当前位置:网站首页>Redis interview question set
Redis interview question set
2022-07-04 06:38:00 【Chat with Lao Wang】
The annual interview peak is coming again , are you ready ? Today, I sorted out what I had done before and what I interviewed Redis The real questions and answers have been sorted out and shared with everyone . In particular, it is classified , It is convenient for everyone to remember according to the module . Ongoing update ...
All the interview questions are here ......
Welcome to your attention + Input [ Interview questions ] + Get all information
Catalog
6、Redis Typical problem solutions
Redis As the mainstream NoSQL technology , It has been widely used in the Internet . Especially in major domestic companies are very popular , For example, Ali. 、 byte 、 Baidu 、 JD.COM 、 Millet, etc. . therefore ,Redis It has also become a must ask in the interview of large factories .
Today, I sorted out what I had done before and what I interviewed Redis The real questions and answers have been sorted out and shared with everyone . In particular, it is classified , It is convenient for everyone to remember according to the module .
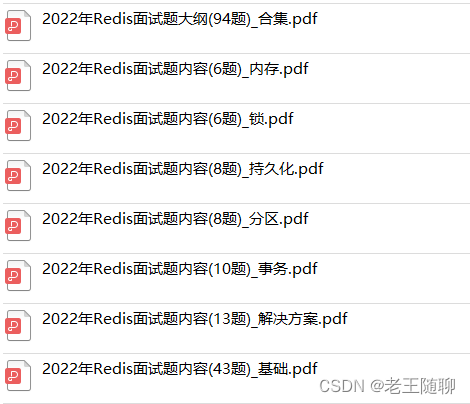
1、Redis Basics
1、 What is? Redis?
2、Redis What are the advantages and disadvantages ?
3、 Why cache Redis?
4、 Why use Redis without map/guava Do the cache ?
5、Redis Why so soon? ?
6、Redis What are the data types ?
7、Redis Application scenarios of ?
8、Redis What are the specific operations and application scenarios of each data type ?
9、Redis How the recycling process works ?
10、 What is the maximum storage capacity of a string type value ?
11、 If Redis There are 1 One hundred million key, Among them is 10w individual key It starts with a fixed known prefix , If you find them all ?
12、 If this redis Providing services for online business , That use keys What's wrong with the instructions ?
13、 Why use redis?
14、 What is distributed lock ?
15、 find redis A large number of key?
16、 How to use redis Do message queuing ?
17、 a large number of key Expire at the same time , What to pay attention to ?
18、 What is cache penetration , Cache breakdown ?
19、redis and memcached What's the difference? ?
20、redis Thread model of ?
21、redis Why single process 、 Single thread is also fast ?
22、redis Expiration strategy ?
23、redis Memory obsolescence mechanism of ?
24、 How to ensure the consistency between cache and database ?
25、redis What is the concurrent competition problem of ? How to solve this problem ? understand redis The transaction CAS The plan ?
26、Redis Of LRU How does the algorithm work ?
27、Redis How to ensure high availability 、 What are the cluster modes ?
28、Redis Threading model ?
29、Redis Master slave architecture ?
30、 say something Redis The concept of hash slot ?
31、Redis Are there any write operations lost in the cluster ? Why? ?
32、Redis How are clusters replicated ?
33、Redis What is the maximum number of nodes in the cluster ?
34、Redis How do clusters choose databases ?
35、Redis It's single threaded , How to improve multicore CPU Utilization ratio ?
36、 How to solve Redis The concurrent competition of Key problem
37、 Distributed Redis Is it done in the early stage or in the later stage ? Why? ?
38、Redis How to implement delay queue
39、Redis And Memcached The difference between
40、Redis Why doesn't the government provide Windows edition ?
41、 What is the maximum storage capacity of a string type value ?
42、 How to ensure the cache and database double write data consistency ?
43、 How to downgrade cache
2、Redis Memory
1、MySQL Are there in 2000w data ,redis The only known 20w The data of , How to ensure Redis The data in is hot data ?
2、Redis What are the main physical resources consumed ?
3、Redis What happens when you run out of memory ?
4、Redis How to optimize memory ?
5、Redis Why so soon?
6、 How do we observe online Redis Memory ?
3、Redis Partition
1、 What is? Redis Partition ?
2、Redis The advantages of zoning ?
