当前位置:网站首页>Project practice, redis cluster technology learning (10)
Project practice, redis cluster technology learning (10)
2022-07-02 10:05:00 【User 1289394】
2. Forget nodes
Because the nodes in the cluster keep passing Gossip Message exchange node status , Therefore, a robust mechanism is needed to make all nodes in the cluster forget the offline nodes . In other words, let other nodes no longer communicate with the nodes to be offline Gossip The message exchange .Redis Provides cluster forget{downNodeId} life
Enable this function .
When the node receives cluster forget{down NodeId} After the command , Will be able to nodeId The specified node is added to the disabled list , Nodes in the disabled list will no longer send Gossip news . The disabled list is valid for 60 second , exceed 60 Second, the node will participate in the message exchange again . That is, when the first time forget When the order is given , We have 60 In seconds, all nodes in the cluster forget to go offline .
Direct use of... Is not recommended for online operation cluster forget Command offline node , Need to interact with a large number of node commands , The actual operation is too cumbersome and easy to miss forget node . It is recommended to use redis-trib.rbdel-node{host:port}{downNodeId} command ,
When the offline master node has a slave node, you need to point the slave node to other master nodes , Therefore, for master-slave
Nodes are offline , It is recommended to offline the slave node first and then the master node , Prevent unnecessary full-scale repetition
system . about 6381 and 6384 Node offline operation , The order is as follows :
redis-trib.rb del-node 127.0.0.1:6379
4fa7eac4080f0b667ffeab9b87841da49b84a6e4 # From the node 6384 id
redis-trib.rb del-node 127.0.0.1:6379
40b8d09d44294d2e23c7c768efc8fcd153446746 # Master node 6381 id
Confirm the node status after the node goes offline :
127.0.0.1:6379> cluster nodes
Cluster node status no longer contains 6384 and 6381 node , up to now , We have completed the safe offline of the node , The new cluster structure is shown in the figure below :
10.5 Request routing
At present, we have built Redis Cluster and understand the communication and scaling details , But the client has not been used to operate the cluster .Redis The cluster has made great changes to the client communication protocol , In order to maximize performance , Instead of using the proxy method, it uses the method of client directly connecting nodes . Therefore, for applications that want to switch from a single machine to a cluster environment, the client code needs to be modified .
2.Smart client ——JedisCluster
(1)JedisCluster The definition of
Jedis by Redis Cluster Provides Smart client , The corresponding class is JedisCluster, Its initialization method
as follows :
public JedisCluster(Set<HostAndPort> jedisClusterNode, int connectionTimeout, int
soTimeout, int maxAttempts, final GenericObjectPoolConfig poolConfig) {
...
}Which includes 5 Parameters :
·Set<HostAndPort>jedisClusterNode: all Redis Cluster Node information ( It can also be part of , Because the client can use cluster slots Auto discovery ).
·int connectionTimeout: Connection timeout .
·int soTimeout: Read write timeout .
·int maxAttempts: Retry count .
·GenericObjectPoolConfig poolConfig: Connection pool parameters ,JedisCluster Would be Redis Cluster Create a connection pool for each node .
For example, the following code shows a JedisCluster The initialization process
1. // Initialize all nodes ( for example 6 Nodes )
2. Set<HostAndPort> jedisClusterNode = new HashSet<HostAndPort>();
3. jedisClusterNode.add(new HostAndPort("10.10.xx.1", 6379));
4. jedisClusterNode.add(new HostAndPort("10.10.xx.2", 6379));
5. jedisClusterNode.add(new HostAndPort("10.10.xx.3", 6379));
6. jedisClusterNode.add(new HostAndPort("10.10.xx.4", 6379));
7. jedisClusterNode.add(new HostAndPort("10.10.xx.5", 6379));
8. jedisClusterNode.add(new HostAndPort("10.10.xx.6", 6379));
9. // initialization commnon-pool Connection pool , And set relevant parameters
10. GenericObjectPoolConfig poolConfig = new GenericObjectPoolConfig();
11. // initialization JedisCluster
12. JedisCluster jedisCluster = new JedisCluster(jedisClusterNode, 1000,
1000, 5, poolConfig);JedisCluster You can call commands , As shown below .
jedisCluster.set("hello", "world");
jedisCluster.get("key");(2) Multi node commands and operations
Redis Cluster Although it provides distributed features , But some commands or operations , Such as keys、
flushall、 Delete the key of the specified mode , You need to traverse all nodes to complete . The following code implements from Redis Cluster Delete the function of the specified mode key :
1. // from RedisCluster Batch delete specified pattern The data of
2. public void delRedisClusterByPattern(JedisCluster jedisCluster, String patte
rn,
3. int scanCounter) {
