely different concepts , They are complementary , Not a substitute relationship .
The core points of host reinforcement :
1、 System reinforcement
Lock the debugged system , Become a trusted system .
In a trusted system , Illegal procedure 、 Scripts can't run . And it will not affect data access .
Even if the system has vulnerabilities , Even administrator privileges are lost , This trusted system is secure .
2、 Program reinforcement
The executable program is signed by trusted signature 、 Start the script in real time hash Value verification , If the verification fails, the startup is rejected , And trusted programs cannot be disguised .
3、 Document reinforcement
Protect files of the specified type from tampering .
4、 Disk encryption
Create a safe sandbox , The sandbox is isolated from the outside , Encrypt the data in the sandbox , Ensure that the data can only be used under the premise of effective authorization management , To be decrypted . If there is no authorization , Even administrators cannot copy and use this data , Even system cloning does not work .
5、 Database hardening ( Structured data )
first floor : Database files are forbidden to be accessed and tampered with by unfamiliar programs . Ensure database file level security .
The second floor : Database port access trusted filtering , Only business programs are allowed to connect to the database port , At the end of the connection string IP+ port + In the account password , Append process identification .
The third level : Database connection SQL Intelligent filtering of text , Prevent critical data from being retrieved and accessed , Prevent the data in the database from being accessed illegally , Prevent dangerous operations of database forms .
Host reinforcement application scenario :
1、 Protect enterprise server security . Server anti blackmail virus 、 Trojan horse 、 mill 、 Data tampering, etc .
2、 Host data anti disclosure protection . Without affecting the normal operation and maintenance of the host , Encrypt and protect sensitive data , Prevent core data from being stolen or tampered with .
3、 Business system host ( Including professional operating system embedded in the equipment ) Best state locking , Reduce viruses through process whitelist control 、 Number of illegal programs running , Greatly reduce the operation and maintenance of the host .
4、 Disk encryption , Even if the server is stolen , The hard disk was removed , The protected data is still encrypted .
Which host reinforcement brands are worth recommending :
At present, several brands that have done well in the field of host reinforcement are known in the market :
1、 Xinda's MCK Mainframe reinforcement .
2、 Wisteria cloud security .
3、 Luoan Technology .
4、 wave .
5、 Anheng .
6、 Convinced .
7、 Tian Rong Xin .

In no particular order . Personal recommendations MCK Strengthen the host , Because what our company buys is MCK Mainframe reinforcement . It is said that their sandbox encryption is also an old brand in the industry , You can rely on .
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption
The purpose is to prevent extortion virus , Mainframe reinforcement , System reinforcement , Industrial control security server anti-virus , Business system anti-virus , Server intrusion prevention , Production line anti-virus , Industrial computer encryption , Industrial computer reinforcement , Server data security , Industrial control system host safety , Device encryption , Industrial computer anti-virus , Industrial computer encryption , Algorithm encryption , Program encryption anti copy , Super dongle , Device anti cracking , Equipment authorization management , Device antivirus , Industrial computer authorization management , Smart device encryption