3、 Why do it Redis Partition ?
4、 You know what Redis Partition implementation scheme ?
5、Redis What are the disadvantages of zoning ?
6、 What are the common methods of partitioning ?
7、 Talk about the shortcomings of partition technology ?
8、 Partition technology problem solving ?
4、Redis Business
1、 What is business ?
2、 say something Redis Concept of transactions ?
3、Redis What are the three phases of a transaction ?
4、Redis Transaction related orders
5、 Business management (ACID) summary
6、Redis Does transaction support isolation
7、Redis Is the transaction atomic , Support rollback
8、 say something CAS Mechanism .
9、 What should I do if there is an error in transaction execution ?
10、 Redis Why does transaction not support rollback ?
5、Redis Persistence
1、 What is? Redis Persistence ?
2、Redis What is the persistence mechanism of ? Advantages and disadvantages of each ?
3、 What are the advantages and disadvantages ?
4、 How to choose the right way to persist ?
5、Redis How to increase the capacity of persistent data and cache ?
6、 What are the deletion strategies for expired keys ?
7、Rediskey How to set the expiration time and permanent validity of ?
8、 redis How to persist ?
6、Redis Typical problem solutions
1、 What is a cache avalanche ?
2、 Cache avalanche solution ?
3、 What is cache penetration ?
4、 Cache penetration solution ?
5、 What is cache breakdown ?
6、 Cache breakdown solution
7、 What is cache degradation ?
8、 Cache hotspot key
9、edis Supported by Java What does the client have ? Which is the official recommendation ?
10、Redis and Redisson What does it matter ?
11、Jedis And Redisson What are the advantages and disadvantages of comparison ?
12、 How to ensure the cache and database double write data consistency ?
13、 Redis Common performance problems and solutions ?
7、Redis lock
1、 What is? RedLock
2、Redis What are the lock categories ?
3、Redis What is the principle of each lock ?
4、Redis What should I do if I find that the lock has failed ? Interrupt request or loop request ?
5、 Loop request , If one gets the lock , Others are going to get locks , Is it easy to grab the lock ?
6、 After the lock has expired in advance , client A We're not done yet , And then the client B Got the lock , At this point, the client A performed , Will you delete the lock B My lock has been deleted ?
边栏推荐
- Bicolor case