4. // Get... Of all nodes JedisPool
5. Map<String, JedisPool> jedisPoolMap = jedisCluster.getClusterNodes();
6. for (Entry<String, JedisPool> entry : jedisPoolMap.entrySet()) {
7. // Get the Jedis Connect
8. Jedis jedis = entry.getValue().getResource();
9. // Delete only the primary node data
10. if (!isMaster(jedis)) {
11. continue;
12. }
13. // Use Pipeline Delete the data with the specified prefix every time
14. Pipeline pipeline = jedis.pipelined();
15. // Use scan Scan data with the specified prefix
16. String cursor = "0";
17. // Specify scan parameters : Number of scans per time and pattern
18. ScanParams params = new ScanParams().count(scanCounter).match(patter
n);
19. while (true) {
20. // Perform a scan
21. ScanResult<String> scanResult = jedis.scan(cursor, params);
22. // Delete the key list
23. List<String> keyList = scanResult.getResult();
24. if (keyList != null && keyList.size() > 0) {
25. for (String key : keyList) {
26. pipeline.del(key);
27. }
28. // Batch deletion
29. pipeline.syncAndReturnAll();
30. }
31. cursor = scanResult.getStringCursor();
32. // If the cursor changes to 0, Indicates that the scan is complete
33. if ("0".equals(cursor)) { more IT For certification courses, please visit beautiful
break;
35. }
36. }
37. }
38. }
39. // Judge the present Redis Is it master node
40. private boolean isMaster(Jedis jedis) {
41. String[] data = jedis.info("Replication").split("\r\n");
42. for (String line : data) {
43. if ("role:master".equals(line.trim())) {
44. return true;
45. }
46. }
47. return false;
48. }It is divided into the following steps :
1) adopt jedisCluster.getClusterNodes() Get the connection pool of all nodes .
2) Use info replication Screening 1) The master node in .
3) Traverse the master node , Use scan Command to find the specified pattern key, Use Pipeline Mechanism delete .
For example, the following operations traverse each time 1000 individual key, take Redis Cluster China and Israel user At the beginning key whole
Department delete .
String pattern = "user*";
int scanCounter = 1000;
delRedisClusterByPattern(jedisCluster, pattern, scanCounter);
So for keys、flushall And other commands that need to traverse all nodes , You can also refer to the above method to realize the corresponding functions .
(3) There are more methods of batch operation IT For certification courses, please visit Meihe learning online ww
Redis Cluster in , because key Distributed to each node , It will make it impossible to achieve mget、mset And so on . But it can be used CRC16 The algorithm calculates key Corresponding slot, as well as Smart The client saved slot Characteristics corresponding to nodes , Will belong to the same Redis Node key Filing , Then, the corresponding sub nodes of each node are analyzed respectively key List execution mget perhaps pipeline operation .
(4) Use Lua、 Methods of transaction and other characteristics
Lua And transactions need to be operated key, Must be on a node , however Redis Cluster Provides hashtag, If developers really want to use Lua Or business , You can set what you want to do key Use one hashtag, As shown below :
1. // hashtag
2. String hastag = "{user}";
3. // user A Your attention list
4. String userAFollowKey = hastag + ":a:follow";
5. // user B My fan list
6. String userBFanKey = hastag + ":b:fans";
7. // Calculation hashtag Corresponding slot
8. int slot = JedisClusterCRC16.getSlot(hastag);
9. // Get specified slot Of JedisPool
10. JedisPool jedisPool = jedisCluster.getConnectionHandler().getJedisPoolFromSl
ot(slot);
11. // Execute transactions on the same node
12. Jedis jedis = null;
13. try {
14. jedis = jedisPool.getResource();
15. // user A Join the user's attention table B, user B Add users to your fan list A
16. Transaction transaction = jedis.multi();
17. transaction.sadd(userAFollowKey, "user:b");
18. transaction.sadd(userBFanKey, "user:a");
19. transaction.exec();
20. } catch (Exception e) {
21. logger.error(e.getMessage(), e);
22. } finally {
23. if (jedis!= null)
24. jedis.close();
25. }All the in the transaction key add to hashtag.
2) Use CRC16 Calculation hashtag Corresponding slot.
3) Get specified slot The corresponding node connection pool JedisPool.
4) stay JedisPool Execute transactions on .
边栏推荐
- [illusory] automatic door blueprint notes
- 2837xd code generation - Summary
- Minimum number of C language
- 【UE5】动画重定向:如何将幻塔人物导入进游戏玩耍
- Inverter Simulink model -- processor in the loop test (PIL)
- How does {} prevent SQL injection? What is its underlying principle?
- Image recognition - data annotation
- What wires are suitable for wiring on bread board?
- Read Day6 30 minutes before going to bed every day_ Day6_ Date_ Calendar_ LocalDate_ TimeStamp_ LocalTime
- Is the C language too fat
猜你喜欢
Bookmark collection management software suspension reading and data migration between knowledge base and browser bookmarks