边栏推荐
- Tar source code analysis 8
- Can the out of sequence message complete TCP three handshakes
- 《国民经济行业分类GB/T 4754—2017》官网下载地址
- ORICO ORICO outdoor power experience, lightweight and portable, the most convenient office charging station
- [backpack DP] backpack problem
- Mysql 45讲学习笔记(十)force index
- MySQL 45 lecture learning notes (VI) global lock
- 2022 wechat enterprise mailbox login entry introduction, how to open and register enterprise wechat enterprise mailbox?
- MySQL 45 learning notes (XI) how to index string fields
- What is a spotlight effect?
猜你喜欢
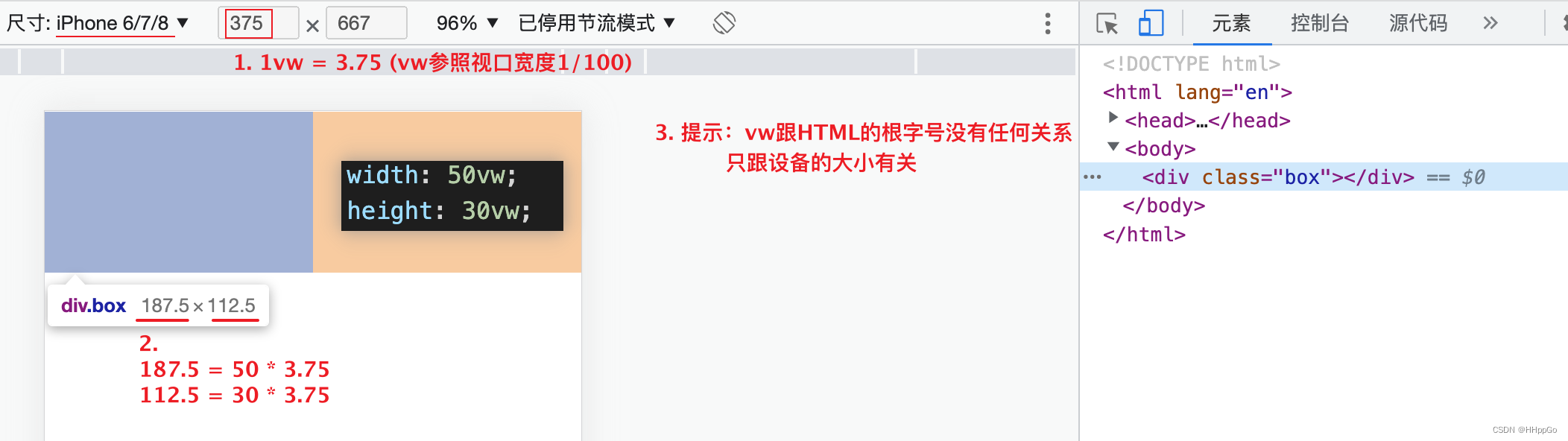
Mobile adaptation: vw/vh
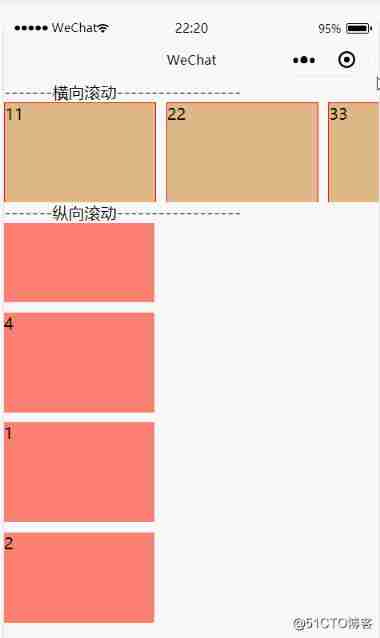
Wechat applet scroll view component scrollable view area