- Abap:ooalv realizes the function of adding, deleting, modifying and checking
- What is the sheji principle?
- Reading notes of Clickhouse principle analysis and Application Practice (4)
- Learn about the Internet of things protocol WiFi ZigBee Bluetooth, etc. --- WiFi and WiFi protocols start from WiFi. What do we need to know about WiFi protocol itself?
- 【问题记录】03 连接MySQL数据库提示:1040 Too many connections
- C language exercises (recursion)
- C realize Snake games
- Displaying currency in Indian numbering format
- 11. Dimitt's law
猜你喜欢
P26-P34 third_ template
QT qtablewidget table column top requirements ideas and codes
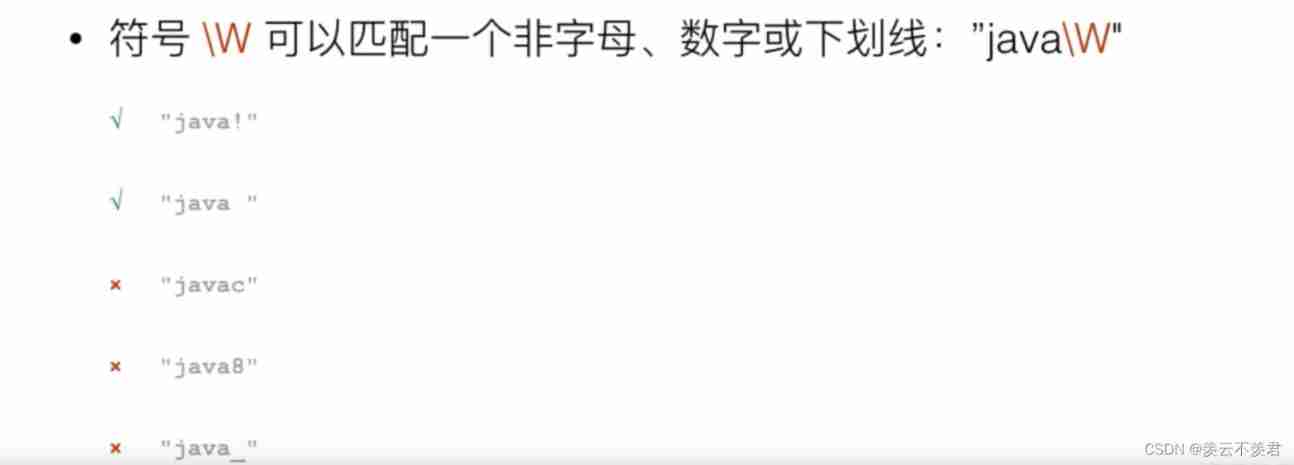
regular expression
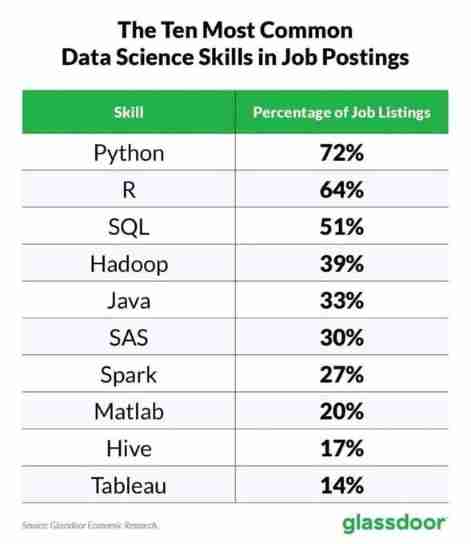
List of top ten professional skills required for data science work
2022 wechat enterprise mailbox login entry introduction, how to open and register enterprise wechat enterprise mailbox?
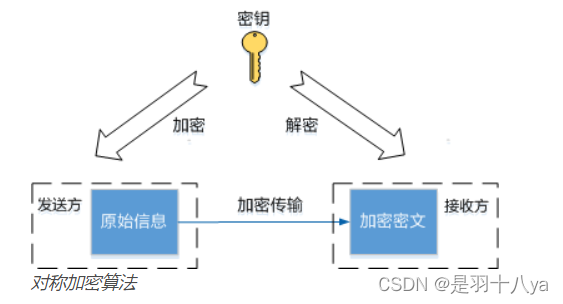
Native Cloud - SSH articles must be read on Cloud (used for Remote Login to Cloud Server)
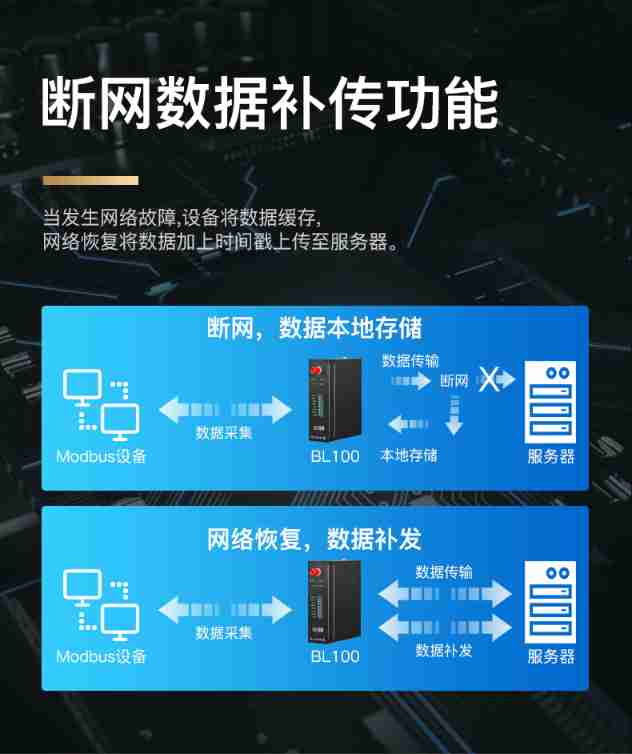
4G wireless all network solar hydrological equipment power monitoring system bms110
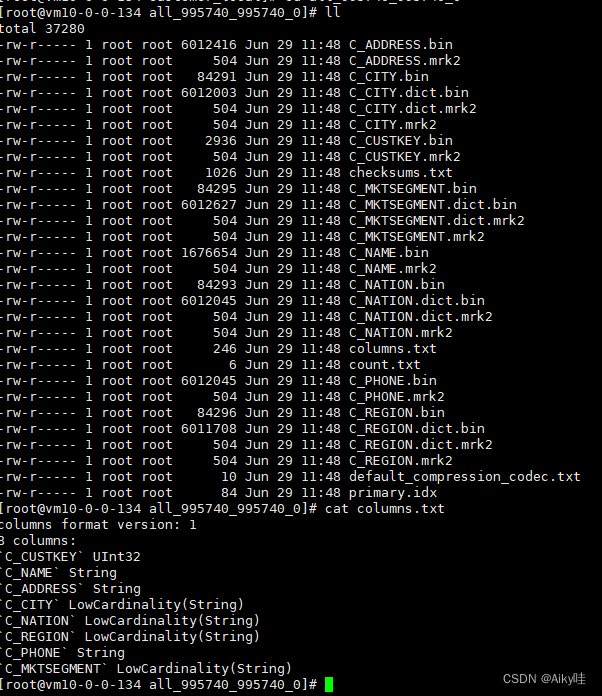