Alibaba cloud SMS service

In SQL injection, why must the ID of union joint query be equal to 0

Eslint reports an error

2837xd 代码生成——StateFlow(3)
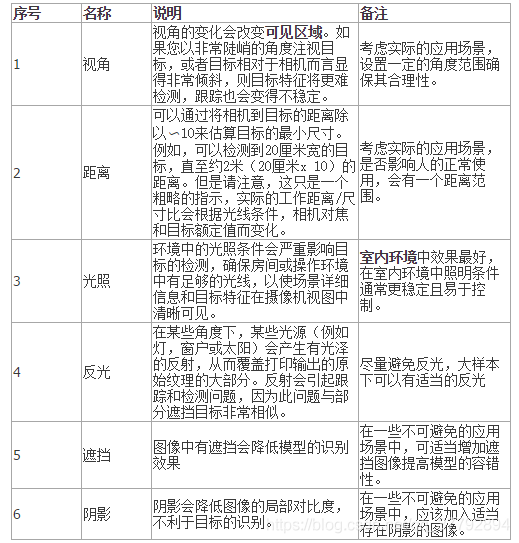
Image recognition - Data Acquisition
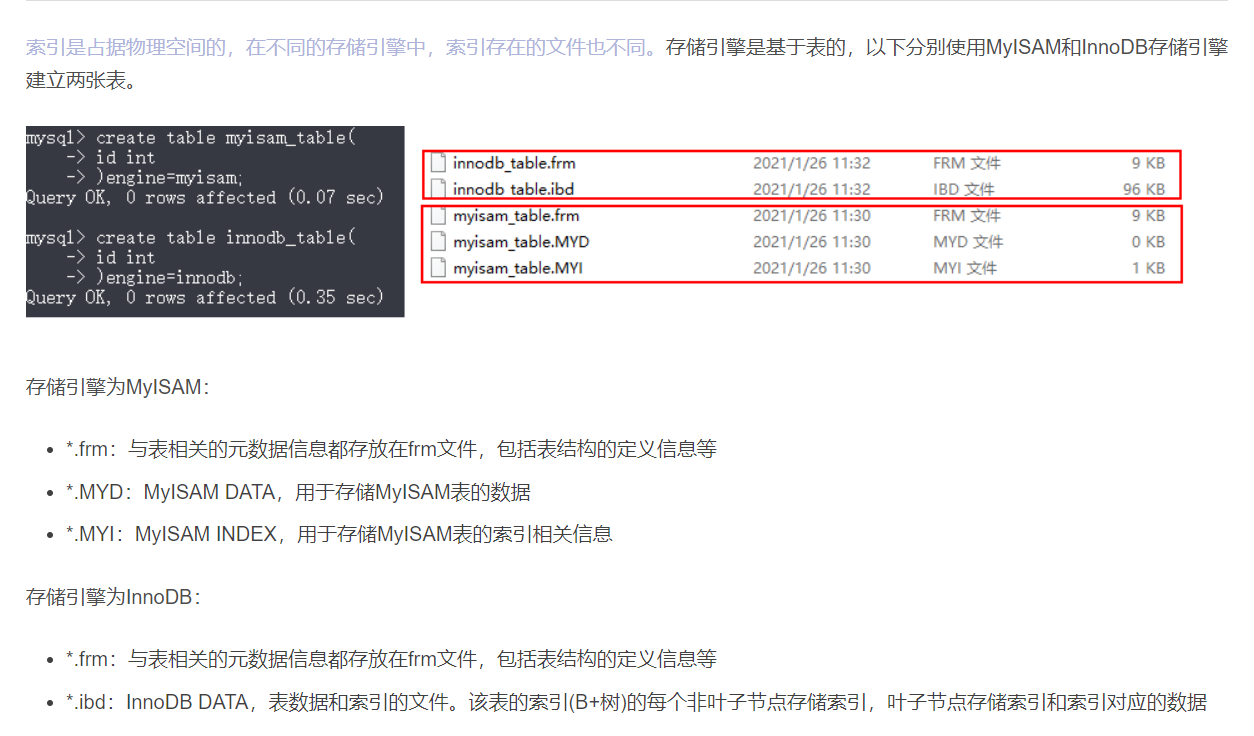
Mysql索引

【UE5】动画重定向:如何将幻塔人物导入进游戏玩耍
Matlab generates DSP program -- official routine learning (6)

图像识别-数据采集
随机推荐
ue虛幻引擎程序化植物生成器設置——如何快速生成大片森林
Junit5 supports suite methods
Alibaba cloud SMS service
2837xd代码生成模块学习(4)——idle_task、Simulink Coder
Mysql索引
Binary and decimal system of C language
【虚幻】武器插槽:拾取武器
QT信号槽总结-connect函数错误用法
Memories of a chat
Idempotent design of Internet API interface
Share a blog (water blog)
ue虚幻引擎程序化植物生成器设置——如何快速生成大片森林
ZK configuration center -- configuration and use of config Toolkit
tinyxml2 读取和修改文件
Record personal understanding and experience of game console configuration
kinect dk 获取CV::Mat格式的彩色RGB图像(openpose中使用)
It is the most difficult to teach AI to play iron fist frame by frame. Now arcade game lovers have something
[ue5] animation redirection: how to import magic tower characters into the game
2837xd 代码生成——补充(2)
Alibaba cloud Prometheus monitoring service