【MySQL】数据库视图的介绍、作用、创建、查看、删除和修改(附练习题)
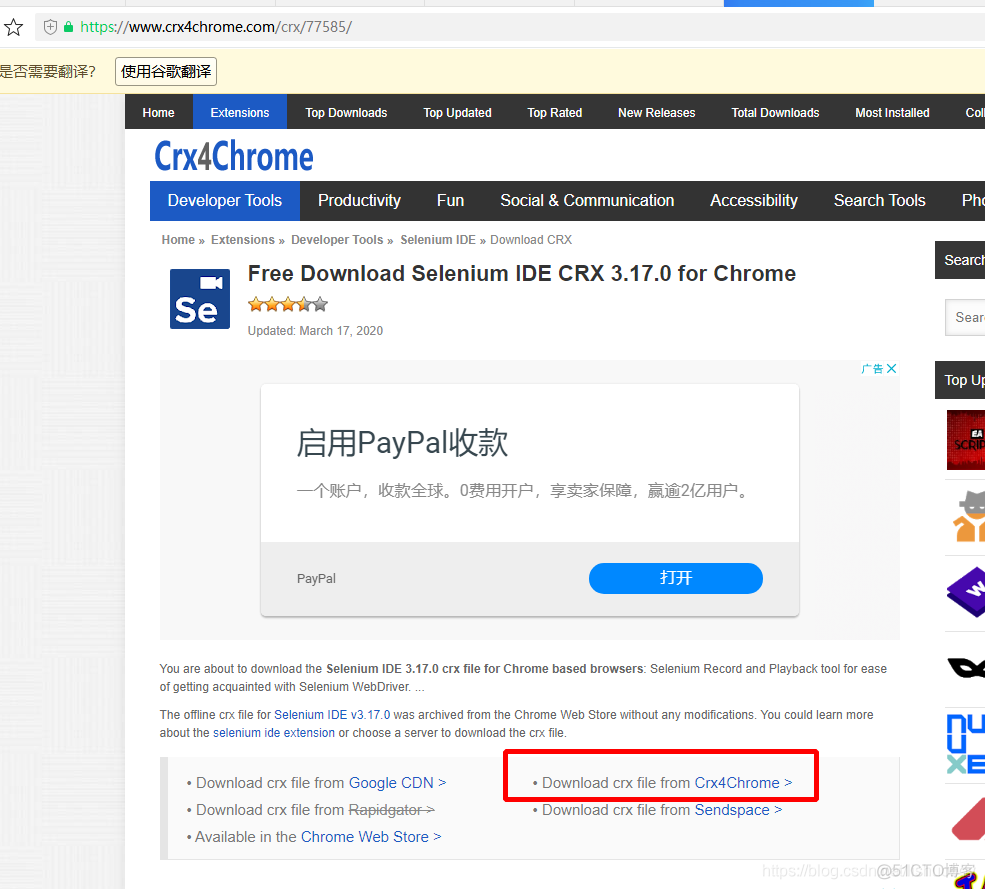
selenium IDE插件下载安装使用教程
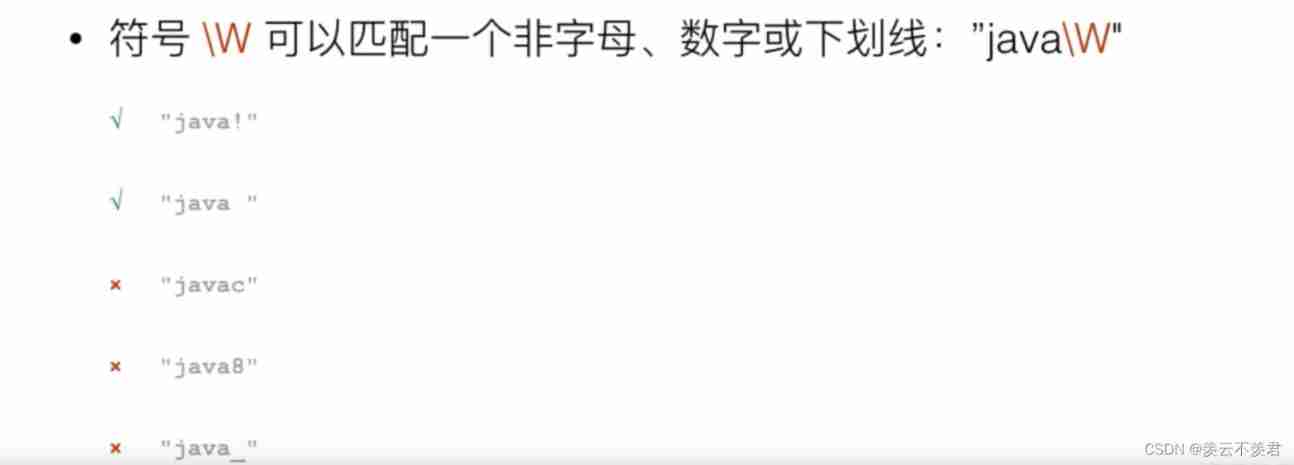
regular expression
uniapp小程序分包

what the fuck! If you can't grab it, write it yourself. Use code to realize a Bing Dwen Dwen. It's so beautiful ~!

Common usage of time library
P26-P34 third_ template
About how idea sets up shortcut key sets
随机推荐
Centos8 install mysql 7 unable to start up
响应式移动Web测试题
Mobile adaptation: vw/vh
Cochez une colonne d'affichage dans une colonne de tableau connue
Responsive mobile web test questions
请问旧版的的常用SQL怎么迁移到新版本里来?
Since DMS is upgraded to a new version, my previous SQL is in the old version of DMS. In this case, how can I retrieve my previous SQL?
tars源码分析之2
CORS is not intended to protect API endpoints - nikofischer
Google Chrome Portable Google Chrome browser portable version official website download method
tars源码分析之8
C # symmetric encryption (AES encryption) ciphertext results generated each time, different ideas, code sharing
MySQL relearn 2- Alibaba cloud server CentOS installation mysql8.0
Arcpy uses the updatelayer function to change the symbol system of the layer
[problem record] 03 connect to MySQL database prompt: 1040 too many connections
【FPGA教程案例7】基于verilog的计数器设计与实现
Variables d'environnement personnalisées uniapp
STM32 单片机ADC 电压计算
2022年,或许是未来10年经济最好的一年,2022年你毕业了吗?毕业后是怎么计划的?
11. Dimitt's law