Reading notes of Clickhouse principle analysis and Application Practice (4)
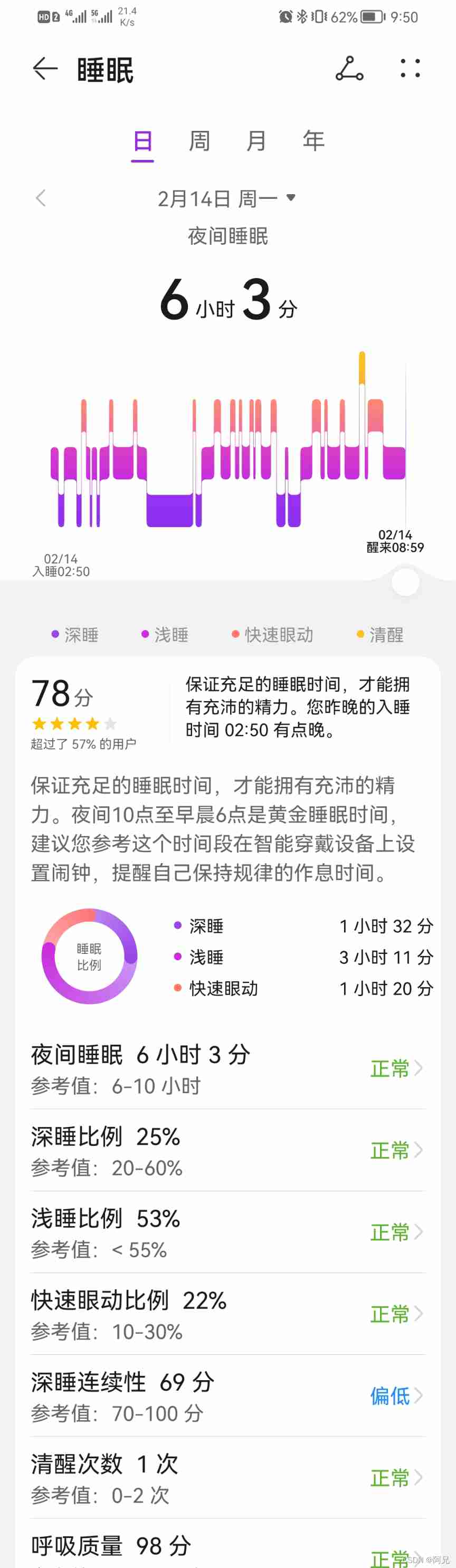
Sleep quality today 78 points
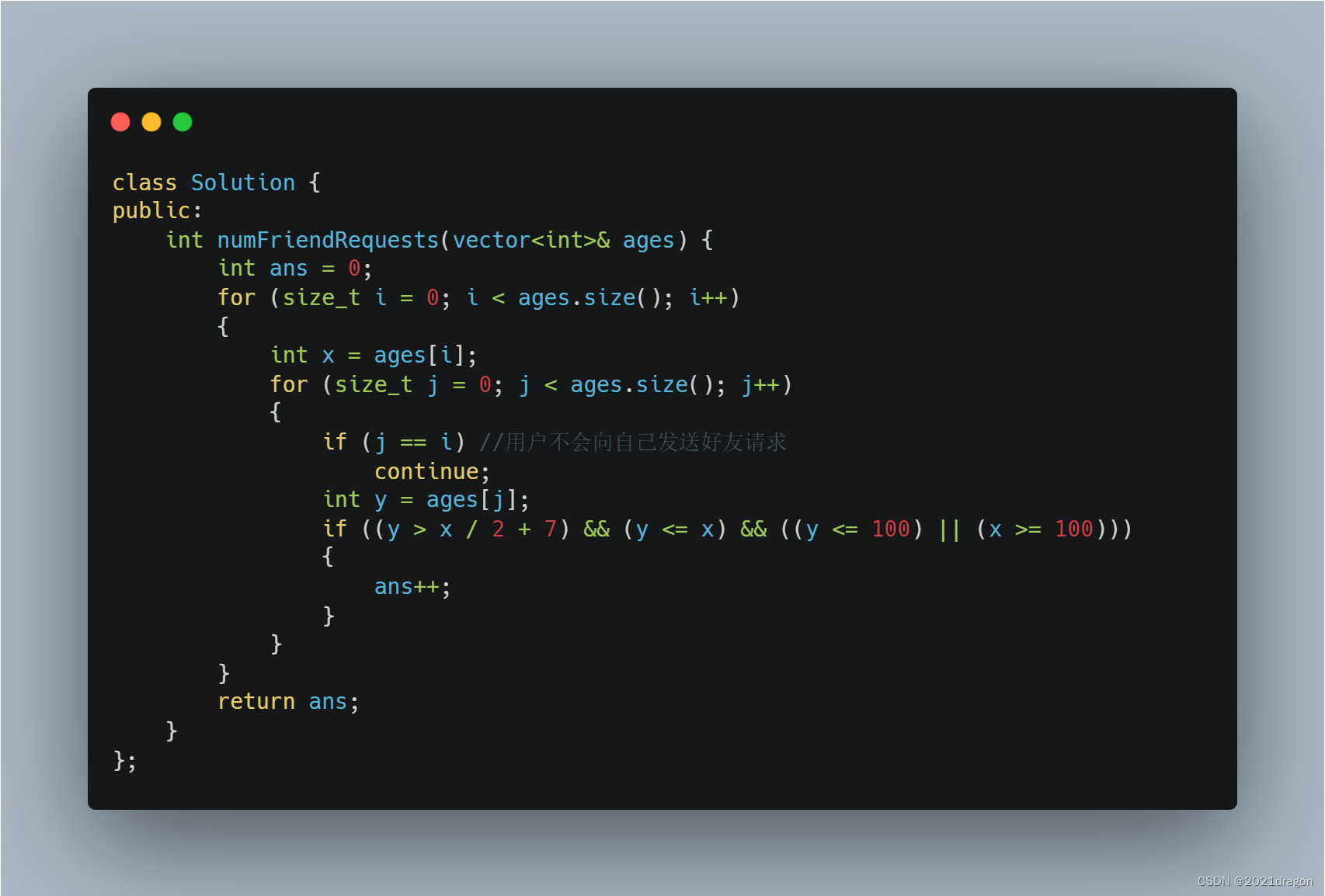
leetcode825. 适龄的朋友
随机推荐
分布式CAP理论
1、 Relevant theories and tools of network security penetration testing
Which water in the environment needs water quality monitoring
Native Cloud - SSH articles must be read on Cloud (used for Remote Login to Cloud Server)
regular expression
Is the insurance annuity product worth buying? Is there a hole?
云原生——上云必读之SSH篇(常用于远程登录云服务器)
Appium foundation - appium installation (II)
Option (024) - do all objects have prototypes?
24 magicaccessorimpl can access the debugging of all methods
C realize Snake games
leetcode825. 适龄的朋友
InputStream/OutputStream(文件的输入输出)
[Android reverse] function interception (CPU cache mechanism | CPU cache mechanism causes function interception failure)
手动对list进行分页(参数list ,当前页,页面大小)
ABCD four sequential execution methods, extended application
2022 Xinjiang's latest eight members (Safety Officer) simulated examination questions and answers
How to avoid JVM memory leakage?
Tar source code analysis 6
tars源码分析之10